Quick Summary
-
Social login is an authentication method that lets users sign in with existing accounts from providers like Google, Apple, Facebook, or LinkedIn instead of creating new credentials.
-
It works by using OAuth 2.0 and OpenID Connect, which securely verify the user with the social provider and return essential profile data back to your application.
-
The primary benefit of social login is reduced friction: faster sign-up, fewer abandoned forms, and a simpler mobile experience.
-
Businesses gain higher conversion rates, more repeat logins, and clean, permission-based customer data that improves personalization and marketing accuracy.
-
Social login is most effective for ecommerce, SaaS, subscription media, and mobile-first consumer apps; it should be paired with MFA or passkeys for high-security industries.
Introduction
Social login is a simple way for users to access your application without creating yet another username and password. Instead of filling out long registration forms, they can sign in with existing accounts from providers like Google, Apple, Facebook, LinkedIn, or GitHub. For end users, it feels like a fast, familiar single sign-on experience. For businesses, it removes friction from onboarding and creates a more reliable path to verified customer data.
As expectations for seamless digital access continue to rise, especially on mobile, social login has become a core authentication pattern across ecommerce, SaaS, media, and consumer apps. But alongside its convenience, product teams and developers still ask the same critical questions: Is social login worth it? How secure is it? And how hard is it to implement safely at scale?
This blog breaks down how social login works, when it makes sense, and what to consider around security, privacy, and deployment so you can make an informed decision for your application.
Social login, also called social sign-in or social authentication is an authentication method that lets users access your application using existing accounts from providers like Google, Apple, Facebook, LinkedIn, and GitHub. Instead of issuing a new username and password, your app delegates authentication to the provider, then uses the returned identity data to create or update the user’s profile.
At a technical level, social login is built on open standards: OAuth 2.0 for authorization and OpenID Connect (OIDC) for identity. When a user clicks “Continue with Google,” for example, your application redirects them to Google’s authorization endpoint, where the provider handles credential verification, consent prompts, and scope approval. After the user authenticates, your app receives an authorization code or ID token that contains verified identity claims such as email, name, or profile attributes.
Social login is distinct from enterprise SSO or workforce federation. It is designed for consumer applications that need a low-friction, high-conversion entry point, especially on mobile devices where typing passwords or completing forms is slow.
For developers, it replaces the need to store, validate, and protect passwords, while giving applications access to permission-based, standardized user data. This combination of reduced complexity and improved user experience is why social login remains a foundational authentication pattern in modern CIAM implementations.
How Social Login Works
Social login is fundamentally an identity delegation workflow. Instead of authenticating users directly, your application relies on a trusted external identity provider, like Google, Apple, Facebook, LinkedIn, GitHub, or any other social IdP to verify the user and return a signed assertion of identity.
At a protocol level, social login is implemented through OAuth 2.0 and, in most modern cases, OpenID Connect (OIDC). These standards provide a secure mechanism for your application to request identity and profile information without ever accessing the user’s credentials.
What the User Sees (The Frictionless Experience)
From the user’s perspective, the flow is intentionally simple:
-
They click a provider button (e.g., Google, Apple, Facebook).
-
They authenticate directly with the provider.
-
They grant permission for your application to access specific data.
-
They are returned to your application already signed in.
What Actually Happens (The Real Identity Flow)
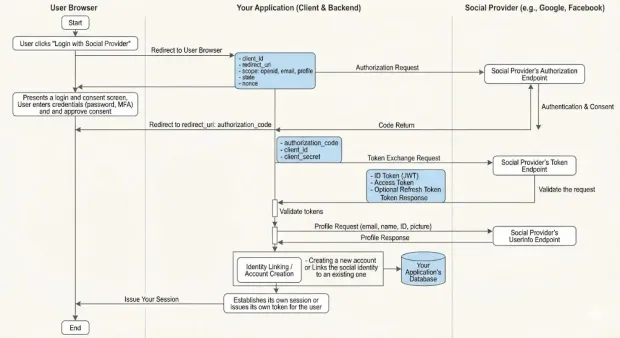
Under the hood, the workflow is precise and standards-driven:
1. Authorization Request
Your application initiates the process by redirecting the user to the provider’s authorization endpoint with parameters such as:
-
client_id -
redirect_uri -
requested
scope(e.g.,openid email profile) -
statefor CSRF protection -
nonceto protect against token replay (OIDC)
2. Provider-Side Authentication and Consent
The provider handles the entire authentication ceremony:
-
Password entry
-
MFA
-
Risk scoring and device evaluation
-
Consent prompts for data access
This is critical: your application never sees any credentials. This is one of the core security benefits of social login.
3. Code Return (Authorization Code Grant)
If the user approves, the provider redirects them back to your application with a short-lived authorization code.
4. Token Exchange
Your backend exchanges this code for:
-
ID Token — a signed JWT that asserts the user’s identity
-
Access Token — used to call the provider’s userinfo endpoint
-
optionally, a Refresh Token
Token validation is non-negotiable: signature, issuer, audience, expiry, and nonce must all be verified.
5. Profile Retrieval
Your application (or CIAM layer) retrieves user profile data:
-
Verified email
-
Name
-
Unique provider ID
-
Locale, picture, or additional authorized attributes
6. Identity Linking or Account Creation
Your system either:
-
Creates a new account with the social identity as the primary login method, or
-
Links the social identity to an existing user profile to preserve continuity across authentication methods.
7. Issue Your Own Session
Once identity is confirmed, your application establishes its own session or issues its own token. The social provider is no longer involved after this point.
What Data You Actually Get
The attributes available through social login depend on:
-
The provider
-
The scopes you request
-
What the user consents to
-
Provider policy (e.g., Apple’s private relay email)
Typical data returned:
-
Verified email address (Google, Apple, Microsoft, LinkedIn)
-
Name and profile metadata
-
Provider-specific unique user ID
-
Profile image
-
Locale / time zone
Because each provider structures attributes inconsistently, enterprise-grade implementations rely on a CIAM layer, like LoginRadius, to normalize fields, unify schema, and keep integrations updated as providers change APIs.
Learn more about the technical implementation of social login.
Social Login Providers: Strengths, Limitations, and When to Use Each
Choosing the right social login providers is an architectural decision that impacts user acquisition, data quality, regulatory compliance, and global usability. Each provider has distinct strengths, constraints, and behavioral patterns that directly affect authentication success rates and downstream identity workflows.
Below is a breakdown of the major providers and how to evaluate them for your application.
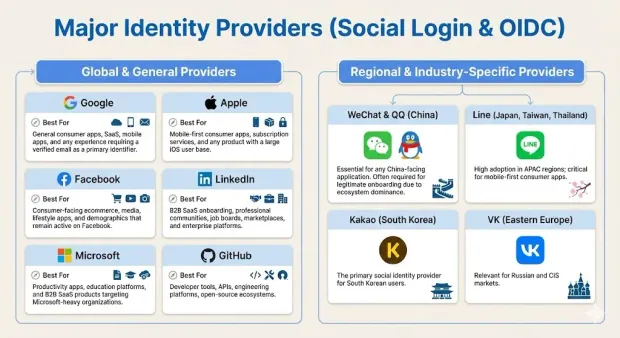
Major Identity Providers
These are the providers most commonly adopted across consumer, SaaS, and mobile-first applications.
Strengths
-
High trust and adoption across nearly all demographics
-
Verified email addresses in most cases
-
Stable, well-documented OIDC implementation
-
Strong fraud detection and MFA adoption
Limitations
-
Some restrictive data scopes
-
Strict branding and UX compliance
-
Corporate Google Workspace accounts may add conditional access policies
Best For: General consumer apps, SaaS, mobile apps, and any experience requiring a verified email as a primary identifier.
Apple
Strengths
-
Mandatory on many iOS apps offering third-party login
-
Strong privacy posture, secure by design
-
Device-level authentication; extremely fast flows
-
High trust within privacy-conscious segments
Limitations
-
Private relay email masks identity; additional linking logic required
-
Limited data attributes returned
-
Requires specific UX adherence on Apple plat
Best For: Mobile-first consumer apps, subscription services, and any product with a large iOS user base.
Strengths
-
Massive global footprint
-
Familiarity and trust among non-technical users
-
Rich optional profile attributes
Limitations
-
More restrictive scopes for user data than in previous years
-
Younger audiences have decreased usage
-
Occasional API and permission policy shifts
Best For: Consumer-facing ecommerce, media, lifestyle apps, and demographics that remain active on Facebook.
Strengths
-
Professional identity data
-
Verified corporate emails
-
High adoption in B2B and SaaS sectors
Limitations
-
Limited profile attributes without elevated permissions
-
Strong restrictions on data usage and storage
Best For: B2B SaaS onboarding, professional communities, job boards, marketplaces, and enterprise platforms.
Microsoft
Strengths
-
Unified identity ecosystem for consumers + enterprise (Outlook, Live, Microsoft 365)
-
Verified email addresses
-
Strong fit for hybrid B2C/B2B apps
Limitations
-
Conditional access policies in enterprise tenants can impact login rate
-
Slightly more complex user identifiers across ecosystems
Best For: Productivity apps, education platforms, and B2B SaaS products targeting Microsoft-heavy organizations.
GitHub
Strengths
-
Strong developer audience trust
-
Minimal friction, fast authentication
-
Useful profile data for technical communities
Limitations
-
Limited general consumer relevance
-
Smaller data set returned
Best For: Developer tools, APIs, engineering platforms, open-source ecosystems.
Regional and Industry-Specific Providers
Global applications cannot rely solely on US-centric providers. Regional identity networks dominate in specific markets.
-
WeChat & QQ (China): Essential for any China-facing application. Often required for legitimate onboarding due to ecosystem dominance.
-
Line (Japan, Taiwan, Thailand): High adoption in APAC regions; critical for mobile-first consumer apps.
-
Kakao (South Korea): The primary social identity provider for South Korean users.
-
VK (Eastern Europe): Relevant for Russian and CIS markets.
How to Choose Providers Strategically
Selecting social login providers should follow a structured evaluation based on four core factors:
1. Audience Demographics
-
Where do your users live?
-
What devices do they use?
-
What identity ecosystems dominate that region?
2. Industry Alignment
For example:
-
B2B SaaS → LinkedIn, Microsoft, Google
-
Consumer ecommerce → Google, Facebook, Apple
-
Developer platforms → GitHub, Google
-
APAC apps → WeChat, Line, Kakao
3. Data Requirements
If you need verified emails or professional attributes, prioritize providers that return them consistently.
4. Compliance and Risk
Some providers have strict data usage rules, and some regions have unique regulatory constraints. A mature CIAM layer helps mitigate these by normalizing and enforcing compliant data handling.
Key Benefits of Social Login
Below are the core benefits enterprises and product teams consistently realize.
1. Reduced Friction and Higher Conversion
Every additional field in a registration form increases abandonment. Social login collapses sign-up and sign-in into a single action by offloading:
-
Password creation
-
Email verification
-
Form fill
-
Identity confirmation
This reduction in friction translates directly into higher completion rates, particularly on mobile where typing and form navigation are exhausting. In most consumer and SaaS applications, adding social login measurably improves conversion at the top of the funnel.
2. Faster Repeat Logins and Fewer Barriers to Return
Users rarely remember which password they created for a service or whether they used email, phone, or a social account on the last visit. Social login eliminates this cognitive burden.
When users click “Continue with Google” or “Sign in with Apple,” they bypass traditional reauthentication friction, including forgotten password flows resulting in:
-
Higher return usage
-
More consistent session re-entry
-
Lower authentication dropout rates
3. Significantly Lower Password-Related Support Costs
Help desks consistently report that a large percentage of support tickets relate to password resets, account lockouts, or login issues. Social login minimizes these events by:
-
Reducing stored passwords
-
Eliminating many reset workflows
-
Moving MFA and account recovery to the provider
The result is a material reduction in support volume and operational overhead, especially in high-scale consumer environments.
4. Verified, Permission-Based Customer Data
Unlike traditional registration, where users may provide inaccurate or disposable email addresses, social login typically returns:
-
Verified email addresses
-
Real names (where allowed)
-
Stable unique identifiers
-
Locale, profile image, or professional data (varies by provider)
This data is consent-based, standardized by the provider, and often more trustworthy than self-entered form fields. It enables:
-
More accurate identity resolution
-
Better personalization
-
Stronger segmentation and lifecycle marketing
-
Reduction in duplicate or fraudulent accounts
5. Higher Quality Identity Graphs and Cross-Device Continuity
Because social providers offer stable, reusable identities, users can authenticate consistently across:
-
Browsers
-
Devices
-
App versions
This reduces fragmentation in customer profiles and improves your ability to unify user activity over time.
No more “three accounts for the same user” because they used email once, phone another time, and a social account later.
6. Marketing and Growth Advantages
Social login strengthens downstream monetization and marketing because identity data becomes more complete and reliable. Teams can:
-
Prefill onboarding fields
-
Apply more accurate audience segmentation
-
Trigger personalized messaging
-
Reduce friction for loyalty or referral programs
-
Build trust through social proof or network-driven recommendations
Even when not used for explicit sharing features, social login gives marketing and product teams a cleaner foundation for engagement.
7. A Smaller Security Attack Surface
Social login decreases exposure to common attack vectors, including:
-
Credential stuffing
-
Password brute forcing
-
Password reuse attacks
-
Weak or compromised credentials
Because authentication happens at the provider level, your application benefits from their built-in security stack: MFA enrollment, device intelligence, behavioral analytics, and threat detection that you do not have to build.
Learn more about Credential Stuffing: How To Detect And Prevent It
8. Faster Time-to-Market for Authentication
Social login removes most of that responsibility from your development team. When paired with a CIAM platform, providers can be enabled with minimal code and maintained centrally, without custom OAuth stacks, manual API updates, or rewriting flows across multiple apps.
This reduces engineering burden and accelerates time-to-market for new authentication experiences.
How Social Login Handles Security, Privacy, and Regulatory Compliance
Security is often the first concern raised when teams evaluate social login, but in practice, it reduces more risk than it introduces. By design, social login offloads the most sensitive part of authentication to providers that already operate hardened identity systems.
Google, Apple, Facebook, Microsoft, and LinkedIn maintain continuous threat detection, MFA enforcement, device intelligence, and credential protection at a scale individual applications cannot replicate. When your users authenticate through these providers, your application avoids storing passwords, eliminating the single largest attack surface in traditional login flows.
From a technical standpoint, the strength of social login comes from OAuth 2.0 and OpenID Connect, which provide predictable token flows, signed ID tokens, and well-defined validation requirements. The critical safeguards—verifying token signatures, checking issuer and audience claims, enforcing nonce/state validation, and applying strict redirect URI rules—prevent common OAuth abuses. When these controls are handled in a centralized CIAM layer, organizations gain consistent security across providers without custom code or one-off integrations.
Privacy is equally important. Social login only grants access to the attributes your application requests and the user consents to during the authorization step. Providers now enforce strict scope policies, and users are accustomed to reviewing consent screens, making social login inherently transparent. Best practice is to request only the minimum data necessary, typically an email and basic profile information and allow users to manage linked identities.
Compliance considerations, GDPR, CCPA, SOC2, and regional data residency rules also factor into social login architecture. Because providers may return different data in different regions or restrict certain scopes entirely, global applications need a layer that applies consistent governance, retention controls, and auditability over social identity data. This is where mature CIAM platforms deliver value: they manage provider-specific policies, maintain compliant integrations, and ensure identity data is stored, processed, and deleted according to regulatory requirements.
Social Providers with LoginRadius
LoginRadius maintains a consistently updated catalogs of social identity providers. The platform supports all major and regional social providers out of the box, including Google, Apple, Facebook, LinkedIn, X/Twitter, GitHub, Microsoft, Amazon, Weibo, QQ, WeChat, Line, Kakao, Yahoo Japan, and many others.
What differentiates LoginRadius is also the depth and stability of those integrations. Every provider has its own authentication nuances, like different token formats, endpoint behaviors, scope requirements, profile schemas, and ongoing API changes. Some providers use strict OIDC implementations; others rely on OAuth 2.0 variations; and a few still maintain older OAuth 1.0a flows. Implementing these individually is error-prone and creates long-term maintenance risk for internal engineering teams.
LoginRadius abstracts this complexity entirely. All social providers are integrated through a unified, standardized social login API that normalizes profile attributes, enforces consistent token validation rules, and applies identity mapping across providers. No matter which provider a user selects, your application receives a clean, normalized identity profile with stable fields. This also ensures resilience: when a provider changes an endpoint, permission model, or data attribute, LoginRadius handles the update centrally without requiring code changes in your applications.
Beyond predefined providers, LoginRadius also supports custom OAuth 2.0 and OpenID Connect providers, enabling organizations to add niche or region-specific identity sources without building custom integrations. This is especially valuable for enterprises operating across APAC, LATAM, or markets where local identity networks dominate.
For engineering teams, the result is straightforward:
-
No per-provider OAuth logic
-
No custom token parsing
-
No inconsistent attribute mapping
-
No need to chase provider API changes
-
No fragmentation of identity data across systems
LoginRadius consolidates social login management into a single, coherent identity layer that can be enabled or updated centrally across all applications. This is the architectural approach required for teams running multiple apps, operating in several regions, or maintaining long-term identity governance at scale.
Learn more about LoginRadius Social Login.
How to Add Social Login with LoginRadius in a Few Steps
Enabling social login in LoginRadius is designed to be configuration-driven and consistent across all providers. Instead of managing OAuth flows individually, you activate providers through the LoginRadius Admin Console and let the platform handle token validation, profile normalization, and policy enforcement.
1. Open the LoginRadius Admin Console and navigate to “Authentication Providers.”
This is the central location for managing all social, enterprise, and custom identity sources. Every supported provider is listed with its configuration status and scope requirements.
2. Choose the social providers you want to enable.
Select from 35+ pre-integrated providers—Google, Apple, Facebook, LinkedIn, GitHub, WeChat, Kakao, and more. Each provider’s configuration dialog includes required credentials, available scopes, and any provider-specific guidelines.
3. Enter your provider credentials and define permissions.
Add your Client ID and Client Secret (or equivalent) obtained from the provider’s developer portal. LoginRadius provides direct links and step-by-step guidance for retrieving these keys, ensuring proper redirect URIs and access scopes are configured.
4. Configure the attributes your application needs.
LoginRadius lets you specify which user profile fields and scopes should be requested from each provider. The platform automatically normalizes attributes into a unified schema, eliminating the need for application-side mapping.
5. Assign providers to your applications or environments.
Enable or disable providers per application, environment, or region with a single configuration toggle useful for multi-app and multi-tenant deployments.
6. Save and deploy.
Once saved, the provider is immediately available across your login flows, whether you’re using hosted pages, JavaScript widgets, mobile SDKs, or custom API integrations. No code changes are required to add or remove providers.
Conclusion
Social login is worth adopting because it removes the weakest part of most authentication stacks: passwords. Delegating identity verification to providers with hardened security, enforced MFA, and real-time threat detection reduces your exposure dramatically. It also gives you verified identifiers and consistent return paths that simplify account creation, recovery, and lifecycle management.
But social login only works at scale when it operates inside a unified identity layer. Without centralized governance, you end up with different OAuth implementations scattered across services, inconsistent attribute handling, and brittle integrations that break when a provider silently changes an endpoint or deprecates a scope. This is why modern architectures place social identity behind a CIAM platform: it standardizes the flow, absorbs provider changes, and exposes a stable interface your applications can depend on.
FAQs
1. What is social login?
Social login is an authentication method that lets users sign in with existing accounts from providers like Google, Apple, Facebook, or LinkedIn instead of creating new credentials.
2. How does social login work?
Social login uses OAuth 2.0 and OpenID Connect to delegate authentication to a social provider, which returns a signed identity token your app can validate and use to create or update a user profile.
3. What data does a social login provider return?
Most providers return verified identifiers, typically email, name, unique user ID, and basic profile metadata based on the scopes your application requests and the user consents to.
4. Which social login providers should I support?
Choose providers based on your audience: Google and Apple for most consumer/mobile apps, LinkedIn and Microsoft for B2B, GitHub for developer platforms, and regional providers like WeChat, Line, or Kakao for APAC markets.
5. What are the main benefits of social login?
It reduces onboarding friction, improves conversion, lowers password-related support costs, delivers verified user data, and reduces your authentication attack surface.
6. When is social login worth implementing?
Social login is ideal when fast onboarding drives growth, especially in ecommerce, SaaS, media, and mobile apps. In high-assurance environments, it should be paired with MFA or passkeys.
7. Is social login secure?
Yes, because authentication is handled by hardened providers with MFA, device intelligence, and strong risk controls. The key is properly validating tokens and scopes on your side.
8. How does social login protect user privacy?
Users explicitly consent to the data shared, providers enforce strict scope rules, and CIAM platforms apply data minimization, normalization, and retention controls.
9. Is social login compliant with GDPR and CCPA?
Social login can be compliant when you request minimal scopes, store data lawfully, honor deletion/access rights, and use a CIAM layer that enforces governance and auditability.
10. How fast can I add social login to my application?
With a CIAM platform, like LoginRadius, social login can be enabled in hours using pre-built providers and unified APIs.


