Purpose-Built IAM for Your B2B Customers, Partners, and Vendors
Legacy IAM wasn’t built for B2B. LoginRadius is.Manage external identities with ease — delegate access, enforcegranular permissions, and onboard entire organizations without hacks,patches, or compromises.
35+
Multi-region data centers
100%
Uptime
7.6 B+
API calls per month
1.5 B+
Identities managed every month
Get Organizations to Onboard in Minutes, Not Months
Flexible Authentication For Each Organization
Tailor secure and seamless sign-in experiences for each partner/vendor organization based on their specific needs. Configure authentication methods like email/password, social login, passkeys, and passwordless login at the organizational level.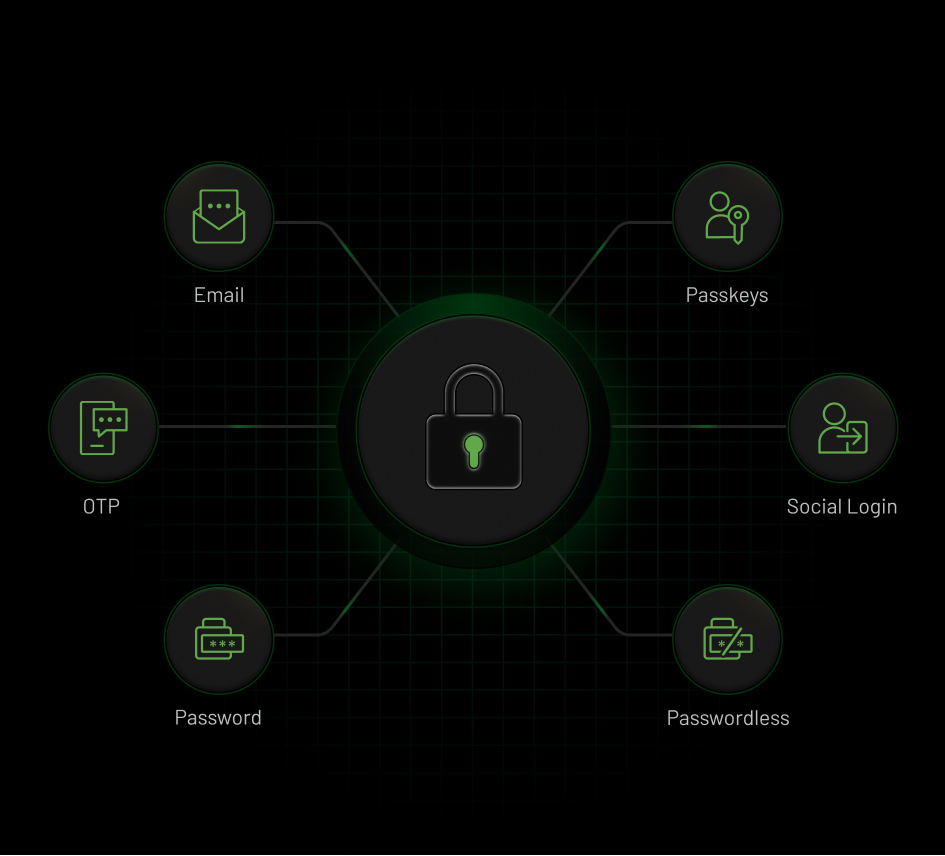
Role-Based Access Management (RBAC)
Assign roles and permissions at the resource level and across each organization. You can choose from predefined roles or create custom roles tailored to your needs.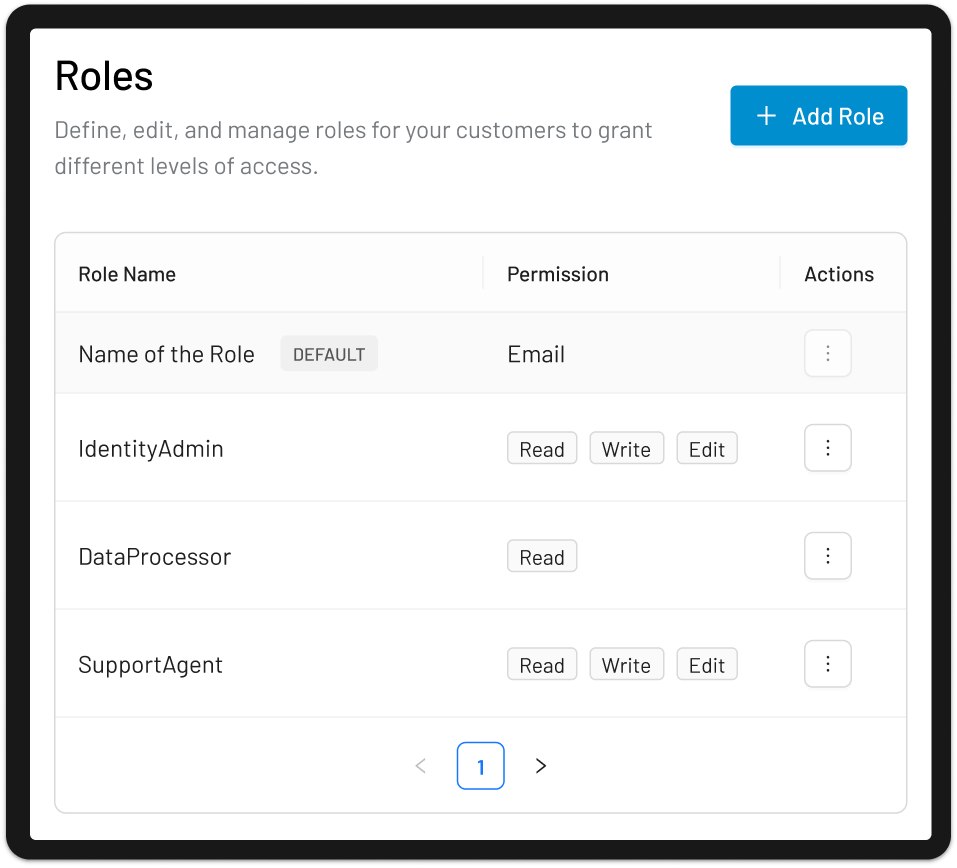
Automated User Provisioning
Simplify access management with directory sync and Just-in-Time (JIT) provisioning, ensuring organizations are automatically onboarded with the right access.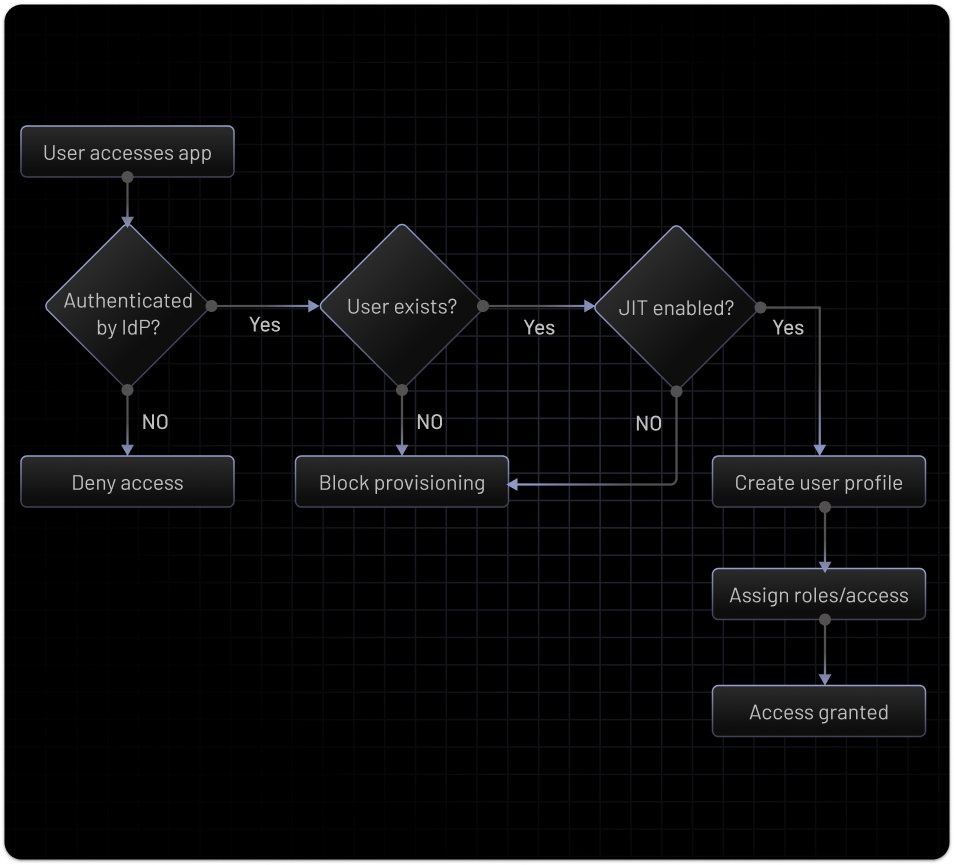
Multi-Tenancy Architecture
Easily onboard and manage multiple organizations within a single platform, each with its own independent settings, user directories, and role-based access controls.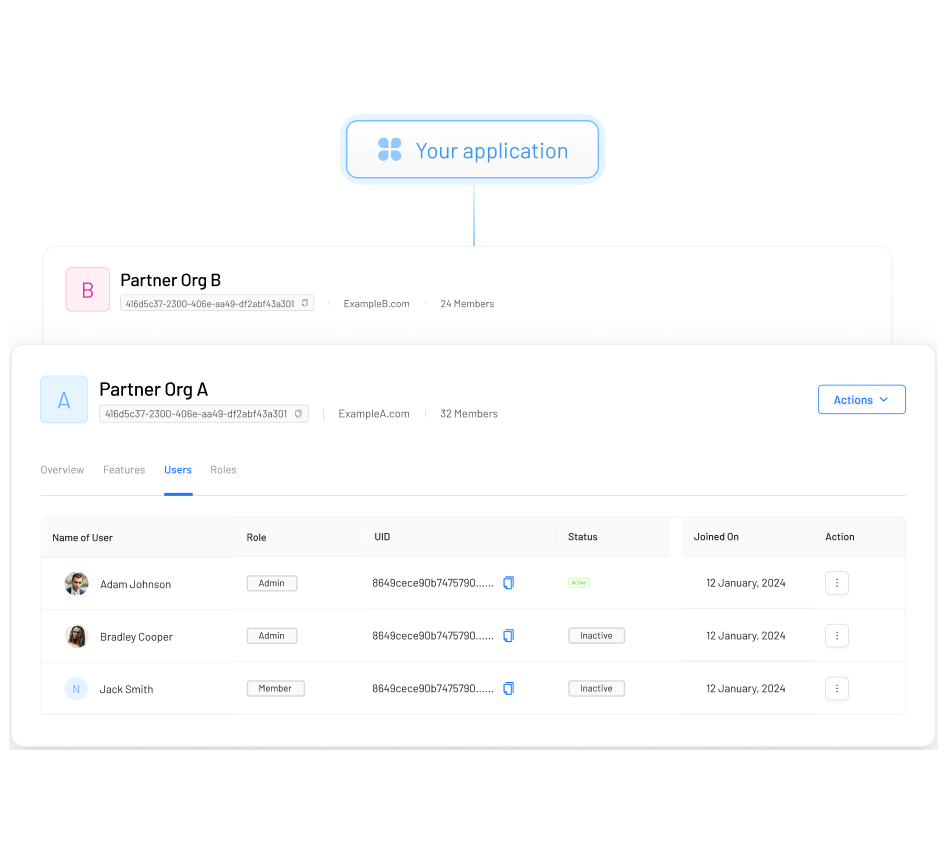
AI-Login Page Builder
Design fully branded login and registration pages tailored for your brand identity in minutes.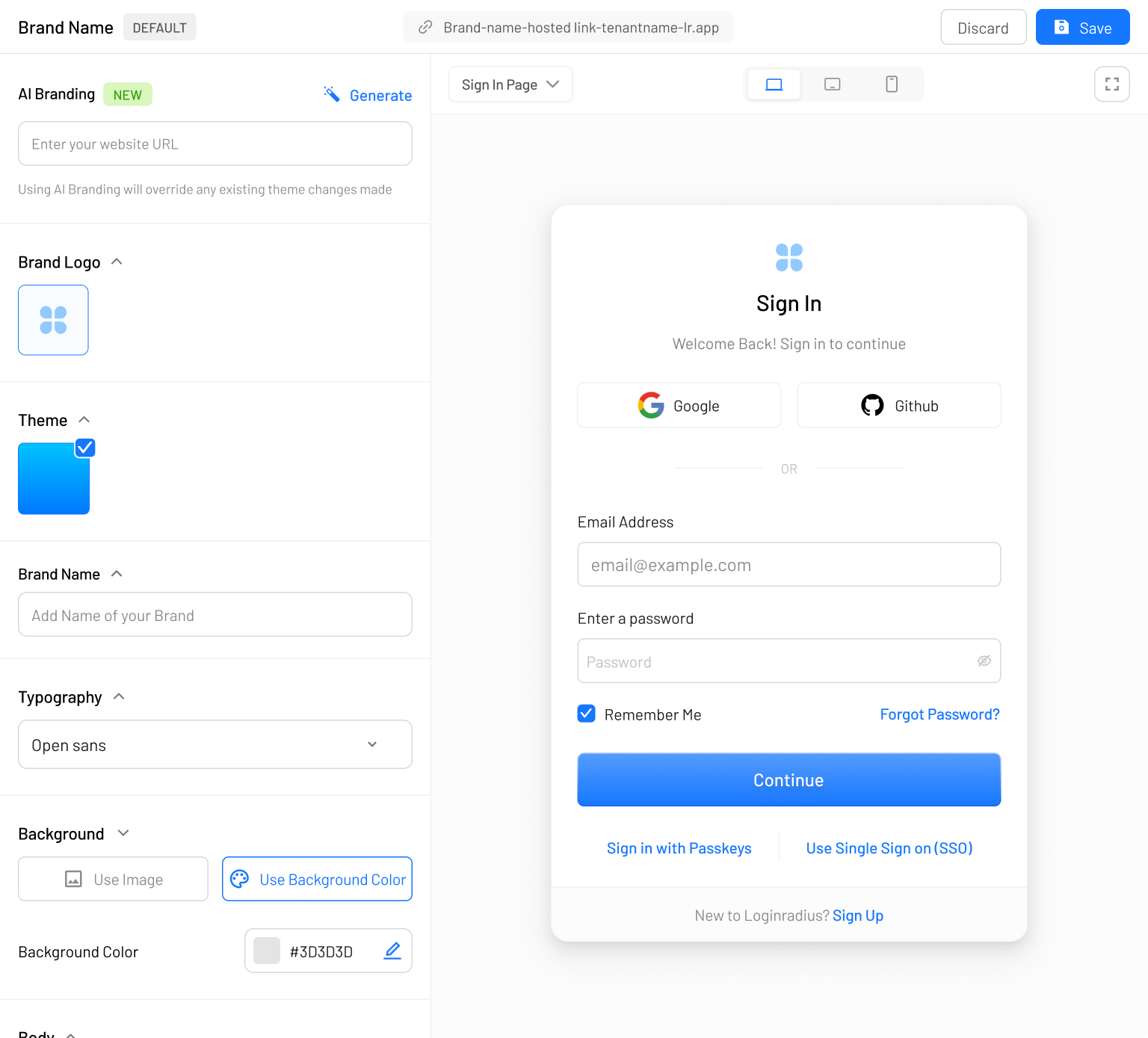
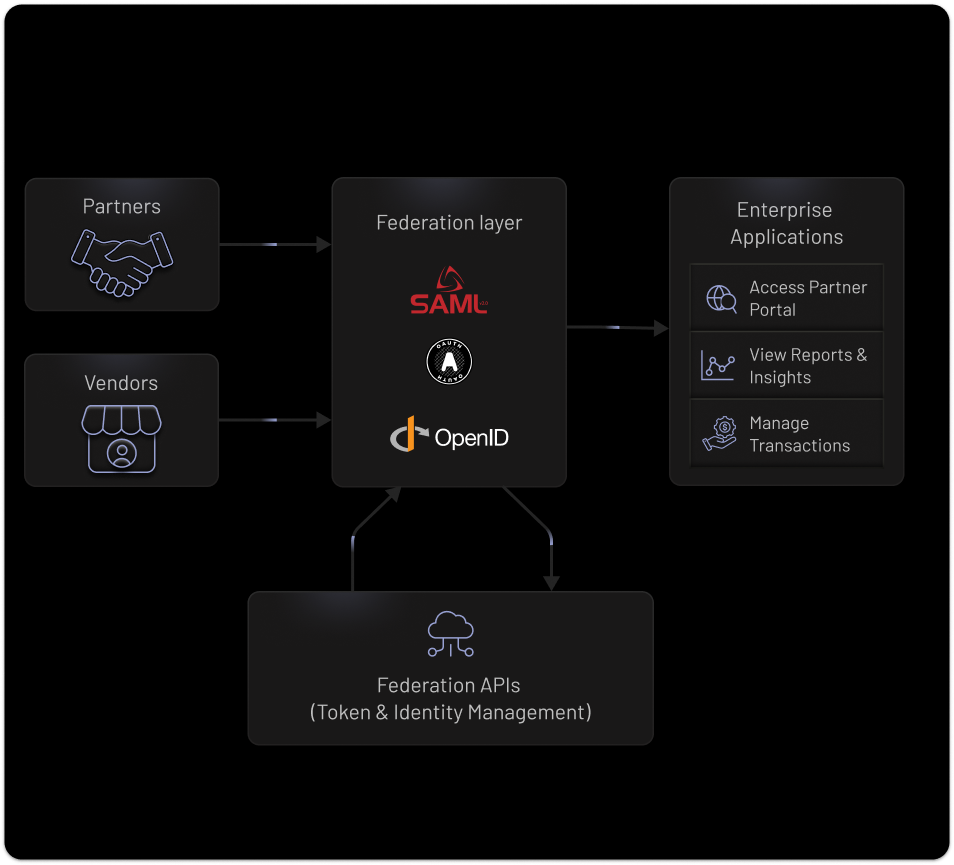
Federated Access Built for Organization Ecosystems
SSO Management
Integrate identity providers at the organization level and enable seamless access across your web portals and mobile apps. Deliver a consistent login experience with centralized session management and zero reauthentication friction.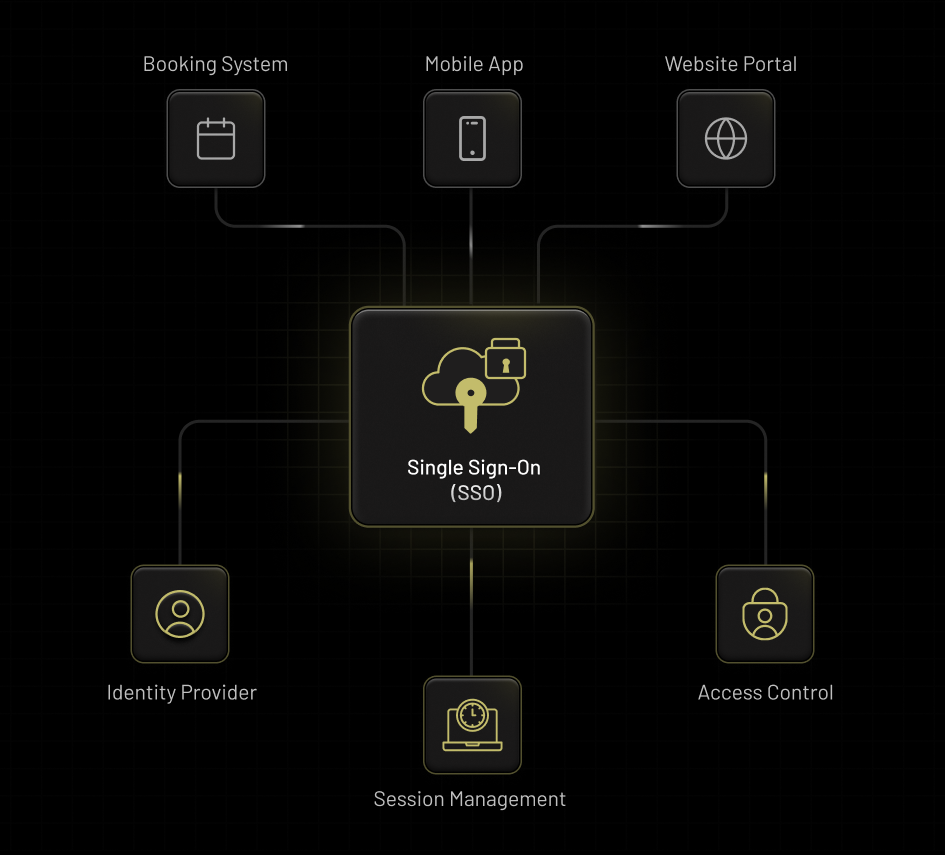
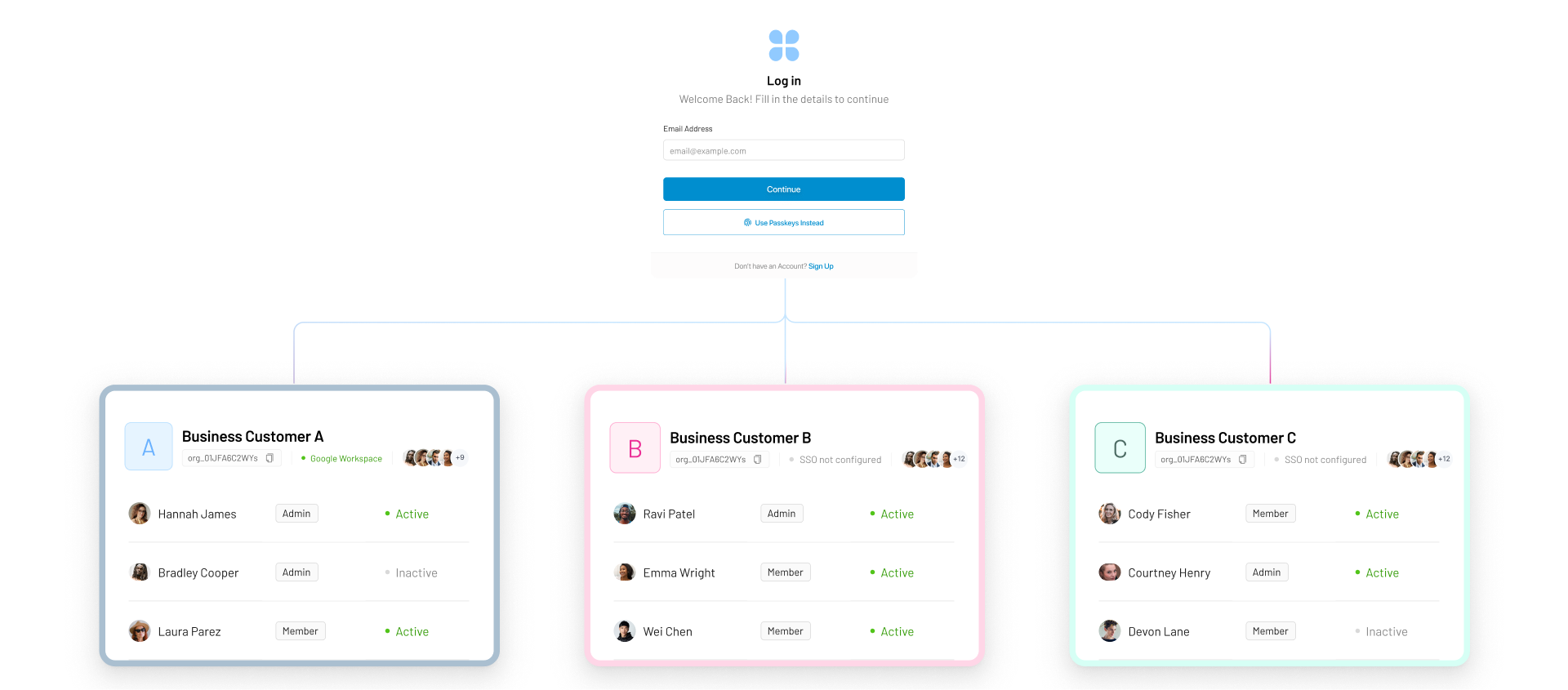
Self-Serve Organization Management Tailored for B2B Use Cases

Self-Serve Admin Portal
Org admins can manage their users, roles, and settings through a dedicated interface—no engineering effort required.
Delegated Admin Control
Assign admin privileges within each organization to enable secure, role-based management of their own users and access.
Automated User Sync (with SCIM)
Sync users and roles automatically across systems with SCIM to reduce manual updates and streamline organization management.
Fine-Grained Access Control (FGA)
Define precise access rules at the user, role, or resource level to enforce least-privilege access across organizations.Enterprise-Grade Security for Every Login, Role, and Action Across Organizations
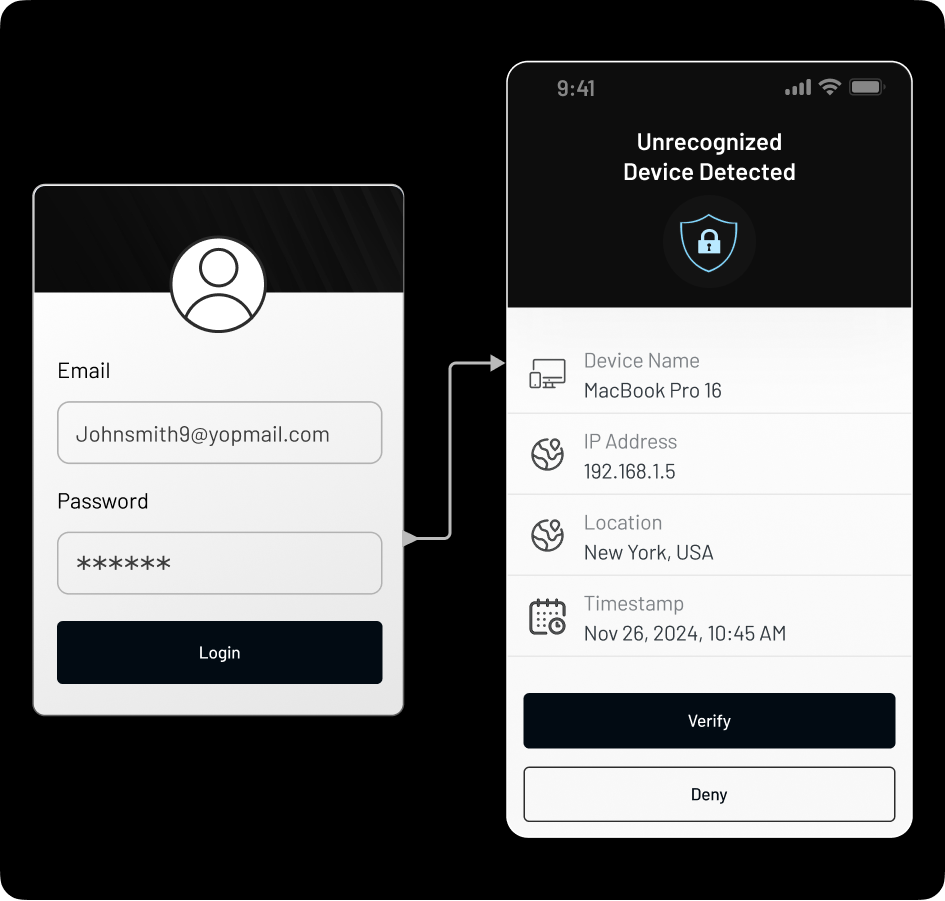
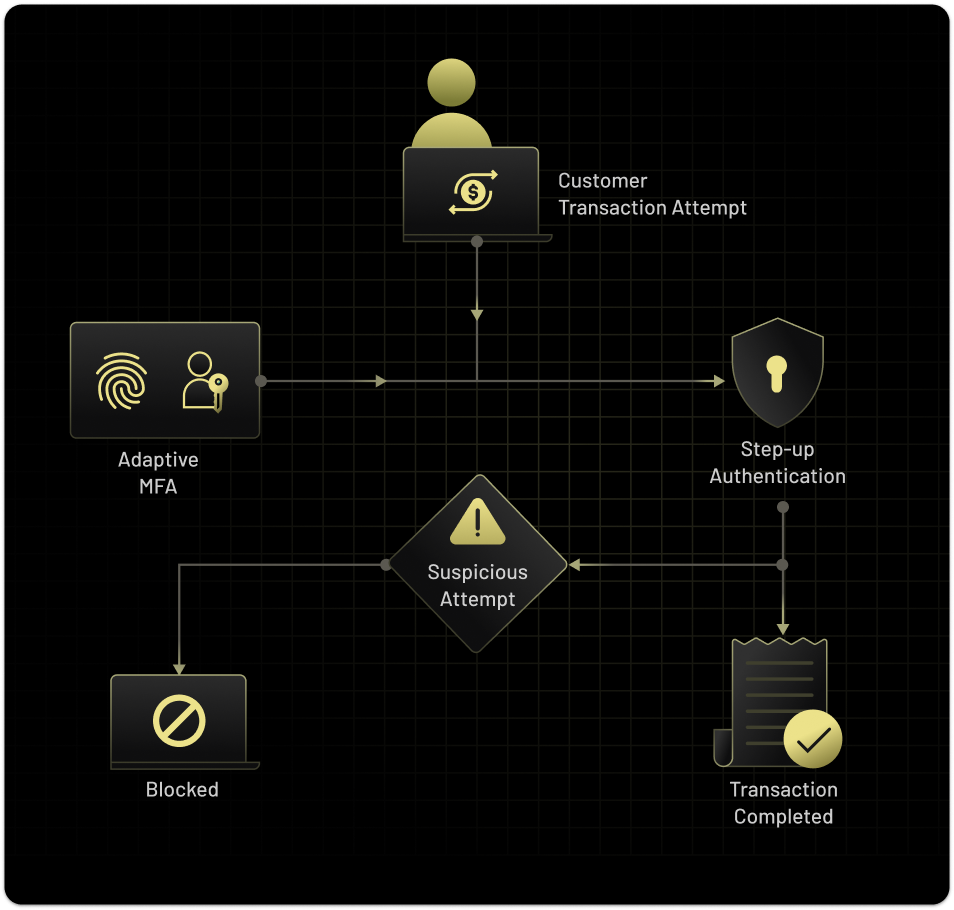
Risk-Based Adaptive Authentication
Implement intelligent, risk-based authentication that evaluates contextual factors, like device, location, and login patterns. Automatically enforce additional verification when suspicious activity is detected.Step-Up Authentication for High-Risk Scenarios
Strengthen security by mandating additional authentication steps for high-risk actions, such as accessing sensitive data or making critical system changes, ensuring the right users have the right level of access.Advanced Attack Protection
Protect organization accounts with automated defenses against common threats, such as bot attacks, brute-force attacks, and the use of breached or compromised passwords.Launch Faster with Pre-Certified Compliance Tools
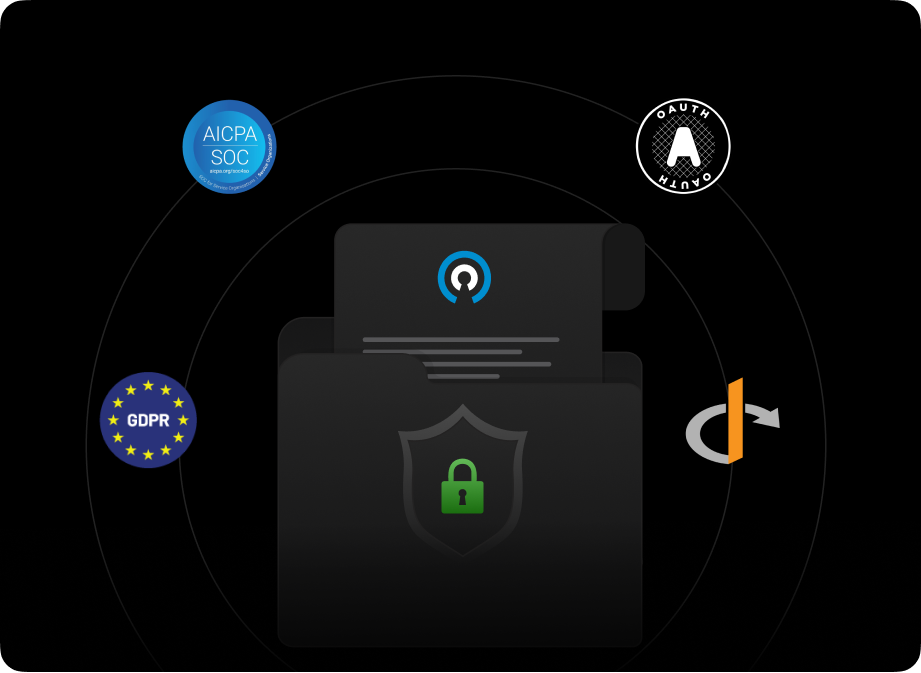
Compliance and Certifications
Achieve compliance with global standards, including SOC 2 Type II and GDPR, with built-in tools to protect customer data, enforce privacy standards, and meet global security requirements.Industry Standard Protocols
Leverage OAuth 2.0 and OpenID Connect for robust authentication workflows. Ensure interoperability and encryption for seamless and secure app connection.From API to Production—Auth That Just Ships!

Ready-to-Use SDKs
Speed up integration with SDKs available for major programming languages.
APIs for Seamless Integration
Easily embed authentication, user provisioning, and access management into your organization's ecosystem with flexible APIs