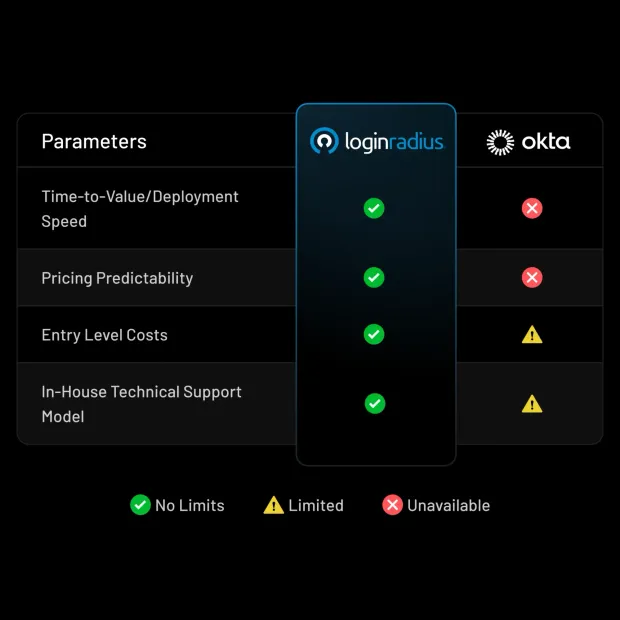
Okta Customer Identity Cloud is widely recognized for its developer-friendly APIs, broad integration ecosystem, and strong standards support. For many teams, especially engineering-led SaaS organizations, Okta CIC has served as a fast way to implement authentication, federation, and basic CIAM capabilities.
However, as customer identity requirements mature, many organizations begin to experience trade-offs that are harder to ignore. CIAM initiatives today must support millions of users, complex B2B and partner models, regional data residency requirements, and modern passwordless experiences, all while keeping costs predictable.
For these teams, Okta CIC’s usage-based pricing, reliance on extensibility for common workflows, and increasing operational overhead often become blockers rather than accelerators. This is why security and product leaders increasingly evaluate modern CIAM alternatives designed specifically for customer and B2B identity at scale.
Evaluation Criteria: What Makes a Great CIAM Platform
Before comparing vendors, it’s important to define what actually matters in a CIAM platform.
Use case fit: CIAM vs workforce vs B2B identity
CIAM platforms must handle external users, not employees. That means unpredictable traffic, consumer-grade UX expectations, and support for B2B use cases like multi-tenant organizations, delegated administration, and partner identity. Platforms adapted from workforce IAM often struggle here.
Security and user experience
Modern CIAM security goes beyond passwords. MFA depth, passkeys, adaptive and risk-based authentication, and bot protection must coexist with low-friction user journeys. Strong CIAM platforms apply security contextually without degrading conversion.
Architecture and scalability
CIAM platforms must be cloud-native, globally distributed, and proven under peak consumer loads. Multi-tenant architecture, high availability SLAs, and predictable performance are non-negotiable for customer-facing systems.
Data residency and compliance
Customer identity data is regulated data. Support for regional hosting, tenant isolation, and compliance with frameworks like GDPR, CCPA, HIPAA, and SOC 2 is critical, especially for global and regulated organizations.
Developer experience and time-to-value
Identity projects fail when they stall engineering teams. Clear APIs, SDKs, documentation, migration tooling, and low-code configuration all directly impact implementation speed and long-term maintainability.
Top Okta Customer Identity Cloud Alternatives
Below are the leading alternatives teams commonly evaluate when moving away from Okta Customer Identity Cloud.
1. LoginRadius
LoginRadius is a CIAM platform designed specifically for high-volume B2C, B2B SaaS, and regulated enterprise identity use cases. Unlike Okta Customer Identity Cloud (CIC), which evolved from a developer-centric extensibility model with usage-based pricing, LoginRadius is purpose-built as a fully managed customer identity platform designed for predictable scale, enterprise security, and long-term CIAM flexibility.
While Okta CIC works well for teams that want deep programmatic control through Actions, Hooks, and custom pipelines, LoginRadius is designed for organizations that need strong security posture, compliance readiness, and fast time-to-value without accumulating long-term engineering and operational overhead as identity requirements grow.
Where LoginRadius Works Especially Well
CIAM-native, enterprise-ready architecture: LoginRadius is built from the ground up for customer and partner identity at scale. The platform supports multi-region cloud deployments, geo-isolated data residency, SLA-backed availability, and native multi-tenant organization models. These capabilities are foundational and managed end-to-end by LoginRadius. With Okta CIC, many of these requirements are achievable, but often require careful tenant design, custom extensibility, and ongoing operational tuning as scale increases.
Enterprise MFA and passwordless authentication: LoginRadius provides native support for push-based MFA, adaptive risk-based authentication, passkeys (FIDO2/WebAuthn), OTPs, magic links, and step-up authentication flows out of the box. Okta CIC supports a wide range of authentication methods as well, but advanced adaptive controls, passwordless journeys, and contextual policies frequently rely on Actions and additional configuration, increasing implementation complexity and long-term maintenance effort.
Predictable pricing and cost control at scale: LoginRadius offers transparent, tiered pricing designed for consumer and B2B identity growth without usage-driven surprises. Many teams re-evaluating Okta CIC cite MAU-based pricing, feature add-ons, and extensibility costs as sources of budget uncertainty as applications scale. LoginRadius is often chosen by organizations seeking clearer cost predictability as identity volumes increase.
Compliance-ready by default: LoginRadius comes with SOC 2 Type II, ISO 27001, GDPR, CCPA, and HIPAA-aligned controls, along with configurable regional data residency options. This simplifies security reviews and procurement cycles. While Okta CIC supports strong compliance standards, teams often still need to align pricing tiers, regions, and configurations carefully to meet regulatory and data residency requirements across multiple markets.
Low-code identity orchestration for faster iteration: Hosted login experiences, configurable workflows, progressive profiling, conditional MFA policies, and theming tools allow product and CX teams to iterate on identity journeys without writing or maintaining custom code. In contrast, Okta CIC commonly requires Actions and Hooks for non-trivial customization, which can slow iteration and shift ownership of identity UX changes back to engineering teams.
Enterprise-grade migration and in-house support model: LoginRadius provides structured migration tooling, hands-on professional services, and access to dedicated in-house CIAM experts for implementation and ongoing optimization. Organizations moving off Okta CIC often cite complex support tiers and reliance on community documentation as friction points. LoginRadius’ support model is designed for teams that want direct access to CIAM specialists throughout deployment and beyond.
Ideal For
-
B2B SaaS platforms requiring native multi-tenant identity, delegated administration, and enterprise security
-
Consumer brands operating at global scale with seasonal or event-driven traffic spikes
-
Regulated industries needing certifications and regional data residency without infrastructure ownership
-
Organizations looking for predictable pricing, faster time-to-value, and a fully managed CIAM platform as identity complexity grows
2. Descope
Descope is a cloud-based identity platform focused on passwordless authentication and rapid implementation through visual flow orchestration. It is commonly evaluated as an Okta CIC alternative by teams that want to reduce engineering effort and move quickly toward modern, passwordless-first authentication experiences.
Descope emphasizes prebuilt authentication journeys and low-code configuration, making it appealing for teams that want to ship quickly without maintaining complex identity logic.
Where Descope Performs Well
-
Passwordless-first authentication: Descope offers native support for magic links, passkeys, OTPs, and biometric-backed authentication flows. Passwordless is a core design principle rather than an add-on, which aligns well with teams prioritizing frictionless user onboarding.
-
Visual flow builder: Authentication and verification flows are configured using a visual interface, reducing the need for custom code and enabling faster iteration compared to Action- or Hook-heavy approaches.
-
Fast time-to-value: Teams can implement login, signup, and verification flows quickly, making Descope attractive for greenfield applications and early-stage products.
CIAM Fit Analysis: Descope works well for teams prioritizing speed, simplicity, and passwordless adoption. However, for complex CIAM use cases, such as large-scale B2B SaaS, multi-tenant identity, or regulated deployments, its feature depth and enterprise controls may be limiting compared to more mature CIAM platforms.
Ideal For
-
Startups and early-stage SaaS companies
-
Teams adopting passwordless-first strategies
-
Products needing fast authentication rollout
Trade-Offs
-
Limited depth for complex B2B and multi-tenant CIAM scenarios
-
Smaller enterprise ecosystem compared to Okta CIC
-
Less flexibility for highly customized identity architectures
3. Ping Identity
Ping Identity is a long-established IAM vendor offering both workforce IAM and CIAM capabilities. It is often evaluated as an Okta CIC alternative by large enterprises seeking a unified identity vendor across employees, customers, and partners.
Ping is known for its standards compliance and flexibility, particularly in complex or regulated environments.
Where Ping Identity Performs Well
-
Strong standards support: Ping has deep, mature support for SAML, OAuth, OIDC, and federation use cases, making it suitable for enterprise identity integration.
-
Enterprise and hybrid deployment options: Supports complex architectures, including hybrid and regulated environments, where identity must integrate with legacy systems.
-
Broad IAM portfolio: Organizations already invested in Ping for workforce IAM may extend it into customer identity to reduce vendor sprawl.
CIAM Fit Analysis: Ping Identity is powerful but heavyweight. While it can support CIAM use cases, implementations often require significant professional services, longer deployment timelines, and ongoing operational investment compared to CIAM-native platforms.
Ideal For
-
Large enterprises with complex IAM environments
-
Regulated industries with hybrid requirements
-
Organizations standardizing on Ping across workforce and CIAM
Trade-Offs
-
High implementation and operational complexity
-
Slower iteration on customer-facing UX
-
CIAM features often require services-heavy deployments
4. Microsoft Entra External ID
Microsoft Entra External ID (formerly Azure AD B2C) is Microsoft’s customer identity offering and is commonly considered by organizations already standardized on Azure and the Microsoft security ecosystem.
It extends Microsoft’s workforce identity foundations into customer identity scenarios.
Where Entra External ID Performs Well
-
Deep Microsoft ecosystem integration: Native alignment with Azure services, Entra ID, and Microsoft security tooling simplifies integration for Azure-first organizations.
-
Baseline CIAM functionality: Supports customer authentication, social login, and federation for straightforward CIAM use cases.
-
Enterprise familiarity: IT teams already using Microsoft identity products benefit from consistent administration and tooling.
CIAM Fit Analysis: Entra External ID works for basic CIAM scenarios but often struggles with consumer-grade UX flexibility and rapid iteration. Custom policies can be complex to manage, making advanced identity journeys harder to evolve over time.
Ideal For
-
Azure-centric organizations
-
Enterprises standardizing on Microsoft identity
-
Simple or low-variation CIAM use cases
Trade-Offs
-
Complex custom policy management
-
Limited flexibility for branded, consumer-grade UX
-
Slower iteration for non-standard identity flows
5. Amazon Cognito
Amazon Cognito is an AWS-native identity service frequently evaluated by teams operating entirely within the AWS ecosystem. It provides foundational authentication services tightly integrated with AWS infrastructure.
Where Amazon Cognito Performs Well
-
Native AWS integration: Seamlessly integrates with AWS IAM, Lambda, API Gateway, and other AWS services.
-
Cost-effective for simple use cases: At small scale or for basic authentication needs, Cognito can be economical.
-
Infrastructure alignment: Fits well for teams that prefer infrastructure-driven identity management.
CIAM Fit Analysis: Cognito is infrastructure-first rather than CIAM-first. Advanced authentication, UX customization, and orchestration typically require Lambda triggers and custom code, increasing engineering ownership and long-term maintenance costs.
Ideal For
-
AWS-native development teams
-
Applications with basic authentication requirements
-
Infrastructure-led identity strategies
Trade-Offs
-
Heavy reliance on custom code for advanced flows
-
Limited consumer-grade UX tooling
-
Weak native support for B2B and multi-tenant CIAM
6. ForgeRock (Ping Identity)
ForgeRock, now part of Ping Identity, is a highly configurable identity platform historically used by governments and large financial institutions. It is often evaluated by organizations with extreme customization requirements.
Where ForgeRock Performs Well
-
Deep customization and control: Offers fine-grained control over identity flows, data models, and policies.
-
Strong fit for bespoke environments: Well-suited for organizations with dedicated IAM teams and unique requirements.
CIAM Fit Analysis: ForgeRock is powerful but resource-intensive. Deployments are typically long, complex, and costly, making it less suitable for teams seeking fast time-to-value or lower operational overhead compared to modern CIAM platforms.
Ideal For
-
Governments and large financial institutions
-
Organizations with dedicated IAM engineering teams
-
Highly customized identity environments
Trade-Offs
-
Long deployment timelines
-
High total cost of ownership
-
Significant operational and maintenance burden
7. WorkOS
WorkOS is a developer-focused platform designed to simplify enterprise SSO and directory synchronization for B2B SaaS products. It is sometimes evaluated alongside Okta CIC by SaaS teams focused primarily on enterprise customer access.
Where WorkOS Performs Well
-
Fast enterprise SSO enablement: Simplifies SAML, OIDC, and directory sync integrations for SaaS products.
-
Clean developer APIs: Well-designed APIs reduce effort for common enterprise identity requirements.
CIAM Fit Analysis: WorkOS is not a full CIAM platform. It focuses on enterprise access rather than consumer identity, authentication journeys, or advanced security controls, making it complementary rather than a complete replacement for Okta CIC.
Ideal For
-
B2B SaaS companies enabling enterprise SSO
-
Developer teams prioritizing speed for enterprise integrations
Trade-Offs
-
Not designed for B2C or consumer CIAM
-
Limited MFA, passwordless, and orchestration depth
-
Requires pairing with another CIAM solution for full coverage
Why People Switch from Okta Customer Identity Cloud to LoginRadius
While Okta Customer Identity Cloud offers strong extensibility and a mature ecosystem, we consistently see teams switch to LoginRadius as their CIAM requirements mature and scale.
Predictable, transparent pricing as identity grows
Okta CIC’s MAU-based pricing model, combined with add-on costs for advanced features and extensibility, can lead to unpredictable spend as applications scale or traffic spikes.
LoginRadius provides simple, tiered pricing designed for consumer and B2B identity growth, helping teams plan long-term without usage-driven budget surprises.
Faster time to value without custom pipelines
Implementing non-trivial identity journeys in Okta CIC often requires Actions, Hooks, and custom logic, which increases engineering effort and slows down iteration for product and CX teams.
With LoginRadius, teams can go live quickly using hosted login experiences, configurable workflows, and low-code orchestration, without building and maintaining custom execution pipelines.
Enterprise-grade security without operational anxiety
Some organizations re-evaluating Okta CIC cite concerns around shared vendor risk and the operational complexity of managing advanced security controls through extensibility.
LoginRadius is built with a CIAM-focused security architecture, offering adaptive MFA, passkeys, breached password protection, and risk-based authentication as native capabilities, backed by a verifiable breach-free platform history.
In-house expert support included
Okta CIC’s support experience varies by plan, with many teams relying heavily on documentation and community resources for complex CIAM scenarios.
LoginRadius includes access to dedicated in-house CIAM experts, SLAs, and hands-on support, ensuring teams receive timely, personalized assistance during implementation, migration, and ongoing optimization.
Easier onboarding and administration for CIAM teams
Okta CIC’s flexibility comes with a learning curve, especially for teams new to CIAM or those without dedicated identity specialists.
LoginRadius offers a modern, intuitive admin dashboard with guided setup, clear documentation, and a shorter learning curve for both developers and administrators managing customer and B2B identity at scale.
Okta Customer Identity Cloud vs LoginRadius: Key CIAM Differences
| Capability | LoginRadius | Okta Customer Identity Cloud (CIC) |
|---|---|---|
| CIAM focus | Purpose-built CIAM platform for B2C, B2B, and partner identity | CIAM offering adapted from a developer-centric IAM model |
| Pricing model | Predictable, tiered pricing designed for scale | MAU-based pricing with add-on feature costs |
| Passwordless & passkeys | Native support for FIDO2/WebAuthn passkeys, magic links, OTPs | Supported, but advanced flows often require Actions and higher tiers |
| MFA depth & adaptive security | Push MFA, adaptive risk-based policies, breached password detection built in | MFA supported; adaptive controls vary by plan and configuration |
| B2B & multi-tenant identity | Native multi-tenant orgs, delegated admin, org-level policies | Limited; often requires custom modeling and add-ons |
| Customization & orchestration | Low-code workflows, hosted pages, theming without custom code | Customization typically requires Actions, Hooks, and engineering effort |
| Data residency & compliance | SOC 2 Type II, ISO 27001, GDPR/CCPA, configurable regional hosting | Strong compliance support, but residency and features depend on tier |
| Support & time-to-value | In-house CIAM experts, guided onboarding, fast deployment | Tiered support; complex setups can slow time-to-value |
Conclusion
Okta Customer Identity Cloud remains a capable solution for teams that value deep extensibility and developer control. However, as CIAM requirements evolve, driven by scale, security expectations, compliance obligations, and cost scrutiny, many organizations find that managing complex identity logic and usage-based pricing models begins to slow them down.
Modern CIAM platforms must deliver security, reliability, compliance, and scalability as built-in capabilities, not as outcomes of ongoing customization and engineering effort. That’s why more teams are reassessing Okta CIC and shortlisting alternatives that are purpose-built for customer and B2B identity at scale.
LoginRadius offers a compelling path forward for organizations that want enterprise-grade CIAM without pricing surprises or operational complexity. By combining predictable cost, native B2B and passwordless capabilities, and a fully managed architecture, LoginRadius makes it easier to scale, secure, and support identity across consumer and partner use cases.
Explore LoginRadius CIAM vs. Okta in detail, or talk to our team about migrating from Okta Customer Identity Cloud to a fully managed CIAM platform designed for long-term growth.