Key Takeaways/ Introduction Summary
-
Digital trust drives modern business. Every click, login, or form submission generates sensitive data that must be protected under global privacy laws.
-
Compliance management ensures that protection is deliberate, consistent, and aligned with regulatory expectations—not left to chance.
-
This guide breaks down:
-
What compliance management means
-
How modern compliance processes work
-
Why a Compliance Management System (CMS) is essential
-
How LoginRadius supports automation, access control, risk management, and audit readiness
-
With the right approach, compliance becomes a strategic advantage that strengthens user trust and accelerates growth—not just a regulatory obligation. Let’s understand.
The shift to cloud infrastructure, remote work, and digital customer journeys has made compliance inseparable from business performance. Data no longer lives in one system; it flows between SaaS apps, mobile devices, and third-party APIs. Each connection introduces risk—and each risk invites regulation.
Regulators worldwide have responded with frameworks such as ting GDPR, CCPA, SOC 2, and ISO 27001 . Meeting these obligations requires structure, not spreadsheets. Compliance management is that structure: a continuous loop of policies, monitoring, and improvement.
For developers, this means implementing secure coding practices, encrypting data in motion and at rest, and logging every transaction for accountability. For business leaders, it means measurable governance and faster enterprise deals because partners can verify your compliance posture instantly.
Identity platforms like LoginRadius make that possible. They centralize authentication, consent, and encryption so compliance becomes built-in rather than bolted-on.
What Is Compliance Management?
Compliance management is the practice of ensuring an organization’s operations, technologies, and data-handling activities meet regulatory, legal, and internal standards. It bridges strategic governance with technical execution to keep businesses secure, audit-ready, and aligned with evolving requirements.
A complete compliance management system gives visibility across three core layers:

-
Governance – defining policies, ownership, and accountability.
-
Execution – enforcing policies through controls, automation, and secure processes.
-
Assurance – verifying compliance continuously through monitoring, audits, and reporting.
For developers, compliance management means building secure-by-default applications: encrypting personally identifiable information (PII), honoring user consent before data use, and integrating compliance APIs.
LoginRadius APIs support these requirements by managing encryption, consent capture, access rights, and deletion requests—helping satisfy regulations like GDPR Article 17 without extra engineering overhead.
For business teams, compliance management reduces financial, legal, and reputational risk. Fines for non-compliance can exceed 4% of global revenue, and the trust impact can be even more damaging. Strong, transparent compliance processes reinforce credibility and protect brand equity.
Why Compliance Management Matters
Compliance management matters because it strengthens organizational resilience, improves operational efficiency, reduces risk, and increases customer trust. It ensures that businesses can meet regulatory obligations, avoid costly penalties, and operate confidently in new markets while maintaining a strong security and privacy posture.
Here’s how effective compliance management creates real value:

1. Risk Reduction
Regulations exist to reduce exposure to threats. A structured compliance management process minimizes human error, insider misuse, and accidental data leaks. Automated alerts catch policy violations early, preventing small issues from becoming major incidents.
2. Operational Efficiency
Manual audits are slow and resource-heavy. Automated evidence collection and centralized dashboards cut audit prep from weeks to hours.
LoginRadius provides built-in audit logs and exportable reports, simplifying SOC 2, ISO 27001, and other compliance reviews.
3. Market Expansion
Compliance often determines whether you can enter or grow in certain markets.
-
GDPR readiness enables European user acquisition.
-
HIPAA compliance opens U.S. healthcare opportunities.
-
ISO 27001 certification boosts global enterprise partnerships.
4. Customer Trust & Brand Loyalty
Users prefer brands that protect their privacy. Displaying strong compliance practices—even during onboarding—signals that security and transparency are core values. This builds trust that directly influences retention and long-term loyalty.
In short, strong compliance management creates a positive chain reaction: better governance → fewer incidents → higher trust → sustained business growth.
What is a Compliance Management System
A compliance management system (CMS) is a framework that turns regulatory requirements into everyday operational workflows. It combines people, processes, and technology to help organizations define policies, assess risk, implement controls, monitor compliance, and remediate issues quickly and consistently.
A strong CMS includes the following components:
1. Governance and Accountability
Assign clear ownership. Appoint a compliance officer and cross-functional leaders from IT, engineering, operations, and marketing to ensure organization-wide coverage.
2. Policy Framework
Document procedures for data collection, consent, access control, incident response, and retention. Link each policy to relevant standards like GDPR, CCPA, HIPAA, or internal requirements.
3. Risk Assessment
Identify where sensitive data lives—databases, APIs, logs, storage buckets—and classify it by sensitivity. Developers can embed metadata tags or automate scanning to detect regulated fields.
4. Control Implementation
Translate policy into technical safeguards such as encryption, MFA, network segmentation, and access restrictions.
LoginRadius CIAM supports this through configurable security policies that automatically enforce compliance.
5. Monitoring and Reporting
Real-time dashboards and audit trails provide visibility into compliance posture and user activity. This ensures traceability and simplifies audit preparation.
6. Remediation and Training
When gaps appear, document the root cause, apply fixes, and educate teams to prevent recurrence. This keeps compliance proactive rather than reactive.
A well-designed compliance management system keeps organizations aligned with regulations, reduces operational risk, and ensures compliance evolves with new threats and standards.
Explore: LoginRadius security and consent management overview:
The Compliance Process
A mature compliance program runs like a continuous improvement cycle—never static, always adapting. Understanding this compliance process helps you build governance that scales rather than breaks under audit pressure.
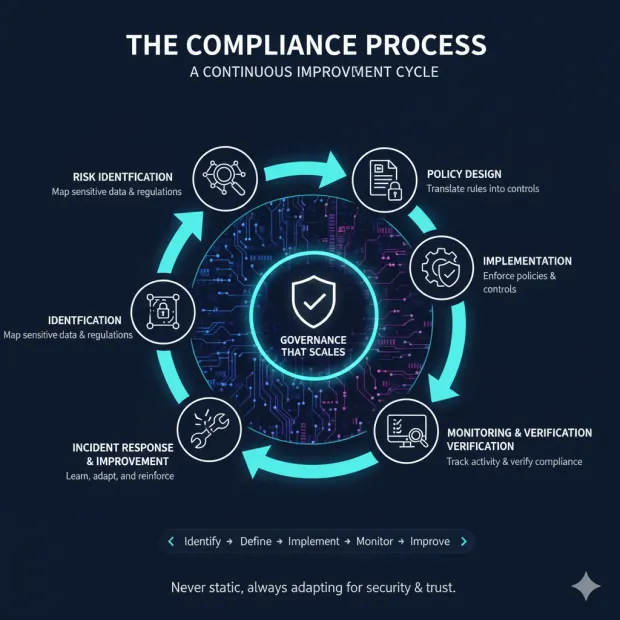
1. Risk Identification and Assessment
Everything starts with knowing your exposure. Map which systems hold sensitive data, who can access it, and which regulations apply.
Developers can instrument their applications with metadata or data-classification tags that surface PII automatically. Business teams can feed this map into risk registers.
LoginRadius simplifies this discovery by centralizing user data, so one identity layer governs all downstream applications.
2. Policy Design and Mapping
Once you know the risks, define how to manage them. Policies should translate legal obligations into practical engineering or operational rules—password complexity, consent prompts, breach notifications, and retention limits.
Through LoginRadius Admin Console, you can enforce these policies as configuration, not code: toggling MFA, setting encryption standards, or defining session lifetimes.
3. Control Implementation
Controls make policies real. They include preventive measures (encryption, MFA), detective measures (logging, alerts), and corrective measures (incident response).
For developers, LoginRadius WebAuthn and Passwordless APIs implement many of these controls automatically, giving secure, compliant login without reinventing crypto or consent workflows.
4. Monitoring and Auditing
Continuous monitoring turns compliance from a yearly scramble into a daily practice. Dashboards track logins, data exports, and policy exceptions in real time.
Compliance teams can export immutable audit logs from LoginRadius for SOC 2 or ISO verification within minutes.
5. Incident Response and Continuous Improvement
No system is perfect. When issues arise, incident response ensures accountability and learning. The best programs feed lessons back into code, policy, and culture—closing the loop between detection and prevention.
Compliance Management Systems and Solutions
Compliance management systems and solutions help organizations move from manual, spreadsheet-driven workflows to automated platforms that centralize policies, controls, evidence, and reporting. Modern CMS tools reduce blind spots, streamline audits, and ensure compliance is enforced consistently across people, processes, and technology.
Manual Systems — The Old Model
Traditional compliance relied on documents, shared drives, manual risk matrices, and long email trails. These siloed workflows created version confusion, inconsistent updates, and limited visibility—making it difficult to track evidence or respond quickly to violations.
Automated Compliance Management Systems — The Modern Model
Automated CMS platforms consolidate everything into a unified environment where teams can:
-
Manage policies
-
Automate evidence collection
-
Centralize risk assessment
-
Trigger alerts for violations
-
Monitor posture with real-time dashboards
Controls map directly to systems and workflows, giving leadership a complete and accurate view of compliance at any moment.
How LoginRadius Strengthens Compliance Management
LoginRadius functions as an identity-centric compliance management layer that supports regulatory and security requirements out of the box. It helps teams:
-
Encrypt data in transit and at rest to protect sensitive information
-
Log every authentication, authorization, and consent event for full auditability
-
Centralize consent collection and user-rights management, including data access and deletion requests
-
Generate compliance-ready reports aligned with GDPR, SOC 2, ISO 27001, and other frameworks
Here’s the list of compliances offered by LoginRadius CIAM platform.
By automating identity-driven controls, LoginRadius helps organizations reduce risk, simplify audits, and maintain continuous compliance without relying on fragile manual processes.
Best Practices to Manage Compliance Effectively
Transforming compliance from a mandatory requirement into a genuine competitive advantage takes consistency, clarity, and the right blend of automation. The practices below help organizations strengthen their compliance posture while leveraging the LoginRadius platform to simplify technical and operational overhead.
1. Start with a Framework
Adopt a recognized framework—ISO 27001, SOC 2, NIST CSF, or other regional standards—as the foundation of your compliance strategy.
A unified framework eliminates duplication and creates a single source of truth across legal, engineering, and business teams.
LoginRadius supports this effort by aligning its platform controls (encryption, consent, MFA, audit logging) with these major frameworks, making it easier for teams to map identity-related requirements to specific regulatory clauses.
2. Automate Evidence Collection
Manual evidence collection slows audits and introduces human error. Automation ensures integrity, consistency, and speed.
Using LoginRadius SDKs and APIs, developers can automatically generate audit events every time authentication, authorization, or consent actions occur. This creates a reliable, time-stamped trail of user activity that can be exported instantly during SOC 2, ISO 27001, or GDPR audits.
Automated logging also helps compliance teams verify policy adherence continuously rather than scrambling at the last minute.
3. Centralize Identity and Access
Access control failures are among the top drivers of compliance violations. When each system has its own login method, enforcing policies becomes complicated and error-prone.
Centralizing all identity workflows through **LoginRadius CIAM **ensures:
-
Consistent MFA enforcement across web and mobile properties
-
**Unified SSO **to simplify authentication paths
-
Least-privilege access that restricts sensitive operations
-
Adaptive policies that adjust based on risk and user behavior
This consolidation makes audits easier and eliminates gaps created by fragmented identity systems.
4. Conduct Regular Risk Reviews
Risk isn’t static—technology, user behavior, and regulations constantly evolve. Treat risk reviews like code updates: versioned, iterative, and measurable.
With LoginRadius, teams can use Admin Console dashboards to review authentication trends, suspicious activity alerts, and policy exceptions. Quarterly or even monthly reviews help teams close gaps before they lead to non-compliance or security incidents.
5. Make Compliance a Shared Value
Compliance only works when all teams—from engineering to product to marketing—treat it as a shared responsibility.
Define compliance KPIs, include security stories in sprints, and encourage transparent communication around risks.
LoginRadius helps foster this culture by giving engineering, product, and security teams a shared platform where policies, analytics, and identity events are visible in one place.
6. Choose Transparent Vendors
Your compliance posture is only as strong as the vendors supporting it. Choose partners that provide full transparency into their controls, audits, and certifications.
The LoginRadius Trust Center clearly lists SOC 2, ISO 27001, GDPR readiness, and other security commitments—making vendor due diligence far easier for compliance teams and third-party auditors.
Compliance in Action: Real-World Scenarios
Developer Scenario — SaaS Expansion
A SaaS company expanding into Europe integrates LoginRadius consent APIs to honor GDPR. It automates “right to be forgotten” requests and stores audit logs proving compliance. Result: expansion completed without hiring additional compliance engineers.
Business Scenario — Financial Services
A financial firm pursuing ISO 27001 certification adopts LoginRadius adaptive authentication to enforce MFA across customer portals. Dashboards provide real-time compliance status to executives, shortening audit prep from 12 weeks to 2.
Both cases show the synergy of automation and governance—developers reduce friction; leaders gain visibility.
Benefits of Effective Compliance Management
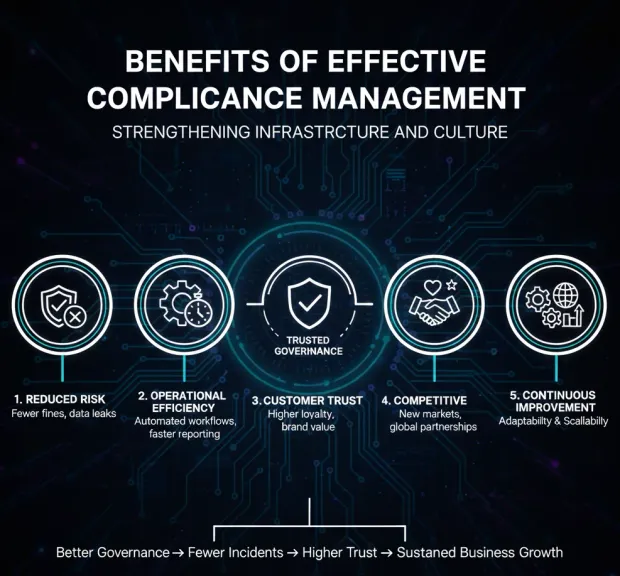
A mature compliance management program strengthens every layer of an organization—from infrastructure to culture.
1. Reduced Risk and Legal Exposure
Centralized policies and automated controls close gaps that lead to fines or breaches.
When identity, access, and encryption are handled through LoginRadius CIAM, personally identifiable information (PII) is protected end-to-end. Audit logs prove compliance with GDPR, SOC 2, and ISO 27001 requirements.
2. Operational Efficiency
Automation replaces manual paperwork. Evidence collection, reporting, and risk scoring happen in real time.
Developers gain pre-built APIs for encryption and consent management; compliance officers gain instant dashboards for audits.
3. Customer Trust and Brand Value
Transparent compliance communicates accountability.
Publishing certifications in your marketing and onboarding flows shows that data privacy is a feature, not an afterthought.
4. Competitive Advantage
Organizations that demonstrate governance maturity accelerate enterprise sales and partnerships. Many vendors now require proof of SOC 2 or ISO compliance before integration—having those in place shortens sales cycles dramatically.
5. Continuous Improvement and Scalability
A configurable compliance management system grows with the business. As new regulations appear, controls can be tuned instead of rebuilt, keeping operations nimble.
Challenges in Compliance Management and How to Overcome Them
Even with solid frameworks, compliance introduces recurring challenges. Anticipating them is half the battle.
| Challenge | Impact | Solution / Mitigation |
|---|---|---|
| Fragmented global regulations | Overlapping laws increase complexity | Map once to a core framework (ISO 27001 + GDPR) and reuse controls |
| Manual workflows | Inefficiency and audit fatigue | Automate checks and evidence collection with APIs |
| Shadow IT & third-party risk | Unmonitored data flows | Centralize identity and access through LoginRadius |
| Human error | Misconfigurations or leaks | Enforce least-privilege access, MFA, and peer reviews |
| Rapidly changing technology | New attack surfaces | Adopt adaptive authentication and continuous monitoring |
A proactive culture plus automation neutralizes most of these risks.
Implementing a Compliance Management Program with LoginRadius
Step 1 – Assess and Map Regulations
List all relevant laws—GDPR, CCPA, HIPAA, SOC 2—and connect them to data types and processes.
LoginRadius’ documentation and Trust Center help identify which platform controls address each obligation.
Step 2 – Centralize Identity and Access
Deploy LoginRadius CIAM to unify authentication, authorization, and consent management across all apps.
This single source of truth prevents inconsistent policy enforcement. Here’s how quickly you can integrate LoginRadius compliance management system from Admin Panel:
Step 3 – Automate Controls
Enable built-in encryption, passwordless login, and MFA.
Use the Passwordless Authentication API for strong-auth compliance and the WebAuthn API for FIDO2 alignment.
Step 4 – Monitor and Audit Continuously
Leverage the Admin Console for dashboards and real-time alerts. Audit logs can be exported instantly for external assessors.
Step 5 – Educate and Iterate
Train teams quarterly on privacy principles. Review risk metrics and refine controls as infrastructure evolves. Compliance should be treated like DevOps—continuous and collaborative.
The Future of Compliance Management
The next wave of compliance is predictive, automated, and integrated.
-
AI-Assisted Monitoring – Machine learning will flag anomalies and potential non-compliance before humans notice.
-
DevSecOps Compliance – Pipelines will block insecure deployments automatically.
-
Privacy as a Service (PaaS) – APIs, like those from LoginRadius, will let developers embed privacy functions on demand.
-
RegTech Convergence – Risk, identity, and compliance tools will merge into unified governance clouds.
-
Global Standardization – Expect cross-border privacy frameworks to simplify multi-region operations.
Forward-looking companies are already preparing by investing in API-first compliance architectures.
Read: Future of Digital Identity Whitepaper
Conclusion
Compliance is the architecture of trust. For developers, it means writing secure, auditable code and leveraging APIs that enforce privacy by design. For executives, it ensures legal protection, operational resilience, and stronger customer relationships.
With LoginRadius, compliance management becomes an integrated capability—automated, transparent, and scalable.
By turning complex regulations into simple configurations, LoginRadius helps organizations stay audit-ready while delivering seamless user experiences.
Compliance done right isn’t just about avoiding penalties; it’s about building digital ecosystems users believe in.
Start simplifying compliance today: Get Started with LoginRadius
FAQs
1. What is compliance management?
It’s the continuous process of ensuring an organization meets regulatory, legal, and internal standards through policies, controls, and automation.
2. What is a compliance management system?
A CMS unifies governance, risk, and monitoring functions—automating evidence collection and policy enforcement.
3. How do you manage compliance effectively?
Centralize identity, automate reporting, and monitor risks in real time with platforms like LoginRadius CIAM.
4. Why is compliance management important?
It protects customer data, reduces legal exposure, and demonstrates corporate accountability.
5. What are compliance management solutions?
Software platforms that automate audits, map regulations to controls, and maintain continuous regulatory alignment.



