Quick Summary
-
SAML is an XML-based federation protocol designed in the early 2000s, still dominant for browser-based enterprise SSO (think HR, CRM, internal tools).
-
OIDC (OpenID Connect) is a modern identity layer on top of OAuth 2.0, using JSON and JWTs, ideal for APIs, SPAs, and mobile apps.
-
Both are secure and mature; the decision is mainly about ecosystem fit, client types, and your modernization roadmap, not which is “more secure” in the abstract.
-
Most enterprises end up running SAML + OIDC together, using an identity platform like LoginRadius as the hub to broker SSO across old and new applications.
-
LoginRadius supports SAML, OIDC, OAuth 2.0, and JWT-based federated SSO, with prebuilt connectors and an Admin Console to configure assertions, claims, flows, and logout policies centrally.
Introduction
Single sign-on (SSO) often comes down to choosing the right authentication standard, and most organizations evaluate SAML vs OIDC when designing or modernizing their identity strategy. Both protocols support federated authentication, but they were created for different eras and application models.
SAML, established in the early 2000s, remains a dominant standard for enterprise SSO, relying on XML-based assertions and long-standing trust frameworks across workforce and SaaS applications. OpenID Connect (OIDC), a newer, lightweight identity layer built on OAuth 2.0, uses JSON and JWTs to support modern web, mobile, and API-driven environments.
While OpenID Connect vs SAML comparisons often focus on high-level similarities, the protocols differ significantly in workflow, integration patterns, and long-term scalability. Understanding those differences is essential for choosing the right approach for your architecture today and the roadmap you’re building toward.
Quick Comparison: SAML vs OIDC at a Glance
Although both SAML and OIDC enable federated authentication, they differ in format, design goals, and the types of applications they were intended to support. The following table summarizes these differences before we examine each protocol in detail.
| Aspect | SAML (Security Assertion Markup Language) | OIDC (OpenID Connect) |
|---|---|---|
| Primary purpose | Federated authentication and SSO for browser-based applications | Federated authentication for web, mobile, and API-based applications |
| Era / maturity | Early 2000s; long-standing enterprise SSO standard | 2014+; newer protocol built as an identity layer on top of OAuth 2.0 |
| Data / token format | XML-based SAML assertions | JSON-based ID Tokens (JWT) and Access Tokens |
| Built on | Independent standard with its own bindings and profiles | Extends OAuth 2.0 with an identity layer |
| Typical client types | Browser-based enterprise and SaaS apps | Web apps, SPAs, native/mobile apps, API clients |
| Common use cases | Workforce SSO, B2E portals, older and traditional SaaS integrations | Customer and partner apps, B2B SaaS, mobile-first and cloud-native architectures |
| Integration experience | XML-heavy; often configured via enterprise IdP products | JSON/JWT-based; strong SDK and framework support |
| Token consumption | Primarily consumed by web apps via browser redirects/posts | Consumed by web backends, APIs, mobile apps, and microservices |
| Strengths | Mature, widely supported in enterprise, strong fit for legacy SSO | Lightweight, flexible, well-suited for modern web, mobile, and API-driven environments |
| Typical confusion point | Often treated as the only “SSO standard” in older environments | Often conflated with OAuth in “OIDC vs SAML vs OAuth” discussions |
What is SAML?
Security Assertion Markup Language (SAML) is an XML-based federation standard designed to let an identity provider (IdP) authenticate a user and securely pass that result to a service provider (SP). Introduced in the early 2000s, SAML became the default for enterprise single sign-on (SSO) because it allowed organizations to centralize authentication while distributing access across multiple browser-based applications.
The SAML assertion (the signed XML document returned by the IdP) is the core artifact that applications trust. It contains the user’s identity information, optional attributes, and conditions that govern when and how the assertion can be used.
Read more: LoginRadius SSO product overview
How Does SAML Authentication Flow Work?
SAML’s design reflects the web environment it was created for, meaning browser redirects, form posts, and server-validated XML signatures. A typical SAML authentication flow looks like this:
-
The user attempts to access an application that relies on an external IdP.
-
The application (SP) redirects the user to the IdP’s SAML SSO endpoint.
-
The IdP authenticates the user with its own policies (password, MFA, risk checks, etc.).
-
Once authenticated, the IdP generates a signed SAML assertion containing user identity data and session details.
-
The assertion is returned to the SP via a browser POST or redirect binding.
-
The SP validates the XML signature, checks the assertion conditions, and creates a local session.
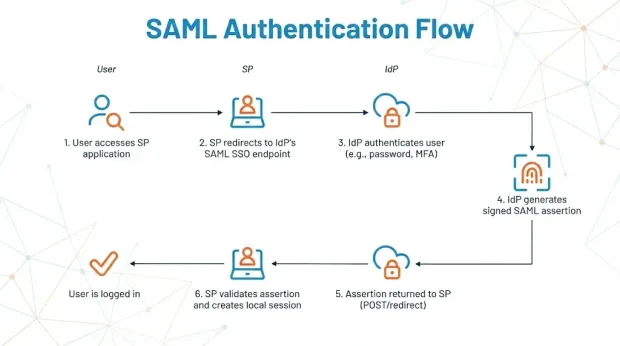
This model enables federated authentication without requiring the SP to store or verify user credentials. It also explains why SAML is still dominant across enterprise SaaS products, even as newer standards emerge.
Some Common SAML Use Cases
SAML remains widely used because many platforms and identity ecosystems were built around its assumptions: browser-based access, enterprise directories, and centralized IdPs. Some common scenarios include:
1. Enterprise SaaS and Workforce Applications
HR systems, CRM platforms, productivity tools, ITSM solutions, and internal portals often rely on SAML 2.0. These applications typically expect a long-standing IdP relationship and stable XML-based assertions for workforce SSO.
2. Government and Regulated Environments
SAML’s structured schema and predictable assertion format make it suitable for public sector frameworks that require consistent auditing, identity assurance, and cross-agency interoperability.
3. Business-to-Employee (B2E) Portals
Legacy internal applications, especially those predating mobile-first or API-first development, commonly depend on SP-initiated or IdP-initiated SAML flows to provide centralized workforce access.
What is OpenID Connect (OIDC)?
OpenID Connect (OIDC) is an identity protocol that sits on top of OAuth 2.0 to provide authenticated user identity information in a standardized way. OAuth 2.0 handles authorization by granting limited access to resources, while OIDC adds a reliable method for applications to verify who the user is. This separation is what makes OIDC a preferred choice for modern architectures: it brings identity into environments built around APIs, microservices, and mobile-first interactions.
OIDC accomplishes this through lightweight, JSON-based messages, making it significantly easier to integrate than XML-driven federation protocols. In openid connect vs saml evaluations, this distinction is one of the primary reasons OIDC is now ubiquitous in cloud-native applications.
Also read: LoginRadius OAuth 2.0 overview
Understanding ID Tokens, Access Tokens, and JWTs
At the center of the OIDC protocol are a set of token types that applications use for authentication and API authorization:
-
ID Token: A signed JSON Web Token (JWT) that carries verified user identity information (“claims”).
-
Access Token: Issued alongside the ID Token to authorize access to APIs. While technically part of OAuth 2.0, it is commonly used in OIDC-based architectures to support both authentication and delegated authorization.
-
JWT (JSON Web Token): The format used for OIDC tokens. JWTs are compact, easy to validate, and compatible with a wide range of languages and frameworks, especially important for SPAs, mobile clients, and microservices.
Together, these tokens reduce parsing overhead and simplify how identity propagates between front-end and back-end components. This design pattern is a large part of why OIDC has become the preferred alternative in the wider saml vs oidc comparison.
How Does OIDC Work?
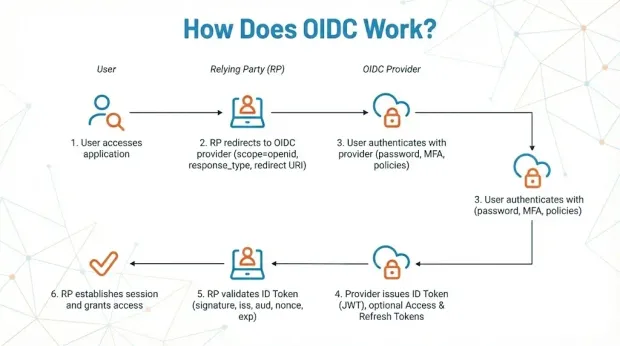
OpenID Connect (OIDC) works by allowing an application to verify a user’s identity through an external identity provider using OAuth 2.0 flows. Instead of the application authenticating the user directly, the identity provider performs the authentication and returns standardized tokens (primarily the ID Token, formatted as a JWT) that confirm who the user is.
Usually, the OIDC protocol follows this sequence:
-
The application (Relying Party) redirects the user to the OIDC provider: The request specifies the desired scope (commonly openid), the response type, and a redirect URI where tokens should be returned.
-
The user authenticates with the identity provider: The provider handles all authentication logic, like password, MFA, risk checks, or any other configured policy.
-
The identity provider issues tokens: After successful authentication, the provider returns:
- An ID Token (JWT containing user identity claims)
- Optionally an Access Token for API authorization
- A Refresh Token in flows where long-lived sessions are required
-
The application validates the ID Token: The application checks the token signature, issuer (
iss), audience (aud), nonce, and expiration to verify authenticity and integrity. -
The application establishes a session: Once the ID Token is validated, the application creates its own session and grants the user access, without ever handling credentials.
Common OIDC Flows for Modern Web, SPA, and Mobile Applications
OIDC supports multiple authorization flows to accommodate modern client types, each designed to address specific security requirements:
1. Authorization Code Flow
Used for traditional web applications. The application exchanges an authorization code for tokens securely on the server side. This is typically the default model for server-rendered apps.
2. Authorization Code Flow with PKCE
Used by SPAs and mobile apps where a client secret cannot be securely stored. PKCE (Proof Key for Code Exchange) prevents interception attacks and is now the recommended approach for public clients. This flow is one of the reasons developers increasingly choose OIDC when comparing saml vs oidc vs oauth in mobile-first environments.
3. Hybrid Flow
Used in certain implementations where applications need token information earlier in the authentication sequence, but still maintain the security of server-side token retrieval.
These flows reflect the environments OIDC was designed for—API-connected clients, distributed front ends, and mobile experiences where browser-based assumptions no longer apply.
Key Differences Between SAML and OIDC
Understanding the difference between SAML and OIDC is essential when deciding how to support legacy applications, modern web platforms, and mobile-first experiences within a unified identity strategy.
Below are the core distinctions that matter in practice.
1. Token Format and Data Structure
SAML uses XML-based assertions. These assertions are verbose, signed using XML Signature, and typically transported through browser redirects or form posts.
OIDC, by contrast, uses compact JSON Web Tokens (JWTs) for ID Tokens and often for Access Tokens. JWTs are easier for modern applications, especially SPAs, APIs, and mobile clients to parse and validate.
Why it matters:
-
XML favors older enterprise stacks and server-rendered web apps.
-
JSON/JWT aligns with microservices, API gateways, and distributed front ends.
Also read: A Complete Guide to JSON Web Token (JWT) and How It Works
2. Protocol Foundations and Purpose
SAML is a standalone federation standard focused solely on authentication and attribute exchange for browser-based SSO.
OIDC is an identity layer on top of OAuth 2.0, inheriting modern authorization flows while adding a standardized way to communicate user identity.
Why it matters:
In openid connect vs saml comparisons, OIDC’s OAuth 2.0 foundation makes it more suitable for ecosystems where clients, APIs, and services need consistent token behavior.
3. Application and Client Compatibility
SAML was designed for traditional browser SSO. Most implementations assume full-page redirects and server-side processing.
OIDC supports a range of client types, from traditional web apps, SPAs, mobile apps, to native applications through flows like Authorization Code with PKCE.
Why it matters:
-
SAML fits established enterprise SaaS and B2E portals.
-
OIDC fits API-first, mobile-first, and cloud-native applications.
4. Integration Experience and Developer Workflow
Integrating SAML often involves configuring XML metadata files, mapping attributes, and working with more rigid IdP/SP templates.
Integrating OIDC is typically lighter: developers rely on well-supported libraries, JSON parsing, standardized discovery endpoints, and broadly available SDKs.
Why it matters:
OIDC reduces implementation overhead, especially for teams adopting modern frameworks or building distributed systems.
5. Session Management and Logout Behavior
SAML uses front-channel single logout (SLO), relying on browser redirects between the IdP and SPs. Coordination issues often arise when multiple SPs are involved.
OIDC supports front-channel and back-channel logout options defined through the OAuth 2.0 ecosystem, allowing more predictable handling of distributed sessions.
Why it matters:
OIDC provides more flexibility for multi-application environments where consistent logout behavior is critical.
6. Alignment With Modern Security Patterns
Both protocols can be highly secure when correctly implemented, but their default patterns differ:
-
SAML relies on XML Signature and canonicalization, which can be complex and error-prone.
-
OIDC relies on JOSE standards (JWS, JWK), which align with modern cryptographic libraries and are simpler to implement across languages.
Why it matters:
This impacts long-term maintainability and reduces risk in environments where identity systems must support continuous updates.
7. Fit Within Legacy vs Modern Environments
SAML is widely supported across older enterprise systems and remains essential for workforce SSO.
OIDC is increasingly expected in modern SaaS ecosystems, developer platforms, and customer-facing products.
Why it matters:
Most organizations end up running both SAML for legacy compatibility and OIDC for modern growth. This is where federation hubs or modern CIAM platforms become important.
OIDC vs SAML: Clearing Up What to Choose
Choosing between SAML and OIDC depends less on which protocol is “better” and more on the type of applications you support, how users access them, and the broader identity architecture you’re building. Find out below each protocol is the more appropriate choice.
When to Choose SAML
1. You Support Established Enterprise Applications
Many workforce and B2E applications, like HR systems, CRM platforms, ITSM tools, and productivity suites were built with SAML 2.0 as their primary federation option. If your environment includes a significant number of these systems, SAML remains the most compatible and lowest-friction choice.
Why it fits: SAML’s XML assertions and long-standing IdP/SP expectations align directly with enterprise SSO patterns.
2. Your Authentication Model Is Browser-Centric
SAML’s design assumes full browser redirects and server-side session handling. If your organization primarily uses web-based applications accessed through standard browsers, the SAML workflow remains efficient and predictable.
Why it fits: Browser-oriented SSO is where SAML continues to provide stable federation without requiring architectural changes.
Learn more about SAML: LoginRadius SAML Configuration Guide
3. You Operate in Regulated or Government Environments
Government agencies and regulated sectors often rely on SAML-based trust frameworks that emphasize standardized XML schemas, well-defined assertion structures, and predictable auditing models.
Why it fits: SAML’s maturity and interoperability align with long-established compliance requirements.
4. Legacy Applications Must Remain Unchanged
If you maintain applications that cannot be refactored to support newer authentication methods, SAML provides a reliable way to keep these systems integrated while modernizing the identity layer elsewhere.
Why it fits: Organizations can centralize authentication through SAML while progressively adding OIDC for newer applications.
When to Choose OIDC
1. You Build or Support Modern Web, Mobile, or API-Driven Applications
OIDC’s JSON-based ID Tokens and OAuth 2.0 foundation make it a natural fit for modern application architectures, like SPA frameworks, native mobile apps, cloud-native services, and distributed APIs.
Why it fits: The OIDC protocol supports token validation directly in backend services and client applications using lightweight libraries.
Learn more about OIDC: LoginRadius OIDC Documentation
2. You Need Smooth Integration With Microservices or API Gateways
OIDC tokens (JWTs) are validated locally by microservices or gateways without redirect-heavy browser flows. This is a major difference in the saml vs oidc comparison, especially when services operate independently.
Why it fits: JSON tokens align tightly with modern service-to-service communication patterns.
3. Your User Journeys Are Mobile-First or Multi-Device
OIDC flows such as Authorization Code with PKCE were designed specifically for public clients that cannot securely store secrets on mobile apps, SPAs, and desktop clients.
Why it fits: OIDC allows consistent authentication across devices without relying on browser redirects.
4. You Want Greater Flexibility for Future Growth
If part of your strategy involves expanding APIs, supporting partner integrations, or delivering features across multiple channels, OIDC provides a more adaptable base than XML-bound SAML.
Why it fits: OIDC’s flexibility helps prevent architectural constraints as your platform grows, especially relevant in openid connect vs saml evaluations.
When Each Protocol Fits Best
Choose SAML if:
-
Your application ecosystem is browser-based and enterprise-heavy
-
You rely on mature SaaS platforms that only support SAML
-
Compliance and XML-based governance frameworks influence your deployment
-
You need stable compatibility with legacy systems
Choose OIDC if:
-
Your architecture is cloud-native, API-driven, or mobile-first
-
You need flexible flows across web, SPA, and native apps
-
You want lightweight token formats suited to distributed systems
-
You plan to grow through modern developer integrations or partner APIs
Why Most Organizations Use Both SAML and OIDC
Even though companies often frame the decision as SAML vs OIDC, the reality is that most identity ecosystems include applications built across different eras and architectures. As a result, organizations rarely adopt one protocol exclusively. Instead, they use both, depending on what each application supports and how users interact with the system.
Legacy Applications Still Depend on SAML
Many established enterprise applications were built during a period when SAML 2.0 was the default method for federated authentication. These systems still expect XML-based assertions, metadata configuration, and browser redirects as part of their normal workflow.
Examples include:
-
HRIS and payroll platforms
-
Internal portals and department-level applications
-
Legacy CRM and ITSM systems
-
Older SaaS tools with limited support for newer protocols
Why this persists: Rebuilding or replatforming these applications is often costly or unrealistic. Maintaining SAML support ensures stability while broader modernization efforts continue.
Modern Applications Expect OIDC
Newer SaaS products, cloud-native services, mobile apps, and developer-facing platforms typically support OIDC as their primary authentication method. These systems assume OAuth 2.0 flows, JSON-based tokens, and client types that operate outside the assumptions of traditional browser-based SSO.
Typical examples include:
-
Customer or partner portals
-
SPAs built with React, Angular, Vue
-
iOS and Android mobile apps
-
API gateways and microservices architectures
Why this trend continues: OIDC’s flexibility, token formats, and broad SDK support make it ideal for distributed systems.
Identity Providers Must Bridge Both Protocols
IdPs now serve as the translation layer between ecosystems that rely on SAML and those built on OIDC. Instead of forcing all applications to adopt a single protocol, organizations centralize authentication at the IdP and maintain protocol-specific connections at the edges.
This approach avoids duplicate identity stores, inconsistent session handling, and custom integration work in every application.
Why a Hybrid Model is Often the Best Path Forward
A hybrid model supports immediate compatibility and long-term modernization:
-
No disruption to legacy systems that rely on SAML
-
Immediate support for modern apps that expect OIDC
-
Consistent authentication policies, MFA, and risk-based controls applied across both
-
Centralized user management without protocol fragmentation
-
Gradual migration of older applications to newer standards when feasible
This hybrid reality is also what makes the broader difference between SAML and OIDC discussion meaningful—each protocol excels in different layers of the identity stack, and most organizations need both to maintain continuity while enabling growth.
Summary
SAML and OIDC are not competing standards in most environments. Rather they complement each other.
-
SAML ensures compatibility with existing enterprise applications.
-
OIDC enables modern, API-driven experiences
A unified identity layer that handles both protocols eliminates fragmentation and creates a clear path toward a more flexible and future-proof authentication architecture.
Modernizing a SAML-Heavy Environment With OIDC Support
Environments b uilt around SAML often reach a point where newer applications, mobile experiences, or API-driven services require OIDC instead of XML-based federation.
Modernizing such environments doesn’t mean replacing existing SAML integrations. Instead, it involves layering OIDC alongside SAML so that applications can adopt the protocol that matches their architecture while maintaining consistent authentication policies.
This approach reflects the practical reality behind most saml vs oidc modernization decisions: both protocols remain relevant, but their roles shift over time.
Mapping Applications, Protocols, and Integration Requirements
A structured modernization plan begins with understanding which applications rely on SAML, which can support OIDC, and where architectural constraints influence protocol choices. This typically includes:
-
Cataloging existing SAML integrations: Many enterprise applications still support SAML 2.0 exclusively, particularly internal portals, department tools, and legacy SaaS services.
-
Identifying applications capable of OIDC adoption: Modern SaaS platforms, SPAs, and mobile applications often already support OAuth 2.0 and OIDC flows.
-
Reviewing partner or tenant expectations: Some partners require SAML-based SSO from their IdPs, while others rely on OIDC discovery mechanisms.
-
Documenting user journeys: Browser-centric workflows tend to align with SAML; distributed or device-based experiences favor OIDC.
Introducing OIDC Without Disrupting Existing SAML Integrations
In most modernization efforts, OIDC is added incrementally rather than replacing SAML outright. Applications that already rely on SAML continue using it, while new or replatformed services adopt OIDC. This avoids reengineering existing systems and allows organizations to support modern authentication workflows without breaking established connections.
Key considerations when introducing OIDC include:
-
Maintaining SAML for applications that depend on XML assertions: These systems typically use established SAML metadata, signing keys, and IdP-initiated or SP-initiated flows.
-
Configuring OIDC for new applications that prefer JSON tokens: This is particularly relevant for SPAs, mobile clients, and API-based architectures supported by OAuth 2.0.
-
Ensuring policy consistency across protocols: Even though SAML and OIDC differ technically, authentication rules, MFA requirements, and session policies should remain unified at the identity layer.
-
Avoiding protocol-specific logic in applications: By centralizing SAML and OIDC configuration in one identity platform, applications only need to integrate once and do not manage protocol details themselves.
Strengthening Authentication Across Both Protocols
As organizations support both SAML and OIDC during modernization, authentication policies must remain consistent across protocols. The underlying standards differ—XML assertions for SAML and JSON-based ID Tokens for OIDC, but users should experience the same level of assurance regardless of how an application authenticates. Centralizing security controls at the identity layer ensures that both protocols follow the same verification, risk evaluation, and session policies.
A unified approach typically includes three components:
1. Consistent Use of MFA at the Identity Provider
Whether an application relies on SAML or OIDC, multi-factor authentication (MFA) should be applied at the identity provider rather than inside individual applications. This ensures that:
-
Users encounter the same MFA requirements across legacy and modern systems
-
Application teams do not implement protocol-specific MFA logic
-
Policy updates (e.g., enabling or enforcing MFA) cascade uniformly across all integrations
This retains a consistent user experience even when authentication flows differ behind the scenes.
2. Applying Adaptive or Risk-Based Authentication Uniformly
Adaptive authentication adds another layer of protection by evaluating contextual signals such as device, IP reputation, or unusual access patterns. When managed centrally, these controls apply to:
-
SAML-based logins returning XML assertions
-
OIDC-based logins returning ID Tokens
This creates uniform enforcement regardless of protocol and avoids fragmented security behavior.
3. Maintaining Session and Logout Consistency
Because SAML and OIDC define sessions differently, maintaining a consistent user experience requires central coordination. This includes:
-
Standardized session duration and renewal behavior
-
Coordinated logout flows across applications
-
Clear reauthentication requirements for sensitive actions
Handling these policies at the identity layer avoids protocol-specific inconsistencies and prevents applications from managing sessions independently.
How LoginRadius Functions as a Central Identity Hub
SAML and OIDC often coexist in the same environment, which creates operational complexity if each application has to manage its own protocol-specific integration. A central identity platform simplifies this by acting as an intermediary between applications and external identity providers. LoginRadius operates in this role by supporting both SAML 1.1/2.0 and OIDC within a single configuration framework.
Rather than having each application maintain direct trust relationships, LoginRadius becomes the point where SAML metadata, OIDC discovery details, token settings, and session policies are managed. Applications connect once, and LoginRadius handles the underlying protocol requirements for each connection. This is particularly useful in environments evaluating saml vs oidc adoption because both protocols can remain active without complicating application architecture.
LoginRadius also centralizes user profiles, authentication policies, and multi-factor flows, ensuring consistent behavior regardless of the protocol an application uses. This avoids the fragmented experience that typically develops when each system implements its own federation logic.
Supporting Partner IAM in Mixed SAML and OIDC Environments
Partner and tenant ecosystems introduce additional complexity because external organizations often bring their own identity providers. Some rely on SAML-based enterprise IdPs; others use OIDC for their developer platforms, cloud services, or modern SSO systems. A flexible identity layer needs to accommodate both without imposing requirements on partners.
LoginRadius supports these scenarios by allowing administrators to configure external IdPs using either SAML or OIDC. Each connection can be managed independently, including endpoints, certificates, scopes, and claim/attribute mappings. This allows partners to authenticate using their existing identity systems while the application receives a normalized set of user attributes through LoginRadius.
Also read: Adding Partner IAM With LoginRadius: A Complete Guide to B2B Identity Management
For multi-tenant B2B applications, this decouples partner-specific configurations from the core platform. Each tenant can be onboarded using their preferred protocol, while the application interacts only with LoginRadius as the consistent identity interface. This reduces onboarding time and avoids embedding protocol-specific logic into the product.
Sign up for a Free Forever account with LoginRadius and start implementing SAML or OIDC SSO through LoginRadius today. Have questions about your specific use case? Speak with our identity specialists for support and implementation guidance.
FAQs
1. What is SAML and how does it work in single sign-on?
SAML (Security Assertion Markup Language) is an XML-based federation standard used to enable single sign-on (SSO) between an identity provider and a service provider. The identity provider authenticates the user and issues a signed SAML assertion, which the service provider validates to establish a session. This allows users to access multiple applications without re-entering credentials.
2. What is OpenID Connect (OIDC) and how is it different from OAuth 2.0?
OpenID Connect (OIDC) is an identity layer built on top of OAuth 2.0. While OAuth 2.0 authorizes access to resources, OIDC adds a standardized way for applications to verify user identity using ID Tokens formatted as JSON Web Tokens (JWTs). This makes OIDC suitable for modern web, mobile, and API-driven applications that need both authentication and authorization.
3. How does OIDC authenticate users?
OIDC authenticates users by redirecting them to an identity provider that performs the login. After successful authentication, the provider issues an ID Token containing verified identity claims and may also issue Access Tokens for API authorization. The application validates the ID Token and uses it to establish a session without handling user credentials directly.
4. Which OIDC flows are commonly used for web, SPA, and mobile apps?
OIDC supports multiple flows to match different application types. Traditional web applications typically use the Authorization Code Flow. SPAs and mobile applications use Authorization Code with PKCE for added security, because secrets cannot be stored safely on client devices. Hybrid Flow is sometimes used when applications need token information earlier in the authentication process.
5. What is the main difference between SAML and OIDC?
The core difference is in design and data format. SAML uses XML-based assertions and was created for browser-based enterprise SSO. OIDC uses JSON Web Tokens (JWTs) and extends OAuth 2.0, making it better suited for modern, API-driven, and mobile applications. Both provide federated authentication, but each aligns with different architectural eras and use cases.
6. When should I use SAML instead of OIDC?
SAML is typically the right choice when integrating with older enterprise systems or SaaS platforms that support SAML 2.0. It is well suited for browser-based workforce applications, government systems, and internal portals that rely on XML assertions and established trust models. SAML remains widely used in environments where long-standing SSO patterns are already in place.
7. When is OIDC a better choice than SAML?
OIDC is a better fit for modern web, mobile, and API-driven applications. Its JSON-based tokens and OAuth 2.0 foundation make it easier to integrate with SPAs, native mobile apps, microservices, and cloud-native platforms. OIDC is also preferred when applications require flexible token validation and support across distributed architectures.
8. Why do organizations often use both SAML and OIDC?
Most environments support applications built across different eras. Older systems rely on SAML, while newer applications expect OIDC. Running both allows organizations to maintain compatibility with legacy platforms while adopting modern authentication standards for new development. A centralized identity layer ensures consistent security and user experience across both protocols.
9. How can I modernize a SAML-only environment to support OIDC?
Modernization usually involves identifying which existing applications must keep SAML and introducing OIDC for new or re-architected services. Organizations often run both protocols in parallel, using a central identity platform to enforce consistent authentication policies. This approach avoids disrupting legacy systems while enabling gradual adoption of OAuth 2.0–based workflows.
10. Can SAML and OIDC coexist in the same identity architecture?
Yes. SAML and OIDC often coexist in hybrid identity architectures. Legacy systems continue using SAML while newer applications adopt OIDC. An identity platform can manage protocol-specific configurations, apply uniform authentication policies, and unify user experiences. This approach supports modernization without requiring all applications to migrate simultaneously.
11. What role does an identity hub play in managing SAML and OIDC?
An identity hub centralizes authentication logic so applications do not need to implement protocol-specific flows. It manages SAML metadata, OIDC discovery endpoints, certificates, claims, and session policies. This reduces integration complexity and ensures a consistent authentication experience across systems that use different protocols.
12. How does LoginRadius support both SAML and OIDC?
LoginRadius supports SAML 1.1/2.0 and OIDC within its identity platform. Organizations configure SAML and OIDC connections through the Admin Console, and applications authenticate through LoginRadius instead of managing each protocol directly. This allows SAML-based and OIDC-based applications to operate simultaneously while sharing consistent MFA, session, and policy controls.
13. Is it difficult to implement SAML or OIDC SSO without an identity platform?
Implementing SAML or OIDC directly inside applications can be challenging because each protocol requires its own token handling, certificate management, and security considerations. An identity platform centralizes these responsibilities, reducing integration overhead and ensuring consistent authentication behavior across systems.
14. Can I onboard partners or tenants using either SAML or OIDC?
Yes. Many partners and tenants use their own identity providers, and these may support either SAML or OIDC. With a flexible identity platform like LoginRadius, each tenant can authenticate using the protocol they already support while your application integrates only once. This simplifies partner onboarding and keeps protocol logic centralized.
15. Does using OIDC mean replacing all existing SAML integrations?
No. OIDC does not replace SAML. Most organizations keep SAML active for systems that depend on it and use OIDC for new applications. A hybrid approach avoids costly rewrites while allowing teams to adopt modern OAuth 2.0–based patterns where appropria



