SMS Passcode Authenticator
In the SMS Passcode flow, consumers receive a One-Time Passcode (OTP) on their registered phone number, which is used during the second step of Multi-Factor Authentication (MFA).
Flow Diagram:
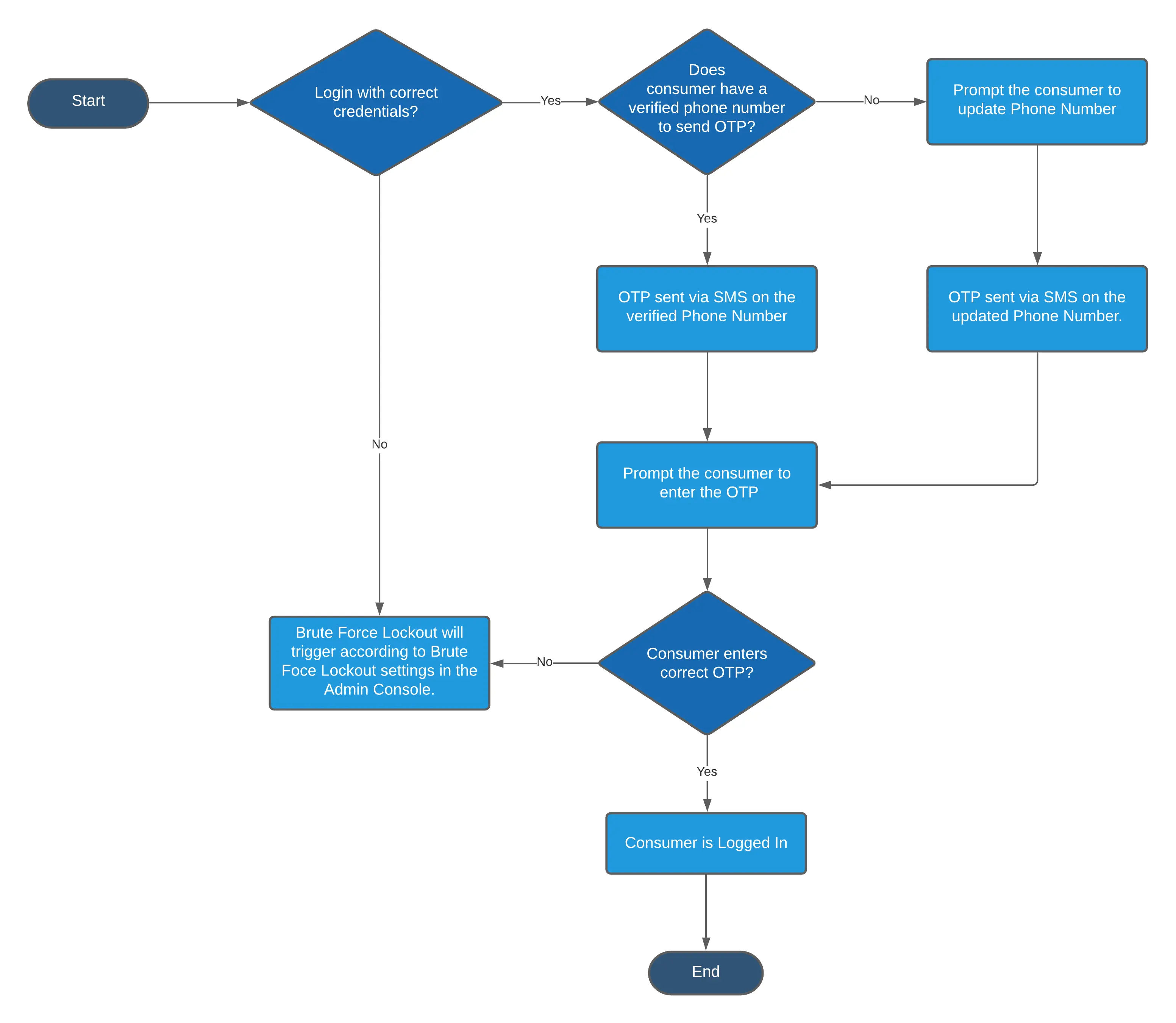
MFA SMS OTP configuration
Console
JavaScript Interface Integration
To use the LoginRadius JavaScript Interface for SMS-based MFA:
- Initialize the LoginRadius interface on your page as shown here.
- Once you intitalize the LoginRadius JS interface follow this document to integrate the MFA interface in your application.
- In the configuration options, add:
- twoFactorAuthentication (Required): Set to true to enable MFA
- smsTemplate2FA (Optional): Specify your custom SMS template name. If not provided, the default template will be used.
- After successful login, you may give consumers options to manage their MFA settings (e.g., change phone number, disable MFA).
SMS API Implementation
Follow the steps below to implement MFA via our MFA API, which uses a mix of front-end and back-end API calls.
Note: If an API call requires an API Secret, it should be called from the back end. Otherwise, the API call can also be used on the front end.
First Factor Authentication
Verifying OTP via SMS
Resetting/Upating SMS Authenticator
Set up the initial login using one of the following MFA-enabled APIs:
- MFA Email Login API: To have a Standard Login flow requiring email and password.
- MFA UserName Login API: Use UserName and Password instead of Email and Password.
- MFA Phone Login: If your API has been configured for Phone-based Authentication, use this API to authenticate the user via phone.
After successful authentication, the response includes details for MFA, including Sms OTP status and available questions:
{
SecondFactorAuthentication": {
"SecondFactorAuthenticationToken": "32ba53ff-XXXX-XXX-XXX-XXXXXXXXXXXX",
"ExpireIn": "2017-08-31T01:39:28.1427384Z",
"QRCode": "http://chart.googleapis.com/chart?cht=XXXXXXXXXXXXX",
"ManualEntryCode": "XXXXXXXXXXXXXXXXXXXX",
"IsGoogleAuthenticatorVerified": false,
"IsEmailOtpAuthenticatorVerified": false,
"IsOTPAuthenticatorVerified": false,
"OTPPhoneNo": null,
"OTPStatus": null,
"Email": [
"x**z@e****le.c*m"
],
"EmailOTPStatus": {
"Email": "x**z@e****e.c*m"
},
"IsSecurityQuestionAuthenticatorVerified": false,
"SecurityQuestions": [
{
"QuestionId": "<QuestionId>",
"Question": "<Question>"
}
]
},
"Profile": null,
"access_token": "00000000-0000-0000-0000-000000000000",
"expires_in": "0001-01-01T00:00:00"
}
If IsOTPAuthenticatorVerified is false or null, the consumer has not yet verified a phone number. Prompt them to verify using the Update Phone Number API.
Validate OTP (Standard MFA Flow)
Use Case: Consumer has received the OTP via SMS.
- API: MFA Validate OTP
- Inputs:
API KeySecondFactorAuthenticationTokenOTP(received by SMS)
- Inputs:
Allow consumers or admins to reset the SMS authenticator using the following APIs:
Reset by Token
Reset by UID (Server-side)
Update MFA Settings
Update Phone Number After Login
- API: MFA Reset SMS Authenticator by Token
- Inputs:
Access TokenAPI Key
- API: Reset MFA SMS Authenticator Settings by UID
- Inputs:
UIDAPI KeyAPI Secret
Use Case: Consumer wants to manage MFA preferences after login.
- API: Update MFA settings
- Inputs:
Access TokenMFA optionsAPI Key
Use Case: Consumer wants to update their MFA phone number.
- API: Update Phone Number API by token
- Inputs:
Access TokenNew Phone NumberAPI Key