Introduction Summary
Biometric security has moved far beyond fingerprints on a smartphone. Today, it powers high-assurance authentication, fraud prevention, adaptive identity verification, and secure access control across digital and physical environments. As cyberattacks evolve and passwords continue to fail, biometric protection has become one of the most reliable ways to verify identity—using traits that are inherently unique to each individual.
In this guide, you’ll learn:
-
What biometric security is and how modern biometric protection works
-
Types of biometric security systems, including physical and behavioral
-
The advantages and limitations of biometrics in security
-
How biometric data security is maintained and regulated
-
How organizations use biometrics for access control, authentication, fraud prevention, and compliance
-
How LoginRadius supports biometric authentication within a CIAM platform
By the end, you’ll understand how biometrics and security intersect to create safer, smarter identity systems—and where to use biometric authentication with confidence.
Biometric security is a method of identity verification that uses unique biological or behavioral traits—such as fingerprints, facial recognition, iris patterns, voice, or typing behavior—to confirm who a person is. A biometric security system captures these traits, converts them into encrypted templates, and matches them during authentication to provide strong, passwordless protection.
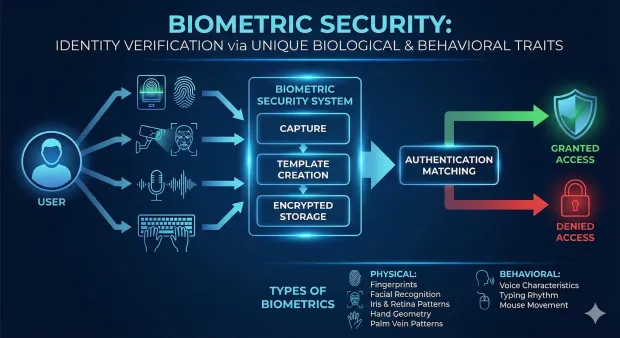
Biometric security refers to technologies that verify identity based on physical or behavioral characteristics that are unique to each person. Instead of depending on what you know (passwords) or what you have (tokens), biometric protection works by analyzing who you are.
These traits can include:
-
Fingerprints
-
Facial structure
-
Iris or retina patterns
-
Voice characteristics
-
Hand geometry
-
Palm vein patterns
-
Behavioral patterns such as typing rhythm or mouse movement
A biometric security system captures one or more of these traits, converts them into a digital representation (a biometric template), stores them securely—usually on the device—and then matches the template during future authentication attempts.
Biometric security is becoming essential across industries because it solves modern identity challenges:
-
Passwords are easy to forget
-
OTPs can be intercepted
-
Knowledge-based factors can be guessed
-
Devices now come with built-in biometric sensors
-
Regulations demand stronger identity assurance
In short, biometrics and security now go hand-in-hand because biometric authentication connects identity to something that cannot be phished, forgotten, or loaned out.
How Biometric Security Works
Biometric security systems follow a structured workflow that ensures accuracy, encryption, and privacy. The process appears simple on the surface—a fingerprint scan or a facial recognition glance but the underlying mechanics are sophisticated.
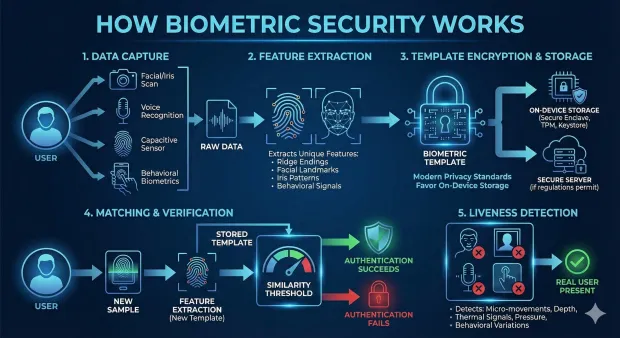
1. Data Capture
The system collects a biometric sample using a sensor:
-
Camera for facial or iris scans
-
Microphone for voice recognition
-
Capacitive sensor for fingerprints
-
Gyroscope or touch sensors for behavioral biometrics
The goal is to extract clear, high-quality biometric characteristics.
2. Feature Extraction
Instead of storing the raw image, the system analyzes the biometric input and extracts unique features—ridge endings on fingerprints, facial landmarks, iris patterns, or behavioral signals. These features form the basis of your biometric template.
3. Template Encryption & Storage
The template is encrypted and stored either:
-
On-device (Secure Enclave, TPM, Keystore)
-
In a secure server, if regulations permit
Modern privacy standards strongly favor on-device storage, ensuring biometric data never leaves user hardware.
4. Matching & Verification
During authentication, the system captures a new sample and converts it into another feature set. It then compares it to the stored template. If similarity exceeds a threshold, authentication succeeds.
5. Liveness Detection
To prevent spoofing—like printed face images, recorded voices, or silicone fingerprints—modern biometric security systems detect:
-
Micro-movements
-
Depth
-
Thermal signals
-
Pressure response
-
Natural behavioral variations
This ensures “the real user” is present.
Biometric security delivers frictionless login while maintaining strong protection, making it ideal for passwordless and adaptive authentication.
What Is a Biometric Access Control System?
A biometric access control system uses fingerprints, facial recognition, iris scans, or other biometric identifiers to grant or deny entry to physical or digital spaces. Instead of keys or passwords, the system verifies identity using unique biometric traits.
A biometric access control system regulates who can access a system, resource, device, or physical location by verifying identity using biometrics rather than keycards, PINs, or passwords. It replaces vulnerable access methods with something intrinsic to the user.
Biometric access control is widely used for:
-
Corporate building entry
-
Data centers and secure rooms
-
Patient records in hospitals
-
Airport and border control
-
High-security manufacturing facilities
-
Device unlocking (phones, laptops)
-
Workforce identity verification
These systems may use:
-
Fingerprint locks
-
Facial recognition gates
-
Palm-vein scanners
-
Iris and retina readers
-
Voice-controlled entry systems
Compared to traditional access control, biometric systems prevent:
-
Badge sharing
-
Key duplication
-
Password guessing
-
Device theft leading to unauthorized entry
When paired with robust biometric data security practices, biometric access control improves safety while reducing operational friction for users and administrators.
Types of Biometric Security Systems
Biometric security systems can be categorized into two core types: physical (physiological) and behavioral biometrics. Many modern systems combine them for greater accuracy and fraud resistance.
1. Physical (Physiological) Biometrics
These rely on fixed human traits that rarely change over time.
Fingerprint Recognition
The most widely used biometric security system.
-
Scans ridge patterns
-
Converts them into encrypted templates
-
Supports on-device matching for phones and laptops
-
Affordable and widely supported
Facial Recognition
Uses 2D or 3D imaging to map facial geometry.
-
Fast and contactless
-
Built into all modern smartphones
-
Ideal for frictionless authentication
Iris and Retina Scanning
Ultra-secure biometric protection.
-
High precision
-
Near-zero false acceptance rates
-
Used in border control and regulated industries
Voice Recognition
Analyzes vocal features and pitch.
-
Useful for call centers or hands-free access
-
Must include anti-spoofing to prevent recorded voice attacks
Palm Vein & Hand Geometry
Scans internal vein patterns or hand structure.
-
Extremely hard to spoof
-
Ideal for high-security environments
2. Behavioral Biometrics
Behavioral biometrics analyze how a user interacts with devices.
Includes metrics such as:
-
Typing cadence
-
Swipe patterns
-
Mouse movement
-
Gait analysis
-
Touch pressure
-
Device handling motion
These systems run continuously in the background, providing “always-on authentication.”
Behavioral biometrics help detect:
-
Account takeover
-
Bot activity
-
Fraudulent transactions
-
Abnormal usage patterns
Together, physical and behavioral biometrics create a holistic biometric security strategy.
Advantages of Biometric Security
Biometric security delivers benefits across convenience, security, fraud protection, compliance, and user experience. Below are expanded advantages with deeper explanations.
Frictionless User Experience With High Assurance
Biometrics eliminate the need for passwords, PINs, or physical tokens. A simple touch, glance, or voice confirmation unlocks access instantly. This ease of use reduces login fatigue, increases engagement, and improves onboarding completion rates. Because biometric authentication is both fast and accurate, it delivers a smooth experience without compromising identity verification.
Enhanced Security Through Unrepeatable Biological Traits
Biometrics rely on characteristics that are extremely difficult to steal, guess, or clone. A fingerprint cannot be phished. A face scan cannot be brute-forced. Even if attackers intercept traffic, biometric templates are useless due to encryption and on-device storage. This makes biometric protection particularly powerful against credential theft and social engineering attacks.
Reduced Operational Costs and Password Overhead
Password resets remain one of the most expensive IT support burdens. With biometric security systems, fewer users rely on passwords, dramatically reducing reset tickets and recovery workflows. Organizations can reallocate resources from troubleshooting to innovation. Over time, biometric authentication lowers maintenance costs and simplifies identity governance.
Continuous Monitoring for Fraud Detection
Behavioral biometrics allow ongoing session verification. Instead of authenticating once at login, the system monitors user interactions to detect suspicious behavior. If behavioral signals shift unexpectedly—typing slower, swiping differently, or using unusual movement patterns—the system can trigger step-up authentication or session termination. This is a powerful defense against fraud and account takeover.
Strong Compliance Alignment and Privacy Enhancements
Regulations like GDPR, PSD2, HIPAA, and CCPA demand secure identity proofing and ongoing protection. Biometric data security measures—like encryption, local storage, and explicit consent—ensure compliance. Biometrics provide strong identity assurance, helping organizations meet regulatory requirements for authentication, eKYC, and fraud prevention workflows.
Challenges and Risks of Biometric Security
While powerful, biometric protection must be implemented responsibly.
Privacy Concerns
Users worry about misuse of biometric data. Organizations must store templates securely (preferably on-device), avoid reusing data, and maintain clear consent flows.
False Positives / False Negatives
Biometric systems rely on thresholds. Poor calibration can cause lockouts or unauthorized acceptance.
Sensor Quality Variability
Low-quality cameras or fingerprint scanners reduce accuracy.
Spoofing Attempts
Without strong liveness detection, attackers may try:
-
Photos
-
Recordings
-
Silicone fingerprints
Regulatory Requirements
Biometric data is legally protected and requires strict governance, retention rules, and deletion rights.
Best Practices for Biometric Protection
To deploy biometric security responsibly, organizations should follow these practices:
1. Prioritize On-Device Storage
Store templates in secure hardware elements (TPM, Secure Enclave) to avoid centralization risks.
2. Use Multi-Modal Biometrics
Combining two biometric types increases accuracy and avoids sensor limitations.
3. Apply Liveness Detection
Use anti-spoofing models to detect presentation attacks.
4. Minimize Data Retention
Keep biometric templates only as long as needed.
5. Transparent Consent & Communication
Tell users how biometric data is collected, stored, and used.
6. Integrate Biometrics Into Adaptive Authentication
Trigger biometrics only when risk signals indicate unusual activity.
Biometric Security Use Cases
Consumer Applications
-
Phone unlocking
-
Banking apps
-
Payment authorization
Enterprise & Workforce
-
Secure employee login
-
Workstation access
-
High-security area entry
Financial Services
-
Fraud prevention
-
Behavioral risk scoring
Healthcare
-
Patient identity verification
-
EMR/EHR access
Government & Border Control
-
Passport control
-
National ID verification
Biometric systems dramatically improve identity accuracy across regulated industries.
How LoginRadius Supports Biometric Security
LoginRadius integrates biometric authentication as part of a broader Customer Identity and Access Management (CIAM) strategy. Here’s how LoginRadius enhances biometric protection:
1. WebAuthn-Based Biometric Authentication
Supports fingerprint, Face ID, Windows Hello, and Android biometrics using FIDO2 and WebAuthn standards.
2. Passwordless Biometric Login
Biometrics replace passwords for frictionless, secure user access.
3. Device-Bound Credentials
Biometric keys stay on-device, ensuring biometric data never touches servers.
4. Adaptive Authentication Integration
Biometrics trigger only during high-risk events, reducing friction.
5. Strong Encryption & Compliance Support
LoginRadius helps organizations comply with GDPR, CCPA, ISO 27001, and SOC 2.
6. Developer-Friendly SDKs
SDKs for web, iOS, Android enable easy biometric integration across applications.
LoginRadius ensures biometric security becomes a scalable, compliant part of your identity ecosystem.
Conclusion
Biometric security has become one of the most powerful tools for modern identity protection. Whether used for authentication, fraud prevention, or access control, biometrics offer unmatched accuracy and convenience. But biometric data must be handled responsibly—with encryption, secure storage, transparent consent, and adaptive usage.
LoginRadius makes biometric authentication secure, privacy-first, and easy to integrate—empowering organizations to deploy frictionless user experiences without compromising safety.
Biometric security isn’t just the future of authentication—it’s the foundation of modern digital trust.
FAQs
1. What is biometric security?
Biometric security uses unique physical or behavioral traits—like fingerprints, face, or voice—to verify identity securely.
2. What is biometric protection?
Biometric protection refers to safeguarding biometric data using encryption, secure storage, and strong authentication controls.
3. What is a biometric security system?
A biometric security system captures biometric traits, converts them into encrypted templates, and matches them during login or access control.
4. What is a biometric access control system?
It is a system that uses biometric traits to control entry to buildings or digital systems instead of keys, cards, or passwords.


