Introduction
Most organizations believe their data is secure because access is “restricted.” Users log in. Roles are assigned. Dashboards appear or disappear exactly as designed.
And yet data exposure keeps happening.
Not because teams ignore security, but because RBAC security is often implemented only at the surface level. The system knows who you are, but it doesn’t always know what data you should actually see once you’re inside.
Here’s the uncomfortable truth: In modern applications, data is the product. Customer records, financial fields, usage logs, medical attributes, partner data, this is what attackers want, and this is what compliance teams worry about. Controlling access to a screen or API endpoint is no longer enough.
This is where many teams misunderstand what role-based access control is in practice.
RBAC isn’t just about allowing or denying entry. It’s about controlling visibility down to individual records and sensitive fields. Without that depth, RBAC becomes a checkbox exercise rather than a real data security strategy.
A surprising pattern we’ve seen across SaaS, healthcare, finance, and enterprise platforms is this: Teams often implement a solid RBAC model for objects, but leave rows and fields wide open. Everyone with “read access” sees far more than they should. Over time, that turns into over-permissioning, audit failures, and data leaks that are hard to explain after the fact.
This blog takes a practical look at RBAC in data security, focusing on how object-level, row-level, and field-level access control work together. No theory overload. No textbook framing. Just how RBAC is actually used and misused in real systems today.
Whether you’re trying to understand what is RBAC in security for the first time or you’re refining a production-grade authorization model, this guide will help you see where RBAC truly protects data and where it quietly falls short.
What Is Role-Based Access Control (RBAC)?
At its core, RBAC is a way to manage access by grouping permissions into roles that reflect real responsibilities inside an organization. Instead of deciding what every individual user can do, systems define what a role can do, and users inherit those permissions by holding that role.
This is why role-based access control RBAC often comes up in enterprise security conversations. It replaces ad-hoc access decisions with structure. A support agent, a finance analyst, and an administrator don’t need custom rules written for each person. Their job function already defines the boundaries.
From a security perspective, what is RBAC in security isn’t just about convenience. It’s about control at scale. When implemented correctly, RBAC reduces permission sprawl, simplifies audits, and makes access behavior predictable.
But RBAC is often misunderstood as a “set it and forget it” model. In reality, the RBAC model only works when roles are intentionally designed and continuously reviewed. Otherwise, roles turn into permission buckets that quietly grow until everyone sees more than they should.
RBAC in Cyber Security Is About Data, Not Just Screens
Here’s where many RBAC implementations drift off course.
Teams design roles around user interfaces that can open which dashboard, and who can click which button. That works for usability, but it falls short for RBAC cybersecurity.
Attackers don’t care about dashboards. They care about data.
Real security questions sound more like:
-
Can this role access customer records from other tenants?
-
Can this role see financial fields it doesn’t need?
-
Can this role export raw data without restriction?
This is why role-based security must extend beyond screen-level access. RBAC should define not just what applications a role can reach, but what data the role is allowed to interact with once inside.
When RBAC is limited to UI control, sensitive data often becomes exposed through APIs, exports, reports, or background jobs. That’s not a failure of RBAC as a concept, it's a failure of depth.
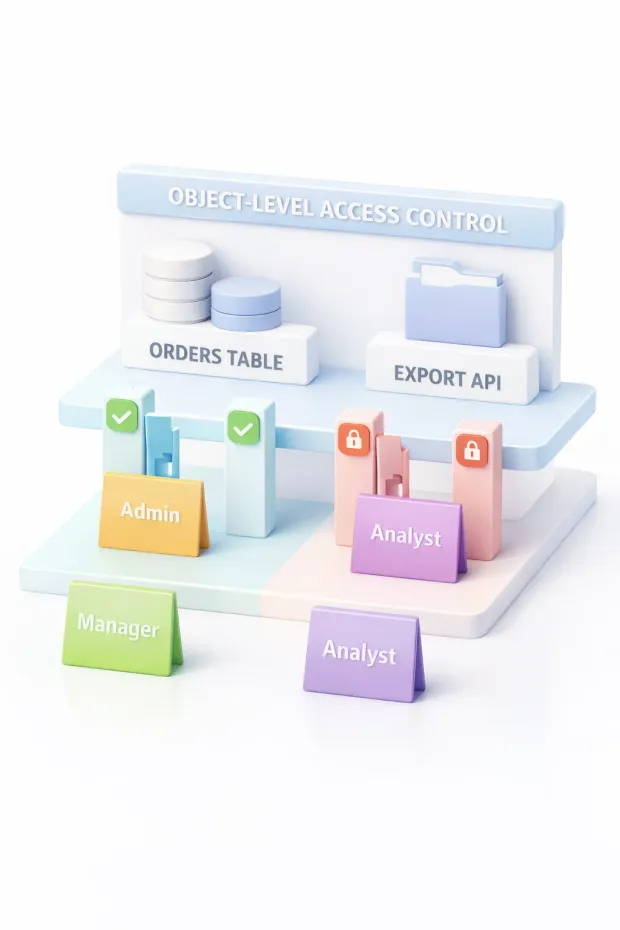
Object-Level Access Control: The First Gate
Object-level access control is where most RBAC implementations begin and sometimes where they end.
It determines whether a role can access a specific object: a database table, an API endpoint, a service, or a system feature. This layer answers the basic question: Should this role even be here?
A simple RBAC model example might look like this:
-
A Support role can access the Orders object
-
A Finance role can access the Invoices object
-
An Admin role can access everything
For beginners, this is the easiest RBAC layer to understand. For experts, it’s the foundation everything else depends on.
But object-level control only defines entry, not scope. Once a role is allowed to access an object, it doesn’t automatically mean every record or every field inside that object should be visible.
That’s why object-level RBAC is necessary but never sufficient for strong data security.
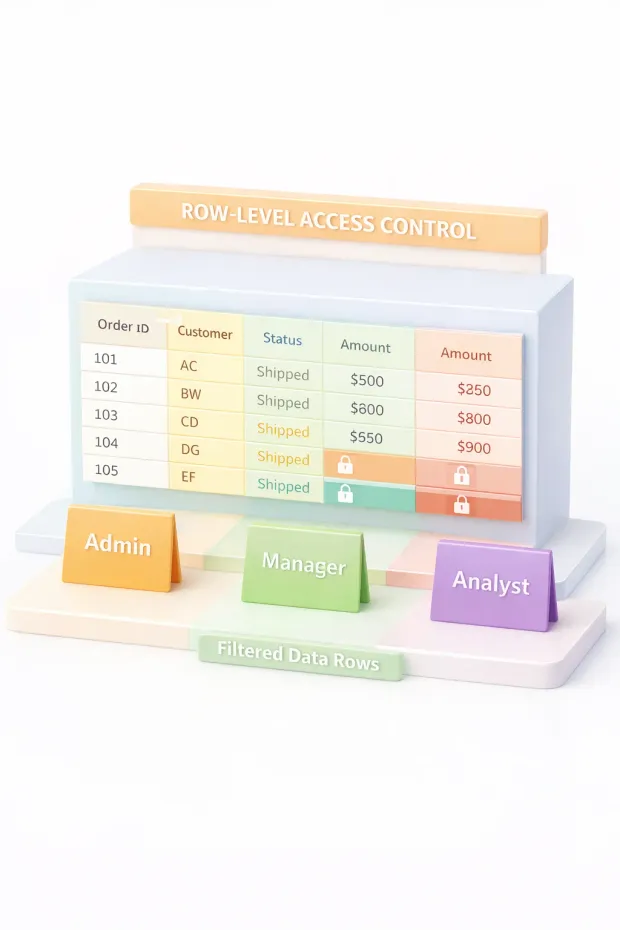
Row-Level Access Control: Same Table, Different Truth
Row-level access control solves a problem that object-level RBAC can’t.
Even when two users are allowed to access the same table or resource, they often shouldn’t see the same data inside it. This is where row-level security becomes critical.
Row-level access control restricts visibility based on conditions such as ownership, tenant boundaries, or organizational scope. A user may query the same table as another user, but receive a completely different result set.
In practice, this shows up everywhere:
-
A SaaS customer sees only their own tenant’s data
-
A manager sees records for their team, not the entire company
-
A regional user sees records tied to their geography
From a what is RBAC in cybersecurity standpoint, row-level rules prevent horizontal data exposure. Without them, RBAC roles tend to become overly broad, especially as systems scale.
This is also where teams start to feel RBAC’s limitations. Context creeps in. Conditions matter. Ownership logic grows complex. But skipping row-level control altogether is far more dangerous than managing that complexity.
Field-Level Access Control: Where Breaches Get Expensive
Field-level access control is the most overlooked and often the most critical layer of RBAC.
It answers a question many teams avoid asking: Even if a role can see this record, should it see every detail inside it?
Sensitive fields like personal identifiers, financial data, credentials, or health information rarely need to be visible to everyone with record-level access. Field-level control ensures that exposure is intentional, not accidental.
For example:
-
Support staff may see account status but not payment details
-
Managers may see salary bands but not exact compensation
-
Compliance teams may see full records that others can’t
This is where RBAC security directly intersects with compliance, privacy laws, and breach impact. Most high-profile data incidents don’t happen because someone accessed the wrong table they happen because someone accessed too much detail within the right one.
Strong role-based access control models treat field-level permissions as first-class citizens, not afterthoughts. When this layer is ignored, RBAC becomes coarse-grained, and sensitive data exposure becomes a matter of time not chance.

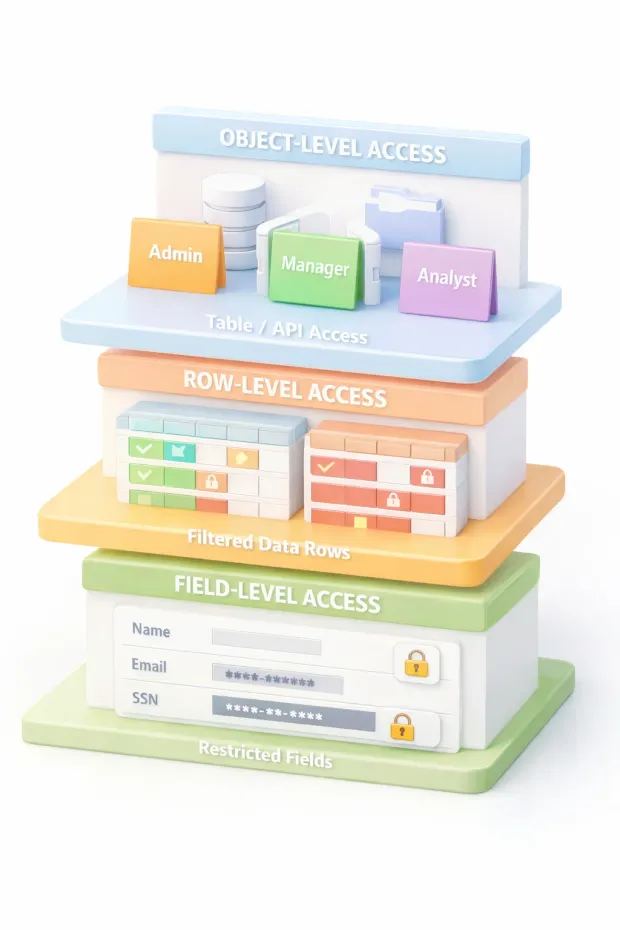
How These Three Layers Work Together
RBAC becomes truly effective when object-level, row-level, and field-level controls operate as a single decision chain, not as isolated rules scattered across systems.
Here’s how access is actually granted in well-designed environments.
First, object-level access control answers the simplest question: Is this role allowed to access this resource at all? If the answer is no, the request stops immediately. No queries run. No data moves.
Once that gate is passed, row-level access control narrows the scope. The role may be allowed to access the table or service, but only specific records qualify. Ownership, tenant boundaries, organizational structure, or regional rules determine what data even exists for that user.
Finally, field-level access control trims the response down to what’s strictly necessary. Sensitive attributes are hidden, masked, or excluded entirely based on role responsibility, not convenience.
The key point is this: RBAC doesn’t make a single yes-or-no decision. It makes a sequence of narrowing decisions.
When these layers are aligned, RBAC security feels invisible to users but highly intentional to auditors. When they aren’t, systems either leak data or become so restrictive that teams bypass controls altogether.
Where Teams Usually Go Wrong With RBAC Security
Most RBAC failures don’t happen because teams misunderstand the model. They happen because RBAC is treated as a one-time setup rather than a living system.
Here’s the pattern that repeats itself.
Roles are created quickly to meet immediate needs. A new team launches. A partner is onboarded. An internal project needs access “just for a few weeks.” Permissions are added, rarely removed, and almost never revisited.
Over time, roles drift away from their original purpose. Support roles gain export access. Admin-like permissions sneak into operational roles. Temporary access becomes permanent by default.
This is where RBAC security quietly erodes.
Another common issue is stopping at object-level control. Teams feel confident because users can’t access the wrong services, but inside those services, data boundaries are vague or nonexistent. Rows aren’t filtered. Fields aren’t restricted. Everything technically works until someone notices they can see far more than expected.
RBAC doesn’t break because it’s outdated. It breaks because governance is skipped once things seem “stable.”
RBAC vs Context-Aware Models (ABAC & PBAC)
RBAC was designed to answer a stable question: What is someone allowed to do based on their role? That question still matters and it still holds up well.
But modern systems often need to answer additional questions:
-
Is this access happening from a trusted device?
-
Is the request coming from a risky location?
-
Is the data sensitive enough to require stricter conditions right now?
This is where context-aware models like ABAC (Attribute-Based Access Control) and PBAC (Policy-Based Access Control) enter the picture.
Here’s the important part: These models don’t replace RBAC. They extend it.
RBAC defines who you are in the system. Context defines whether this moment is appropriate.
In practice, RBAC remains the backbone. It keeps access predictable, explainable, and auditable. Context-aware controls layer on top to handle risk, variability, and edge cases without exploding the number of roles.
Teams that try to skip RBAC entirely often end up rebuilding it implicitly, just with more complexity and less clarity.
Why RBAC Still Matters in Modern Data Security
Despite newer access models and zero-trust conversations, RBAC still remains one of the most reliable foundations in data security.
There’s a simple reason for that.
RBAC maps cleanly to how organizations think. Job functions exist. Responsibilities differ. Accountability matters. When access aligns with roles, security decisions become understandable, not just enforceable.
From a data security perspective, RBAC excels at setting clear boundaries. It defines what should never be accessible to certain roles, regardless of context. That clarity is critical when protecting sensitive data at scale.
Modern systems haven’t outgrown RBAC. They’ve outgrown shallow RBAC.
When RBAC is extended into row-level and field-level controls and supported by governance, it remains a powerful, durable model. One that auditors can trace, teams can reason about, and systems can enforce consistently.
RBAC still matters because security isn’t just about reacting to risk. It’s about designing access that makes misuse difficult by default.
Conclusion
RBAC doesn’t usually fail loudly. It fails quietly.
Systems keep running. Users keep working. Reports keep loading. And somewhere in the background, roles slowly accumulate permissions they were never meant to have.
That’s the real risk in RBAC cybersecurity, not broken logic, but unchecked expansion.
When RBAC is treated as a UI-level control, it creates a false sense of safety. Users may only see the screens they’re supposed to, but behind those screens, rows and fields often remain exposed. That gap is where sensitive data leaks, compliance issues surface, and trust erodes.
Strong role-based security goes deeper. Together, these layers turn RBAC from a permissions framework into a data protection strategy.
The most effective teams don’t abandon RBAC when systems grow more complex. They reinforce it. They pair a clear RBAC model with thoughtful governance, periodic reviews, and fine-grained data controls that reflect real business boundaries.
If there’s one takeaway to remember, it’s this: RBAC is only as strong as the deepest layer it enforces.
Secure the data not just the doors and RBAC becomes what it was always meant to be: a reliable foundation for modern data security. Book a Demo today.
FAQs
Q: What is RBAC in security?
A: RBAC in security controls access by assigning permissions to roles instead of individual users. This makes access predictable, auditable, and easier to manage as systems and teams scale.
Q: How is RBAC used for data security?
A: RBAC secures data by controlling access at multiple layers—object-level, row-level, and field-level. This ensures users see only the data their role genuinely requires.
Q: What is the difference between object-level and row-level access control?
A: Object-level access determines whether a role can access a resource at all. Row-level access filters which specific records within that resource are visible to the user.
Q: Is RBAC enough on its own for modern applications?
A: RBAC works well as a foundation, but modern systems often combine it with context-aware controls like ABAC or PBAC to handle risk, location, and sensitivity without creating too many roles.


