CIAM Maturity Model: How to Choose the Right Identity Platform at Every Stage of Company Growth
As companies grow, their identity needs evolve from simple logins to complex, global CIAM ecosystems. This CIAM Maturity Model explains how identity requirements change from startup to enterprise. Learn how to choose the right CIAM platform at each stage—without costly re-platforming later.
Table of Contents
- Introduction
- Understanding the CIAM Maturity Model
- Stage 1 — Early-Stage Startups: Speed and Simplicity First
- Stage 2 — Small and Medium Businesses (SMBs): Balancing Cost, Security, and Scale
- Stage 3 — Mid-Market & Hyper-Growth Companies: Scaling Identity Without Complexity
- Stage 4 — Large Enterprises: Global Scale, Security, and Compliance at the Highest Level
- How to Evaluate CIAM Vendors Across Maturity Stages
- Why Choosing the Right CIAM Foundation Early Matters
- The LoginRadius Advantage Across All Growth Stages
- Conclusion
- Identify Your CIAM Maturity Stage and Plan Your Next Step
Introduction

Learn How to Master Digital Trust

The State of Consumer Digital ID 2024

Top CIAM Platform 2024
Introduction
Identity is one of the few technology decisions every company must revisit multiple times as it grows. What works at the startup stage almost never works for a mid-sized business. What satisfies an SMB’s needs rarely meets the scale, security, and compliance expectations of a global enterprise.
And somewhere between these milestones, organizations discover that CIAM (Customer Identity and Access Management) is no longer just a login feature—it’s a core infrastructure layer that shapes security, compliance, user experience, and long-term scalability.
That’s where the CIAM Maturity Model becomes essential.
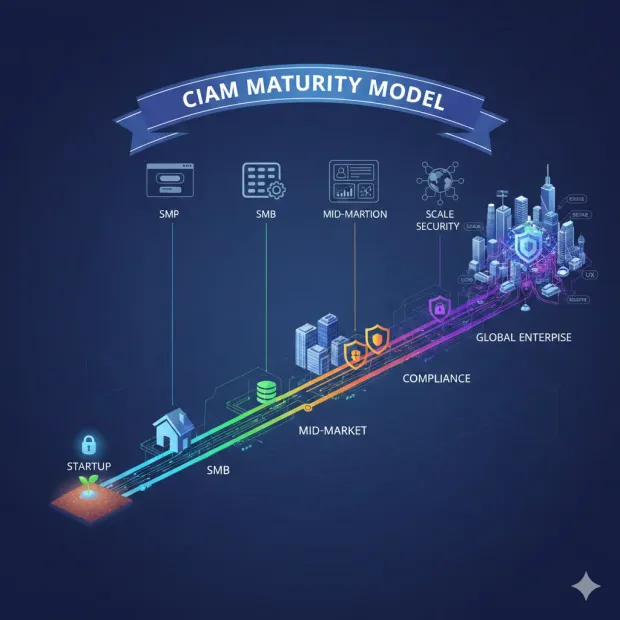
It provides a structured way to understand how your identity needs evolve as the business moves from early-stage startup → SMB → mid-market → enterprise. More importantly, it helps teams choose the right platform before hitting roadblocks like performance constraints, audit failures, fragmented user directories, or forced re-platforming.
In this guide, we share a practical, experience-backed CIAM maturity model that helps organizations evaluate where they are today and what capabilities they’ll need next. Whether you’re building your first product or modernizing a global identity ecosystem, this framework shows how to choose the right CIAM solution for your company’s growth stage.
Understanding the CIAM Maturity Model
CIAM maturity reflects how well an organization’s identity infrastructure supports:
-
Security and threat protection
-
Compliance and privacy obligations
-
Authentication and user experience
-
Multi-brand or multi-application identity unification
-
B2B and partner identity
-
Data residency and sovereignty
-
Scalability and high availability
-
Developer productivity and integration velocity
Identity needs change dramatically as organizations scale across team sizes, user volumes, compliance boundaries, and business models. The CIAM maturity model helps leaders answer four critical questions:
-
What identity capabilities do we need right now?
-
What capabilities will we need in the next 12–24 months as we grow?
-
Which CIAM platforms can support our full maturity path without migrations?
-
How do we avoid choosing a CIAM solution that becomes a bottleneck later?
Without a maturity model, companies often overbuild early or underinvest until forced into costly, disruptive migration projects. With it, identity becomes a strategic enabler—not a barrier.
Stage 1 — Early-Stage Startups: Speed and Simplicity First
Early-stage startups focus on launching products quickly and validating use cases. Engineering teams are small, timelines are fast, and identity is usually a means to an end. Yet even at this stage, secure and reliable CIAM is essential to build trust and reduce risk.
Identity Priorities
-
Fastest possible time-to-market
-
Minimal configuration
-
Low development overhead
-
Core authentication working across web/mobile
-
Basic MFA support (email OTP, SMS, authenticator apps)
Startups want to ship features—not build identity infrastructure.
Typical Challenges
-
Limited engineering and security resources
-
Pressure to release quickly
-
Early growth can expose security gaps
-
MVP-level identity tools break quickly as usage scales
Many startups start with Firebase Authentication, Amazon Cognito, or lightweight open-source packages because they allow teams to get moving fast. But these solutions often introduce future constraints once the company begins to scale, handle sensitive data, or sell into regulated or enterprise markets.
Recommended CIAM Capabilities
-
Email/password + social login
-
Basic MFA
-
Secure default configuration
-
Optional passwordless when ready
-
Ability to scale to 10K–20K MAUs without re-architecture
The right CIAM choice here reduces friction without burdening the engineering team. And importantly, it avoids forcing a rebuild six months later when MAUs spike or compliance demands begin.
Stage 2 — Small and Medium Businesses (SMBs): Balancing Cost, Security, and Scale
SMBs are past the MVP phase. They are acquiring customers, optimizing onboarding and authentication flows, and preparing for more structured security and compliance expectations. At this stage, reliability and ease of maintenance take priority—but budgets remain tight.
Identity Priorities
-
Stronger security compared to startup defaults
-
Cost-effective CIAM with predictable pricing and ROI
-
Better control over user experience and flows
-
Ability to support 20K–100K+ MAUs
SMBs don’t yet need the full depth of enterprise capabilities—but they do need more than what startup-focused tools provide.
Typical Challenges
-
No dedicated identity engineers
-
Emerging compliance requirements
-
Increasing bot traffic and ATO attacks
-
Platform limitations forcing engineering workarounds
-
Multiple apps or properties requiring shared identity
Many SMBs outgrow their initial identity stack right here.
Recommended CIAM Capabilities
-
Adaptive MFA and secure session management
-
Consent and privacy tools
-
Customizable login and registration flows
-
Predictable MAU pricing without enterprise upsells
-
High availability and consistent performance
-
Developer-friendly APIs and admin dashboards
This is where many organizations begin evaluating CIAM platforms like LoginRadius, Auth0, and other mid-market identity providers. The goal is to secure customer experience and prepare for future scale—without overwhelming complexity.
Stage 3 — Mid-Market & Hyper-Growth Companies: Scaling Identity Without Complexity
Identity complexity rises significantly once organizations reach the mid-market—typically when they pass:
-
100K+ MAUs
-
Multiple product lines
-
Global user distribution
-
Growing compliance obligations
-
Early enterprise customer requirements
This is often the point where companies realize they need a future-proof CIAM platform to prevent identity from becoming a bottleneck.
Identity Priorities
-
High uptime and global performance
-
Stronger compliance posture (SOC 2, HIPAA readiness, GDPR enforcement)
-
More flexible authentication and authorization journeys
-
B2B features (SSO, SCIM, organization management)
-
Multi-application identity unification
Typical Challenges
-
Outgrowing basic developer-auth tools
-
Rising fraud threats requiring adaptive security
-
Expansion into new markets requiring data residency
-
Selling into enterprise customers demanding SSO, SCIM, audit logs
-
Fragmented identities across brands or applications
Mid-market companies often begin restructuring their identity stack here.
Recommended CIAM Capabilities
-
Multi-region hosting with failover
-
Authentication orchestration for complex scenarios
-
Strong MFA + passwordless + adaptive risk scoring
-
B2B features: SSO, SCIM, delegated admin
-
Unified identity for multi-application or multi-brand environments
-
Audit trails and governance controls
At this stage, companies must judge CIAM platforms not only by current features—but by their ability to scale easily over the next five years.
Stage 4 — Large Enterprises: Global Scale, Security, and Compliance at the Highest Level
Large enterprises live in a completely different identity reality. They manage millions of customer identities, operate in dozens of regions, face aggressive security threats, and must maintain strict SLAs across global infrastructure. Identity is a mission-critical system that supports digital operations, compliance, and customer trust.
Identity Priorities
-
Global scale with low-latency authentication
-
Region-specific data residency and sovereignty
-
Advanced authentication (adaptive, passkeys, risk-based, behavioral)
-
CIAM for multi-brand portfolios and M&A consolidation
-
Full B2B partner identity ecosystems
-
Strict auditability across multiple regulatory frameworks
-
Robust identity governance
Typical Challenges
-
Large, complex identity environments accumulated over years
-
Multiple identity stores across brands or acquired companies
-
Regulatory pressure across multiple jurisdictions
-
Legacy modernization efforts
-
Extremely high uptime requirements
Enterprise CIAM requires a platform that can support massive scale, support diverse architectural environments, and maintain strong compliance.
Recommended CIAM Capabilities
-
Multi-region, multi-zone global infrastructure
-
Configurable data residency (by app, region, or tenant)
-
Advanced threat detection and fraud prevention
-
Fine-grained access policies
-
Full B2B identity suite (SSO, SCIM, tenant isolation, delegated admin)
-
Flexible integration with legacy + modern stacks
-
Enterprise-grade SLAs and support
Only a small set of CIAM platforms can meet the full enterprise requirement spectrum—and this is where enterprises re-evaluate vendors carefully.
How to Evaluate CIAM Vendors Across Maturity Stages
As you move through each stage of CIAM maturity, the importance of specific capabilities evolves.
Security & Compliance Evolution
-
Startups → MFA basics
-
SMBs → adaptive MFA + compliance workflows
-
Mid-market → audit logs + risk-based authentication
-
Enterprise → advanced threat detection, global governance, strong privacy posture
Scalability and Architecture Evolution
-
Startups → simple SDK integration
-
SMBs → reliable uptime and moderate MAU growth
-
Mid-market → multi-region and multi-app scale
-
Enterprise → global deployments, redundancy, and complex orchestration
Data Residency & Privacy Evolution
-
Startups → general privacy alignment
-
SMBs → GDPR and CCPA
-
Mid-market → region-specific residency options
-
Enterprise → full sovereignty controls, per-tenant residency
Developer Experience Evolution
-
Startups → plug-and-play login
-
SMBs → customization + low maintenance
-
Mid-market → orchestration and advanced flows
-
Enterprise → extensibility across large, multi-team engineering environments
When choosing a CIAM platform, leaders should look beyond immediate needs and evaluate whether the platform supports your full growth trajectory.
Why Choosing the Right CIAM Foundation Early Matters
Many organizations only realize they chose the wrong CIAM solution when:
-
Compliance requires features their current platform lacks
-
User volume overwhelms their existing authentication system
-
New business models (B2B, multi-brand, global expansion) demand more flexibility
-
Legacy identity stacks block modernization
-
Identity threats outgrow the platform’s security capabilities
Re-platforming identity is expensive, disruptive, and often risky. Making the right foundational decision early prevents:
-
Customer experience disruptions
-
Security threats stemming from weak identity architecture
-
Forced re-architectures during hyper-growth
-
Integration failures across multiple apps or brands
-
Compliance gaps that slow enterprise deals
A CIAM platform should grow with your business—not hold it back.
The LoginRadius Advantage Across All Growth Stages
LoginRadius is uniquely designed to support the full CIAM maturity lifecycle—from startup launch to global enterprise identity modernization.
For Startups
-
Quick implementation
-
Secure defaults
-
Affordable pricing
-
Fast, frictionless login experiences
For SMBs
-
Adaptive MFA
-
Privacy and consent management
-
Predictable MAU pricing
-
More customization without heavy overhead
For Mid-Market & Hyper-Growth Companies
-
Multi-region hosting
-
B2B features like SSO, SCIM, and organization management
-
Authentication orchestration
-
Audit trails and compliance readiness
For Large Enterprises
-
Global hosting and data residency
-
Advanced security and threat protection
-
Support for complex partner ecosystems
-
Identity governance and enterprise-grade SLAs
Many organizations choose LoginRadius because they can adopt us early and stay with the same identity architecture as they scale—avoiding costly migrations later in their growth journey.
Conclusion
The CIAM maturity model illustrates a fundamental truth: identity is not static. As companies grow, their authentication needs become more sophisticated—from rapid deployment to compliance frameworks, multi-application consolidation, global scale, and full enterprise governance.
By understanding your current maturity stage, you can:
-
Make better strategic identity decisions
-
Avoid costly re-platforming
-
Improve customer experience
-
Strengthen security posture
-
Support new business models
-
Scale confidently
Choosing the right CIAM platform is one of the most important architectural decisions an organization can make. The goal is to invest in an identity foundation that supports each stage of growth—without forcing painful transitions as the business evolves.
Identify Your CIAM Maturity Stage and Plan Your Next Step
Whether you're a startup validating your MVP, an SMB facing new compliance expectations, or an enterprise modernizing global identity infrastructure, our team can help you determine the right CIAM capabilities for your stage of growth.
Explore our documentation, review platform capabilities, or connect with our solution architects for a personalized CIAM maturity consultation.

