Introduction
Access control is rarely the thing teams plan to rethink. It usually works. Until it doesn’t.
Most SaaS products start with RBAC because it feels obvious. You define roles. You assign permissions. You move on. Early customers understand it. Admins can reason about it. Security teams can explain it during reviews. From the outside, everything looks under control.
But something subtle happens as products mature.
Users don’t just exist in the system anymore. They collaborate. They invite others. They share projects. They inherit access through teams, organizations, folders, workspaces, and environments. Suddenly, access is no longer about who someone is, but how they are connected to something.
That’s the moment when the RBAC vs ReBAC conversation starts showing up in architecture meetings.
Not because RBAC is broken.
Not because ReBAC is trendy.
But because the product itself has changed shape.
Here’s a pattern many teams recognize: roles keep growing, permissions get copied across services, and access logic starts leaking into application code. Engineers add condition after condition. Support tickets rise. Someone eventually asks, “Can we actually explain why this user has access?”
That’s not a failure of RBAC. It’s a signal that the authorization problem has shifted.
This is where relationship-based access control enters the picture, not as a replacement, but as a response to modern SaaS realities. Collaboration-heavy products, multi-tenant platforms, partner ecosystems, and shared resources all push beyond what static roles were designed to express.
This blog isn’t about declaring a winner.
It’s about helping you understand when RBAC works beautifully, when ReBAC becomes necessary, and why most modern SaaS platforms quietly end up using both even if they don’t label it that way.
What is RBAC in security?
At its simplest, RBAC (Role-Based Access Control) is a way of deciding who can do what without having to think about every individual user.
Instead of assigning permissions directly to people, RBAC assigns permissions to roles and users inherit access by being placed into those roles. That small abstraction is what made RBAC one of the most widely adopted authorization models in security.
When people ask what is RBAC in security, they’re usually not looking for a theory. They want to know why it became the default. The answer is control. RBAC gives organizations a way to standardize access without constantly reinventing rules. Security teams define roles once. Engineering teams enforce them consistently. Everyone speaks the same language.
RBAC also fits naturally with how companies think about responsibility. Job functions already exist. RBAC simply maps digital permissions to them. That alignment between human structure and system structure is what makes RBAC feel intuitive even to non-technical stakeholders.
It doesn’t try to infer intent. It doesn’t analyze context. It just enforces clearly defined boundaries. And in many environments, that’s exactly what’s needed.
RBAC examples you see in almost every SaaS product
You’ve probably interacted with RBAC today without realizing it.
Workspace roles like Owner, Admin, Member, and Guest are classic RBAC examples. Each role carries a predefined set of permissions, and users gain access simply by being assigned the right label.
Billing access is another common case; only certain roles can update payment methods or view invoices. Support tooling often relies on RBAC to separate agents from administrators. Production environments usually restrict deployment access to a small group of trusted roles.
What makes these examples effective is consistency. The permissions don’t change based on context or relationships. They reflect responsibility, not situation. If someone is an Admin, they remain an Admin until that role is explicitly changed.
RBAC works best in these scenarios because access needs to be predictable. Users understand it. Admins can manage it without second-guessing. And support teams can explain it without diving into complex logic.
RBAC implementation: where it works and where it strains
A textbook RBAC implementation looks clean. You define a small set of permissions. You bundle them into roles. You assign users. Done.
In reality, things rarely stay that clean.
As products grow, RBAC starts absorbing edge cases. A customer asks for limited admin access. A feature needs partial permissions. Another team wants environment-specific control. Instead of revisiting the model, teams often respond by creating new roles.
This is where RBAC begins to strain not because it’s flawed, but because it’s being stretched beyond its original purpose. Roles multiply. Permissions overlap. Understanding why someone has access becomes harder than granting the access itself.
RBAC handles stable, organization-level authority extremely well. It struggles when access depends on dynamic conditions, shared resources, or inherited relationships. That tension is usually the first signal that RBAC is being asked to do more than it was designed for.
How RBAC solutions support compliance requirements
From a compliance perspective, RBAC is hard to beat.
Auditors want clarity. They want to know who has access, what that access allows, and how changes are controlled. RBAC provides clear answers to all three. Roles are explicit. Permissions are documented. Assignments can be reviewed and revoked in a structured way.
This is why how RBAC solutions support compliance requirements is rarely controversial. RBAC aligns naturally with principles like least privilege, separation of duties, and periodic access reviews. It produces clean audit trails and predictable governance workflows.
Even organizations that move toward more advanced authorization models often keep RBAC at the core of their compliance strategy. It gives security and risk teams something concrete to stand behind especially in regulated industries where explainability matters as much as enforcement.
RBAC may not solve every access problem, but when compliance enters the conversation, it remains one of the strongest foundations you can build on.
Relationship-Based Access Control explained without theory overload
Relationship-Based Access Control (ReBAC) exists because modern SaaS access patterns stopped being linear.
In early systems, access could be decided by answering one question: Who is this user?
In modern products, that question isn’t enough.
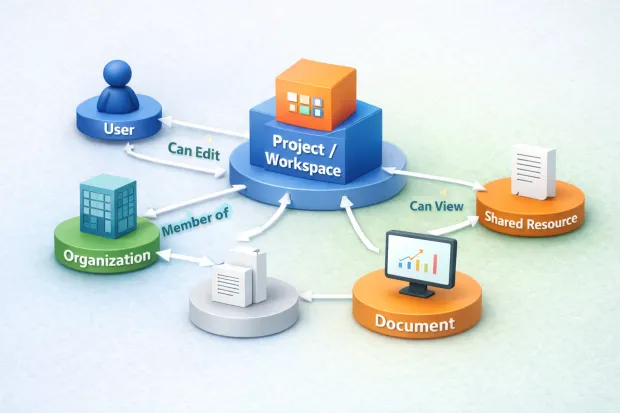
Today, access depends on connections. A user belongs to a team. That team belongs to an organization. That organization owns a project. The project contains files, dashboards, environments, or workflows. Whether someone can act on a specific resource depends on how those connections line up at that moment.
That’s all ReBAC really does.
It doesn’t ask what role someone has globally. It asks whether a valid relationship exists between the user and the thing they’re trying to access. If the relationship exists, access is granted. If it doesn’t, it isn’t.
What makes ReBAC powerful is that it mirrors how people already explain access in conversation.
“She can edit this because she’s on our team.”
“He can view this because he owns the account.”
No one says, “He can access this because he has Role X, Variant Y, with Exception Z.” ReBAC removes that translation gap between how humans think and how systems enforce permissions.
ReBAC vs RBAC: what actually changes in decision-making
The real difference between ReBAC vs RBAC isn’t philosophical. It shows up at runtime right when a system needs to decide whether an action is allowed.
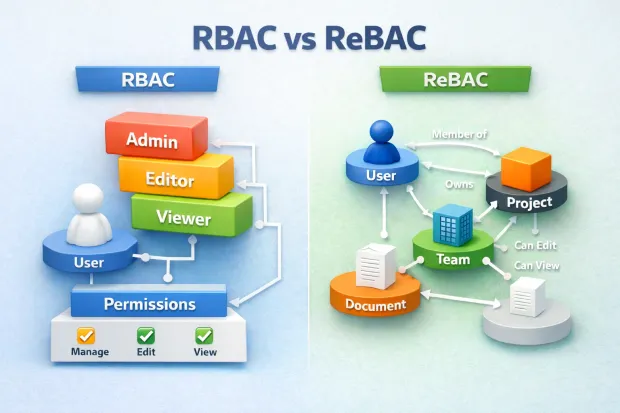
RBAC makes decisions based on classification. The system checks the user’s role and looks up the permissions tied to that role. The answer is static. If the role allows it, access is granted everywhere that role applies.
ReBAC makes decisions based on relationships. The system evaluates whether the user is connected to the specific resource in a meaningful way. The answer can change as relationships change even if the user’s identity remains the same.
This shift matters because products are no longer static environments. Users move between teams. Projects change ownership. Access needs to adapt without forcing administrators to constantly reconfigure roles.
RBAC answers who you are. ReBAC answers why you should have access right now.
That distinction becomes critical as products scale.
Where ReBAC naturally fits in modern SaaS apps
ReBAC feels inevitable in products built around collaboration.
Any SaaS platform that allows users to share resources documents, projects, dashboards, environments quickly runs into the limits of role-based thinking. Access becomes situational. Temporary. Inherited.
ReBAC fits naturally here because it doesn’t require predefining every possible scenario. When relationships change, access changes with them. When a user joins a team, they gain access. When they leave, access disappears without manual cleanup.
This is especially valuable in multi-tenant SaaS, partner ecosystems, and platforms that support delegated administration. Instead of creating special roles for every variation, ReBAC lets the product model real-world relationships directly.
When access feels intuitive to users and invisible to admins, ReBAC is usually doing the heavy lifting.
Where RBAC still wins clearly
Despite all this flexibility, RBAC remains essential and in some areas, superior.
Administrative access is the clearest example. Billing, security settings, user management, and system-wide configuration benefit from predictability. These permissions shouldn’t change dynamically based on relationships. They should be tightly controlled, easy to audit, and simple to explain.
RBAC also excels in environments where compliance and governance matter more than flexibility. Roles provide a shared language across security teams, auditors, and leadership. When someone asks who can access a sensitive function, RBAC gives a clean answer.
In practice, RBAC often governs the platform layer, while ReBAC governs the product layer. One establishes authority. The other enables interaction.
RBAC vs ABAC vs ReBAC: how teams actually combine them
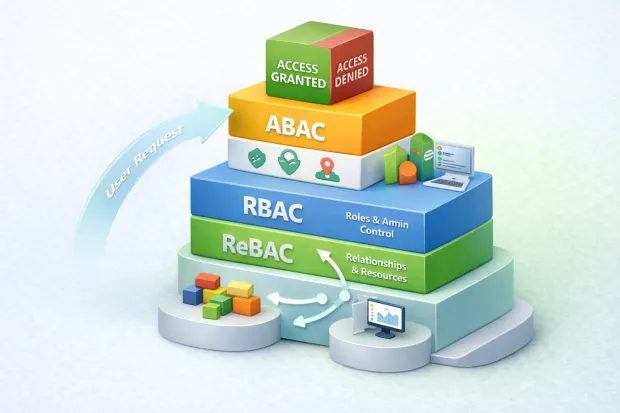
Discussions around RBAC vs ABAC vs ReBAC often frame them as competing models. Real systems don’t work that way.
RBAC defines baseline access who is allowed to operate at all.
ABAC refines decisions using context device posture, location, risk, or time.
ReBAC determines entitlement whether a user should access a specific resource through relationships.
Together, they form a layered authorization strategy.
Roles establish trust boundaries. Attributes add conditional checks. Relationships express ownership and collaboration. Each model covers a gap the others leave behind.
Teams that understand this stop asking which model to choose. They start asking where each model fits best. And that’s usually when access control stops being a bottleneck and starts feeling like part of the product.
RBAC best practices that still matter in hybrid systems
When teams introduce ReBAC or other fine-grained models, there’s a temptation to treat RBAC as “solved” or secondary. That’s usually a mistake.
In hybrid systems where RBAC handles platform authority and ReBAC handles resource-level access RBAC becomes even more important, not less. It forms the guardrails around everything else.
One practice that continues to matter is keeping roles limited and intentional. Roles should represent responsibility, not convenience. When roles start encoding edge cases, RBAC quietly turns into a dumping ground for exceptions. In hybrid systems, roles should stay boring. Boring is good.
Another overlooked practice is documenting role intent, not just permissions. It’s easy to say what a role can do. It’s harder but far more useful to explain who should have it and why. That context becomes critical when roles coexist with relationship-based rules and access reviews become more complex.
Regular access reviews also remain essential. In hybrid systems, reviews shouldn’t stop at “Who has the Admin role?” They should extend to ownership and delegation paths. Who owns projects? Who can assign roles? Who can create relationships that grant access indirectly? RBAC reviews anchor those conversations.
Finally, auditability still matters. Even if relationships determine most access decisions, RBAC provides the clearest audit trail for authority. When something goes wrong, teams almost always start by asking who had elevated privileges. RBAC answers that quickly.
Hybrid authorization systems work best when RBAC is treated as the stable core—not legacy baggage.
Common mistakes teams make when choosing an access model
Most access control failures don’t come from bad models. They come from bad timing and assumptions.
One common mistake is over-engineering too early. Teams adopt relationship-based access control before the product actually needs it. The result is complexity without payoff—more logic to maintain, more edge cases to test, and fewer people who truly understand the system. ReBAC shines when relationships are central to the product. Before that, it can slow teams down.
The opposite mistake is just as common: clinging to RBAC for too long. As collaboration features grow, teams keep adding roles to patch gaps instead of acknowledging that the access model no longer fits. Role explosion is often a symptom, not the problem. It’s a sign that relationships are trying to emerge.
Another mistake is treating authorization as a one-time architectural decision. Access models aren’t static. Products evolve. Use cases change. Teams grow. The access model that worked at launch may quietly become the source of friction two years later. Ignoring those signals is how technical debt accumulates.
Finally, many teams underestimate the human cost of unclear access decisions. When users don’t understand why they have or don’t have access, trust erodes. Support tickets increase. Engineers start hard-coding exceptions. That’s usually the point where teams realize the model wasn’t wrong, it was misaligned.
The best teams don’t obsess over picking the perfect access model upfront. They choose what fits today, watch for strain, and evolve deliberately as the product demands it.
Conclusion
The most important thing to understand about RBAC vs ReBAC is this: you’re not choosing a philosophy, you're choosing a fit.
RBAC is still widely used for a reason. It gives structure to access control. It supports compliance requirements. It keeps governance understandable. For admin access, billing controls, security settings, and operational privileges, RBAC remains hard to beat.
ReBAC exists because modern SaaS products don’t stop at administration. They revolve around relationships between users, teams, organizations, projects, and shared resources. When access depends on how things connect, roles alone start to feel restrictive.
What we’ve consistently seen is this:
RBAC handles who you are in the system.
ReBAC handles how you interact inside the product.
Teams get into trouble when they treat this as an either-or decision. The healthiest systems don’t. They use RBAC where clarity and control matter most, and ReBAC where flexibility and collaboration define the user experience.
If you’re early-stage, RBAC will likely carry you far.
If your product enables sharing, delegation, or cross-org collaboration, ReBAC or a hybrid approach will eventually feel unavoidable.
The real mistake isn’t picking the “wrong” model.
It’s refusing to evolve the model when the product outgrows it.
Access control isn’t a one-time design choice. It’s something your architecture grows into. The sooner you recognize that, the fewer permission rewrites and production surprises you’ll face later.
FAQs
Q: Is ReBAC better than RBAC for SaaS applications?
A: ReBAC isn’t “better” by default. It works best for products with sharing, collaboration, and nested resources, while RBAC remains strong for admin access and compliance-driven controls.
Q: Can RBAC and ReBAC be used together?
A: Yes. Most modern SaaS platforms use RBAC for platform-level permissions and ReBAC for resource level access like projects, files, or shared workspaces.
Q: When does RBAC start to break down?
A: RBAC starts to strain when access depends on relationships—such as team membership, ownership, or delegation rather than fixed job roles.
Q: How is ReBAC different from ABAC?
A: ReBAC evaluates relationships between users and resources, while ABAC relies on attributes like location, device, or risk signals. They often complement each other in layered authorization systems.


