Hey there!
Ever wonder who really controls your personal information when you sign up for a new website or app? We all share a lot of data online—our emails, our birthdays, where we live, and what we like to buy.
But just giving away your data isn't the whole story. The smart companies know that building trust is the secret ingredient for keeping customers. And trust, in the digital world, means giving you control.
That's where Identity Governance in CIAM comes in.
CIAM stands for Consumer Identity and Access Management. Think of it as the system that handles all your customer sign-ups, logins, and profile details. Identity Governance is the set of rules, policies, and tools that make sure that the whole system is running ethically, securely, and legally.
If you’ve been following our series on Identity Governance and Administration (IGA), you know how important it is for employees. But for your customers? It’s even more critical because the rules (like the laws) are much stricter.
This blog is your pillar guide to the five big ideas behind modern Identity Governance in CIAM: Consent, Privacy, Approvals, Sharing, and Compliance.
Why Governance Matters in Consumer Identity (CIAM)
CIAM deals with millions of people, not just a few hundred employees. This big difference makes the stakes much higher. Governance is essential in CIAM for three main reasons:
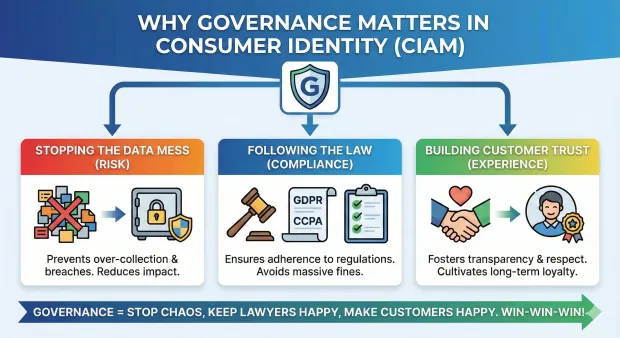
-
Stoping the Data Mess (Risk): Without clear rules, companies end up collecting data they don't need, storing it forever, and letting too many people see it. This is a huge risk! If a data breach happens, the more data they have, the worse the problem is.
-
Following the Law (Compliance): Laws like GDPR (Europe) and CCPA (California) are very clear: customers have rights over their data. If a company messes up, the fines are massive. Governance is the framework to make sure those fines never happen.
-
Building Customer Trust (Experience): When you feel a company respects your privacy, you're more likely to keep using their service. Governance ensures a transparent, respectful, and controlled relationship, which turns into long-term customer loyalty.
In short, governance stops the chaos, keeps the lawyers happy, and makes the customer happy. That’s a win-win-win!
🤝 Consent Management: The Heart of Privacy
Consent isn't just a box you tick on a form. In modern privacy laws, it's a deep, meaningful agreement.
Purpose-Based Consent: Know What You’re Saying Yes To
You wouldn't let a friend borrow your car just to move their entire house, right? The same is true for data.
Purpose-based consent means that a company must ask for your permission for each specific thing they want to do with your data.
-
They need your email to send you a shipping update? They must ask for shipping updates.
-
They want to use your purchase history to suggest new products? They must ask for personalized marketing.
You should be able to say "Yes" to shipping updates and "No, thanks" to marketing, all in one place—a Preference Center. This level of detail shows respect.
Timestamping Your Choices
Have you ever wondered if an online form changed after you signed it?
In identity governance, every piece of consent needs a digital receipt. This is called timestamping. The system must record:
-
What you agreed to (e.g., “I consent to email marketing”).
-
When you agreed (e.g., October 25, 2025, at 10:15 AM EST).
-
What version of the privacy policy did you saw?
This is critical for audits. If a government regulator asks for proof that a company got your consent, the timestamped record is the unshakeable evidence.
👨👩👧👦 Parental Consent: Protecting the Youngest Users
When kids under a certain age use an online service, the rules get even stricter. Here in the U.S., the most well-known law is COPPA—the Children's Online Privacy Protection Act.
COPPA and similar international laws say that for services directed at children under 13, the company must get verifiable parental consent before collecting any personal information.
This isn't just a checkbox; it often requires a more serious step, like:
-
Signing a consent form that is then scanned.
-
Paying a small, refundable fee with a credit card (proving you're an adult).
-
Connecting with a trained representative by video or phone.
CIAM systems must be smart enough to recognize a young user, block the collection of their personal data, and start a formal parental consent workflow. Getting this wrong can lead to major legal trouble and is a serious breach of trust.
⚙️ Identity Approval Workflows: The "Who Gets Access?" Rules
While a customer is busy using your service, behind the scenes, internal teams—like Customer Support, Marketing, and Fraud Protection—might need to see their data. Identity Governance manages this with Approval Workflows.
Think of it like getting a key: you need a good reason, and your manager has to sign off.
For a CIAM platform, a good workflow means:
-
The Request: A support agent needs to see a customer’s login history to help them with a security issue. They submit a formal request inside the identity platform.
-
The Approval: Their manager or the compliance officer gets an alert and either approves or denies the request based on their role and policy.
-
The Time Limit: The access is only granted for a specific, short period (e.g., 4 hours). After that, the "key" automatically expires.
-
The Audit: Every step—who asked, who approved, when they looked, and for how long—is logged in a permanent audit trail.
This ensures that access to sensitive customer data is always on a need-to-know basis, heavily controlled, and completely transparent for audits.
🗺️ Identity Data Residency & Data Minimization
These two concepts are about where you keep the data and how much of it you keep.
Data Residency
Data Residency simply means the geographical location where customer data is stored. Why does this matter? Because different countries have different privacy laws.
For example, the GDPR requires that the personal data of European citizens largely stays inside the European Economic Area (EEA).
A proper CIAM governance solution allows companies to meet these laws by:
-
Geo-Segmentation: Automatically storing the data of a French customer on a server in France (or the EU) and the data of a Japanese customer on a server in Japan.
-
Access Control by Location: Ensuring that only specific, authorized personnel in a given region can access that regional data.
Data Minimization
This is a powerful concept: If you don’t need the data, don’t collect it!
-
A clothing retailer selling a T-shirt doesn't need to know the customer's political preference.
-
A blog only needs your email for a subscription; it doesn't need your phone number.
Data minimization means companies:
-
Collect only the essentials. (e.g., just an email address for a newsletter).
-
Delete it when it's no longer needed. (e.g., deleting payment data after a transaction is complete and the legal hold period is over).
This practice significantly lowers the risk because if a data breach occurs, there’s simply less sensitive information for a hacker to steal.
🗑️ Revocation and the Right-to-Be-Forgotten (RTBF)
In the past, once your data was with a company, it was basically theirs forever. Not anymore. Modern privacy laws have given customers two critical rights.
Consent Revocation
This is your right to simply change your mind. If you gave consent to email marketing last year, you must be able to withdraw (revoke) that consent today easily.
-
A good CIAM system makes this simple with a self-service Preference Center.
-
The moment you opt-out, the system automatically stops sharing your data with the marketing tools. This change must be instant and effective immediately.
The Right-to-Be-Forgotten (RTBF)
Also known as the Right to Erasure, this is the digital equivalent of wiping the slate clean. You have the right to ask a company to delete all your personal data from their systems.
While it’s not an absolute right (companies can sometimes hold onto data if a law requires them to, like a tax record), in most cases, a company must delete:
-
Your user profile.
-
Your login history.
-
Any connected marketing or analytics data.
A governance-focused CIAM platform makes sure this deletion is carried out across all connected systems, proving that the user is truly "forgotten" and providing the customer with a confirmation of deletion for the audit trail.
🧑💻 Customer-Controlled Data Sharing
Imagine a future where you, the customer, are the gatekeeper for your own data. This is what customer-controlled data sharing is all about.
When you sign up for two different services from the same parent company, do you really want to fill out your name and address twice? Probably not.
Identity Governance allows for a trust framework where:
-
You log in to App A.
-
You then go to App B (which is also owned by the same company).
-
Instead of automatically sharing your data, App B asks you for permission: "App B would like to use your name and email from App A to create your new account. Do you approve?"
You click Yes, and the data is shared instantly and securely. This gives you fine-grained control, meaning you decide exactly what information is shared between different parts of the company or even with third-party partners. It’s transparent, respectful, and fully auditable.
✅ LoginRadius's Compliance Stance: Built for Global Trust
As a leading CIAM platform, we know that technology is only as good as the trust it inspires. Our entire platform is built with Identity Governance at its core, so you can focus on your business, not on complex compliance checks.
We are a compliance-ready platform that adheres to major global and regional standards, including:
-
GDPR: Full support for consent management, RTBF, data portability, and purpose-based processing.
-
CCPA/CPRA: Ensuring California residents have control over the sale of their personal information.
-
HIPAA: Providing a secure framework for healthcare providers dealing with sensitive patient information.
-
COPPA: Tools for implementing verifiable parental consent workflows.
-
ISO/IEC 27001, SOC 2 Type II: Independent third-party audits confirming our security, availability, and confidentiality controls are world-class.
Our goal is to give you the tools—like the Preference Center, Geo-Data Residency options, and automated Approval Workflows—so you can easily respect your customers' rights and maintain global compliance.
Check the complete list of compliances that LoginRadius adheres to.
In Conclusion: Governing Identity is Governing Trust
The digital world is all about relationships, and the foundation of any strong relationship is trust.
Identity Governance in CIAM is how a company proves they deserve that trust. It’s the framework that moves a business from just collecting data to actively respecting it. By focusing on purposeful consent, strong approval processes, data minimization, and honoring the Right-to-Be-Forgotten, you don’t just comply with the law—you build a loyal customer base that feels respected and safe.
📞 Take the Next Step
Ready to move beyond basic security and build a CIAM strategy that drives compliance and customer loyalty?
Talk to our Identity Governance experts today! We can show you how to set up a world-class CIAM platform with automated workflows for consent, parental approval, and the Right-to-Be-Forgotten, all while ensuring compliance across every global market you serve.
FAQs
Q1: What is the main difference between CIAM and IAM?
A: IAM (Identity and Access Management) is mainly for a company's employees. It controls who in the office can access internal systems and data. CIAM (Consumer Identity and Access Management) is for a company's customers. It manages user sign-ups, logins, and profiles for public-facing websites and apps. CIAM is much more focused on high-volume scalability, frictionless user experience, and strict data privacy/governance laws.
Q2: Does the "Right-to-Be-Forgotten" mean a company has to delete my data instantly?
A: Companies must erase the data "without undue delay," which usually means within 30 days. However, it is not absolute. They can refuse to delete your data if they have a legal obligation to keep it (like tax records, transaction history for fraud prevention, or data needed for a legal claim). But even then, they must tell you why they can't delete it.
Q3: How does Purpose-Based Consent help my business?
A: It actually helps build a better customer profile! When you ask a customer to opt-in for specific purposes, you get higher-quality data and better engagement. Customers who opt-in to personalized offers are genuinely interested, making your marketing budget more effective. It also drastically reduces the risk of fines by making your compliance instantly auditable.
Q4: What is the risk of not implementing Identity Approval Workflows?
A: The biggest risk is a data breach from the inside or a major compliance violation. Without workflows, a simple customer support agent might have unlimited, unchecked access to highly sensitive customer data (like passwords, payment details, or private communication). This is an open door for misuse, mistakes, and legal non-compliance, which could lead to huge fines and a loss of customer trust.


