Data Privacy & Compliance – What, How, Why, When
Data Privacy & Compliance defines how customer identity data is collected, stored, processed, and governed in line with global regulations. In modern CIAM systems, privacy is not an afterthought; it is embedded directly into identity architecture, user flows, and governance controls.

What is Data Privacy & Compliance in CIAM?
Data Privacy & Compliance in CIAM refers to the frameworks, controls, and policies that ensure customer identity data is handled lawfully, transparently, and securely across its entire lifecycle.
It is built around regulatory requirements such as GDPR and CCPA, and operationalized through consent management, data minimization, access governance, and auditable identity systems. A compliant CIAM platform acts as the system of record for customer permissions, preferences, and privacy rights.
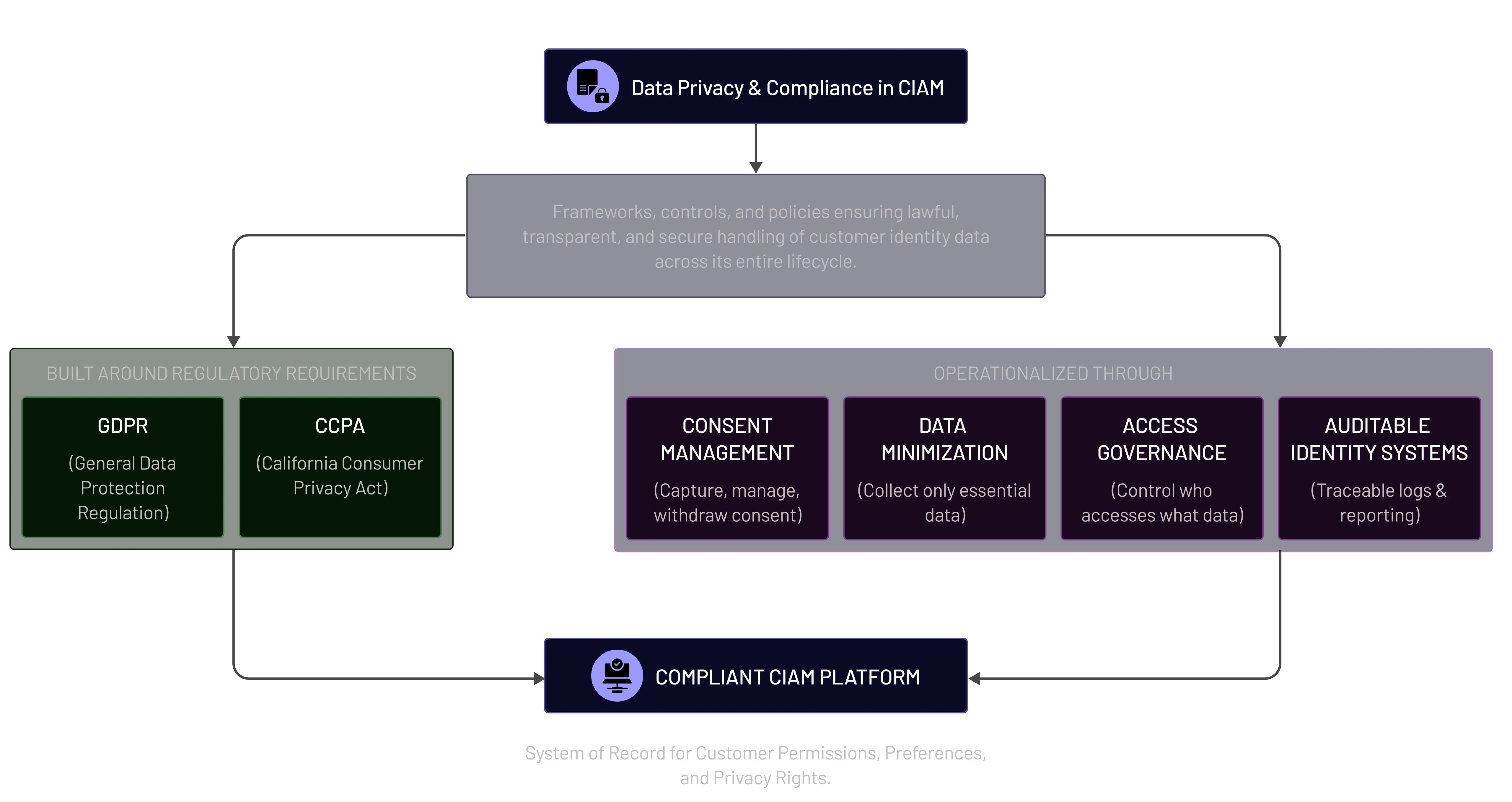
Core Pillars of Data Privacy & Compliance in CIAM
Privacy-First CIAM vs Legacy Identity Systems
Why legacy identity systems fall short of modern privacy and compliance requirements?