Introduction
You’ve likely typed a password today, maybe even the same one you’ve been using for years. For most of us, passwords are a routine part of logging in to devices, apps, and services. But they’re also one of the weakest links in cybersecurity.
They can be forgotten, stolen, reused across platforms, or cracked by attackers using brute force or phishing tactics. In fact, the majority of security breaches still stem from compromised passwords. Multi-factor authentication (MFA) often adds complexity to the user experience without fully eliminating the threat.
That’s why organizations are turning to biometric authentication, a method that uses biological traits like fingerprints or facial features to verify identity. It is not just more secure, but also intuitive, fast, and increasingly familiar to users across devices.
You have probably used biometric login without realizing it, like unlocking your phone with Face ID or approving a payment with your fingerprint. The convenience is seamless. The security? Built-in.
As digital identity becomes a part of everyday life, from banking to online doctor visits, what is biometric authentication, and why is it becoming the future of how we log in?

What Is Biometric Authentication?
Biometric authentication is the process of verifying a person’s identity based on unique physical or behavioral traits. Features such as fingerprints, voice, face, or eye scans are unique to each person, making them very difficult to copy or fake.
Biometric authentication is a subset of authentication that verifies a user’s identity based on unique biological traits, such as fingerprints, facial recognition, or iris patterns. Unlike traditional methods that rely on something you know (like a password) or something you have (like a security token), biometric authentication uses something you are to provide a more secure and seamless login experience.
When people ask “What is biometric login?”, it usually means you are using something like a fingerprint or face scan to log into a device or app, without typing a password.
So, what type of authentication is biometrics? It is considered one of the three pillars of multi-factor authentication (MFA) and is commonly used as either a standalone method or as part of a layered security approach.
Real-world examples of biometric authentication include:
-
Scanning a fingerprint to unlock your smartphone
-
Using facial recognition to access mobile banking apps
-
Speaking a passphrase to verify your identity in a voice-based IVR system
The power of biometric authentication lies in its accuracy, convenience, and built-in security because you can’t forget or misplace your fingerprint.
How Does Biometric Authentication Work?
Understanding how biometric authentication works involves breaking the process into a few core stages. While the mechanics may differ slightly between methods (e.g., fingerprint vs. facial recognition), the overall workflow follows a common pattern:
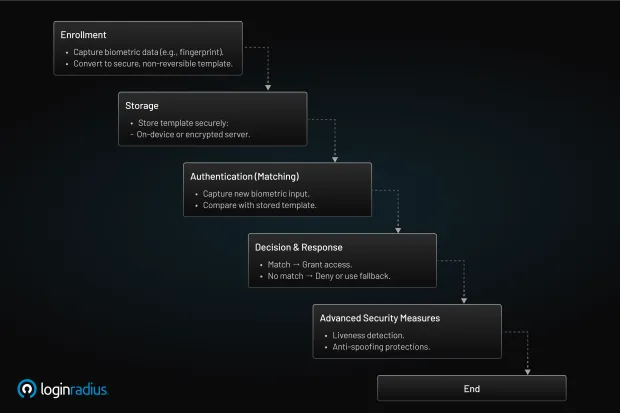
1. Enrollment
This is the first step, where the system captures a user’s biometric data. For example, a fingerprint scanner reads the unique ridges and patterns of your finger. This information is then converted into a digital format called a biometric template.
Importantly, this template is not a raw image; it’s a mathematical representation that cannot be reversed back into the original biometric. This ensures that even if data were compromised, an attacker couldn’t recreate your fingerprint.
2. Storage
The biometric template is then securely stored. Depending on the implementation, this could be:
-
On the user’s device (e.g., in a secure enclave on a smartphone)
-
In a centralized server with high-level encryption
-
In a decentralized identity system that ensures data never leaves the device
The goal is to store the data in a way that balances privacy, security, and accessibility.
3. Authentication (Matching)
When a user attempts to log in, a new biometric scan is performed (e.g., a fresh fingerprint or facial capture). The system then compares this new input to the stored biometric template.
4. Decision and Response
If there’s a match between the new scan and the template, with a score above a predefined confidence threshold, access is granted. Otherwise, access is denied, or a fallback method (like a password or OTP) is requested.
“What do biometrics use to perform authentication of identity?” Biometric systems use distinct measurable biological data (like voice pitch, eye patterns, or touch dynamics) and convert these into mathematical templates.
These templates become the baseline for future comparisons. The uniqueness and consistency of these traits are what make biometric authentication so effective.
Advanced biometric authentication systems also employ additional techniques like:
-
Liveness detection: To ensure that the biometric input is from a live person and not a static image or recording.
-
Anti-spoofing mechanisms: To detect and reject attempts using masks, photos, or 3D models.
The result is a login experience that’s not only faster but more secure, reducing the likelihood of fraud while eliminating the need for memorizing complex passwords.
Types of Biometric Authentication Methods
Biometrics go far beyond just fingerprints. Today’s biometric authentication methods span a wide range of physical and behavioral traits, each offering its own strengths depending on the use case.
Let’s explore the most common types of biometric authentication technologies used today:
1. Fingerprint Authentication
This is the most widely adopted form of biometric technology, thanks to its simplicity and speed. Fingerprint scanners are embedded in smartphones, laptops, and even payment systems.
-
How it works: The system scans the ridges and valleys of your finger, converts it into a digital map, and compares it during authentication.
-
Use cases: Device unlocking, time-tracking systems, and mobile banking apps.
2. Facial Recognition
Your face becomes your password. This method uses unique facial geometry, like the distance between eyes, jaw shape, and nose width, to identify users.
-
How it works: A camera captures your face and analyzes key landmarks. Modern systems include liveness detection to prevent spoofing.
-
Use cases: Airport check-ins, eKYC in finance, and smartphone logins.
3. Iris and Retina Scanning
These are among the most precise but also the most invasive and expensive methods. They scan the unique patterns in the colored ring of the eye (iris) or blood vessels in the retina.
-
How it works: Uses near-infrared light to scan the eyes and compare stored templates.
-
Use cases: Border control, government security, and high-assurance enterprise access.
4. Voice Recognition
Each person's voice carries a distinct tone, pitch, cadence, and accent. Voice recognition systems capture these features to verify identity.
-
How it works: Users are asked to speak a phrase or respond to prompts. The voice is then analyzed for acoustic patterns.
-
Use cases: Banking IVRs, smart assistants (like Alexa), and call center verification.
5. Biometric Signature
This method captures the unique way a person signs their name, focusing on how, not just what, they write.
-
How it works: Tracks speed, pressure, angle, and stroke patterns.
-
Use cases: Document approvals, e-signatures, and digital onboarding.
6. Behavioral Biometrics
Still an emerging space, this includes things like:
-
Typing rhythm (keystroke dynamics)
-
Mouse movement patterns
-
Walking style (gait recognition)
Behavioral biometrics provide continuous, passive verification ideal for real-time fraud detection.
Together, these biometric authentication methods offer flexible and scalable security options across industries from healthcare and retail to fintech and enterprise platforms.
Benefits of Biometric Authentication
Biometric authentication isn’t just a buzzword; it’s solving real-world challenges in usability and security. Here’s why it’s gaining adoption across the board.
1. Stronger Security
Biometric traits are incredibly hard to duplicate or share. Unlike passwords, they’re not easily stolen, guessed, or phished.
-
No more password reuse vulnerabilities.
-
Less exposure to brute-force attacks or credential stuffing.
-
Built-in protection through liveness detection and secure storage.
2. Faster Login Experience
Users don’t want to remember long, complex passwords or reset them every 60 days. Biometrics offer a smooth, nearly invisible authentication experience.
-
Unlocks take milliseconds.
-
Great for mobile-first and on-the-go users.
3. Reduced IT and Support Costs
Fewer password resets = lower support burden. That’s a win for both security and business efficiency.
- Biometrics eliminate the most common support ticket: “I forgot my password.”
4. Better User Adoption and Satisfaction
End users prefer convenience. When the login process feels effortless, adoption rises.
-
Biometrics align with modern user expectations.
-
Particularly helpful for users with accessibility needs (e.g., difficulty typing passwords).
5. Compliance and Risk Mitigation
With growing pressure to secure personal data, biometric systems help organizations meet compliance standards when implemented correctly.
-
Support for FIDO2/WebAuthn
-
Encryption and privacy-by-design models for GDPR/CCPA compliance
In short, biometric authentication brings security and user experience together, offering a reliable alternative to traditional credentials.
Risks of Biometric Authentication
While biometric authentication has many upsides, it’s not without its challenges. Like any security system, it must be implemented thoughtfully, especially when dealing with personally identifiable information (PII).
1. Permanence and Irreversibility
You can reset a password. You can't reset a fingerprint.
-
If a biometric template is compromised, the damage may be permanent.
-
This raises significant concerns around long-term identity theft.
2. Spoofing and Presentation Attacks
Although modern systems use liveness detection, attackers have used photos, masks, or 3D models to trick facial or fingerprint scanners.
-
Low-cost or poorly designed biometric systems are more vulnerable.
-
Voice recognition systems can be fooled using deepfake audio or recordings.
3. Privacy and Data Storage Concerns
Biometric data is deeply personal. Mishandling or leaking it could violate privacy laws and customer trust.
-
Centralized storage of biometric templates is a high-value target.
-
Organizations must use encryption, hashing, and strict access controls.
4. Bias and Inaccuracy
Some biometric systems show performance differences across demographics.
-
Facial recognition may underperform on underrepresented groups.
-
False positives or false negatives can degrade trust in the system.
5. Regulatory and Ethical Issues
Using biometric authentication comes with legal responsibilities:
-
Consent must be explicit and documented.
-
Compliance with laws like GDPR, BIPA (Illinois), and others is non-negotiable.
In conclusion, while biometric authentication technology offers unmatched convenience and security, organizations must address its limitations with strong safeguards, transparency, and user control.
Passwords vs Biometrics: Which One is Stronger?
The debate between password and biometrics is less about replacement and more about evolution. While passwords have been the foundation of digital security for decades, their flaws are increasingly evident in today's threat landscape.
Let’s compare both approaches side by side:
| Feature | Passwords | Biometrics |
|---|---|---|
| What you need | A secret phrase or combination | Your body or behavior |
| Ease of use | Often hard to remember or manage | Intuitive, built into devices |
| Security risk | Susceptible to phishing, reuse, theft | Harder to spoof but permanent if stolen |
| Reset capability | Easily changed if compromised | Cannot be changed once exposed |
| Adoption barrier | Low setup costs, universal compatibility | Requires biometric hardware |
| Attack surface | Brute-force, keylogging, and social engineering | Spoofing, biometric data leaks |
Passwords rely on secrecy. Unfortunately, that secrecy is easily broken, whether through a data breach, social engineering, or password reuse. Once stolen, passwords can be sold on the dark web and used for credential stuffing attacks.
Biometric authentication, by contrast, uses who you are, not what you remember. It’s not something you can forget or accidentally share. And with technologies like fingerprint authentication, face ID, and behavioral biometrics, it’s now embedded in many of the devices we use daily.
However, it is important to understand that biometric login and passwords don’t always have to be adversaries. Many systems now use them together in multi-factor authentication (MFA) setups, combining “something you know” with “something you are” for higher assurance.
So, Which One is Stronger?
-
For convenience and usability: biometrics win hands down.
-
For recoverability: passwords are easier to manage.
-
For security: biometrics are stronger in most scenarios—provided they’re implemented with robust privacy controls.
The best approach often blends both. Especially in regulated environments, pairing passwords and biometrics is becoming the new norm.

How Secure Is Biometric Authentication?
A common question we hear is: How secure is biometric authentication? The short answer—it’s one of the most secure methods available, if implemented correctly.
Let’s break down what makes it secure and where the caveats lie. Why It’s Secure
1. Hard to Forge or Share
You can’t guess a fingerprint. You can’t share your iris pattern with a colleague. Biometric authentication technology ensures that credentials are unique to the user.
2. Reduced Phishing Risk
Since there’s no password to steal, phishing attacks become significantly less effective.
3. On-Device Processing
Modern biometric systems (like Face ID or Windows Hello) store encrypted templates locally within a secure enclave on your device, so your biometric data never leaves your device.
4. Advanced Spoof Protection
Technologies like liveness detection and thermal imaging reduce the risk of photos, deepfakes, or 3D-printed masks fooling the system.
5. FIDO2 & WebAuthn Compliance
FIDO2 and WebAuthn are open standards allow biometric logins to work securely across browsers and devices without passwords, paving the way for safer digital experiences.
Where the Risks Lie
-
Permanence of Data: Unlike passwords, you can’t “reset” a biometric trait if it’s compromised.
-
Centralized Storage Risks: If biometric data is stored on a central server (not recommended), a breach could have irreversible consequences.
-
Bias and Accessibility: Systems must be trained on diverse datasets to avoid false rejections for certain demographics.
Security Best Practices
To maximize the security of biometric authentication systems, organizations should:
-
Always use on-device matching where possible.
-
Combine biometrics with adaptive MFA for higher-risk scenarios.
-
Implement data encryption and secure lifecycle management of biometric templates.
-
Educate users about how biometric authentication works to build trust and adoption.
Ultimately, the security of biometric authentication depends on how thoughtfully it's implemented. With the right infrastructure and compliance in place, it offers a powerful defense against today’s most common threats while delivering a smoother, faster experience for users.
Must-Have Features for Biometric Authentication Tools
Not all biometric tools are created equal. When evaluating a biometric authentication system for your app, enterprise platform, or digital service, there are critical capabilities that can significantly impact its security and user experience.
Let’s break down the must-have features for biometric authentication tools:
1. Multi-Modal Biometric Support
A robust solution should offer support for various biometric authentication methods, such as:
-
Fingerprint authentication
-
Facial recognition
-
Iris/retina scans
-
Voice recognition
-
Behavioral biometrics
Why it matters: Offering multiple options enhances accessibility, allowing users to choose the method that works best for their device or environment.
2. Liveness Detection
A critical feature that distinguishes real human interaction from spoofing attempts.
-
Detects blinking, head movement, pulse, or 3D depth
-
Blocks attacks using photos, videos, or masks
Why it matters: Prevents fake biometric data from tricking the system, which is essential for high-security applications like finance and healthcare.
3. On-Device Matching
Whenever possible, biometric data should be processed and stored on the user’s device, not sent to or stored in centralized servers.
-
Secure enclaves like Apple’s Secure Enclave or Android’s Trusted Execution Environment (TEE)
-
Ensures biometric templates never leave the device
Why it matters: Minimizes risk of a breach and increases user trust.
4. WebAuthn and FIDO2 Compliance
WebAuthn and FIDO2 are industry standards that enable secure, passwordless logins using biometrics across devices and browsers.
-
Works seamlessly with Face ID, Touch ID, Windows Hello, and Android biometrics
-
Eliminates reliance on passwords entirely
Why it matters: Ensures your solution is future-proof and compatible across platforms.
5. User Consent & Privacy Controls
Your biometric tool should include features for explicit consent capture, data minimization, and secure template lifecycle management.
-
Biometric templates should be encrypted and anonymized
-
Logs and audit trails should show who accessed what, and when
Why it matters: Supports compliance with GDPR, CCPA, BIPA, and growing global privacy frameworks.
6. Fail-Safe Mechanisms & Fallback Options
What if someone’s fingerprint sensor malfunctions? Or does facial recognition fail in poor lighting?
-
Offer fallbacks like PINs or recovery email/SMS
-
Fallbacks should be secure, but not cumbersome
Why it matters: Prevents lockouts and maintains a smooth user experience.
Choosing the right biometric authentication tool is about more than scanning faces or fingers it’s about implementing security, privacy, and flexibility at scale.
How Accurate Is Biometric Authentication?
Accuracy in biometric systems is not just a nice-to-have; it’s the backbone of trust. But accuracy is more nuanced than it may seem.
So, how accurate is biometric authentication in real-world use? Let's look at the key metrics that define this. Key Accuracy Metrics
1. False Acceptance Rate (FAR)
-
The percentage of times an unauthorized person is incorrectly granted access.
-
A lower FAR means the system is harder to spoof.
2. False Rejection Rate (FRR)
-
The percentage of times a legitimate user is denied access.
-
A lower FRR ensures a smoother user experience.
3. Equal Error Rate (EER)
- The point where FAR and FRR intersect. The lower the EER, the better the overall system performance.
In summary, modern biometric authentication technology can be highly accurate, especially when fine-tuned for specific use cases. However, accuracy depends on careful implementation, regular updates, and fallback planning for edge cases.
Is Biometric Authentication Hackable?
A fair question—and one that needs an honest answer. So, is biometric authentication hackable? Yes, but not in the same way as traditional credentials like passwords or PINs. Biometric systems raise the bar significantly for attackers, but no system is immune to compromise.
Let’s explore the potential attack vectors and the countermeasures that protect against them.
Common Biometric Attack Vectors
1. Spoofing Attacks
-
Using printed fingerprints, 3D-printed face masks, or deepfake audio to mimic biometric traits.
-
Example: In early facial recognition systems, attackers used photos to unlock phones.
2. Template Theft
-
If biometric templates are stored in centralized databases without encryption, they become a target.
-
Unlike passwords, biometric data cannot be reset, making leaks more serious.
3. Replay Attacks
- Capturing and replaying the biometric signal (e.g., a fingerprint scan) during transmission, if not encrypted.
- Sensor Bypass
- Hardware-based attacks that attempt to trick or override the biometric reader itself.
Defense Mechanisms
1. Liveness Detection
- Prevents spoofing by checking for signs of life (e.g., blink detection, heat sensing, muscle movement).
2. On-Device Processing
- Keeps biometric templates secure within the device’s hardware-level protection zones, like Secure Enclave or TEE.
3. Template Encryption & Salting
- Even if a database is breached, the stolen biometric data remains unintelligible and unusable.
4. Multi-Factor Authentication (MFA)
- Combine biometric login with device-bound keys or OTPs to further strengthen security.
So, Should You Worry?
While biometric systems can be hacked under specific and often expensive conditions, the effort required is significantly higher than traditional methods. That’s why biometric authentication is increasingly favored in high-assurance use cases.
To stay safe:
-
Avoid storing raw biometric data on central servers.
-
Use standards-based authentication like FIDO2.
-
Keep software, AI models, and detection systems updated.
The takeaway? With the right safeguards in place, biometric authentication technology is not only secure but also more resilient to common attack vectors than passwords alone.
Biometric Authentication with LoginRadius
Implementing biometric authentication doesn’t have to be complicated, especially if you have a developer-ready identity platform like LoginRadius.
We built our biometric authentication system to make modern, password-free logins accessible to every application, without sacrificing security, speed, or scalability.
Here’s how LoginRadius enables you to offer secure, seamless biometric login to your users in just a few lines of code:
Standards-Based Integration with WebAuthn & FIDO2
At the core of LoginRadius’ biometric capabilities is full support for FIDO2 and WebAuthn, the industry standards for passwordless authentication.
-
This allows you to offer fingerprint authentication, facial recognition, and device-based biometrics (like Windows Hello or Apple Touch ID) out of the box.
-
Your users can authenticate using their device's native biometric mechanisms—no separate hardware or custom infrastructure needed.
Device-Bound Security
All biometric data remains on the user's device. We never store or process raw biometric information on our servers.
-
This approach aligns with zero-trust principles and ensures maximum privacy compliance (including GDPR and CCPA).
-
Instead of capturing and storing biometric templates, we verify identity using public-private key cryptography linked to device-bound credentials.
Developer-Friendly APIs and SDKs
We understand that time-to-market matters. Our platform provides:
-
Pre-built SDKs for JavaScript, React, Android, and iOS
-
Detailed documentation and developer guides
-
A unified dashboard to manage passwordless and biometric flows
So whether you're adding biometric login to a consumer app or securing admin access to your B2B platform, LoginRadius makes it fast, flexible, and scalable.
Security Meets Experience
Biometrics should enhance security and UX, not trade one for the other. With LoginRadius:
-
Users can log in using the same method they use to unlock their devices
-
Frictionless flows increase conversion and retention
-
Admins can enforce MFA that includes biometrics as a primary factor or step-up method
By offering biometric authentication technology built on global standards and designed for modern developers, LoginRadius helps you meet today’s security expectations without complicating your stack. Want to see it in action? Contact our team to get a personalized demo.
Conclusion
The login box is no longer just a password field. It is an experience, a critical touchpoint that determines whether users feel secure, confident, and seen. Biometric authentication is at the forefront of this transformation.
Yet, with great power comes great responsibility. Implementing biometrics requires considering high level of security, privacy, accuracy, and accessibility at every step. From fingerprint authentication and face scans to behavioral signatures and voice recognition, biometric authentication methods are no longer futuristic; they are foundational.
Whether you're building a consumer app, scaling an enterprise platform, or securing a partner ecosystem, LoginRadius makes it easy to integrate biometric authentication with confidence.
The future of authentication is personal. Are you ready to build it? Talk to us about adding biometric login to your digital experience.
FAQs
1. How do I set up biometric authentication?
A. To set up biometric authentication, users enroll a fingerprint, face, or voice pattern on their device. Developers can implement it using standards like FIDO2/WebAuthn for seamless integration with native biometrics.
2. How does biometric authentication work?
A. Biometric authentication captures a user’s biological trait, converts it into a digital template, and compares it against a stored version. If the match is close enough, access is granted.
3. What type of authentication is biometrics?
A. Biometrics fall under “something you are” in the multi-factor authentication model, using unique physical or behavioral traits to confirm identity.
4. What do biometrics use to perform authentication of identity?
A. Biometrics use distinct biological data, like fingerprint ridges, facial geometry, or voice pitch, to create encrypted templates that are matched during the login process.




