1Kosmos BlockID has built a strong reputation around biometric-first, passwordless authentication, particularly in workforce and regulated identity environments. Its focus on high-assurance identity verification and phishing-resistant access makes it appealing for internal users, government use cases, and industries where identity proofing is tightly controlled.
However, as organizations expand into large-scale customer and partner experiences, many teams begin to question whether a workforce-oriented, biometric-heavy approach translates well to modern CIAM requirements. Customer identity introduces very different challenges, millions of users, diverse devices, peak traffic events, branding expectations, and a constant need to balance security with minimal friction.
For CIAM teams, common points of friction emerge around repeated PIN or OTP prompts, limited flexibility in authentication journeys, and feature depth that skews toward workforce biometrics rather than consumer-centric needs like social login, consent management, profile data control, and marketing integrations. As a result, many organizations start exploring alternatives to 1Kosmos BlockID that are purpose-built for scalable, customizable, and customer-first CIAM architectures.
Evaluation criteria: What makes a great CIAM platform
Not all identity platforms are designed for the same job. Many tools that work well for workforce IAM or high-assurance internal access struggle when applied to customer identity at scale. To fairly evaluate alternatives to 1Kosmos BlockID, it’s important to look at CIAM platforms through a customer-first lens.
Below are the core criteria we use when assessing a modern CIAM solution.
Use case fit: CIAM vs workforce IAM vs B2B/partner IAM
The first and the most critical question is whether a platform is truly built for CIAM. Workforce IAM platforms typically prioritize internal security controls, strict authentication policies, and smaller, known user populations. CIAM platforms, by contrast, must support millions of external users, unpredictable traffic spikes, and a wide range of authentication preferences.
For B2C and B2B CIAM use cases, such as consumer apps, SaaS customer portals, or partner ecosystems, the platform must handle multi-tenant identity models, delegated administration, and flexible onboarding flows. Tools that are overly optimized for workforce biometrics or internal identity proofing often introduce unnecessary friction when applied to these customer-facing scenarios.
Security and user experience balance
Security is non-negotiable in CIAM, but it cannot come at the expense of usability. Strong CIAM platforms support layered security controls, such as MFA, adaptive authentication, and phishing-resistant options while still allowing teams to tailor the experience based on risk, context, and user type.
Modern CIAM solutions also extend beyond a single authentication method. Support for social login, passwordless options like passkeys, and step-up authentication is essential for reducing friction during registration and login. The goal is not maximum security at all times, but the right level of security at the right moment in the user journey.
Architecture, scalability, and performance
CIAM platforms must be architected for internet-scale usage. That means cloud-native infrastructure, elastic scaling, and proven performance under peak traffic conditions, such as product launches, seasonal spikes, or viral growth.
Multi-tenant architecture is especially important for B2B and partner IAM scenarios, where each organization or customer may require isolated identity policies and data boundaries. Clear SLAs, resilience, and high availability are also critical, as authentication downtime directly impacts revenue and customer trust.
Data residency and compliance readiness
Customer identity data is subject to a growing list of privacy and regulatory requirements. A strong CIAM platform provides clear options for regional data hosting, supports compliance with regulations like GDPR and CCPA, and offers transparent data handling practices.
Unlike workforce IAM, CIAM often spans multiple geographies and customer segments. Platforms that lack flexible data residency options or require complex custom deployments can become a bottleneck for global growth.
Developer experience and implementation effort
Finally, CIAM platforms must be practical to implement and evolve. Clear APIs, SDKs, and documentation are table stakes, but modern teams also expect low-code or no-code tools that allow product and security teams to adjust authentication flows without heavy engineering effort.
Migration support is equally important. Organizations moving away from platforms like 1Kosmos BlockID often look for solutions that reduce rework, accelerate time-to-value, and allow iterative improvements to the login experience without repeated redevelopment cycles.
Top 7 1Kosmos BlockID Alternatives to Consider in 2026
Below are some of the most commonly evaluated alternatives when organizations reassess 1Kosmos BlockID for customer identity and access management (CIAM) use cases.
1. LoginRadius
LoginRadius is a CIAM platform designed specifically for high-scale B2C, B2B SaaS, and public-sector identity use cases. Unlike platforms rooted in workforce IAM or biometric-only authentication models, LoginRadius is designed to support consumer-scale traffic, flexible authentication journeys, and rapid iteration across diverse customer experiences.
Where LoginRadius Works Especially Well
CIAM-native architecture at internet scale : LoginRadius is purpose-built for customer identity, with cloud-native infrastructure that supports global deployments, regional data residency, multi-tenant organizations, and high-availability SLAs. These capabilities are foundational to the platform rather than retrofitted from workforce IAM or identity proofing systems.
Frictionless identity orchestration without custom code : Authentication journeys, including registration, login, MFA, step-up verification, and progressive profiling can be designed and updated visually using low- and no-code tools. Teams avoid repeated PIN or OTP friction by tailoring flows dynamically based on user context, risk, and device without engineering-heavy customization.
Broad CIAM feature coverage out of the box : LoginRadius supports a wide range of customer authentication methods, including passwords, OTP, magic links, passkeys (WebAuthn), passwordless flows, social login, adaptive MFA, and enterprise federation. Consent management, profile data governance, and marketing data integrations are native features rather than add-ons.
Modern CIAM security controls built for consumer traffic : Security features such as breached password detection, anomaly detection, bot mitigation, IP velocity checks, and DDoS protection are designed specifically for CIAM threat models. This allows teams to maintain strong security posture without introducing unnecessary friction for legitimate customers.
Branding and customization at scale
LoginRadius provides full control over hosted login experiences, theming, and UI customization, enabling organizations to align authentication flows with their brand identity across multiple products, regions, or customer segments.
Ideal For
-
Consumer-facing brands handling high-volume authentication traffic (retail, media, gaming)
-
B2B SaaS platforms requiring multi-tenant identity and delegated administration
-
Public-sector and regulated organizations with regional data residency needs
-
Teams optimizing signup and login conversion without sacrificing security
2. Ping Identity
Ping Identity is an enterprise IAM platform commonly evaluated by large organizations that need advanced federation, policy-driven access controls, and hybrid deployment options across workforce and customer identity use cases.
Where Ping Identity Performs Well
-
Strong federation and protocol support : Deep support for SAML, OAuth 2.0, OpenID Connect, and complex enterprise federation scenarios.
-
Hybrid and on-prem flexibility : Supports cloud, hybrid, and on-prem deployments for organizations with strict regulatory or infrastructure requirements.
-
Granular access policies : Advanced policy engines allow fine-grained authentication and authorization decisions based on attributes, context, and risk.
CIAM Fit Analysis : Ping Identity is powerful for enterprise IAM but is not CIAM-native by design. Customer identity use cases often require additional products, configuration, or professional services to achieve consumer-grade UX, branding, and journey orchestration. This can slow down iteration for teams focused on optimizing signup and login experiences at scale.
Ideal For
-
Large enterprises with existing Ping Identity deployments
-
Organizations requiring hybrid or on-prem IAM models
-
Complex partner and federation-heavy environments
Trade-Offs
-
Higher implementation and operational complexity for CIAM
-
Slower time-to-value for consumer-facing use cases
-
UX customization typically requires engineering effort
3. Microsoft Entra ID (External ID / Azure AD B2C)
Microsoft Entra External ID is commonly evaluated by organizations already standardized on Azure and Microsoft security tooling that want a basic CIAM capability without introducing a separate identity vendor.
Where Microsoft Entra External ID Performs Well
-
Microsoft ecosystem alignment : Native integration with Azure services, Entra ID, and Microsoft security controls.
-
Baseline CIAM functionality : Supports customer authentication, social login, and federation for relatively straightforward use cases.
-
Enterprise familiarity : Often easier to adopt for IT teams already managing Microsoft identity infrastructure.
CIAM Fit Analysis : Originally derived from workforce IAM concepts, Entra External ID can struggle with the UX flexibility and rapid iteration required for consumer-facing CIAM. Custom policies, complex configuration, and IT-driven workflows often make it difficult for product teams to quickly optimize signup and login journeys.
Ideal For
-
Azure-first organizations
-
Enterprises with existing Entra ID investments
-
CIAM use cases with low UX variation
Trade-Offs
-
Complex custom policy management
-
Limited consumer-grade UX customization
-
Identity changes often require IT-heavy workflows
4. Amazon Cognito
Amazon Cognito is a cloud-native identity service designed primarily for AWS-based applications. It is often evaluated by teams looking for a low-cost, infrastructure-aligned authentication solution.
Where Amazon Cognito Performs Well
-
Tight AWS integration : Native alignment with AWS services such as API Gateway, Lambda, and IAM.
-
Cost-efficient entry point : Attractive pricing for early-stage applications or low-complexity use cases.
-
Basic CIAM support : Provides user pools, federation, and MFA for standard authentication needs.
CIAM Fit Analysis : While Cognito works well for simple authentication, it lacks many CIAM-native capabilities required at scale. Customization, branding, and journey orchestration often require custom development, making it less suitable for teams focused on conversion optimization and rapid iteration.
Ideal For
-
AWS-native startups
-
Engineering teams building internal or simple customer apps
-
Cost-sensitive early-stage projects
Trade-Offs
-
Limited UX customization and branding
-
Weak support for complex CIAM journeys
-
Heavy reliance on custom code for advanced use cases
5. ForgeRock
ForgeRock is an enterprise IAM platform historically used for large-scale identity deployments across workforce and customer identity, particularly in complex or regulated environments.
Where ForgeRock Performs Well
-
Comprehensive IAM feature set : Strong coverage across authentication, authorization, identity governance, and federation.
-
Highly configurable architecture : Supports complex identity policies and custom deployment scenarios.
-
Enterprise and regulated market presence : Frequently used in telecom, finance, and government sectors.
CIAM Fit Analysis : ForgeRock can support CIAM at scale, but doing so often requires significant configuration, customization, and operational investment. For teams prioritizing speed, simplicity, and low-friction CIAM iteration, the platform’s complexity can become a barrier.
Ideal For
-
Large enterprises with complex IAM requirements
-
Regulated industries with custom policy needs
-
Organizations with dedicated IAM teams
Trade-Offs
-
High implementation and maintenance overhead
-
Slower time-to-value for CIAM initiatives
-
Requires specialized expertise to operate effectively
6. WSO2
WSO2 is an open-source–driven IAM platform often evaluated by organizations seeking maximum architectural control and deployment flexibility.
Where WSO2 Performs Well
-
Open-source flexibility : Enables deep customization and self-hosted deployments.
-
Protocol and standards support : Strong support for OAuth, OIDC, SAML, and API security.
-
Cost control for self-managed environments : Attractive for teams that prefer infrastructure ownership.
CIAM Fit Analysis : WSO2 provides building blocks for CIAM rather than a fully productized CIAM experience. Organizations must invest engineering effort to design, deploy, and maintain consumer-grade identity journeys, which can slow iteration and increase long-term operational cost.
Ideal For
-
Engineering-led organizations
-
Teams requiring self-hosted or highly customized IAM
-
Organizations with strong internal IAM expertise
Trade-Offs
-
Significant setup and operational complexity
-
Limited out-of-the-box CIAM UX
-
Ongoing maintenance responsibility remains internal
7. Transmit Security
Transmit Security is a risk- and fraud-focused identity platform emphasizing continuous authentication, behavioral biometrics, and adaptive security controls.
Where Transmit Security Performs Well
-
Advanced fraud and risk detection : Strong behavioral analytics and continuous authentication capabilities.
-
Phishing-resistant authentication : Emphasis on passwordless and risk-based access.
-
Layered security approach : Designed to reduce account takeover and fraud.
CIAM Fit Analysis : Transmit Security excels as a security layer but is not a standalone CIAM solution. Core CIAM functions such as user lifecycle management, multi-tenant identity, and flexible journey orchestration often require pairing with another CIAM platform.
Ideal For
-
Organizations prioritizing fraud reduction
-
Financial services and high-risk industries
-
Teams augmenting an existing CIAM stack
Trade-Offs
-
Not a standalone CIAM platform
-
Requires integration with another identity system
-
Less focus on end-to-end customer identity management
Why People Switch From 1Kosmos BlockID to LoginRadius
Organizations that move away from 1Kosmos BlockID often cite a consistent set of challenges that emerge as customer identity programs mature and scale beyond workforce-style authentication.
Rigid Authentication Flows & User Friction
1Kosmos BlockID relies heavily on PIN- and OTP-driven authentication patterns that can feel repetitive for returning users. These flows are optimized for high-assurance access rather than low-friction, high-frequency customer logins.
LoginRadius enables adaptive, context-aware authentication with visual, no-code orchestration. Teams can eliminate unnecessary prompts and tailor login flows dynamically based on user behavior, device, and risk, without engineering rework.
Limited CIAM Feature Breadth
1Kosmos BlockID’s capabilities are primarily centered on biometric authentication and identity assurance, with less emphasis on consumer-centric CIAM features such as social login, consent management, profile data control, and marketing integrations.
LoginRadius delivers a comprehensive CIAM feature set out of the box, including social authentication, passkeys, consent and preference management, rich customer profiles, and seamless integration with downstream marketing and analytics systems.
Branding & Customization Constraints
Customization options in 1Kosmos BlockID are frequently cited as limited, especially when organizations need to support multiple brands, regions, or differentiated customer experiences.
LoginRadius provides full control over branding and UX through hosted pages, headless APIs, and customizable UI components. Teams can maintain consistent brand experiences across products and geographies without custom service engagements.
Cost Efficiency & Time-to-Value
Customer feedback often indicates that 1Kosmos BlockID’s pricing and complexity do not scale efficiently for consumer CIAM use cases, particularly when additional tooling is required to fill feature gaps.
LoginRadius is designed for fast deployment and high ROI at scale. Its CIAM-first architecture reduces implementation effort, lowers ongoing operational costs, and supports growth without constant reconfiguration.
Scale & Performance for Consumer Identity
The architecture behind 1Kosmos BlockID, while effective for controlled access environments, can become overly complex when applied to unpredictable, high-volume consumer traffic.
LoginRadius is built for internet-scale CIAM, supporting billions of identities with cloud-native infrastructure, multi-region deployments, and strong availability guarantees, ensuring consistent performance during traffic spikes and growth phases.
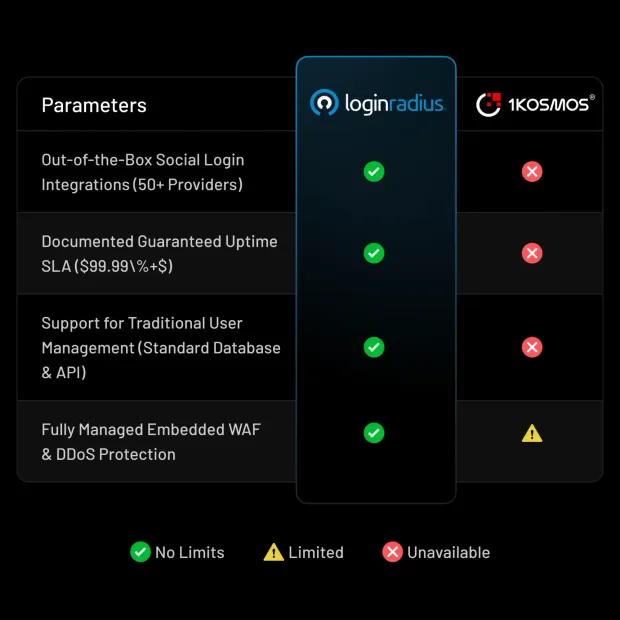
LoginRadius vs 1Kosmos BlockID: Key Differences
| Category | LoginRadius | 1Kosmos BlockID |
|---|---|---|
| CIAM-native multi-tenant support | Strong support for multi-tenant orgs and geo-isolated deployments | Focused more on identity verification and workforce use cases |
| Guaranteed uptime SLA (99.99%+) | Supported | Not publicly documented |
| Scalability & performance (RPS / global scale) | Designed for high-volume consumer workloads | Limited consumer traffic optimization |
| Social login breadth | Broad, built-in support | Limited (secondary factor only) |
| Passwordless & modern authentication | OTP, magic link, passkeys (FIDO2), progressive flows | Biometrics + PIN/OTP support; limited modern CIAM UX |
| MFA options | Push, TOTP, passkeys, adaptive MFA | Push and TOTP supported; PIN as factor |
| Risk-based authentication | Configurable risk policies, browser/device risk scoring | Limited explicit risk priority features |
| Visual identity orchestration | Drag-and-drop flows, pre-built templates | Not supported (workflow customization limited) |
| Federation & SSO | Broad SSO connectors, cross-device SSO | Supported, though more enterprise-centric |
| Security & bot protection | Managed WAF, DDoS, brute-force/bot mitigation | Limited native bot/risk controls |
| Developer tooling | Rich SDKs, CLI, integrations, low-code tools | API/SDK available but CIAM tooling limited |
| Experience layer (UX customization) | Localized UI, theme builder, headless support | Basic customization; less CIAM focus |
Conclusion
1Kosmos BlockID delivers strong value in passwordless and identity assurance scenarios, particularly in workforce and regulated access environments. However, as organizations expand into large-scale customer, B2B, and partner identity use cases, its biometric-centric and workforce-leaning architecture can introduce friction, limit flexibility, and increase operational complexity.
Modern CIAM requires more than strong authentication alone. Teams increasingly need adaptive journeys, broad authentication options, multi-tenant identity models, branding control, and the ability to iterate quickly as customer expectations evolve. Platforms that are not CIAM-native often struggle to balance security with usability at consumer scale.
LoginRadius is designed specifically to meet these needs. With a CIAM-first architecture, no-code identity orchestration, comprehensive customer identity features, and proven performance at massive scale, it offers a pragmatic alternative for organizations that have outgrown workforce-oriented or biometric-only identity solutions. For teams reassessing 1Kosmos BlockID, LoginRadius is often shortlisted as a platform better aligned with long-term CIAM strategy, growth, and customer experience goals.
If you’re actively evaluating alternatives to 1Kosmos BlockID, a side-by-side comparison can help clarify which platform best fits your CIAM requirements.
You can start by reviewing the detailed LoginRadius vs 1Kosmos BlockID comparison, or connect with our team to discuss how a CIAM-first approach can support your specific B2C or B2B identity use cases as you scale.