ForgeRock has long been recognized as a powerful identity platform for large enterprises, governments, and highly regulated industries. Its flexibility, standards support, and ability to handle deeply customized identity deployments have made it a staple in complex IAM environments for years.
However, customer identity and access management (CIAM) requirements have changed dramatically. Today’s organizations need more than configurable identity engines; they need fast deployment, modern MFA and passwordless authentication, seamless B2B and partner identity, and the ability to iterate on customer journeys without months of professional services or custom code.
As a result, many teams evaluating their long-term CIAM strategy are reassessing whether ForgeRock remains the right fit. In this guide, we break down the top ForgeRock alternatives and explain what to look for in a modern CIAM platform built for scale, security, and developer velocity.
Evaluation Criteria: What Makes a Great CIAM Platform
Before comparing alternatives, it’s important to define how modern CIAM platforms should be evaluated. From our experience working with consumer brands, B2B SaaS companies, and regulated organizations, five dimensions consistently matter most.
Use Case Fit: CIAM vs Workforce IAM vs B2B Identity
Not all identity platforms are designed for the same purpose. Workforce IAM tools focus on employee access, while CIAM platforms must handle millions of external users, unpredictable traffic spikes, and frictionless onboarding.
Increasingly, organizations also need B2B and partner identity, including multi-tenant architectures, delegated administration, account hierarchies, and enterprise federation. A strong CIAM platform should support B2C, B2B, or hybrid use cases without architectural workarounds.
Security & User Experience
Security can no longer come at the expense of user experience. Modern CIAM platforms should provide:
-
Deep MFA coverage (push, TOTP, passkeys)
-
Adaptive and risk-based authentication
-
Passwordless options that are production-ready, not experimental
Just as important is applying security contextually, reducing friction for trusted users while escalating protection when risk changes.
Architecture & Scalability
CIAM platforms must be cloud-native, highly available, and proven at scale. This includes multi-region deployments, strong SLAs, predictable performance during peak events, and architectures that don’t require heavy customization to scale.
Legacy and hybrid stacks often struggle here, especially when orchestration and customization are layered on top.
Data Residency & Compliance
Customer identity data is regulated data. Support for regional hosting, clear data residency controls, and compliance with frameworks such as GDPR, CCPA, HIPAA, and SOC 2 is critical, especially for global brands and public-sector organizations.
Developer Experience & Migration Effort
CIAM implementations succeed or fail based on developer adoption. Clear APIs, modern SDKs, documentation, sandbox environments, and migration tooling all reduce time to value. Platforms that require extensive professional services for routine changes often slow teams down over time.
7 Best ForgeRock Alternatives for CIAM & B2B Identity
Below are seven of the most commonly evaluated ForgeRock alternatives for modern CIAM use cases.
1. LoginRadius
LoginRadius is a CIAM platform designed specifically for high-volume B2C, B2B SaaS, and public-sector identity use cases. Unlike ForgeRock, which is designed for highly customized and resource-intensive IAM environments, LoginRadius is purpose-built for customer identity at scale. Its architecture prioritizes consumer-scale traffic handling, identity-native security controls, flexible UX orchestration, and global cloud deployment, without the operational overhead, long implementation cycles, or services-heavy customization typically associated with ForgeRock deployments.
Where LoginRadius Works Especially Well
CIAM-native architecture: LoginRadius is designed from the ground up for customer identity rather than adapted from a generalized IAM stack. It offers multi-region cloud hosting, high-availability SLAs, geo-isolated tenancy options, and native multi-tenant organization support. These capabilities are foundational to the platform, not layered on through custom configuration, scripting, or infrastructure workarounds as is often required with ForgeRock.
Rapid deployment without complex orchestration frameworks: Teams can implement authentication, MFA, social login, progressive profiling, passkeys, and branded login experiences without standing up complex identity trees, custom scripts, or long-running professional services engagements. This significantly reduces time-to-value and ongoing maintenance compared to ForgeRock environments, where even minor flow changes can require specialized IAM expertise.
Broad authentication coverage out of the box: LoginRadius supports passwords, OTP, magic links, WebAuthn passkeys, fully passwordless flows, social login, adaptive MFA, and enterprise federation through unified APIs and configuration. This enables teams to modernize authentication without stitching together multiple ForgeRock modules or building custom extensions to fill capability gaps.
Modern CIAM security stack: Security controls such as native push authentication, TOTP, breached password detection, anomaly scoring, adaptive risk analysis, IP velocity checks, and bot mitigation are built directly into the CIAM layer. These protections are identity-native and readily configurable, rather than dependent on complex policy trees or external security integrations commonly required in ForgeRock deployments.
Low-/no-code identity orchestration: Hosted templates, journey builders, conditional workflows, and theming tools allow product, growth, and CX teams to iterate on signup, login, and verification flows without creating engineering bottlenecks. Identity experiences can evolve quickly without repeated code changes or lengthy regression cycles, an area where ForgeRock’s flexibility often comes at the cost of speed and operational simplicity.
Ideal For
-
Consumer brands requiring elastic global scale (retail, media, gaming)
-
B2B SaaS platforms that need native multi-tenant identity and delegated administration
-
Public-sector and regulated organizations with strict data residency and compliance requirements
-
Teams that frequently iterate on onboarding, authentication, and verification journeys without dedicated IAM specialists
2. Auth0 (Okta Customer Identity Cloud)
Auth0 is a developer-focused CIAM platform that emphasizes extensibility and programmability. It is frequently evaluated by teams that want more flexibility and faster iteration than traditional enterprise IAM platforms like ForgeRock, without managing identity infrastructure themselves.
Where Auth0 Performs Well
-
Developer-first extensibility: Auth0 provides Actions, hooks, rules, and a wide range of SDKs that allow developers to customize authentication logic, token claims, and identity flows. This model is significantly more approachable for application teams than ForgeRock’s identity trees and scripting-heavy configurations.
-
Large integration ecosystem: Auth0 offers a broad marketplace of integrations covering analytics, fraud prevention, marketing platforms, and enterprise IdPs, making it easier to connect identity into existing SaaS ecosystems.
-
B2B SaaS enablement: Supports SAML, OIDC, RBAC, enterprise SSO, and tenant-level configuration, which makes it a common choice for SaaS platforms serving business customers.
-
CIAM Fit Analysis: Auth0 works best for engineering-led organizations that want programmatic control over identity without the operational burden of managing a complex IAM stack. At large consumer scale, however, pricing, rate limits, and long-term ownership of custom logic can become friction points compared to more CIAM-native platforms.
Ideal For
-
Developer-driven SaaS companies
-
Teams replacing ForgeRock for faster CIAM iteration
-
Products with heavy third-party integrations
Trade-Offs
-
Pricing scales aggressively with MAUs and extensibility usage
-
Rate limits can affect high-volume consumer traffic
-
Long-term CIAM logic remains tightly coupled to engineering teams
3. Microsoft Entra External ID
Microsoft Entra External ID (formerly Azure AD B2C) is Microsoft’s customer identity offering, extending workforce IAM concepts into external user scenarios. It is most often evaluated by organizations already standardized on Azure infrastructure and Microsoft security tooling.
Where Microsoft Entra External ID Performs Well
-
Microsoft ecosystem alignment: Native integration with Azure services, Entra ID, Conditional Access, and Microsoft security tooling makes it appealing for Azure-first organizations.
-
Enterprise federation support: Strong SAML and OIDC capabilities for enterprise SSO and partner identity scenarios.
-
Baseline CIAM coverage: Supports customer authentication, social login, and external identity federation for relatively straightforward use cases.
CIAM Fit Analysis: Entra External ID works best when customer identity is tightly coupled to Microsoft infrastructure and IT-driven workflows. For consumer-facing products requiring frequent UX iteration, flexible orchestration, or rapid experimentation, policy complexity and limited CIAM-native tooling often become constraints.
Ideal For
-
Azure-centric enterprises
-
Organizations with existing Entra ID investments
-
Low-variation customer identity use cases
Trade-Offs
-
Complex custom policy management
-
Limited consumer-grade UX flexibility
-
Slower iteration driven by IT-heavy processes
4. Ping Identity
Ping Identity is an enterprise IAM platform offering both workforce and customer identity capabilities. It is commonly evaluated alongside ForgeRock in large organizations with complex security, compliance, and hybrid deployment requirements.
Where Ping Identity Performs Well
-
Mature standards and federation support: Ping has long-standing strength in SAML, OAuth, and OIDC, making it reliable for complex enterprise federation and partner access scenarios.
-
Hybrid and on-prem deployment options: Supports environments that require on-prem, private cloud, or hybrid identity deployments, which can be critical for regulated industries.
-
Enterprise security posture: Strong alignment with enterprise security controls, governance models, and compliance-driven identity programs.
CIAM Fit Analysis: Ping Identity is powerful but heavy. While it can support CIAM use cases, implementations often resemble traditional IAM projects with long timelines, professional services dependency, and slower customer-facing iteration, similar to the challenges teams experience with ForgeRock.
Ideal For
-
Large enterprises with hybrid IAM environments
-
Regulated industries with strict deployment requirements
-
Organizations with existing Ping investments
Trade-Offs
-
High implementation and operational complexity
-
Slower iteration on customer UX
-
Significant services and expertise requirements
5. Amazon Cognito
Amazon Cognito is AWS’s native identity service, designed primarily as an infrastructure component rather than a full CIAM platform. It is most often evaluated by teams building entirely within the AWS ecosystem.
Where Amazon Cognito Performs Well
-
Native AWS integration: Deep integration with AWS services, IAM policies, and infrastructure tooling makes Cognito convenient for AWS-centric development teams.
-
Cost efficiency at small scale: For low to moderate usage, Cognito can be cost-effective compared to enterprise IAM platforms.
-
Basic authentication coverage: Provides baseline support for user pools, social login, and token-based authentication.
CIAM Fit Analysis: Cognito is infrastructure-first, not CIAM-first. Advanced authentication, orchestration, and UX customization typically require Lambda triggers and custom engineering. Compared to ForgeRock, it reduces licensing complexity but shifts identity responsibility heavily onto development teams.
Ideal For
-
AWS-native application teams
-
Simple authentication requirements
-
Infrastructure-driven identity strategies
Trade-Offs
-
Heavy reliance on custom code and Lambda triggers
-
Limited UX and orchestration capabilities
-
Weak B2B and multi-tenant CIAM support
6. Descope
Descope is a newer identity platform focused on passwordless authentication and flow-based identity design. It is often evaluated by teams prioritizing modern login experiences over traditional IAM depth.
Where Descope Performs Well
-
Passwordless-first approach: Strong support for passwordless authentication methods, including magic links, OTPs, and passkey-style flows.
-
Flow-based identity design: Visual flow builders make it easier to design and modify authentication journeys compared to code-heavy IAM platforms like ForgeRock.
-
Fast time-to-value: Quick setup for modern authentication use cases with minimal infrastructure management.
CIAM Fit Analysis: Descope works well for teams focused on modern authentication experiences, but it lacks the broader CIAM depth required for large-scale consumer, B2B, or regulated deployments. Compared to ForgeRock, it simplifies auth but does not fully replace enterprise-grade CIAM needs.
Ideal For
-
Startups and mid-market products
-
Teams prioritizing passwordless UX
-
Applications with limited identity complexity
Trade-Offs
-
Limited enterprise and B2B CIAM features
-
Smaller ecosystem and partner integrations
-
Less proven at a very large consumer scale
7. WorkOS
WorkOS is a B2B identity platform focused on enterprise SSO, directory sync, and onboarding for SaaS products. It is not a full CIAM platform but is often considered by B2B SaaS teams evaluating alternatives to heavyweight IAM solutions like ForgeRock.
Where WorkOS Performs Well
-
Enterprise SSO enablement: Simplifies SAML-based SSO onboarding for SaaS customers without requiring deep IAM expertise.
-
Directory sync and SCIM: Strong support for user provisioning and lifecycle management in B2B environments.
-
Developer-friendly APIs: Designed to be embedded quickly into SaaS products with minimal friction.
CIAM Fit Analysis: WorkOS addresses a narrow but important slice of B2B identity. It is not a replacement for ForgeRock in broad CIAM scenarios and typically needs to be paired with a CIAM platform like LoginRadius for customer-facing authentication and lifecycle management.
Ideal For
-
B2B SaaS companies
-
Products focused on enterprise customer onboarding
-
Teams needing fast SSO enablement
Trade-Offs
-
Not a full CIAM solution
-
Limited consumer identity capabilities
-
Requires complementary CIAM tooling for B2C use cases
Why People Switch From ForgeRock to LoginRadius
Organizations moving away from ForgeRock often cite similar challenges that directly impact speed, cost, and customer experience.
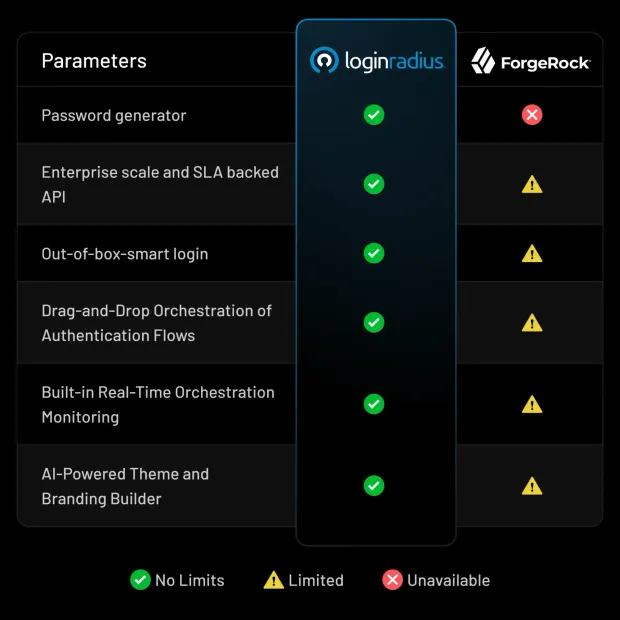
Simpler, Faster Deployments
ForgeRock environments are powerful but complex to configure and maintain, often requiring specialized IAM expertise.
LoginRadius offers a cloud-native CIAM platform with unified configuration, drag-and-drop orchestration, and real-time monitoring, reducing setup time and operational overhead.
Modern MFA and Passwordless Without Complexity
ForgeRock provides partial support for modern MFA but often lacks native push customization and streamlined passwordless experiences.
LoginRadius delivers native push, TOTP, adaptive MFA, LR Authenticator, and full passwordless workflows without bolted-on tooling.
Complete Credential and Risk Management
ForgeRock has limited built-in credential generation and constrained risk-event retention.
LoginRadius includes a built-in password generator, full audit retention, and adaptive risk intelligence as first-class features.
Enterprise Scalability and Federation
ForgeRock can struggle with SLA-backed APIs and social or third-party identity federation at scale.
LoginRadius supports enterprise-grade SLAs, SAML, OIDC, and multi-IDP federation across B2C, B2B, and partner environments.
Developer-First Flexibility
ForgeRock’s limited SDK and CLI tooling can slow integration cycles.
LoginRadius’ 40+ SDKs, APIs, CLI, and turnkey widgets accelerate development and CI/CD integration.
LoginRadius vs ForgeRock: Feature Comparison
| Capability | LoginRadius | ForgeRock |
|---|---|---|
| CIAM focus | Purpose-built CIAM for B2C, B2B, partners | Generalized IAM adapted for CIAM |
| Architecture | Cloud-native, headless CIAM | Complex, resource-intensive stack |
| Passwordless | Native passkeys and passwordless flows | Limited native support |
| MFA depth | Push, TOTP, adaptive MFA | Partial, often complex to configure |
| Orchestration | Low-/no-code journey orchestration | Configuration-heavy |
| B2B identity | Native multi-tenant support | Requires significant customization |
| Developer tooling | 40+ SDKs, APIs, CLI, Terraform | Limited developer tooling |
| Analytics & audit | Real-time analytics and full audit logs | More constrained visibility |
| Migration support | Purpose-built migration accelerators | Services-heavy migrations |
Conclusion
ForgeRock remains a powerful identity platform for highly customized and regulated environments. However, modern CIAM requirements, passwordless authentication, adaptive security, B2B identity, and rapid iteration are pushing many organizations to explore alternatives built specifically for customer identity at scale.
Platforms like LoginRadius reflect a broader shift toward cloud-native CIAM architectures that prioritize developer velocity, user experience, and long-term flexibility. For teams struggling with complexity, slow deployment cycles, or rising operational costs, reassessing ForgeRock is often a strategic move.
If your organization is evaluating the next phase of its CIAM strategy, shortlisting a modern platform designed for today’s identity challenges can reduce friction now while future-proofing your architecture for what comes next.
Compare ForgeRock and LoginRadius in detail, or speak with our team to explore migration paths and CIAM architecture options tailored to your use case.