IBM Security Verify vs Cyber Ark Identity
Which One Is A Better Workforce IAM?
Read on to find out what they reveal:
- IBM Security Verify's Integration with IBM Ecosystem & Customization makes them a fan favorite.
- Cyber Ark Identity offers Deepest PAM Specialization.
- IBM Security Verify suits best for Large Enterprise, whereas Cyber Ark Identity has target audience in Enterprise.( Link )
Industry Analysts pick IBM Security Verify over Cyber Ark Identity
By the way, if you are looking for a CIAM platform, do explore LoginRadius, which has been recognized as an overall leader by Kupingercole, ahead of IBM Security Verify!
Your Peers pick Cyber Ark Identity over IBM Security Verify
ProsStrong compliance postureCentralized IGAdeep external integrations
ConsComplex initial setup and coding
ProsIntegration with M365SecurityIdentity Governance and SSO
ConsExpensive and external integration issues
When we were looking for an customer identity management platform, we tried a lot of big companies. Of which some were too expensive, and some were not feature-rich enough. We needed something that was as powerful as it was cost-effective. That’s when we found LoginRadius, and it was kind of exactly that right fit—easy to use, feature-rich, and had reasonable pricing.

Why Organizations Choose LoginRadius for CIAM

Purpose-built CIAM

Expert Support - NOT Outsourced!

Developer-Supported Deployment

Flexible Partnership
We believe that the best CIAM platform is one that is purpose-built for your use cases and can help your developers go-to market quickly. See for yourself.
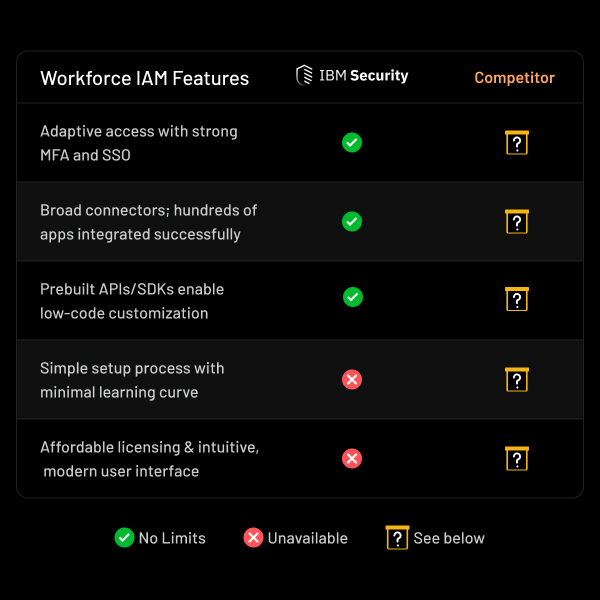
Feature-by-Feature Comparison
Category
Parameter