Introduction
Modern enterprises don’t just work within four walls - they collaborate dynamically with partners, vendors, agencies, and external teams worldwide. This dynamic ecosystem enables faster innovation, broader reach, and more agile operations.
Yet, alongside the upside comes a downside: granting external teams access can pose significant security risks. Consider projects that depend on timely vendor deliveries or the rapid onboarding of strategic partners.
Granting them access to internal tools or data systems by sending generic credentials may be expedient, but it also opens doors to credential leakage, orphaned accounts, and potential breaches. Traditional IAM systems, designed to control internal employees, are often ill-suited for managing external parties.
They often lack intuitive self-service onboarding, scalable provisioning, or granular access policies required by partner organizations. The result is friction in business processes and tension between IT teams and external collaborators.
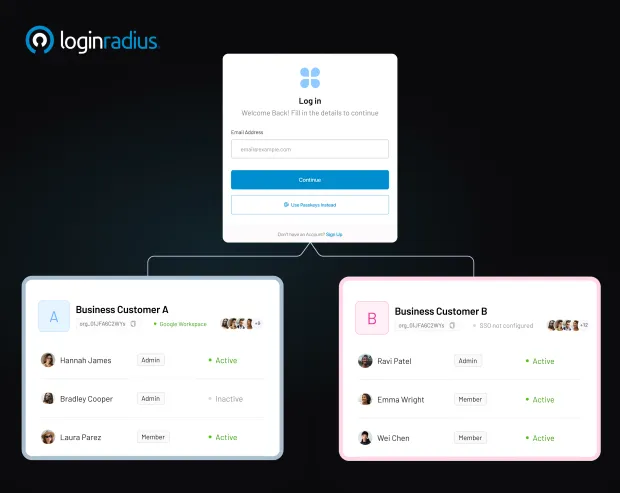
That’s where B2B Partner IAM - also known as partner identity and access management, IAM for partners, or partner access management—comes in. So, what does B2B authentication mean? It’s specifically designed to manage external identities, including vendors, resellers, suppliers, agencies, and strategic business partners.
It treats them differently from employees: offering secure invitations, branded portals, SSO onboarding, role-based permissions, just-in-time provisioning, and complete lifecycle governance. This ensures both trust and ease, eliminating the compromise that has long been accepted.
By the end of this post, you’ll understand how Partner IAM transforms external collaboration, mitigating security risk, reducing manual onboarding processes, and building trusted ecosystems at scale.
You’ll also discover why LoginRadius Partner IAM is a standout solution, featuring developer-first APIs, a low-code flow builder, and a multi-tenant architecture.
What is Partner IAM / B2B IAM?
Partner IAM, aka B2B IAM is an Identity and Access Management system specifically tailored to handle external users - partners, vendors, contractors, and third-party collaborators. Unlike traditional IAM, which focuses on employees and internal staff, Partner IAM/ B2B recognizes that external collaborators require secure onboarding, federated login, scoped permissions, and offboarding workflows distinct from internal user flows.
Key Characteristics:
-
Federated authentication through external identity providers (SAML, OIDC).
-
Invitation-based onboarding, allowing secure access without sharing passwords.
-
JIT provisioning, where accounts are created dynamically at first login.
-
Multi-organization support, enabling separate policies per partner group.
-
Multi-branded login portals, aligning with partner domains and corporate identity.
-
Fine-grained RBAC, mapping each external user to the exact resources they need.
Who Benefits from Partner IAM?
Partner IAM is versatile and spans multiple industries, each with unique collaboration patterns:
1. SaaS Platforms and B2B Services
SaaS platforms serving enterprise clients often interact with external agencies, freelancers, or partner teams who need access to project data, dashboards, or customer environments. Without proper IAM, this usually means manual account creation, credential sharing, and messy permission management.
Partner IAM allows SaaS providers to offer invitation-based onboarding, SSO via partner IdPs, and role-based access scoped to only the relevant data.
For instance, a client’s marketing agency can securely log in, manage campaign settings, and view analytics—without accessing other clients' data. When the agency is replaced or rotates staff, access can be revoked instantly. This not only improves security but also enhances the partner experience and reduces operational overhead for IT teams.
2. Supply Chain Networks
Supply chains encompass a wide ecosystem, including shipping carriers, warehouses, customs agents, and logistics vendors, all of which require real-time access to internal systems. Traditional access management often leads to shared credentials, audit gaps, or unauthorized access.
Partner IAM enables companies to create secure, auditable login flows for each external party, ensuring seamless access and authentication. Each vendor gets scoped access via their own custom identity provider or a custom-branded login portal, depending on role.
A warehouse team may upload delivery receipts, while a shipping carrier only sees tracking dashboards. When contracts expire or partnerships end, their access can be automatically revoked. This ensures compliance, prevents data sprawl, and provides full visibility into third-party activity, critical in highly regulated or globally distributed operations.
3. Consulting Firms
Consulting firms working with regulated industries need temporary, precise access to internal systems, without compromising sensitive data. Traditional IAM often involves over-provisioned roles or delayed offboarding, both of which are security liabilities.
Partner IAM enables internal teams to assign limited-time, role-based access tied to a specific consulting engagement. Analysts or auditors sign in via their firm’s Single Sign-On (SSO), receive read-only or scoped access to dashboards, and have all activity logged for audit trails.
Moreover, MFA ensures secure entry, while just-in-time provisioning creates accounts only when needed. Once the engagement ends, access is automatically revoked. This protects compliance integrity while empowering consultants to deliver insights efficiently and securely.
4. Retailers
Retailers rely on sellers, resellers, service providers, and merchants to interact with their internal systems, such as uploading products, communicating with customers, and updating inventory.
Each partner has different access needs, which traditional Identity and Access Management (IAM) systems aren’t equipped to handle. Partner IAM enables self-service onboarding, SSO, and role-based permissions that match the user’s function.
A reseller can log in securely, manage their storefront, and view sales metrics, without seeing other vendor data or platform configurations. Branded login portals offer a familiar experience, and federated identity support removes the need for duplicate credentials. As partnerships evolve, access updates are automatically applied, ensuring the ecosystem remains clean, secure, and scalable.
These scenarios underscore why Workforce IAM isn’t enough: internal systems are designed for hierarchical, always-on employees—not for segmented, temporary, or multi-org access needs.
5. Media and Entertainment Platforms
Media and Entertainment Platforms rely on Partner IAM to manage secure access for global users and partners across digital properties. One global broadcaster leveraged LoginRadius to unify authentication, strengthen security, and deliver seamless login experiences across regions. If you're looking to modernize identity infrastructure across your media platforms,explore the A+E Networks case study and see how Partner IAM can power your strategy.
6. Healthcare B2B Networks
Managed care platforms often need to share sensitive patient or referral data with hospitals, pharmacies, and labs, all while maintaining strict regulatory compliance. Partner IAM plays a crucial role by enforcing HIPAA-level security, supporting adaptive MFA, and applying scoped role permissions—such as view-only for lab access or modify rights for care providers.
Every action is logged for audit purposes, helping organizations pass compliance reviews while safeguarding patient privacy. A real-world example of this can be seen in how Health Vision streamlined secure data sharing across its healthcare network using LoginRadius. Read the case study.
7. Manufacturing Ecosystems
A manufacturing company interfaces with machinery vendors, maintenance teams, quality auditors, and parts suppliers. Each partner uses a branded portal, signs in via their Identity Provider (IdP), interacts only with specific operational modules, and is automatically offboarded when contracts end. Partner IAM solves complex workflows across multi-vendor environments.
These real-world workflows highlight the breadth of business scenarios where Partner IAM supports secure and coordinated collaboration—empowering external users while keeping internal systems safe and audit-ready.
Workforce vs. Partner IAM: A Snapshot
-
User Type : Internal employees vs. external individuals or organizations.
-
Authentication : Corporate AD vs. partner’s own IdP.
-
Onboarding : HR-managed vs. invitation + self-service + JIT.
-
Branding : One company look-and-feel vs. customized per partner organization.
-
Governance : Central audit only vs. cross-organizational visibility and compliance.
LoginRadius Partner IAM supports all these workflows using its partner APIs and multi-tenant architecture, enabling secure, federated, and branded external access at scale . With roles, permissions, workflows, and IdPs managed per organization, external collaborators feel secure and respected upon login.
Why Businesses Need Partner IAM
There are three compelling reasons to invest in a Partner IAM system: security and trust, operational agility, and partner experience. Let’s understand:
1. Security and Trust
Uncontrolled external access can expose businesses to risks such as shared credentials and orphaned accounts. By offering invitation-only access, automatic deactivation, and audit logs, Partner IAM solves these issues decisively. Security teams regain visibility and control, knowing who accessed what and when—even if users belong to different companies.

2. Operational Agility
Manual onboarding processes are time-consuming and error-prone. Setting up external access often involves sending credentials, programming roles, and reacting when users leave.
Partner IAM automates these steps: send an invite, partner completes sign-up, JIT provisioning handles user creation, and users log in—all without IT involvement. This decimates onboarding time and lets technical teams focus on core projects rather than admin tasks.
3. Better Partner Experience
Partners expect modern SaaS-level experiences. With Partner IAM, they enjoy branded login portals, Single Sign-On (SSO) with their corporate IdP, MFA prompts where needed, and self-service options.
A secure invitation that respects their corporate identity fosters trust and professionalism. When multiple brands are involved—like platforms serving many vendors—Partner IAM supports multi-brand customization under a single identity infrastructure.
Together, these benefits make Partner IAM not only a security tool, but also a business enabler. It builds stronger external relationships, accelerates setup, and ensures governance—all while delivering polished partner-facing experiences.
How Partner IAM/ B2B IAM Works
Partner IAM/B2B IAM orchestrates a secure and seamless access journey through key capabilities:
A. External Identity Federation
Instead of asking partners to create new accounts, Partner IAM leverages SAML/OIDC/OAuth2 federation, allowing them to authenticate with their existing corporate IdP or social identity. This eliminates password fatigue and follows decentralized identity best practices.
B. Role-Based Access Control (RBAC)
Admins define organizational roles—like Vendor Admin or Support Agent—with scoped permissions. During onboarding, each partner user is assigned a role, ensuring they can only access the necessary resources, reducing lateral visibility and risk.
C. Just-In-Time (JIT) Provisioning
JIT provisioning ensures partner accounts are generated at first login—no more idle inactive accounts clogging directories. This not only saves admin time but also gears account creation to actual necessity, reducing license and audit overhead.
D. Branded Self-Service Portals
Partners engage through branded UIs and invitation flows that feel native. Password reset options, profile editing, and invite management are all available without raising tickets for IT teams.
These capabilities combine to deliver:
-
Onboarding - Admin sends a branded invite → Partner logs in via their IdP or email link → JIT provisioning creates an account automatically.
-
Authentication - Federated login captures identity → RBAC assigns permissions → MFA is prompted based on risk profiles.
-
Access & Management - Partners use scoped access; admins can review roles, revoke access, and audit all actions.
-
Multi-Tenant Architecture - Support multiple partner organizations under a single parent tenant - each with isolated access policies, roles, and management controls.
-
Branding Flexibility - Configure custom login pages, email domains, and portal colors per partner—creating a professional, trustworthy experience for all collaborators.
-
Low-Code Orchestration - Visual builders allow drag-and-drop assembly of invitation, provisioning, authentication, MFA, and onboarding flows—no need for custom backend scripts.
-
Comprehensive APIs & SDKs - REST APIs encompass invitations, organization creation, domain mapping, role and permission management, and user-role provisioning, providing developers with full control and integration flexibility.
-
Security Standards Support - Expect SSO, SAML, OIDC, JIT provisioning, RBAC, adaptive MFA, domain restrictions, and audit logging—all aligned with B2B security requirements.
-
Scalable Collaboration - Quickly invite entire partner organizations, manage federation, provision hundreds of users per partner, and monitor access—all while maintaining a simple architecture.
Organizations gain a platform that handles everything from federation to analytics, without needing to adapt tools built for internal staff to external use cases. This structured, white-labeled, secure approach makes Partner IAM a true enabler of partner growth strategies.
LoginRadius is a cutting-edge CIAM vendor offering a Partner IAM solution that handles the entire external access journey—from managing invitations and partner organizations to setting roles, permissions, and secure self-service portals—all with built-in logging and governance. This unified solution gives teams complete visibility and control without the complexity of custom development.
Best Practices:
-
Use JIT provisioning to align account creation with actual usage.
-
Enforce SSO + MFA for all external access.
-
Regularly recertify partner roles and remove permissions no longer needed.
-
Customize branding and domain restrictions per partner organization.
-
Integrate logs into SIEM and implement anomaly detection per partner session.
LoginRadius Partner IAM – Purpose‑Built for B2B
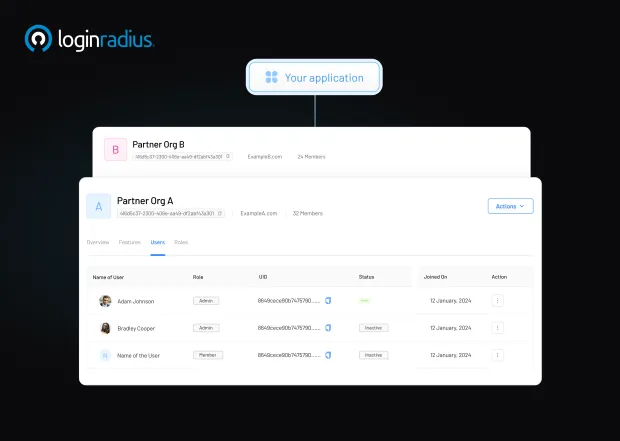
Many IAM platforms are born to serve internal workforces, and Partner IAM features are often afterthoughts. LoginRadius Partner IAM, by contrast, is purpose-built for external collaboration in B2B environments. Built on a multi-tenant architecture, each external partner gets its own organization within a shared infrastructure, with separation, governance, and flexibility.
See how easy it is to manage partners through the LoginRadius admin console:
Security and Compliance in Partner IAM
Security and compliance are not optional—they are foundational when external parties connect to internal systems within B2B/ partner IAM space. Modern CIAM solutions like LoginRadius, are designed with regulatory frameworks and security best practices in mind:
Regulatory Alignment
-
GDPR : Data residency, consent logging, and right-to-be-forgotten features.
-
SOC 2 : Access logging, monitoring, and alerting to support audit evidence.
-
HIPAA : Data encryption in transit and at rest, role-level privacy access.
Governance Controls
-
Audit Trails : Every invitation, login, permission change, or offboarding is recorded.
-
Access Revocation : Administrator can revoke partner roles instantly, and automated processes remove access after expiration or exit.
-
Adaptive MFA & SSO : Enforce strong authentication using federated IdPs with adaptive MFA for high-risk access.
-
Policy Enforcement : Set domain restrictions, session lifetimes, passwordless or OTP-only options based on compliance needs.
Encryption and Infrastructure
All identity data is encrypted at rest and in transit. Multi-region data centers allow for geo-compliance flexibility. Domain and email controls prevent impersonation or phishing risks.
Monitoring & Incident Response
-
Real-time monitoring and alerts flag suspicious behavior like repeated failed logins or logins from unusual geolocations.
-
Integration with SIEM allows external login activity to feed corporate or cloud-based security dashboards.
-
Periodic Access Reviews align with internal compliance audits and partner renewal cycles.
By combining strict access policies, lifecycle automation, federated authentication with MFA, and full audit trail visibility, Partner IAM ensures that external collaboration never introduces unmanaged risk. Platforms like LoginRadius enable organizations to safely expand digital ecosystems while meeting regulatory demands.
Partner IAM vs. Traditional IAM
| Aspect | Traditional Workforce IAM | Partner IAM (External Collaboration) |
|---|---|---|
| Target Users | Employees, internal contractors | Vendors, agencies, resellers, third parties |
| Identity Sources | Internal directories, AD/LDAP | External IdPs (SAML, OIDC), email links |
| Onboarding Flow | HR-based manual provisioning | Invitation + self-service + JIT provisioning |
| Branding | Corporate-branded only | Customized per partner organization |
| Access Management | Employee roles, company-wide policies | Scoped, cross-org RBAC, guest access |
| Compliance Oversight | Internal audit logs | Cross-organization visibility, GDPR/SOC2 audit logs |
| Authentication | Internal SSO and MFA | Partner SSO + adaptive MFA |
| Lifecycle Management | HR exit triggers | Automated expiration or manual offboarding |
The key difference lies in audience, workflow, and contextual needs. Organizations can no longer displace workforce IAM to manage external access without introducing friction or risk. On the other hand, partner IAM provides purpose-built solutions.
Implementation Roadmap
Phase 1: Identity Federation
Begin by integrating external IdPs using SAML or OIDC. Configure metadata exchanges, trust certificates, and test partner logins. Federation enables secure SSO without managing passwords.
Phase 2: Role & Permission Modeling
Define partner roles and map permissions aligned with actual workflows. Roles may include Support, Reseller Admin, or Data Viewer. This planning ensures access is scoped and compliant.
Phase 3: Invitation & Branding
Use invitation APIs to send branded emails with partner-specific URLs. Incorporate corporate logos, color schemes, language preferences, and link the portal to the partner domain.
Phase 4: JIT Provisioning and Onboarding
Set JIT provisioning, so partner accounts auto-generate at first login, removing manual account setup. Combined with invitation links, this minimizes idle accounts and streamlines access.
Phase 5: Enforce Security Policies
Configure adaptive/risk-based authentication by risk rule or profile. Use domain restrictions, session timeouts, IP filters, then test SSO works while MFA triggers on new device or network. Learn more about adaptive/ risk-based authentication:
Phase 6: Testing & Audit
Simulate the full lifecycle: invitation, login, access review, role changes, offboarding. Pull audit logs, search SIEM pipeline, confirm compliance data and log retention meet audit standards.
Phase 7: Pilot & Monitoring
Roll out to pilot partners and monitor sign-in success, access patterns, support response. Capture metrics (provisioning time, login frequency, role change requests) and refine roles or flows accordingly.
Phase 8: Full Launch & Reviews
Launch across partner core and schedule recurring access reviews and audit verifications. Decommission stale accounts and refresh roles based on business changes.
LoginRadius enhances this entire roadmap with a drag-and-drop orchestration builder and full partner API suite—automating invites, organization mapping, role assignments, JIT provisioning, and offboarding flows.
Geo‑Focused Applications & Localization
Partner IAM plays a key role in global business expansion, offering localization and compliance-by-region:
-
Europe : GDPR compliance baked in—cookie banners, EU data centers, right-to-be-forgotten support, and consent tracking across international partners.
-
USA/Canada : SOC 2 audit-ready logs, HIPAA options for healthcare data exchange, FedRAMP readiness for government-facing portals.
LoginRadius’s global architecture supports regional data centers, customizable UI language, and compliant data workflows . By enabling localization, businesses ensure partner comfort, secure collaboration, and reduced regulatory friction across borders.
Conclusion
Partner IAM is more than a security feature - it’s a strategic apparatus that enables fast-paced, governed, and trust-based collaboration with external businesses. By replacing password-sharing and manual onboarding with invitation flows, federation, branded portals, RBAC, and automated offboarding, companies unlock operational efficiency, reinforce compliance, and foster partner loyalty.
LoginRadius Partner IAM offers a developer-ready, multi-tenant, low-code platform. With REST APIs for invitations, organization and domain management, role provisioning, identity federation, JIT provisioning, and adaptive MFA, it is purpose-built for B2B authentication workflows . Its drag-and-drop orchestration and global data-center infrastructure elevate both developer experience and security posture.
Ready to modernize your partner access? Contact LoginRadius or explore the Partner IAM Developer Documentation and start building secure, scalable, and empathetic partner ecosystems today.
FAQs
1. What is Partner IAM?
A. Partner IAM secures external relationships—vendors, agencies, resellers—by enabling invitation-based access, federated login, and scoped provisioning. It’s distinct from employee IAM and focuses on cross-organizational security.
2. How does partner identity management work?
A. Admin sends invitation → partner accepts via branded portal → login through partner IdP → account created on first use (JIT provisioning) → scoped role permissions assigned → MFA applied if risky → access is logged and approved.
3. Why use Partner IAM for B2B?
A. It enables secure collaboration while automating tasks and improving partner satisfaction. Rather than sharing generic credentials, organizations govern access, offer seamless experiences, and maintain auditability—all critical in B2B ecosystems.
4. What common challenges arise with Partner IAM?
A. Challenges include handling diverse IdP integrations, maintaining role-to-permission mapping, coordinating onboarding/offboarding workflows with partners, achieving regulatory readiness, and delivering a consistent experience across organizations.
5. How to secure partner access with IAM?
A. Best practices include: implementing SSO with partner IdPs, enforcing adaptive MFA, using JIT provisioning, fine-grained RBAC, regularly reviewing access, maintaining audit trail, and integrating logs into corporate SIEM. Automate offboarding and use branded portals to reduce phishing and increase partner confidence.