OneWelcome has built a reputation as a flexible identity platform, particularly in European enterprise environments where complex access policies, orchestration, and regulatory requirements are common. Its strengths lie in handling sophisticated identity scenarios and supporting organizations with mature IAM teams that can invest time in configuration and governance.
However, as CIAM requirements evolve, many product and engineering teams find that OneWelcome’s approach can feel heavy for modern customer and partner identity use cases. Implementations often require specialized expertise, extended onboarding, or professional services, and teams can run into friction when trying to iterate quickly on login experiences, branding, or authentication flows.
For organizations focused on fast-moving B2C and B2B products, where conversion rates, developer velocity, and time-to-market matter, this complexity becomes a trade-off. As a result, more teams are reassessing whether OneWelcome is the right long-term fit for CIAM and are actively exploring alternatives that prioritize usability, customization, and developer efficiency without sacrificing security or scale.
Evaluation Criteria: What Makes a Good CIAM Platform
Before comparing OneWelcome alternatives, it’s important to understand what separates a basic authentication solution from a good Customer Identity and Access Management (CIAM) platform. From our experience working with B2C and B2B product teams, these are the criteria most organizations use when reassessing OneWelcome or similar enterprise-focused identity platforms.
Use Case Fit: CIAM, Workforce IAM, and B2B Identity
A strong CIAM platform is purpose-built for external identities, not adapted from workforce IAM. Customer identity systems must support millions of users, unpredictable traffic spikes, and highly variable authentication journeys, while still delivering a fast, low-friction user experience. Platforms that originated in employee IAM often carry assumptions around static user populations, centralized administration, and rigid policies, which can create friction when applied to customers or partners.
B2B and partner identity adds another layer of complexity. Multi-tenant organizations, delegated administration, role hierarchies, tenant-level authentication policies, and customer-managed users are now common requirements for SaaS platforms and partner ecosystems.
Security and User Experience
Security in CIAM is inseparable from user experience. A modern platform must support a broad range of authentication methods including MFA, passwordless login, passkeys, and social identity without making login flows cumbersome or confusing. Risk-based and adaptive authentication are increasingly important, allowing teams to apply stronger controls only when context or behavior indicates elevated risk.
At the same time, CIAM platforms must give teams fine-grained control over authentication journeys. This includes step-up authentication, progressive profiling, and contextual policies that balance fraud prevention with conversion rates.
Architecture, Scalability, and Performance
CIAM platforms need to be cloud-native by design. This means elastic scaling to handle seasonal traffic spikes, built-in redundancy, and performance that remains consistent across regions. High availability and clearly defined SLAs are critical, especially for customer-facing applications where identity downtime directly translates into lost revenue and support costs.
Multi-tenant architecture also matters. For B2B SaaS platforms, identity systems must isolate tenants cleanly while still enabling centralized management and reporting. Platforms that rely heavily on custom deployments or tenant-specific configurations can become harder to operate and upgrade as environments grow.
Data Residency and Compliance
Data residency is no longer optional for many organizations. CIAM platforms must support regional data hosting to meet privacy regulations such as GDPR and other local data protection laws. Beyond residency, teams should evaluate a vendor’s overall compliance posture, including how identity data is stored, processed, and audited.
Importantly, compliance should not come at the cost of agility. Platforms that require complex deployment models or manual processes to meet regulatory requirements can slow down global expansion and increase operational risk.
Developer Experience and Maintainability
Developer experience is one of the most common reasons teams reconsider OneWelcome. A strong CIAM platform should provide clear documentation, modern APIs, well-maintained SDKs, and sandbox environments that make it easy to prototype and deploy identity flows.
Low- and no-code tools can accelerate delivery, but they should not limit flexibility. Teams need the ability to fully customize authentication logic, integrate with existing systems, and evolve identity workflows over time. Migration effort, ongoing maintenance, and the ability to roll out changes quickly are all critical factors that influence long-term platform success.
Top 7 OneWelcome Alternatives to Consider in 2026
Below are the leading alternatives teams commonly evaluate when moving away from OneWelcome.
1. LoginRadius
LoginRadius is a CIAM platform designed specifically for high-volume B2C applications, B2B SaaS products, and regulated enterprise identity use cases. Unlike OneWelcome, which offers a powerful but often complex identity orchestration layer, LoginRadius is designed as a fully managed CIAM infrastructure that prioritizes usability, customization, and developer velocity at scale.
Where OneWelcome typically appeals to organizations with mature IAM teams willing to manage complexity and configuration overhead, LoginRadius is built for teams that want enterprise-grade security, compliance readiness, and architectural flexibility without taking on long implementation cycles or ongoing operational burden as identity requirements evolve.
Where LoginRadius Works Especially Well
CIAM-native, enterprise-ready architecture: LoginRadius is purpose-built for customer and partner identity from the ground up. The platform natively supports multi-tenant organization models, geo-isolated data residency, multi-region cloud deployments, and SLA-backed availability. These capabilities are fully managed as part of the platform, whereas OneWelcome implementations often require deeper configuration, orchestration expertise, and ongoing tuning to achieve similar outcomes at scale.
Advanced MFA and passwordless authentication: LoginRadius provides built-in support for adaptive, risk-based authentication, including push notification MFA, passkeys, WebAuthn, hardware-backed security keys, OTPs, magic links, and step-up authentication flows. While OneWelcome supports strong authentication methods, implementing adaptive policies or evolving MFA strategies can require more manual configuration and specialized knowledge, slowing iteration.
Compliance readiness without operational overhead: LoginRadius includes SOC 2 Type II, ISO 27001, GDPR, and CCPA compliance as part of its managed service, along with configurable regional data residency options. This simplifies security reviews and procurement processes. With OneWelcome, compliance responsibilities are more closely tied to tenant configuration and deployment models, which can increase internal coordination and long-term maintenance effort.
Predictable scalability with SLA-backed APIs: LoginRadius is designed to handle millions of identities and high-traffic events such as seasonal spikes, product launches, or large enterprise onboarding. Its APIs are SLA-backed and supported by globally distributed infrastructure. OneWelcome can scale effectively, but performance and rollout speed are more dependent on implementation choices and tenant complexity.
Low-code orchestration for faster iteration: Hosted login experiences, configurable workflows, progressive profiling, conditional MFA policies, and theming tools allow teams to update authentication and onboarding journeys without continuous engineering involvement. By comparison, OneWelcome’s flexibility often comes with a steeper learning curve, making simple UX or policy changes more time-consuming.
Enterprise migration and support model: LoginRadius offers structured migration tooling, hands-on professional services, and dedicated customer success support, particularly valuable for regulated industries and large CIAM programs. Feedback around OneWelcome frequently highlights slower response times or limited flexibility in support tiers as deployments grow more complex.
Ideal For
-
B2B SaaS platforms requiring multi-tenant identity, delegated administration, and enterprise security
-
Consumer brands operating at global scale with fluctuating traffic patterns
-
Regulated industries that need compliance and regional data residency without custom infrastructure
-
Organizations seeking fully managed CIAM that can evolve without re-platforming as identity complexity increases
2. Auth0
Auth0 is a cloud-based identity platform widely adopted by developer teams building modern web and mobile applications. It is often evaluated as an alternative to OneWelcome by organizations looking for a managed CIAM service with strong APIs, fast onboarding, and an extensive integration ecosystem.
Compared to OneWelcome’s orchestration-heavy model, Auth0 emphasizes developer ergonomics and speed of implementation. This makes it attractive for teams that want to get customer authentication up and running quickly without deep IAM specialization.
Where Auth0 Works Well
-
Developer-friendly APIs and SDKs: Auth0 offers broad language and framework support with well-documented APIs and SDKs. Teams can integrate authentication into applications quickly, making it well suited for agile, product-led development environments.
-
Extensible authentication flows: Rules and Actions allow teams to inject custom logic into authentication flows, enabling integrations with external services, custom claims, and conditional behavior. This flexibility appeals to developers who want control without managing underlying infrastructure.
-
Large integration ecosystem: Auth0’s marketplace includes a wide range of prebuilt integrations with SaaS platforms, analytics tools, and infrastructure services, reducing time spent on custom development.
CIAM Fit Analysis: Auth0 works well for teams that want a managed CIAM service with strong developer experience and minimal operational overhead. However, as CIAM usage grows, particularly in large B2C or B2B environments, pricing complexity and add-on–driven feature access can become friction points. Advanced CIAM requirements such as predictable pricing at scale, deeper B2B identity models, or regional data residency often require careful tier planning.
Where Auth0 Can Fall Short
-
Pricing can escalate quickly as MAUs increase
-
Many advanced CIAM features are gated behind higher tiers
-
Limited flexibility for complex data residency or sovereign cloud requirements
Ideal For
-
Developer-led product teams prioritizing speed and ease of integration
-
Startups and mid-market SaaS companies with straightforward CIAM needs
-
Applications requiring rapid IAM implementation without custom infrastructure
3. Ping Identity
Ping Identity is an enterprise identity provider best known for large-scale IAM programs that blend workforce, partner, and customer identity requirements. Teams evaluating alternatives to OneWelcome often shortlist Ping when they need mature federation, strong policy controls, and enterprise-grade deployment patterns that can support complex org structures.
Compared with OneWelcome’s orchestration-led approach, Ping typically appeals to organizations that prioritize deep enterprise IAM capabilities, established governance models, and broad integration across legacy and modern systems.
Where Ping Identity Works Well
-
Enterprise-grade federation and SSO: Ping has long-standing strength in SAML/OIDC federation and single sign-on across diverse application portfolios. This is valuable for enterprises consolidating identity across many internal and external apps.
-
Flexible policy and access controls: Ping supports advanced access policies and conditional controls that help centralize authentication and authorization decisions, useful for regulated environments and security-led teams.
-
Deployment options for complex environments: Ping is often used in hybrid scenarios where organizations need flexibility across cloud and on-prem components, particularly when legacy constraints or regulatory requirements limit pure SaaS adoption.
CIAM Fit Analysis: Ping can work well for customer identity, especially when a program is driven by enterprise architecture and security teams who want strong governance and federation capabilities. That said, for product-led CIAM teams focused on rapid UX iteration, onboarding conversion, and fast time-to-market, Ping implementations can introduce heavier planning and integration work. In practice, teams should evaluate whether they need enterprise IAM breadth or a CIAM-first platform optimized for customer journeys and developer velocity.
Where Ping Identity Can Fall Short
-
Implementation and long-term operations can be heavier than CIAM-first platforms
-
Product teams may face slower iteration on login UX and journey changes
-
Total cost can rise as enterprise modules and advanced capabilities are added
Ideal For
-
Large enterprises running broad IAM programs across workforce + customer use cases
-
Highly regulated environments needing mature governance and federation patterns
-
Organizations modernizing legacy IAM while maintaining hybrid requirements
4. Microsoft Entra ID
Microsoft Entra ID extends Azure Active Directory to external users through Entra ID for customers, and is frequently evaluated as a OneWelcome alternative by organizations already deeply invested in Microsoft’s cloud and productivity ecosystem.
Rather than being built first as a CIAM platform, Entra ID evolves from Microsoft’s workforce IAM foundation. This heritage shapes how customer identity, policies, and experiences are modeled, which can be both a strength and a limitation depending on the use case.
Where Microsoft Entra ID Works Well
-
Deep Microsoft ecosystem integration: Entra ID integrates tightly with Azure services, Microsoft 365, and enterprise IT tooling. For organizations standardized on Microsoft, this can simplify identity governance and reduce the need to introduce additional vendors.
-
Enterprise-grade security and identity controls: Backed by Microsoft’s global security infrastructure, Entra ID benefits from mature threat detection, conditional access, and identity protection capabilities inherited from Azure AD.
-
Global scale and reliability: Running on Azure’s global cloud footprint, Entra ID can support large, geographically distributed user bases with strong availability.
CIAM Fit Analysis: Entra ID can support customer and partner identity scenarios, but it remains fundamentally an extension of a workforce IAM system. CIAM teams often need to invest significant effort to configure customer-friendly login journeys, branding, and progressive authentication flows. As a result, Entra ID tends to align better with IT-led identity programs than with product teams focused on optimizing onboarding, conversion rates, and rapid UX experimentation.
Where Microsoft Entra ID Can Fall Short
-
Limited flexibility for CIAM-specific UX customization
-
Complex configuration for customer authentication journeys
-
Less adaptable for non-Microsoft or multi-cloud environments
Ideal For
-
Enterprises standardized on Microsoft and Azure
-
IT-led identity initiatives extending internal IAM to external users
-
Organizations prioritizing ecosystem consolidation over CIAM specialization
5. Amazon Cognito
Amazon Cognito is Amazon Web Services’ native identity service for web and mobile applications. It’s commonly considered by teams looking for a OneWelcome alternative when their infrastructure is already heavily invested in AWS and they want a basic, cloud-native CIAM option without introducing an additional vendor.
Cognito is designed to fit naturally into the AWS ecosystem, but it prioritizes infrastructure alignment over CIAM depth or user experience flexibility.
Where Amazon Cognito Works Well
-
Native AWS integration: Cognito integrates seamlessly with other AWS services such as API Gateway, Lambda, and IAM. For teams building entirely on AWS, this can reduce integration effort and simplify access control across services.
-
Cost-effective for simple use cases: For straightforward authentication needs, Cognito’s pricing can be attractive, especially when usage remains within lower MAU tiers and advanced CIAM features are not required.
-
Scalable infrastructure foundation: Built on AWS’s global infrastructure, Cognito can scale to support large user bases without teams needing to manage underlying capacity or availability.
CIAM Fit Analysis: While Cognito can handle basic customer authentication, it is not a CIAM-first platform. Many advanced requirements, such as rich login customization, complex B2B identity models, progressive profiling, or fine-grained authentication journeys, require significant custom development using Lambda functions and supporting AWS services. This shifts CIAM complexity back onto engineering teams and can slow iteration as requirements evolve.
Where Amazon Cognito Can Fall Short
-
Limited control over hosted UI and user experience
-
Advanced CIAM features often require custom development
-
Steep learning curve outside the AWS ecosystem
Ideal For
-
AWS-native teams building greenfield applications
-
Simple consumer or internal-facing use cases
-
Organizations optimizing for infrastructure consolidation rather than CIAM specialization
6. ForgeRock
ForgeRock is an enterprise identity platform historically positioned for large, complex IAM deployments across regulated industries. Teams evaluating OneWelcome alternatives often consider ForgeRock when they require deep policy control, flexible deployment models, and strong support for compliance-heavy environments.
ForgeRock offers extensive identity capabilities, but that breadth comes with operational and architectural trade-offs, particularly for teams focused primarily on CIAM rather than broader IAM consolidation.
Where ForgeRock Works Well
-
Advanced identity and access controls: ForgeRock provides granular policy management, flexible authentication trees, and strong support for complex identity workflows. This makes it suitable for environments with strict regulatory or security-driven requirements.
-
Flexible deployment options: ForgeRock supports cloud, on-premises, and hybrid deployments, which can be important for organizations with data sovereignty constraints or legacy infrastructure dependencies.
-
Strong fit for regulated industries: Financial services, government, and healthcare organizations often evaluate ForgeRock for its ability to support rigorous compliance and audit requirements.
CIAM Fit Analysis: ForgeRock can support customer identity at scale, but it is not optimized for speed or simplicity. CIAM implementations typically require significant planning, customization, and ongoing operational effort. For product-led teams that need to iterate quickly on authentication UX or reduce identity-related maintenance, this complexity can become a limiting factor compared to CIAM-first, fully managed platforms.
Where ForgeRock Can Fall Short
-
High total cost of ownership as deployments scale
-
Significant implementation and maintenance effort
-
Slower time-to-value for CIAM-specific use cases
Ideal For
-
Highly regulated industries with strict compliance mandates
-
Large enterprises running complex IAM programs
-
Organizations prioritizing control and flexibility over simplicity and speed
7. WorkOS
WorkOS is an identity and enterprise-readiness platform focused primarily on B2B SaaS use cases. It is often considered by teams looking beyond OneWelcome when their immediate need is enabling enterprise features, such as SSO and directory sync, without building them from scratch.
Rather than positioning itself as a full CIAM platform, WorkOS acts as an identity abstraction layer that helps SaaS companies meet enterprise customer requirements quickly.
Where WorkOS Works Well
-
Fast enablement of enterprise SSO: WorkOS makes it straightforward to add SAML-based SSO, SCIM provisioning, and directory sync to SaaS products. This is especially valuable for teams selling into mid-market and enterprise accounts with strict IT requirements.
-
Developer-friendly APIs: The platform provides clean APIs and clear documentation, allowing engineering teams to integrate enterprise identity features without deep IAM expertise.
-
Focused B2B use case: WorkOS is intentionally narrow in scope, which helps teams avoid the complexity of broader IAM platforms when their primary goal is enterprise readiness.
CIAM Fit Analysis: WorkOS is not a full CIAM replacement for platforms like OneWelcome. It does not manage consumer-scale identity lifecycles, authentication UX, or advanced CIAM security controls. Instead, it complements an existing authentication system. For teams seeking a single platform to handle B2C, B2B, and partner identity at scale, WorkOS alone is typically insufficient.
Where WorkOS Can Fall Short
-
Not designed for consumer identity or large-scale CIAM
-
Limited authentication UX and policy controls
-
Requires pairing with another identity system
Ideal For
-
B2B SaaS companies adding enterprise SSO and provisioning
-
Product teams focused on enterprise deals rather than consumer CIAM
-
Organizations seeking quick enterprise enablement, not full CIAM consolidation
Why People Switch From OneWelcome to LoginRadius
Organizations that move away from OneWelcome are rarely questioning its core capabilities. Instead, the decision usually comes down to operational friction, speed, and long-term maintainability as CIAM programs grow beyond initial deployments.
Easier to Implement and Maintain
LoginRadius is designed for fast, plug-and-play CIAM implementation. Its intuitive admin interface, hosted login options, and prebuilt workflows allow teams to deploy and iterate without deep IAM specialization.
With OneWelcome, implementations often require extensive configuration, orchestration expertise, or professional services, which can slow initial rollout and increase long-term maintenance effort.
True Freedom in Customization
LoginRadius enables teams to build fully custom login flows, UI experiences, and authentication policies without being constrained by rigid templates. Teams can evolve branding, onboarding, and security journeys independently of core application development.
In contrast, OneWelcome’s customization model, while powerful, can be limited by predefined structures, making seemingly small changes more time-consuming to implement.
Faster Rollouts and Continuous Updates
LoginRadius operates as a fully managed, cloud-native CIAM platform with continuous global updates. New capabilities and improvements are rolled out without customer-side deployment cycles.
With OneWelcome, update cadence and feature availability can vary depending on tenant configuration and deployment models, which may slow adoption of new functionality.
Predictable, Scalable Pricing
LoginRadius uses a simple, usage-based pricing model that includes core CIAM capabilities upfront. This makes it easier for teams to forecast costs as user volumes and feature needs grow.
OneWelcome’s modular pricing approach can become expensive as organizations add features, tenants, or user tiers, often introducing cost uncertainty at scale.
Built for Developers
LoginRadius provides modern REST APIs, web and mobile SDKs, detailed documentation, and sandbox environments that enable rapid integration and iteration. Developer teams can own identity workflows without becoming identity specialists.
While OneWelcome is powerful, teams new to its ecosystem often face a steeper learning curve, which can slow delivery and increase reliance on specialized resources.
Global, Responsive Support
LoginRadius offers 24/7 technical support, structured onboarding, and dedicated customer success resources for enterprise and regulated deployments. This hands-on support model is especially valuable during migrations or large-scale rollouts.
Feedback around OneWelcome frequently highlights slower response times or limited flexibility across support tiers.
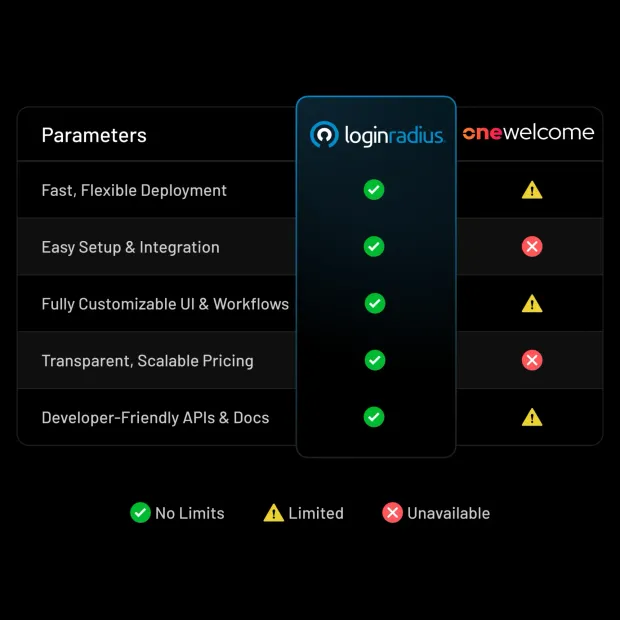
OneWelcome vs LoginRadius: Feature comparison
| Capability | LoginRadius | OneWelcome |
|---|---|---|
| Primary focus | Purpose-built CIAM for B2C, B2B, and partner identity | Enterprise IAM with strong orchestration capabilities |
| Deployment model | Fully managed, cloud-native CIAM | Tenant-based deployments with configuration-heavy setup |
| CIAM customization | Full control over login UX, flows, and policies without rigid templates | Customization possible but often constrained by predefined structures |
| Multi-tenant B2B identity | Native support for organizations, roles, and delegated admin | Supported, but often requires deeper configuration |
| MFA & passwordless | Push MFA, adaptive risk-based auth, passkeys, WebAuthn, magic links | Strong authentication support, but adaptive flows require more setup |
| Developer experience | Modern APIs, SDKs, clear docs, sandbox environments | Powerful but steeper learning curve |
| Data residency | Configurable regional data residency options | Supported, but tied to deployment configuration |
| Compliance posture | SOC 2 Type II, ISO 27001, GDPR, CCPA included | Enterprise-grade, but compliance responsibilities vary by setup |
| Scalability & performance | SLA-backed APIs built for high-volume CIAM | Scales well, but depends on tenant and architecture choices |
| Pricing model | Simple, usage-based pricing with CIAM features included | Modular pricing that can expand as features are added |
| Time to value | Fast deployment with low operational overhead | Longer implementation cycles for complex use cases |
| Support model | 24/7 support, structured onboarding, customer success | Support tiers vary; feedback notes slower response at scale |
Conclusion
OneWelcome remains a capable identity platform, particularly for organizations with mature IAM teams and complex orchestration requirements. Its flexibility and enterprise focus make it a strong option in scenarios where identity governance and policy depth take precedence over speed and simplicity.
That said, many modern CIAM teams, especially those supporting B2C products and B2B SaaS platforms, find that OneWelcome’s complexity, customization boundaries, and operational overhead create friction over time. As customer expectations rise and identity journeys need to evolve quickly, platforms that slow iteration or require specialized expertise can become a constraint rather than an enabler.
Choosing the right CIAM platform ultimately comes down to alignment with your real-world use cases. Teams should evaluate whether they need workforce-style IAM extensibility, or a CIAM-first solution designed for scale, usability, and developer efficiency. For organizations prioritizing fast deployment, full customization, predictable pricing, and managed compliance, LoginRadius is often a strong alternative worth shortlisting.
If you’re planning a migration or want guidance on CIAM architecture for B2C or B2B identity, our team can help you assess requirements, risks, and timelines, so you can move forward with confidence, not complexity.