Akamai Identity Cloud, previously known as Janrain, was an early player in customer identity and access management. For years, it helped large consumer brands centralize authentication, manage user profiles, and support social login at scale. Its tight association with Akamai’s broader edge and security ecosystem has also made it appealing for organizations already invested in Akamai infrastructure.
However, CIAM requirements have evolved significantly. What worked a decade ago for basic login and profile storage is no longer sufficient for today’s environments. Modern applications demand passwordless authentication, adaptive security, real-time analytics, and flexible orchestration across multiple brands, regions, and business models.
Many teams now see Akamai Identity Cloud as a legacy CIAM platform nearing its practical limits. Common challenges include rigid policy engines, limited native passwordless and MFA capabilities, complex implementations, and long timelines for customization or migration. As a result, organizations evaluating long-term identity strategies are increasingly exploring modern CIAM alternatives built specifically for growth, security, and developer velocity.
Evaluation Criteria: What Makes a Great CIAM Platform
Before comparing alternatives, it’s important to define what “good” looks like in a modern CIAM solution. From our experience working with global consumer brands, B2B SaaS companies, and regulated industries, five dimensions consistently matter most.
Use Case Fit: CIAM vs Workforce vs B2B Identity
Not all identity platforms are designed for the same job. Workforce IAM tools prioritize employee access and internal controls, while CIAM platforms must handle millions of external users, unpredictable traffic spikes, and frictionless onboarding. Increasingly, organizations also need B2B and partner identity support, including tenant isolation, delegated administration, and account hierarchies.
A strong CIAM platform should support pure B2C, B2B, or hybrid use cases without forcing architectural workarounds.
Security & User Experience
Security can no longer come at the expense of UX. Modern CIAM platforms must offer built-in MFA depth, including push-based authentication, FIDO2 passkeys, and adaptive risk-based controls. Passwordless is no longer experimental, it’s becoming table stakes.
Equally important is the ability to apply security contextually, reducing friction for trusted users while escalating protection when risk signals change.
Architecture & Scalability
CIAM platforms must be cloud-native, highly available, and proven at scale. This includes multi-tenant architecture, regional deployments, strong SLAs, and predictable performance during peak traffic events such as product launches or seasonal spikes.
Legacy architectures often struggle here, especially when customization and orchestration are layered on top.
Data Residency & Compliance
Customer identity data is regulated data. Support for regional hosting, clear data residency controls, and compliance with frameworks like GDPR, CCPA, HIPAA, and SOC 2 is critical, especially for global brands and regulated industries.
Developer Experience & Migration Effort
CIAM implementations live or die by developer adoption. Clear APIs, SDKs, modern documentation, sandbox environments, and migration tooling all reduce time to value. Platforms that require heavy professional services for basic changes often slow teams down over time.
Top 9 Akamai Identity Cloud Alternatives to Consider in 2026
Below are some of the most commonly evaluated alternatives when teams reassess Akamai Identity Cloud.
1. LoginRadius
LoginRadius is a CIAM platform designed specifically for high-volume B2C, B2B SaaS, and public-sector identity, not adapted from workforce IAM or CDN tooling. Its design prioritizes consumer-scale traffic, identity-specific security controls, flexible UX orchestration, and global deployment without custom engineering overhead.
Where LoginRadius Works Especially Well
CIAM-native architecture: LoginRadius is built for customer identity at scale, with multi-region cloud hosting, high-availability SLAs, geo-isolated tenancy options, and native multi-tenant organization support. These capabilities are foundational, not layered on through custom services.
Rapid deployment without Lambda-style dependencies: Teams implement authentication, MFA, social login, progressive profiling, passkeys, and branded login experiences without writing event-trigger code or managing brittle customization pipelines.
Broad authentication coverage out of the box: Supports passwords, OTP, magic links, WebAuthn passkeys, passwordless flows, social login, adaptive MFA, and enterprise federation through unified APIs and configuration.
Modern CIAM security stack: Breached password detection, anomaly scoring, bot mitigation, IP velocity checks, and DDoS protection are native CIAM controls rather than inherited indirectly from infrastructure layers.
Low-/no-code identity orchestration: Hosted templates, journey builders, conditional workflows, and theming allow product and CX teams to iterate on identity flows without creating engineering backlogs.
Ideal For
-
Consumer brands requiring elastic global scale (retail, media, gaming)
-
B2B SaaS platforms needing multi-tenant identity and delegated admin
-
Public-sector and regulated organizations with data residency mandates
-
Teams frequently iterating on signup, login, and verification journeys
2. Auth0 (Okta Customer Identity Cloud)
Auth0 is a developer-oriented CIAM platform commonly evaluated by teams outgrowing the customization limits of legacy CIAM or cloud-native IAM tools.
Where Auth0 Performs Well
-
Developer-first extensibility: Rules, Actions, hooks, and SDKs provide engineers deep control over tokens, claims, and authentication logic.
-
Large integration ecosystem: A broad marketplace of connectors for analytics, fraud prevention, marketing platforms, and enterprise IdPs.
-
B2B SaaS enablement: Supports SAML, OIDC, RBAC, enterprise SSO, and tenant-level configuration.
CIAM Fit Analysis: Auth0 works best where engineering teams want maximum programmability. At very large consumer scale, cost growth, rate limits, and operational complexity can become friction points.
Ideal For
-
Early-stage to mid-market SaaS companies
-
Engineering-led organizations
-
Products with heavy third-party integrations
Trade-Offs
-
Pricing scales aggressively with MAUs and extensibility usage
-
Rate limits can affect high-volume consumer traffic
-
Long-term CIAM logic ownership stays with engineering
3. Microsoft Entra External ID (Azure AD B2C)
Microsoft Entra External ID is often considered by organizations already standardized on Azure infrastructure and Microsoft security tooling.
Where Azure AD B2C Performs Well
-
Microsoft ecosystem alignment: Native integration with Azure services, Entra ID, and Microsoft security controls.
-
Baseline CIAM coverage: Supports customer authentication, social login, and federation for straightforward use cases.
CIAM Fit Analysis : Originally derived from workforce IAM concepts, Azure AD B2C often struggles with UX flexibility and rapid iteration needed for consumer-facing applications.
Ideal For
-
Azure-first organizations
-
Enterprises with existing Entra investments
-
Low-variation CIAM requirements
Trade-Offs
-
Complex custom policy management
-
Limited consumer-grade UX control
-
Identity changes often require IT-heavy workflows
4. 1Kosmos
1Kosmos is an identity platform focused primarily on passwordless authentication and identity verification, with strong roots in workforce IAM and regulated access use cases. It is often evaluated by organizations looking to eliminate passwords through biometric-backed authentication and verified digital identity.
Where 1Kosmos Performs Well
-
Passwordless-first approach: 1Kosmos centers its platform around biometric authentication and cryptographic credentials, enabling organizations to remove passwords entirely for supported use cases.
-
Strong identity proofing and verification: The platform places heavy emphasis on identity assurance, including identity verification workflows designed for regulated industries and high-trust access scenarios.
-
Compliance-oriented positioning: 1Kosmos is frequently positioned for environments with strict identity assurance requirements, such as financial services or regulated workforce access.
CIAM Fit Analysis : While 1Kosmos excels in passwordless and identity verification, it is not a CIAM-native platform in the traditional consumer-scale sense. It lacks many of the UX orchestration, multi-tenant customer identity, and large-scale consumer journey management capabilities required for modern B2C and B2B CIAM deployments.
Ideal For
-
Organizations prioritizing passwordless workforce access
-
Regulated environments requiring strong identity verification
-
High-assurance authentication use cases
Trade-Offs
-
Limited CIAM-native features for large-scale consumer identity
-
Less flexibility in customer journey orchestration
-
Not optimized for high-volume B2C or B2B SaaS identity scenarios
5. Amazon Cognito
Amazon Cognito is frequently evaluated by teams operating entirely within AWS environments.
Where Cognito Performs Well
-
Native AWS integration: Tight coupling with AWS services and IAM policies.
-
Cost-effective at small scale: At low to moderate usage, Cognito can be economical.
CIAM Fit Analysis : Cognito is infrastructure-first, not CIAM-first. Advanced authentication, UX control, and orchestration typically require Lambda triggers and custom engineering.
Ideal For
-
AWS-centric development teams
-
Simple authentication needs
-
Infrastructure-driven identity strategies
Trade-Offs
-
Heavy reliance on custom code
-
Limited UX customization
-
Weak support for B2B and multi-tenant CIAM
6. Ping Identity
Ping Identity targets large enterprises needing both workforce IAM and CIAM capabilities.
Where Ping Performs Well
-
Strong standards support: Mature SAML, OAuth, and federation capabilities.
-
Hybrid deployment options: Supports complex enterprise and regulated environments.
CIAM Fit Analysis : Ping is powerful but heavy. CIAM implementations often require professional services and long deployment cycles.
Ideal For
-
Large enterprises
-
Hybrid IAM environments
-
Organizations with existing Ping investments
Trade-Offs
-
High implementation complexity
-
Slower iteration on customer UX
-
Significant services dependency
7. ForgeRock (now part of Ping)
ForgeRock historically focused on customizable identity for large-scale deployments.
Where ForgeRock Performs Well
- Highly configurable identity stack: Strong control over identity flows and data models.
CIAM Fit Analysis : While powerful, ForgeRock is resource-intensive and best suited for organizations with dedicated IAM teams.
Ideal For
-
Governments and large financial institutions
-
Highly customized identity environments
Trade-Offs
-
Long deployment timelines
-
Heavy operational overhead
-
High total cost of ownership
8. OneLogin Customer Identity
OneLogin extends workforce IAM concepts into customer identity scenarios.
Where OneLogin Performs Well
- Simplified IAM administration: Familiar tooling for teams already using OneLogin internally.
CIAM Fit Analysis : OneLogin lacks many advanced CIAM-native capabilities required for modern consumer experiences.
Ideal For
-
Small customer portals
-
Organizations already using OneLogin
Trade-Offs
-
Limited CIAM depth
-
Weak passwordless and orchestration support
-
Not designed for massive consumer scale
9. Keycloak (Open Source)
Keycloak is an open-source identity platform often self-hosted or managed via third parties.
Where Keycloak Performs Well
- Open-source flexibility: Full control over identity infrastructure and customization.
CIAM Fit Analysis : Keycloak shifts identity responsibility entirely to internal teams, which can become costly and risky at scale.
Ideal For
-
Teams with strong IAM expertise
-
On-prem or sovereign deployments
Trade-Offs
-
No native SLAs
-
Significant maintenance burden
-
Limited CIAM UX tooling out of the box
Why People Switch From Akamai Identity Cloud to LoginRadius
Organizations that move away from Akamai Identity Cloud often cite a common set of challenges that directly impact their roadmap and customer experience.
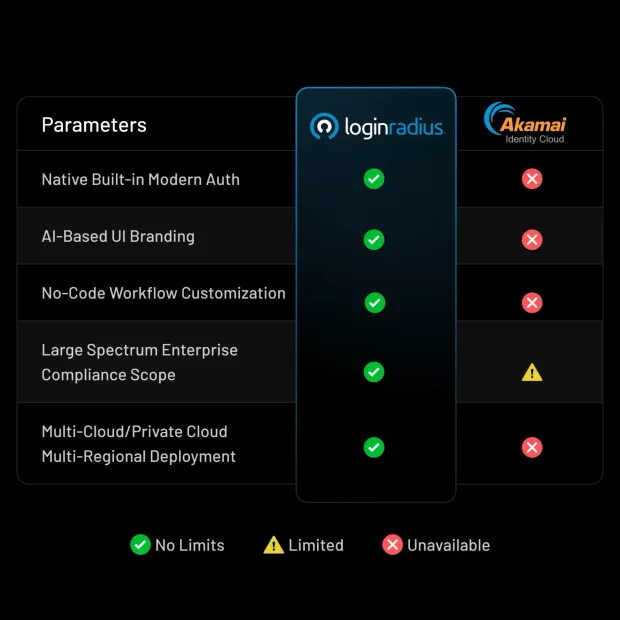
Modern Authentication & Passwordless
Akamai Identity Cloud lacks native support for modern passwordless authentication and advanced MFA options. Teams frequently rely on custom integrations or external tools to meet evolving security requirements.
LoginRadius provides FIDO2 passkeys, push-based MFA, adaptive authentication, and risk-based controls as first-class features, allowing organizations to modernize security without re-architecting their identity stack.
Branding & Customization Limitations
Janrain’s legacy UI and limited branding controls make it difficult to deliver consistent, branded login experiences across products and regions.
LoginRadius’ headless architecture gives teams full control, whether through hosted pages, fully custom UIs, or white-label authenticator apps, without sacrificing security or compliance.
Rigid Orchestration & Multi-Tenancy
Akamai Identity Cloud’s policy engine can be inflexible when adapting flows across brands, regions, or business models.
LoginRadius enables no-code orchestration, event-driven webhooks, and native multi-tenancy, making it easier to support B2C, B2B, and partner identity use cases from a single platform.
Analytics, Visibility & Compliance
Limited real-time visibility makes it harder to detect anomalies or optimize user journeys on legacy platforms.
With LoginRadius, teams gain real-time identity analytics, granular audit logs, and built-in compliance with GDPR, CCPA, HIPAA, and SOC 2 Type II, without bolted-on tooling.
LoginRadius vs Akamai Identity Cloud: Feature Comparison
| Capability | LoginRadius | Akamai Identity Cloud |
|---|---|---|
| CIAM focus | Purpose-built CIAM platform for B2C, B2B, and partner identity | Legacy CIAM platform originating from Janrain |
| Passwordless authentication | Native FIDO2 passkeys and passwordless flows | No native FIDO2 or modern passwordless support |
| MFA options | Push MFA, TOTP, SMS, email, adaptive MFA | Limited MFA; often requires custom or third-party integrations |
| Adaptive / risk-based authentication | Built-in adaptive and risk-based policies | Limited contextual authentication capabilities |
| Architecture | Cloud-native, headless CIAM with flexible orchestration | Legacy architecture with rigid policy framework |
| Orchestration & workflows | No-code orchestration, event-driven webhooks, custom journeys | Policy changes often require complex configuration |
| Multi-tenancy (B2B / partners) | Native multi-tenant support with tenant isolation | Limited and difficult to extend for B2B use cases |
| Branding & UI customization | Fully headless, hosted pages, custom UIs, white-label options | Restricted branding and UI customization |
| Identity analytics & visibility | Real-time analytics, anomaly detection, detailed audit logs | Limited real-time visibility and reporting |
| Compliance & certifications | GDPR, CCPA, HIPAA, SOC 2 Type II supported | Compliance depends on broader Akamai ecosystem |
| Migration tooling | Purpose-built migration accelerators and expert support | Migrations often lengthy and services-heavy |
| Developer experience | Modern APIs, SDKs, clear documentation, fast time-to-value | Steeper learning curve and heavier implementation effort |
Conclusion
Akamai Identity Cloud played an important role in the early days of CIAM, but today’s requirements have outgrown its legacy foundations. As customer expectations rise and security threats evolve, organizations need identity platforms that are flexible, passwordless-ready, and designed for scale from day one.
Modern CIAM platforms like LoginRadius, Auth0, and others reflect this shift, placing developer experience, adaptive security, and multi-tenant architecture at the core. For teams evaluating the next phase of their identity strategy, the right choice comes down to long-term fit, not just historical presence.
If your organization is struggling with complexity, customization limits, or slow innovation on Akamai Identity Cloud, it may be time to reassess. Shortlisting a modern CIAM platform built for growth can reduce friction today while future-proofing your identity stack for what comes next.
Explore how LoginRadius supports modern CIAM, B2B identity, and passwordless authentication or schedule a technical consultation to discuss migration paths from Akamai Identity Cloud.