Introduction: Why Authorization Services Are Business-Critical
In today’s digital-first economy, organizations handle millions of user interactions daily. Every login, transaction, or data request carries a security risk if not properly authorized. That’s why authorization services have become an essential layer of modern cybersecurity and customer identity access management (CIAM). Unlike authentication, which verifies identity, authorization ensures that users only access the data and applications they are permitted to.
The stakes are higher than ever. Gartner predicts that by 2026, 70% of organizations will implement context-based authorization to reduce insider risks. As digital ecosystems expand across apps, APIs, and third-party integrations, fragmented authorization approaches leave dangerous security gaps.
With growing data regulations and sophisticated cyber threats, businesses need scalable, secure, and flexible solutions. This is where Auth as a Service enters the picture—an approach that abstracts away the complexity of policy management while ensuring compliance and seamless user experience.
This blog explores what authorization services are, why organizations are shifting toward cloud-based authorization solutions, and how LoginRadius simplifies enterprise security through its cIAM Authorization Service.
For a detailed breakdown, don’t miss the LoginRadius cIAM Authorization Service Guide:
What is an Authorization Service?
An authorization service is a security framework that determines whether a user has permission to access a particular resource. While authentication answers “Who are you?”, authorization answers “What can you do?”.
For example, within an online banking system, authentication grants you access to your account, while authorization ensures you can only view your own transactions, not someone else’s. This safeguard is critical to prevent insider threats and data misuse.
Traditional authorization models were rigid, with access rules hard-coded into applications. This meant every policy change required developer intervention, slowing innovation and increasing costs. Modern authorization solutions solve this by externalizing access policies, enabling IT teams to apply updates dynamically.
Organizations now adopt models like role-based access control (RBAC), where users inherit permissions through roles, and attribute-based access control (ABAC), which evaluates contextual attributes like location or device type. Emerging trends even point toward policy-driven zero-trust authorization where every request is verified in real-time.
Learn more about how authentication and authorization differ and why both are essential in IAM.
Benefits of Auth as a Service for Enterprises
Auth as a Service gives organizations a cloud-native way to manage authorization policies centrally without rebuilding them for every application. It eliminates the need for multiple access control systems, reducing fragmentation and enhancing security consistency.
Key benefits include:
-
Scalability: Handle millions of user requests without latency, supporting both consumer-facing and internal systems.
-
Compliance: Enforce strict data-access controls to meet GDPR, HIPAA, PCI DSS, and CCPA requirements, reducing audit headaches.
-
Cost Efficiency: Eliminate the overhead of coding authorization into each application, freeing developers to focus on core features.
-
Agility: Quickly adapt policies to evolving roles, regulations, or risk factors without code changes.
-
User Trust: Build confidence among customers by offering seamless yet secure experiences.
For enterprises in finance, healthcare, and eCommerce, Auth as a Service provides both business agility and regulatory alignment. In industries where trust equals revenue, even minor breaches can cost millions.
Pairing Auth as a Service with strong authentication methods like MFA creates a layered defense model, aligning with zero-trust security frameworks.
Authorization Solutions: Modern Security for Complex Infrastructures
Enterprises often run hybrid IT environments—mixing on-premises systems, SaaS applications, APIs, and partner integrations. Managing authorization consistently across such ecosystems is a challenge, especially when user identities need to be recognized across multiple platforms.
That’s where modern authorization solutions come in. The LoginRadius Authorization Service addresses this with:
-
Single Sign-On (SSO): A frictionless experience with one identity across all applications.
-
Federation: Accept partner-issued identities through standards like SAML, JWT, and OAuth 2.0.
-
Role-Based Authorization: Define user hierarchies and assign privileges dynamically.
-
Account Linking: Merge multiple social and enterprise accounts into unified profiles.
-
Social Access Integration: Extend engagement through permission-based interactions with linked networks.
In addition, these solutions support contextual authorization—deciding access based on signals such as device health, location, and behavioral patterns. This makes them invaluable for implementing zero-trust security, where no request is inherently trusted.
By combining authorization with multi-factor authentication (MFA) and OAuth 2.0, businesses gain the flexibility to secure both customer-facing and internal applications seamlessly.
CIAM and Authorization: Why They Matter Together
Customer Identity and Access Management (CIAM) is designed to balance user experience with enterprise-grade security. While authentication verifies users, authorization determines their permissions—making it a critical CIAM component.
With the LoginRadius cIAM Authorization Service, enterprises can:
- Define granular access policies using RBAC, ABAC, or contextual factors. Here’s how easy it is in the LoginRadius admin console:
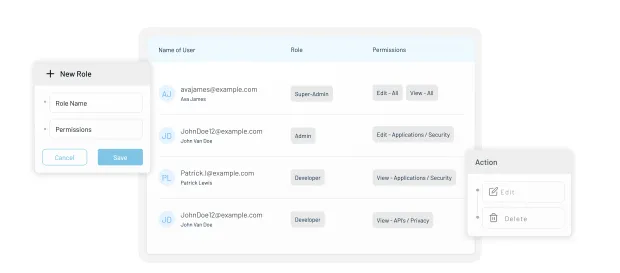
-
Deploy Single Sign-On (SSO) across digital ecosystems.
-
Leverage federation capabilities for smoother partner integrations.
-
Apply zero-trust security by validating every access attempt dynamically.
In highly regulated industries like healthcare and finance, CIAM authorization isn’t optional—it’s mandatory for compliance. For instance, HIPAA requires healthcare organizations to restrict patient data access based on job role, while PCI DSS enforces strict control over who can handle payment card data.
Beyond compliance, authorization also supports personalized experiences. By segmenting users into roles, businesses can deliver relevant content, offers, and services while maintaining strict boundaries. For context, explore how access control in security enhances digital trust.
Real-World Use Cases of Authorization Services
Authorization services aren’t just theory—they power critical business scenarios daily:
-
eCommerce: Customers can view only their orders, while admins can manage inventory without accessing payment details.
-
Healthcare: Doctors view patient medical histories; receptionists see appointment data but not sensitive records.
-
Finance: Accountants manage ledgers while traders execute deals, ensuring compliance with SOX regulations.
-
B2B SaaS: Channel partners access collaboration portals without seeing client-specific data.
-
Education: Students access course materials, while faculty manage grading and compliance tools.
These examples highlight how authorization prevents privilege creep and enforces least-privilege access, a core zero-trust principle.
Businesses using centralized authorization avoid inconsistencies that arise from multiple access models. They also improve compliance readiness, as regulators increasingly demand demonstrable access control.
For a deeper look, see this guide to role-based access control (RBAC).
How LoginRadius cIAM Authorization Service Simplifies Security
The LoginRadius cIAM Authorization Service combines enterprise-grade security with developer-friendly deployment, making it a practical choice for modern organizations.
Core features include:
-
Single Sign-On (SSO): Unified login for web and mobile apps, reducing friction.
-
Role-Based Authorization: Hierarchies that assign and manage permissions directly from the dashboard.
-
Federation: Support for popular protocols like SAML 1.1/2.0, JWT, and OAuth 2.0, enabling partner integrations.
-
Account Linking: Merge multiple social and enterprise logins under one identity.
-
Social Network Access: Permission-based engagement across customer social accounts.
As outlined in the Authorization Service PDF, these features create a single customer view, improve loyalty, and simplify compliance with global privacy standards:
Unlike rigid legacy systems, LoginRadius provides APIs and SDKs for easy integration, making it developer-friendly. Its global infrastructure ensures low latency even at scale, serving billions of monthly logins.
By adopting LoginRadius, businesses gain a secure, scalable, and future-proof authorization layer that aligns with zero-trust frameworks.
Conclusion: Secure the Future with Authorization as a Service
The digital economy demands more than identity verification—it requires authorization services that dynamically enforce access rules across hybrid ecosystems. Businesses adopting Auth as a Service and advanced authorization solutions gain stronger compliance, reduced risk, and improved user trust.
The LoginRadius cIAM Authorization Service unifies Single Sign-On, Federation, Role-Based Authorization, and Account Linking into one powerful platform. It enables enterprises to deliver seamless customer journeys without sacrificing security.
By embracing zero-trust security models and leveraging LoginRadius’ globally scalable infrastructure, enterprises can prepare for the future of identity and access management.
👉 Ready to see it in action? Contact us to discover how LoginRadius can help secure your enterprise with future-ready authorization.
FAQs
1. What’s the difference between authentication and authorization?
Authentication verifies identity; authorization defines permissions. Learn more in this detailed guide.
2. Why do businesses need Auth as a Service?
It reduces complexity, ensures compliance, and centralizes policy management across hybrid IT environments while lowering development costs.
3. How do authorization solutions support compliance?
By enforcing strict access policies (RBAC, ABAC), they align with GDPR, HIPAA, PCI DSS, and SOC 2 requirements.
4. Can authorization services integrate with MFA?
Yes—and they should. Pairing MFA with authorization enhances defense against breaches and credential stuffing.
5. What industries benefit most?
Finance, healthcare, SaaS, government, and eCommerce rely heavily on secure authorization to protect sensitive data.
6. Does LoginRadius support federation with partner systems?
Yes. LoginRadius supports federation protocols such as SAML, JWT, and OAuth 2.0, ensuring seamless partner identity integrations.