Delegated Access in Agentic Systems
Autonomous agents act on a human’s behalf across systems, not as a one-time login event. Agentic IAM reframes identity from authentication to continuous authorization, consent, and oversight. Delegation balances agent autonomy with clear ownership, control, and auditability.

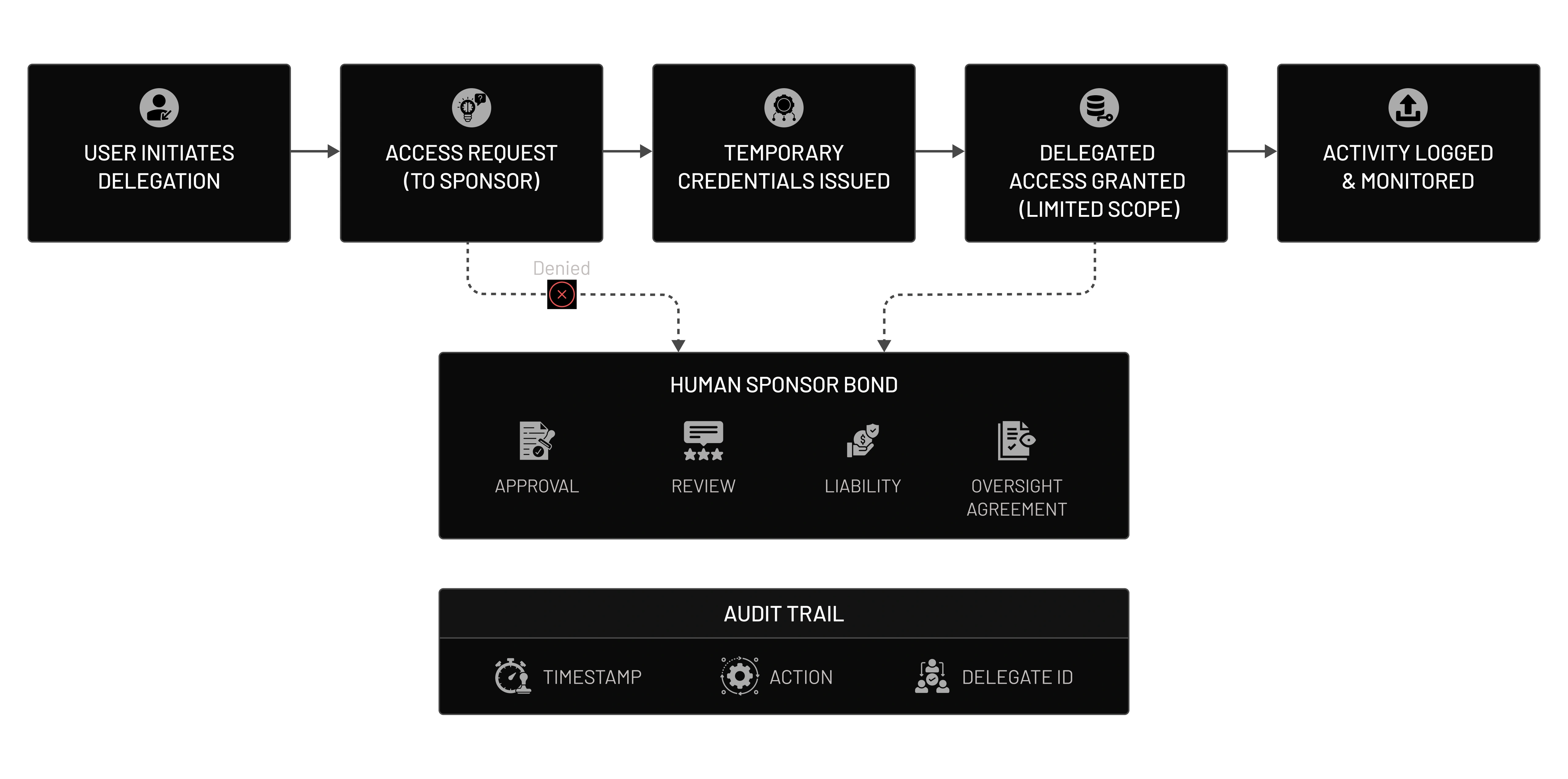
How Delegation & the Human-Sponsor Bond Work?
Delegation is best treated as token-based delegated access, where a resource owner authorizes a client to access resources via access tokens without sharing credentials. This is the core idea behind OAuth 2.0 delegated access.
From there, the “human-sponsor bond” is maintained by making delegation explicit, reviewable, and revocable through consent records, governance APIs, and audit logs tied to actions.
Delegation Pillars
Agentic IAM Pillar
What It Covers
Why It Matters
What It Covers
Delegated access patterns using access tokens so an agent can call APIs “on behalf of” a user or sponsor without ever handling passwords.
Why It Matters
Preserves the human sponsor as the authority while enabling agents to execute tasks safely and repeatedly.
Delegated access patterns using access tokens so an agent can call APIs “on behalf of” a user or sponsor without ever handling passwords.
Preserves the human sponsor as the authority while enabling agents to execute tasks safely and repeatedly.
What It Covers
Capture who consented, when, what they consented to, and keep an audit of consent changes; support consent submission, updates, verification, and logs via APIs.
Why It Matters
Turns “permission” into an enforceable record so you can prove authorization, not just assume it.
Capture who consented, when, what they consented to, and keep an audit of consent changes; support consent submission, updates, verification, and logs via APIs.
Turns “permission” into an enforceable record so you can prove authorization, not just assume it.
What It Covers
Risk-based evaluation (adaptive authentication) that can trigger additional actions like notifying users/admins when behavior looks anomalous.
Why It Matters
Enables human-in-the-loop where it matters most, without slowing down every low-risk action.
Risk-based evaluation (adaptive authentication) that can trigger additional actions like notifying users/admins when behavior looks anomalous.
Enables human-in-the-loop where it matters most, without slowing down every low-risk action.
What It Covers
Role/permission models and delegated admin controls so the right people can manage access without role explosion.
Why It Matters
Keeps delegation manageable at scale especially across partners, orgs, and agent fleets.
Role/permission models and delegated admin controls so the right people can manage access without role explosion.
Keeps delegation manageable at scale especially across partners, orgs, and agent fleets.
What It Covers
Extensive logging for platform interactions and team activity; API-level audit logs that can sync to SIEM tools for “who/when/how” visibility.
Why It Matters
Makes the human-sponsor bond provable every decision and action can be traced and reviewed.
Extensive logging for platform interactions and team activity; API-level audit logs that can sync to SIEM tools for “who/when/how” visibility.
Makes the human-sponsor bond provable every decision and action can be traced and reviewed.