MFA with Risk-Based Authentication (RBA)
Risk-based authentication (RBA), called Adaptive Authentication, enhances login security by evaluating consumer behavior during authentication. Based on historical patterns—such as device, location, or browser—RBA identifies anomalies and triggers additional actions, like notifying users or administrators.
This guide integrates Risk-Based Authentication with Multi-Factor Authentication (MFA) using LoginRadius. It covers configuration steps and best practices to strengthen your application’s login security.
To learn more about RBA in general, visit our detailed RBA documentation.
Key Features
- Behavioral Analysis:
Detects deviations from known consumer behavior using Browser, Device, IP, City, and Country factors. - Layered Security Approach:
RBA acts as an additional security layer after successful MFA verification. - Customizable Notifications:
Admins and consumers can be instantly notified if a risk is detected. - Priority-Based Evaluation:
Risk factors are evaluated in a strict sequence (Device → Browser → City → Country → IP). - Flexible Retention Settings:
Risk evaluation history can be maintained based on time (days) or event counts. - Non-intrusive Action:
No forced authentication challenges; only notifications are sent, preserving user experience while improving security monitoring.
Use Cases
Here are real-world scenarios where RBA combined with MFA provides tangible security benefits:
-
Prevent Credential Stuffing: Even if a user's credentials are compromised, RBA flags unusual access from unknown devices or locations after MFA verification, preventing silent takeovers.
-
Monitor Global Workforce Logins: Enterprises with remote employees can track unexpected logins from unfamiliar countries or cities, helping flag VPN misuse or unauthorized access.
-
Secure Traveler Accounts: For frequent travel users (e.g., sales reps or consultants), RBA ensures that logins from new places are logged and alerted without blocking access.
-
Protect VIP and Admin Accounts: High-privilege accounts can be closely monitored by enabling all five risk factors and routing notifications directly to security teams.
-
Comply with Industry Regulations: RBA helps meet security expectations in regulated industries (e.g., finance, healthcare) by providing visibility into unusual login behaviors.
RBA workflow with MFA
RBA analyzes certain consumer attributes at login, such as browser, city, country, IP address, or device, against their previously recorded activity. Based on the evaluation, it either allows seamless login or triggers risk alerts.
Here’s a typical workflow when RBA is combined with MFA:
-
A consumer logs in with valid credentials.
-
After primary authentication, they complete the configured MFA (e.g., OTP, Authenticator App).
-
LoginRadius evaluates configured risk factors against stored data (e.g., checks if the login is from a recognized device or location).
- If the factors match, the Login is considered safe and proceeds without interruption.
- If the factors mismatch, the system flags it as a potential risk and sends notifications based on the configuration.
Note: RBA with MFA is not enabled by default. You must request activation by contacting LoginRadius Support.
Flow Diagram:
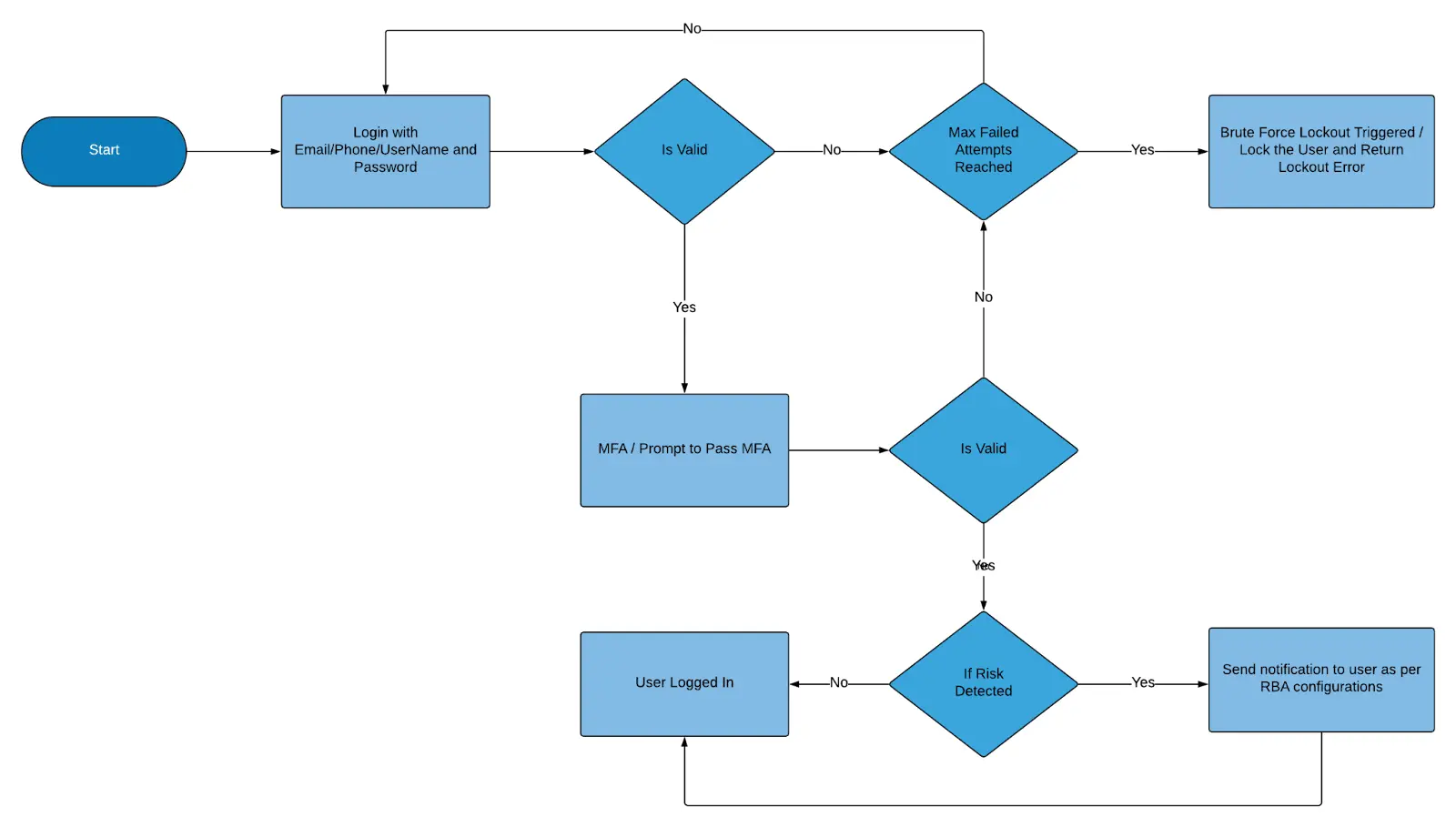
Risk Factors Available
You can configure any of the following as risk factors:
-
Device
-
Browser
-
City
-
Country
-
IP Address
Note: If all five risk factors are configured, the evaluation order is: Device ➔ Browser ➔ City ➔ Country ➔ IP
Configuring RBA with MFA in the Console
To implement Risk-Based Authentication over existing MFA:
- Log in to your LoginRadius Console.
- First, follow the instructions in this documentation to configure the RBA.
- Once the RBA factors are configured, select the Additional Settings tab under the RBA.
- If the detected behavior meets your risk criteria, the user must undergo Multi-Factor Authentication. The Multi-Factor Settings option allows you to configure Multi-Factor Authentication from the dropdown menu.
- You can also configure notifications for Admins when a risk event occurs by adding one or multiple Admin email addresses under the Admin Email section.
Note: No changes are needed in the MFA settings when enabling RBA. RBA acts after MFA verification is complete.
Customizing Email Templates
Manage the email content sent to consumers and admins:
- Navigate to the Email Templates section under the Brading→Email Template section of the LoginRadius Console.
- Select the relevant template type as per the respective Event (e.g., City, Browser, Device) from the left pane menu under the Risk-Based tab.
- Use the default email template content or add your email template as per your needs.
Best Practices
-
Start with High-Impact Risk Factors:
Prioritize configuring the Device and Browser first, as they offer the best early indicators of suspicious activity. -
Use Admin and Consumer Notifications Together:
Enabling notifications for both parties ensures faster detection and resolution of suspicious logins. -
Monitor Notification Volume:
Regularly review risk alert logs to fine-tune sensitivity and avoid alert fatigue. -
Educate Users:
Let consumers know that they will receive notifications for logins from new devices or locations—this will build trust and prevent confusion. -
Review Risk Patterns Regularly:
Use analytics and event reports to spot trends in suspicious login attempts and adapt your security policies accordingly. -
Test Before Going Live:
Thoroughly test RBA behavior in staging environments to avoid excessive or incorrect notifications after rollout.