SecureAuth is well established in enterprise security, particularly in employee authentication, adaptive access controls, and risk-based MFA. For internal users accessing corporate systems, this model works well. Policies are strict, identities are centrally managed, and UX trade-offs are often acceptable.
The challenge arises when SecureAuth is extended into customer identity scenarios. Consumer and partner identities differ significantly from those of employees. Customer logins must scale elastically, support modern passwordless experiences, comply with regional privacy laws, and integrate seamlessly into branded digital experiences. What feels “secure enough” for workforce IAM can feel overly complex or insufficiently flexible when applied to CIAM.
As digital products mature, many organizations reach a tipping point at which reusing workforce IAM for CIAM creates friction for developers, product teams, and end users alike. That’s where purpose-built CIAM platforms come into focus.
Evaluation Criteria: What Makes a Great CIAM Platform
Before comparing SecureAuth alternatives, it’s important to define what actually matters in a CIAM platform. CIAM success isn’t just about strong authentication; it’s about balancing security, UX, scalability, and operational efficiency.
Use case fit (CIAM vs workforce IAM vs B2B/partner IAM)
A strong CIAM platform must be designed specifically for external identities, not retrofitted from workforce IAM. Customer identity introduces fundamentally different requirements: unpredictable scale, unknown users, self-service onboarding, and highly variable access patterns. Platforms built for employees assume controlled directories, limited populations, and centralized IT ownership, assumptions that break down quickly in consumer and partner-facing scenarios.
Leading CIAM platforms support a wide range of external identity models, including B2C applications, B2B SaaS tenant structures, and partner ecosystems. They allow organizations to model customers, tenants, roles, and permissions without forcing workforce-centric constructs. The closer a platform’s core architecture aligns with CIAM use cases, the less customization and technical debt teams accumulate over time.
Security & user experience
Security and user experience are inseparable in modern CIAM. Strong authentication controls, such as multi-factor authentication, passwordless login, and passkeys, must be implemented in ways that reduce friction rather than increase it. If security measures feel intrusive or inconsistent, users abandon logins, reset passwords unnecessarily, or bypass safeguards entirely.
Leading CIAM platforms also incorporate adaptive, risk-based authentication that dynamically adjusts security requirements based on context, behavior, and risk signals. This allows organizations to enforce stronger protection when needed, without applying the same friction to every login. The goal is not just to secure access, but to do so in a way that preserves conversion rates and user trust.
Architecture, scalability, and reliability
CIAM platforms must be architected for scale from day one. Customer identity systems routinely handle millions of users, unpredictable traffic spikes, and global login patterns—especially during product launches, seasonal events, or peak usage windows. Platforms that rely on legacy, hybrid, or on-prem-first architectures often struggle under this load.
Modern CIAM solutions are cloud-native, multi-tenant, and built for elastic scaling. They provide predictable performance, global availability, and strong uptime guarantees backed by clear SLAs. This architectural foundation ensures identity remains a growth enabler rather than a bottleneck as applications scale across regions and user populations.
Data residency, privacy, and compliance
Customer identity is tightly coupled with personal data, making privacy and regulatory compliance core platform requirements rather than add-ons. Organizations must manage where user data is stored, how it is processed, and how consent is collected and enforced—often across multiple jurisdictions with conflicting requirements.
Leading CIAM platforms provide built-in support for regional data residency, consent and preference management, and privacy workflows aligned with regulations such as GDPR and CCPA. When these capabilities are native to the platform, teams avoid bolted-on compliance processes and reduce operational risk while maintaining user trust.
Developer experience and implementation effort
CIAM platforms succeed or fail largely based on developer experience. Clean APIs, well-maintained SDKs, clear documentation, and predictable behavior all determine how quickly teams can implement identity and how easily they can evolve it over time. Platforms with heavy configuration overhead, legacy SDKs, or opaque abstractions slow development and increase long-term maintenance costs.
Strong CIAM solutions prioritize developer autonomy. They enable customization without forcing teams into brittle workarounds, support modern development workflows, and make integrations straightforward across web, mobile, and backend services. Over the lifecycle of an application, this translates into faster delivery, fewer bugs, and lower total cost of ownership.
Top 5 SecureAuth Alternatives to Consider in 2026
Below are five SecureAuth alternatives evaluated through a CIAM-first lens.
1. LoginRadius
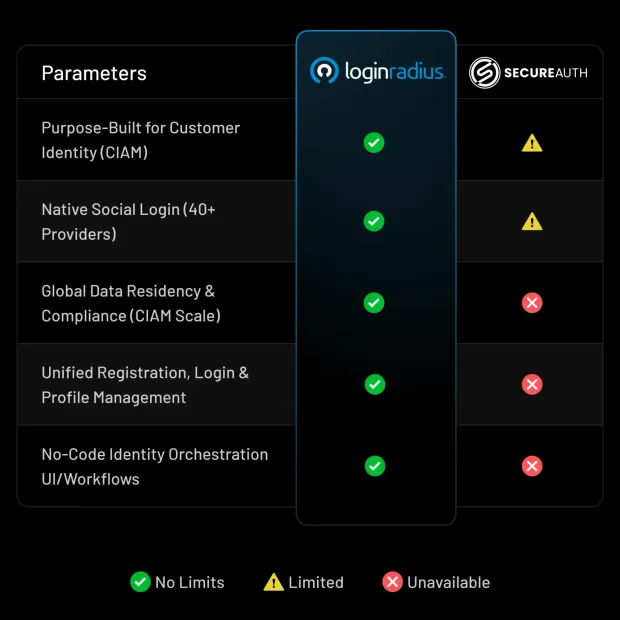
LoginRadius is a Customer Identity and Access Management (CIAM) platform designed specifically for high-volume B2C, B2B SaaS, and regulated enterprise identity use cases. Unlike workforce IAM platforms such as SecureAuth, which are designed around employee access and internal directories, LoginRadius is purpose-built for external identities, customers, partners, and delegated administrators at scale.
Rather than adapting workforce IAM patterns for consumer use, LoginRadius provides a fully managed CIAM infrastructure layer. This allows organizations to deliver secure, branded, and compliant customer experiences without taking on the operational overhead or architectural constraints that typically emerge when workforce IAM is reused for CIAM.
Where LoginRadius works especially well
CIAM-native, enterprise-ready architecture: LoginRadius is built from the ground up for customer and partner identity at scale. The platform supports cloud-native, multi-region deployments, geo-isolated data residency, native multi-tenant organization models, and SLA-backed availability. These capabilities are foundational and fully managed by LoginRadius, eliminating the need for teams to design, operate, or maintain CIAM infrastructure themselves.
Modern MFA and passwordless authentication for customers: LoginRadius provides native support for passkeys and WebAuthn, push notification MFA, adaptive risk-based authentication, hardware-backed keys, OTPs, magic links, and step-up authentication flows. These controls are designed to reduce friction for legitimate users while maintaining strong protection against account takeover and fraud, something workforce-first IAM tools struggle to balance in customer-facing environments.
Built-in privacy and compliance workflows: LoginRadius includes out-of-the-box support for GDPR and CCPA compliance, consent and preference management, secure user data handling, and configurable regional data residency. This allows organizations to meet regulatory requirements without bolting privacy workflows onto authentication flows or building custom compliance tooling.
Full branding and user experience control: LoginRadius enables complete customization of login, registration, passwordless flows, account management, and transactional emails. Teams can deliver seamless, brand-consistent customer journeys without heavy custom code, critical for consumer-facing and B2B SaaS applications where UX directly impacts adoption and retention.
Scalable, SLA-backed APIs and infrastructure: The platform is designed to support millions of identities with predictable performance during peak traffic events such as product launches, seasonal spikes, or large enterprise onboardings. Globally distributed infrastructure and SLA-backed APIs ensure identity remains reliable as applications grow.
Developer-friendly implementation and migration support: LoginRadius offers clean APIs, SDKs, hosted experiences, low-code workflow orchestration, and structured migration tooling. Combined with enterprise-grade support and customer success engagement, this reduces integration effort and long-term maintenance compared to adapting workforce IAM platforms for CIAM.
Ideal for
-
B2B SaaS platforms requiring multi-tenant identity, delegated administration, and enterprise-grade security
-
Consumer brands operating at global scale with highly variable traffic patterns
-
Regulated industries that require compliance certifications and regional data residency
-
Organizations that want fully managed CIAM and expect identity complexity to grow over time without replatforming
3. Microsoft Entra ID (formerly Azure AD)
Microsoft Entra ID is Microsoft’s identity platform, originally built for workforce IAM and deeply integrated into the Microsoft ecosystem. It is often evaluated as a SecureAuth alternative by organizations already standardized on Azure, Microsoft 365, and Active Directory.
Where Microsoft Entra ID Performs Well
-
Strong integration with Microsoft ecosystem: Native integration with Azure services, Microsoft 365, and enterprise IT tooling makes Entra ID a natural choice for Microsoft-centric organizations.
-
Enterprise-grade security controls: Conditional access policies, MFA, and identity protection features are well suited for securing employee access to internal and cloud applications.
-
Familiar IAM model for IT teams: Organizations with existing Active Directory expertise benefit from continuity in identity concepts and administrative workflows.
CIAM Fit Analysis: Entra ID can support external identities, but its architecture and UX patterns remain workforce-first. Customer identity implementations often require workarounds to handle branding, registration flows, and consumer-grade login experiences. For large-scale CIAM use cases, teams may encounter limitations in flexibility and user experience customization.
Ideal For
-
Microsoft-first enterprises
-
Organizations extending existing workforce IAM to limited external use cases
-
Internal and partner-facing portals with modest CIAM requirements
Trade-Offs
-
Workforce-centric architecture limits CIAM UX flexibility
-
Branding and customization options are constrained
-
Not optimized for high-volume consumer identity at scale
4. Ping Identity
Ping Identity is an enterprise IAM provider with a strong legacy in federation, access management, and large-scale identity programs. It is often considered alongside SecureAuth for enterprise security initiatives.
Where Ping Identity Performs Well
-
Enterprise IAM and federation expertise: Strong support for SAML, OAuth, OIDC, and complex enterprise access scenarios.
-
Flexible deployment options: Supports cloud, hybrid, and on-prem environments to meet enterprise infrastructure requirements.
-
Advanced access control capabilities: Well-suited for organizations with complex policy and integration needs.
CIAM Fit Analysis: Ping Identity can support CIAM, but implementations are typically more complex and resource-intensive than CIAM-native platforms. Customer-facing UX, branding, and onboarding flows often require significant customization and professional services, increasing time-to-value.
Ideal For
-
Large enterprises with complex IAM programs
-
Organizations prioritizing federation and access governance
-
Teams with dedicated IAM expertise and resources
Trade-Offs
-
Higher implementation and operational complexity
-
CIAM UX customization requires significant effort
-
Slower iteration compared to CIAM-native platforms
5. Amazon Cognito
Amazon Cognito is AWS’s native identity service and is frequently evaluated by teams building applications on AWS infrastructure.
Where Amazon Cognito Performs Well
-
Native AWS integration: Seamless alignment with AWS services and infrastructure simplifies deployment for AWS-native teams.
-
Cost-effective for basic use cases: Attractive pricing for straightforward authentication and small-scale applications.
-
Managed service model: Reduces infrastructure management compared to self-hosted IAM solutions.
CIAM Fit Analysis: Cognito supports basic CIAM functionality but lacks many features expected in mature customer identity programs. Branding, UX customization, and advanced CIAM controls are limited, making it better suited for simple authentication needs rather than differentiated customer experiences.
Ideal For
-
AWS-native development teams
-
Applications with simple authentication requirements
-
Cost-sensitive projects with limited CIAM complexity
Trade-Offs
-
Limited branding and UX flexibility
-
Sparse advanced CIAM features
-
Not well suited for complex B2C or B2B identity models
Why People Switch From SecureAuth to LoginRadius
Organizations typically don’t leave SecureAuth because of security gaps. Instead, the friction emerges when SecureAuth is pushed beyond its workforce IAM roots into customer-facing scenarios.
Workforce-first design creates CIAM friction
SecureAuth excels in employee authentication, but CIAM demands flexibility, branding, and scale that workforce tools aren’t optimized for. Teams often find themselves over-customizing to bridge this gap.
Legacy complexity slows developers
Feedback from teams highlights challenges with SDK debt, complex setup, and maintenance overhead. These issues compound over time, especially as customer identity requirements evolve.
Modern UX expectations aren’t met
Customers expect passwordless login, smooth registration, and self-service account management. SecureAuth’s employee-centric UX patterns make it harder to deliver consumer-grade experiences.
LoginRadius removes these constraints by offering a CIAM platform purpose-built for customers: scalable cloud infrastructure, customizable UX, modern authentication, and built-in privacy management, all without forcing teams to repurpose workforce IAM.
SecureAuth vs LoginRadius: Key Differences at a Glance
| Capability | LoginRadius | SecureAuth |
|---|---|---|
| Primary Design Focus | Purpose-built CIAM for customers, partners, and B2B tenants | Workforce IAM focused on employee access |
| Core Use Cases | B2C apps, B2B SaaS platforms, partner portals | Internal workforce authentication |
| Architecture | Cloud-native, fully managed, multi-tenant | Workforce-centric, hybrid / on-prem-first roots |
| Scalability | Designed for millions of external users with elastic scaling | Optimized for controlled employee populations |
| Authentication Methods | Passwordless, passkeys, WebAuthn, push MFA, OTP, magic links, adaptive MFA | Strong MFA for employees; limited modern passwordless for CIAM |
| Adaptive & Risk-Based Auth | Native, CIAM-optimized risk and step-up policies | Available, but tuned for workforce security models |
| Branding & UX Control | Full customization of login, registration, emails, and flows | Limited customization for customer-facing journeys |
| Registration & User Management | Prebuilt and configurable registration, progressive profiling, self-service | Directory-centric; customer workflows require customization |
| Privacy & Consent Management | Built-in GDPR/CCPA workflows, consent and preference management | Minimal native privacy tooling for end users |
| Data Residency Options | Configurable regional data residency and geo-isolation | More limited regional flexibility |
| Developer Experience | CIAM-focused APIs, SDKs, hosted experiences, low-code orchestration | Enterprise IAM setup with higher integration complexity |
| Operational Model | Fully managed CIAM with SLA-backed APIs | Greater operational responsibility, especially for CIAM |
| Best Fit | Organizations scaling customer identity and expecting complexity to grow | Enterprises securing internal workforce access |
Conclusion
SecureAuth remains a strong option for workforce IAM, especially in security-conscious enterprise environments. However, as customer identity requirements grow more complex, many teams find that stretching workforce IAM into CIAM introduces unnecessary friction.
Modern CIAM demands scalability, flexibility, and user-centric design. Organizations evaluating SecureAuth alternatives should prioritize platforms that were designed specifically for customer identity, rather than adapted to it.
LoginRadius stands out as a purpose-built CIAM platform that balances security, UX, developer experience, and compliance at scale. For teams building consumer apps, B2B SaaS platforms, or partner ecosystems, it’s a solution worth shortlisting early in the evaluation process.
If you’re evaluating alternatives to SecureAuth for customer identity, we recommend reviewing a detailed feature comparison and discussing your use case with a CIAM specialist. Our team can help you assess fit, migration paths, and architecture considerations before you commit.