Introduction
First, let’s understand what is single sign on. Introducing Single Sign On (SSO) to your customers can offer greater security and improved usability. That’s two of the many key benefits of SSO.
Let’s face it. No one likes remembering credentials. They seem like exerting a lot of pressure on the memory. What's worse is many use the same username and password, irrespective of the application they are using.
This is where the Single Sign On technology comes into focus and works like a champ. To understand this solution, let's consider an analogy: "Imagine going to the mall, and at each store, you must register with the store for your first purchase. Then, every time after that, you have to prove who you are to buy something."
Unfortunately, this is what happens when you shop online. Each website makes you create a new and unique identity specific to that website. On top of that, you have to login and authenticate each time.
While some web properties do offer the option to sign in using social identity, the majority of customers still have to log in to each web property. This often happens even when the websites are part of the same parent organization.
What is Single Sign-On?
Single Sign-On (SSO) is a method of authentication that allows websites to use other trustworthy sites to verify users. Single sign-on allows a user to log in to any independent application with a single ID and password.
SSO is an essential feature of an Identity and Access Management (IAM) platform for controlling access. Verification of user identity is important when it comes to knowing which permissions a user will have. The LoginRadius Identity platform is one example of managing access that combines user identity management solutions with SSO solutions.
How Does Single Sign-On Works?
Single sign-on (SSO) is a system that allows users to access multiple applications and services with just one set of login credentials.
SSO works by authenticating a user's identity once and then granting access to all of the applications and services that the user is authorized to access. When a user attempts to access a resource from a service provider, the SSO system sends a request to the user's identity provider to authenticate the user's identity.
Once the user is authenticated, the identity provider sends the necessary credentials to the service provider, allowing the user to access the requested resource. This process eliminates the need for users to remember and manage multiple usernames and passwords, streamlining the login process and improving the user experience.
SSO also simplifies identity management for organizations, reducing the risk of data breaches and improving overall security.
What Is a Single Sign-On (SSO) Authentication Token?
An SSO authentication token is a crucial aspect of the SSO process. Once a user is successfully authenticated, the Identity Provider (IDP) generates a token. This token contains information about the user's identity and permissions. The Service Provider (SP) then recognizes this token, granting access to the user without the need for re-authentication. Tokens are typically encrypted to ensure secure transmission and storage of user data.
How Are SAML and OAuth Used with Single Sign-On?
- SAML (Security Assertion Markup Language): SAML is an XML-based open standard used for exchanging authentication and authorization data between the IDP and SP. It enables seamless SSO by allowing the IDP to send assertions about the user to the SP, which then grants access based on these assertions.
- OAuth (Open Authorization): OAuth is another protocol used with SSO, often seen in scenarios where a user wants to grant access to their information without sharing their credentials. It allows the user to authorize a third-party application to access their resources on another service provider. OAuth enhances security and user control in SSO scenarios.
What Makes a True Single Sign-On System?
A true SSO system offers several key features:
- Centralized Authentication: Users authenticate once, and this authentication is recognized across all connected applications.
- Seamless Experience: Users navigate between applications without the need for repeated logins.
- Token-Based Access: The system uses tokens to securely transmit and store user credentials and permissions.
- Integration with Identity Providers: The system seamlessly integrates with various identity providers, such as Microsoft Active Directory or Google Directory.
What is an SSO Software vs. an SSO Solution?
- SSO Software: This refers to the technology and tools used to implement SSO, including protocols like SAML, OAuth, and OpenID Connect. It involves the software components that manage user authentication and authorization.
- SSO Solution: An SSO authentication solution is a comprehensive package that includes SSO software along with additional features like user management, multi-factor authentication (MFA), and identity governance. It provides a complete system for managing user access across applications.
What is App-to-App Single Sign-On (SSO)?
App-to-App SSO authentication, also known as Service-to-Service SSO, enables seamless authentication and access between different applications within an organization's ecosystem. Instead of requiring users to log in multiple times when switching between apps, this approach maintains authentication sessions across the apps. It enhances productivity and user experience by eliminating the need for repeated logins.
What is Single Sign-On (SSO) Software as a Service (SaaS)?
SSO Software as a Service (SaaS) is a cloud-based solution that offers SSO functionality to organizations without the need for on-premises infrastructure. With SSO SaaS, organizations can easily implement SSO across their applications and services by subscribing to a third-party provider. This approach simplifies deployment, maintenance, and scalability of SSO, making it accessible to businesses of all sizes.
How Does Single Sign-On (SSO) Fit into an Access Management Strategy?
Integrating SSO authentication into an Access Management Strategy enhances security, user experience, and operational efficiency:
- Enhanced Security: SSO reduces the risk of password-related vulnerabilities and unauthorized access.
- Streamlined User Experience: Users enjoy a seamless login experience across applications, boosting productivity.
- Centralized Access Control: Administrators can manage user access and permissions from a centralized platform, ensuring consistency and compliance.
- Cost Efficiency: SSO reduces IT costs associated with password resets and support, freeing up resources for other critical tasks.
Incorporating SSO into an Access Management Strategy strengthens overall security posture while simplifying user access across the organization's digital assets.
What are the Benefits of Single Sign-On?
Single Sign-On clearly minimizes the risk of poor password habits. Also, removing login credentials from servers or network storage can help a great deal in preventing a cyber attack.
Benefits for Customers
1. Seamless user experience
Customers can use a single identity to navigate multiple web and mobile domains or service applications.
2. Stronger password protection
Because users only need to use one password, SSO makes generating, remembering, and using stronger passwords simpler for them.
3. Reduces customer time
The time spent on re-entering passwords for the same identity. Users will spend less time logging into various apps to do their work. Ultimately it enhances the productivity of businesses.
Benefits for Business
1. Improves conversions and revenue
Customers can access all domains and services with a single active session.
2. Mitigates risk
Accessing third-party sites (user passwords are not stored or managed externally) becomes risk-free.
3. Unifies customer profiles
Creating a single instance of the customer data provides a centralized view of the customer across all channels.
4. Reduces IT costs
Due to fewer help desk calls about passwords, IT can spend less time helping users to remember or reset their passwords for hundreds of applications.
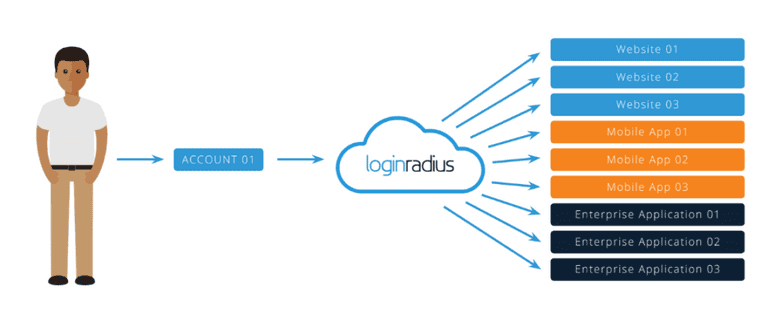
What are the Different Types of Single Sign-On?
Single sign-on (SSO) is not a one-size-fits-all solution, and there are several different types of SSO that organizations can choose from. The most common types of SSO include:
- Web SSO: This type of SSO allows users to access multiple web-based applications and services with a single set of credentials. When a user logs in to one of the web-based applications, they are automatically logged in to all of the other applications that they are authorized to access.
- Enterprise SSO: Enterprise SSO is designed for organizations that use a mix of web-based and non-web-based applications. This type of SSO typically involves the use of a desktop client or browser extension that manages the user's credentials and automates the login process.
- Mobile SSO: Mobile SSO allows users to access mobile applications with a single set of credentials. This type of SSO is becoming increasingly popular as more organizations adopt mobile-first strategies.
How is Single Sign-On Implemented?
Implementing single sign-on (SSO) requires careful planning and coordination between the identity provider and the service providers. The first step in implementing SSO is to choose an identity provider that supports the necessary protocols, such as SAML, OAuth, or OpenID Connect.
Once the identity provider has been selected, the service providers must be configured to accept SSO requests from the identity provider. This typically involves configuring the service providers to trust the identity provider and to use the appropriate SSO protocol.
The identity provider must also be configured to authenticate users and provide the necessary credentials to the service providers. Finally, the SSO system must be tested to ensure that it is working properly and that users are able to access the resources that they are authorized to access.
How to Choose a Secure SSO Solution?
Your SSO solution must meet the basic needs to support IT needs. That means a stable solution and a highly functional one. Today, digital transformation relies on a platform for Customer Identity and Access Management (CIAM), which includes SSO and other tools. So, here what you need to keep in mind while narrowing down your SSO solution.

7 Key Points to Consider While Choosing a Secure Single Sign-On Solution
1. Support for Developers
Make sure your SSO solution provides adequate life-cycle management API support and SDKs for major platforms.
2. Authentication
What about the extra layer of security? Find out if it supports MFA, adaptive authentication, automatic forced authentication, and more.
3. Federation
Find out if you will be allowed to use any corporate identity provider you prefer. Make sure it supports Microsoft Active Directory, Google Directory, etc.
4. Mobile phones ready
Ensure that your identity platform supports SSO for mobile devices and syncs well with various multi-factor authentication tools.
5. Flexible rules governing passwords
It should support password validation requirements like customizable password expiration limit, password complexity, and expiration notifications.
6. Safety reputation
Check out if it meets security standards like ISO 27017, ISO 27018, ISO 27001, SOC 2 Type 2, and global compliances like the GDPR and CCPA, etc.
7. Behavioral analytics
Find out if it allows you to blacklist or whitelist IPs, set responses to counter brute force attempts and there are provisions for re-authentication.
How LoginRadius Single Sign-On Authentication Works?
Since now you know what is single sign on, let’s understand how LoginRadius SSO is superior. Single sign on (SSO) can be implemented in several ways, but typically follows a standard or protocol, as well as several technologies which can enforce the standards/protocols listed below.
1. Web SSO
Web single sign-on enables your customers to access any of your connected web properties with a single identity. As customers navigate from one site to the next, your systems will be able to recognize who they are on each site.
Web Single Sign-On also is known as LoginRadius Single Sign-On, is a browser-based session management system that uses browser storage mechanisms (sessionStorage, localStorage, Cookies) to hold the user session across your assets.
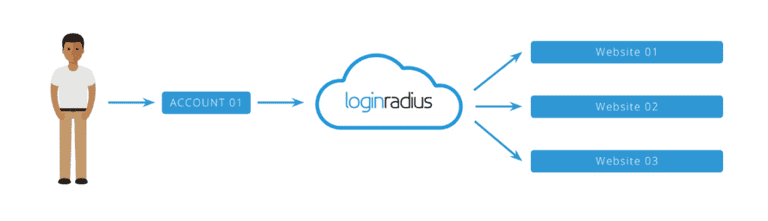
This storage is stored on a centralized domain managed by LoginRadius and can be accessed via our JavaScript Single Sign-On APIs, or directly through a JSONP call. This session is integrated seamlessly into our standard Customer Identity and Access Management scripts.
2. Mobile SSO
Mobile single sign-on is like web SSO, except that customers can use a single identity to access connected mobile apps.
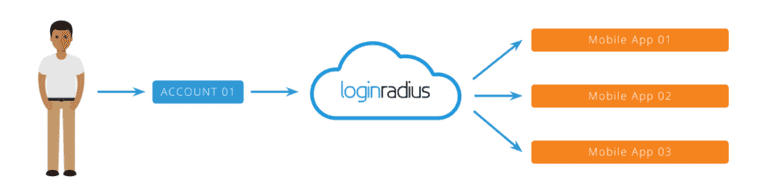
Mobile SSO enables you to unify a user session across multiple apps that are serviced by a single account LoginRadius. It works by storing the LoginRadius access token in a shared session, either shared Android preferences or iOS keychain, which allows you to recognize a currently active session and access current user data sessions to configure your user account with each linked program.
3. Federated SSO
Federated single sign-on works a little differently than the web and mobile SSO. Rather than connecting websites or mobile apps, you use the login credentials held by partners. This happens by using industry-standard SSO protocols, which allow customers to gain access to web properties without authentication barriers.
LoginRadius also acts as an IdP that stores and authenticates the identities used by end-users to log in to customer systems, applications, file servers, and more depending on their configuration.
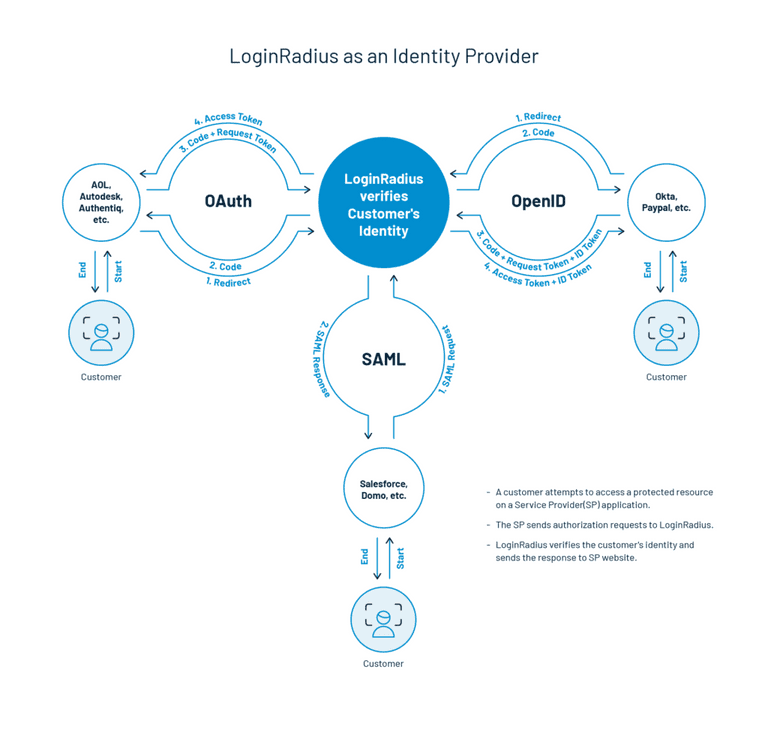
LoginRadius serves as a software provider providing end-user services. LoginRadius does not authenticate users but instead requests third-party Identity Provider authentication. LoginRadius relies on the identity provider to verify a user's identity and, if necessary, to verify other user attributes that the identity provider manages.
SAML
Security Assertion Markup Language (SAML) is an open standard enabling identity providers (IdP) to pass credentials for authorization to service providers. In simple terms, it means that you can log into several different websites using one set of credentials.
LoginRadius supports both SAML 1.1 and SAML 2.0 flows to support LoginRadius either as an IDP or as a Service Provider (SP). LoginRadius supports SAML flows, both initiated by IDP and initiated by SP.
The LoginRadius Admin Console allows the SAML settings to be entirely self-service, allowing you to configure statements, keys, and endpoints to suit any SAML provider.
JWT
JSON Web Token (JWT) is a commonly used Single Sign-On protocol widely used in B2C applications and included in RFC 7519. This protocol helps you to create an encrypted token that is encoded in JSON. In LoginRadius, this can either be created via API or directly requested through the responses to the Login and Social Login interface.
This token is then transferred and consumed on to the third-party service provider. The data to be collected can be mapped to the LoginRadius Admin Console. You can also configure the token's encryption method based on the service provider's specifications, which will consume the token.
OAuth
OAuth is an open-standard authorization protocol or framework that describes how unrelated servers and services can securely enable authenticated access to their assets without actually sharing the initial, related, single login credential. This is known as safe, third party, user-agent, delegated authorization in authentication parlance.
LoginRadius may either function as an OAuth 2.0 Identity Provider or as a Service Provider delegating the authentication process to an IDP supporting the OAuth Project. The specifications for OAuth 2.0 are protected in RFC 6749.
Such specs cover the various specifications and structured processes OAuth embraces. From the authorization of the service provider requesting authentication to the request for authorization from the end-user to the generation of the access token used to request the scoped data from the IDP after authentication.
OpenID Connect
OpenID Connect or (OIDC) is an authentication layer standardized by the OpenID Foundation atop the OAuth 2.0 framework. By following the specifications defined in the OpenID Connect specs, LoginRadius provides a way to integrate your OpenID Connect client with our API. These specs cover the various specifications and structured processes adopted by OpenID Link.
Multipass
Multipass is one of the most simple forms of authentication with SSO. Multipass is done through the generation of an authenticated JSON hash of the values to be sent to the service provider.
Conclusion
Deciding the best implementation method really depends on your individual situation, technical architecture, and business needs. If you think a readymade SSO solution is best for your company, a customer identity provider like LoginRadius will help you achieve fast and easy implementation.
Frequently Asked Questions (FAQs)
1. What is an example of SSO?
The best example of SSO login is Google’s implementation of SSO in its products. For instance, if you’re logged in to Gmail, you automatically gain access to all other products of Google like YouTube, Google Drive, Google Photos, etc.
2. What is the difference between single sign-on (SSO) and social login?
SSO offers seamless authentication with one credential across multiple connected platforms or systems. On the other hand, social login allows users to access services by authenticating themselves using their social account credentials.
3. What are the benefits and business advantages of single sign-on (SSO)?
Businesses can leverage SSO to deliver a seamless user experience at every touchpoint. Moreover, SSO can help online platforms derive more conversions and growth.
4. What is the difference between SSO and federation?
The main difference between Identity Federation and SSO lies in the range of access. SSO allows users to use a single set of credentials to access multiple systems within a single organization (a single domain). On the other hand, Federation lets users access systems across federated organizations.
5. How can I get SSO for my OTT platform?
SSO integration can be done through a cloud-based CIAM solution like LoginRadius. The cutting-edge CIAM helps OTT platforms to deliver a seamless user experience across multiple touchpoints. Read more.
6. What is the Single Sign-On (SSO) protocol?
SSO protocol enables users to access multiple applications with a single set of login credentials using standards like SAML, OAuth, or OpenID Connect.
7. What are three benefits of Single Sign-On (SSO)?
Enhanced security, improved user experience, and increased productivity.
8. What is the difference between Same Sign-On and Single Sign-On?
Same Sign-On is not a standard term; Single Sign-On (SSO) allows users to log in once and access multiple applications securely.
9. What is the purpose of Single Sign-On (SSO)?
Simplify authentication for users and enhance security by allowing access to multiple applications with one login.



