User Authentication & Account Security
Ensuring that every user interaction — from the first login to every action taken within an active session — is trustworthy, intentional, and protected.
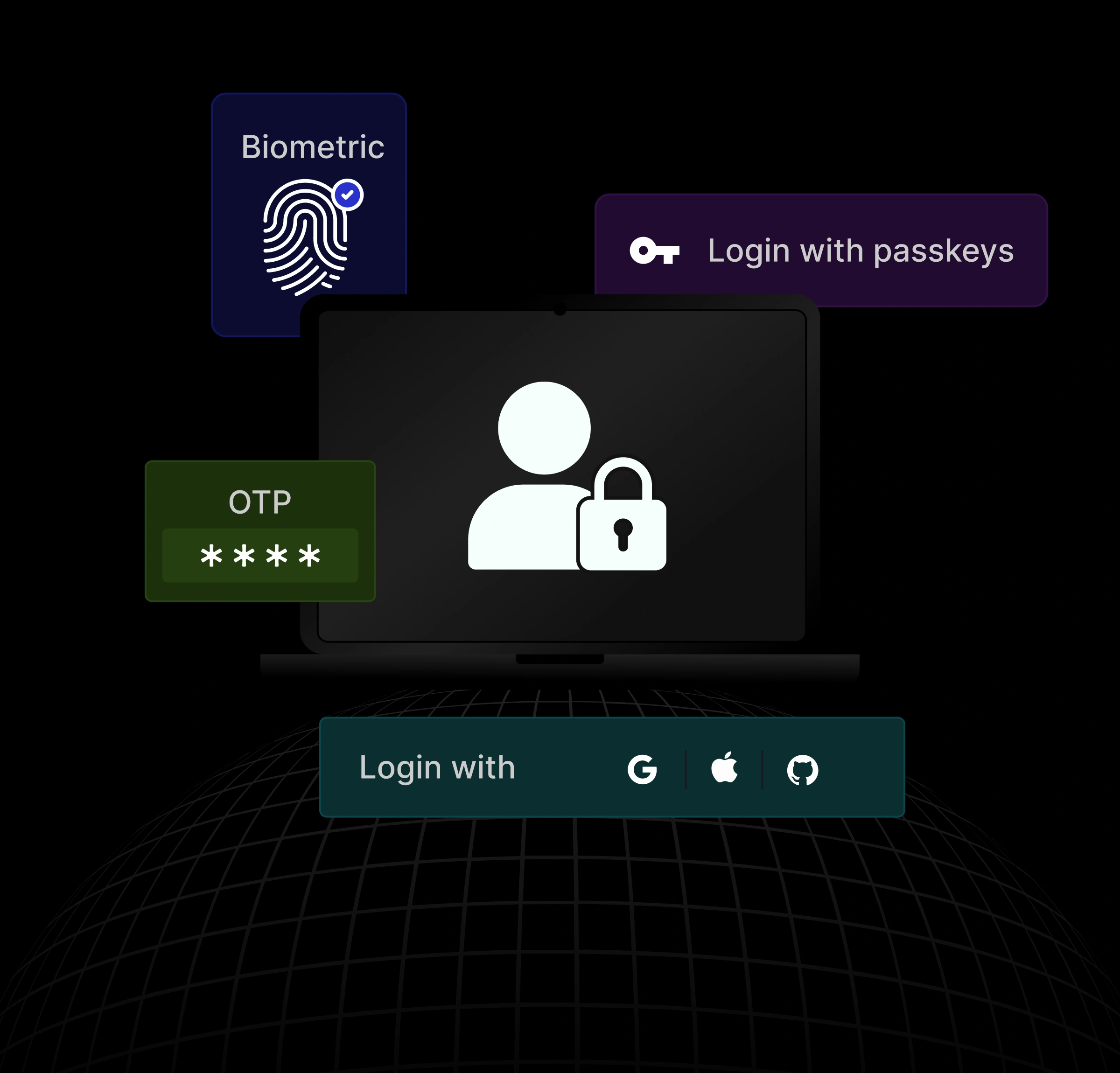
What is User Authentication?
User authentication is the process of verifying that a person trying to access an application is who they claim to be. At its core, authentication answers one question: “Are you really this user?”In modern systems, user authentication is no longer a single password check. It typically uses strong, layered methods, such as multi-factor authentication (MFA), passkeys, or passwordless flows, and relies on standardized protocols like OAuth 2.0 and OpenID Connect to authenticate users securely without exposing credentials to applications.



Account Security & Session Management - What & How
Protect user accounts and active sessions from takeover, misuse, and unauthorized access — even after users are signed in.
Account Protection
Secure user accounts against credential abuse and unauthorized changes using layered security controls.- Prevent account takeover (ATO) and credential stuffing
- Enforce strong authentication and recovery protections
- Monitor account-level activity for suspicious behavior
Secure Session Management
Control how long users stay signed in and how sessions behave across devices and environments.- Manage session lifetimes and inactivity timeouts
- Revoke sessions instantly when risk is detected
- Protect against session hijacking and fixation
Token & Access Control
Limit what authenticated users and sessions can access using scoped, short-lived credentials.- Issue short-lived access tokens and rotate refresh tokens
- Restrict access using scopes and permissions
- Reduce impact of leaked or compromised tokens
Risk-Based Session Protection
Continuously evaluate session risk and respond in real time.- Detect anomalies during active sessions
- Trigger step-up authentication for sensitive actions
- Terminate sessions automatically when risk increases
Key Capabilities for User Auth & Security
Capability
What It Does
When It’s Applied
Risk It Mitigates
Typical Signals / Controls
What It Does
Adds additional verification factors beyond passwords to confirm user identity.
When It’s Applied
At login or during sensitive actions.
Risk It Mitigates
Credential theft, brute-force attacks.
Typical Signals / Controls
OTP, push approval, hardware keys, biometrics.
Adds additional verification factors beyond passwords to confirm user identity.
At login or during sensitive actions.
Credential theft, brute-force attacks.
OTP, push approval, hardware keys, biometrics.
What It Does
Dynamically adjusts authentication requirements based on real-time risk.
When It’s Applied
Before or during session activity.
Risk It Mitigates
Stolen credentials, anomalous access.
Typical Signals / Controls
Device fingerprint, IP reputation, geo-velocity, behavior patterns.
Dynamically adjusts authentication requirements based on real-time risk.
Before or during session activity.
Stolen credentials, anomalous access.
Device fingerprint, IP reputation, geo-velocity, behavior patterns.
What It Does
Requires stronger verification when risk increases or sensitive actions are requested.
When It’s Applied
Mid-session, on high-risk actions.
Risk It Mitigates
Privilege abuse, lateral movement.
Typical Signals / Controls
Transaction value, role change, data access scope.
Requires stronger verification when risk increases or sensitive actions are requested.
Mid-session, on high-risk actions.
Privilege abuse, lateral movement.
Transaction value, role change, data access scope.
What It Does
Controls issuance, scope, rotation, and expiration of access tokens.
When It’s Applied
Throughout session lifecycle.
Risk It Mitigates
Token replay, API abuse.
Typical Signals / Controls
Short-lived access tokens, refresh token rotation, scope restriction.
Controls issuance, scope, rotation, and expiration of access tokens.
Throughout session lifecycle.
Token replay, API abuse.
Short-lived access tokens, refresh token rotation, scope restriction.
What It Does
Manages session duration, inactivity, and revocation.
When It’s Applied
After authentication, continuously.
Risk It Mitigates
Session hijacking, unauthorized persistence.
Typical Signals / Controls
Idle timeout, absolute timeout, global logout.
Manages session duration, inactivity, and revocation.
After authentication, continuously.
Session hijacking, unauthorized persistence.
Idle timeout, absolute timeout, global logout.
What It Does
Monitors session behavior to identify abnormal or malicious patterns.
When It’s Applied
Continuously during sessions.
Risk It Mitigates
Fraudulent transactions, automation abuse.
Typical Signals / Controls
Impossible travel, unusual request rates, behavior deviation.
Monitors session behavior to identify abnormal or malicious patterns.
Continuously during sessions.
Fraudulent transactions, automation abuse.
Impossible travel, unusual request rates, behavior deviation.
What It Does
Combines authentication, session control, and monitoring to block takeovers.
When It’s Applied
Across login and active sessions.
Risk It Mitigates
Full account compromise.
Typical Signals / Controls
Credential stuffing detection, session anomaly detection.
Combines authentication, session control, and monitoring to block takeovers.
Across login and active sessions.
Full account compromise.
Credential stuffing detection, session anomaly detection.
Zero Trust for Customer Identity
Zero Trust is a security approach that assumes no user or device is inherently trusted. Every access request is continuously verified based on identity, context, and risk—protecting customer accounts while keeping experiences seamless.
Continuous Verification : Authenticate users and devices at every interaction, not just at login.

Adaptive Authentication : Trigger MFA or step-up verification dynamically based on risk signals.

Least-Privilege Access : Grant users only the minimum permissions needed for their actions.
Context & Risk Awareness : Consider device trust, location, behavior, and anomalies for every access decision.