Introduction Summary
-
Traditional access control breaks down in modern environments—users change roles, devices shift, and threats evolve too quickly for static rules.
-
Dynamic Access Control (DAC) solves this by continuously evaluating context, risk, identity, and device posture before granting access.
-
In this guide, you’ll learn:
-
What is dynamic access control?
-
How DAC improves secure access control and cyber security
-
Why businesses need dynamic decision-making rather than static access rules
-
Access control meaning, challenges, and implementations
-
How identity platforms like LoginRadius enable real-time evaluation and policy enforcement
-
By the end, you’ll understand why DAC has become the backbone of modern access control programs across enterprises, SaaS platforms, hybrid cloud infrastructures, and regulated industries.
Dynamic Access Control (DAC) is a security method that grants or denies access in real time based on user identity, device posture, behavior, risk level, and context—not fixed rules. It continuously evaluates conditions to enforce secure access control across apps, data, and systems.
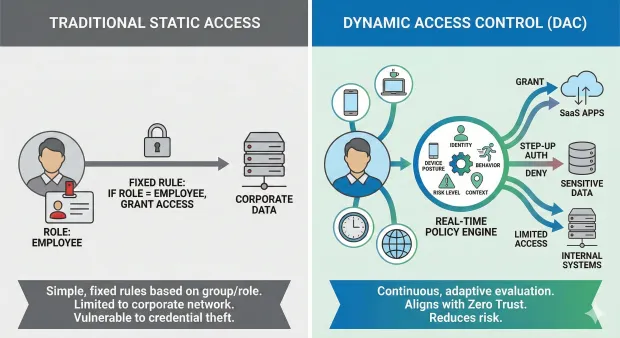
To understand what is dynamic access control, start with the limitations of traditional static access models. Historically, organizations used simple, fixed rules—if a user belonged to a certain group or role, they could access a resource.
This model worked when systems were predictable, devices were limited, and work happened inside a corporate network. But today’s environment is fluid: people log in from personal devices, hybrid locations, and changing roles. Attackers exploit this complexity with credential theft, session hijacking, and lateral movement.
Dynamic Access Control (DAC) modernizes access control in cybersecurity by making authorization adaptive rather than static. Instead of relying solely on predefined group memberships, DAC evaluates real-time attributes such as identity, device health, geolocation, network reputation, user behavior, and risk scores. Access decisions are recalculated continuously, ensuring that permissions adjust to context.
In other words, DAC transforms control of access into a living, intelligent process. When users shift roles, when threats rise, or when device posture changes, DAC modifies access automatically. This reduces over-permissioning, strengthens compliance, and aligns with Zero Trust—“never trust, always verify.”
Understanding DAC gives organizations the clarity they need to build secure access control frameworks that adapt to user activity rather than relying on outdated, static assumptions.
Access Control Meaning & Why Static Models Fall Short
To explain access control, it’s important to start with the fundamentals. Access control is the security practice of defining who can access which resources and under what conditions. Traditional models rely on predefined permissions based on user identity, roles, or groups. In its simplest explanation, access control meaning refers to controlling the “who,” “what,” and “when” of system access.
However, static access models like RBAC (Role-Based Access Control) and ACLs (Access Control Lists) assume environments are stable. But the modern digital ecosystem is anything but stable. Users adopt multiple devices, move between networks, take on temporary assignments, work remotely, and rely on third-party tools. In cyber security, these conditions make fixed access controls increasingly fragile. Permissions often accumulate, creating hidden exposures that attackers can exploit.
Organizations now face access control challenges including:
-
Excessive privileges left unchecked
-
Stale access permissions
-
Lack of visibility across applications
-
Difficulty enforcing least privilege
-
Lack of correlation between identity, device, and risk
This is where Dynamic Access Control becomes crucial. DAC adapts to real-time state changes, enforcing secure access control that evolves as the environment evolves. It aligns with Zero Trust principles, ensuring that access isn’t granted once—it’s continuously evaluated.
How Dynamic Access Control Works
Dynamic Access Control works by evaluating identity, device posture, location, behavior, and risk signals in real time. It uses these attributes to grant, deny, or step-up verification before allowing access.
How Dynamic Access Control Works
Dynamic Access Control applies real-time intelligence to decide whether a user should access a resource, whether the device they're using is trustworthy, and whether contextual factors increase risk. Instead of asking only “who is the user?” DAC asks:
-
Who is the user right now?
-
What device are they using?
-
What is the security posture of that device?
-
Is the access attempt risky or anomalous?
-
What resource are they trying to reach?
-
What is the user’s behavioral pattern?
-
Are environmental conditions normal?
DAC evaluates a combination of identity attributes, device attributes, environmental context, and behavioral signals. These signals feed into a policy engine that determines whether to grant access, deny access, or require step-up verification such as MFA.
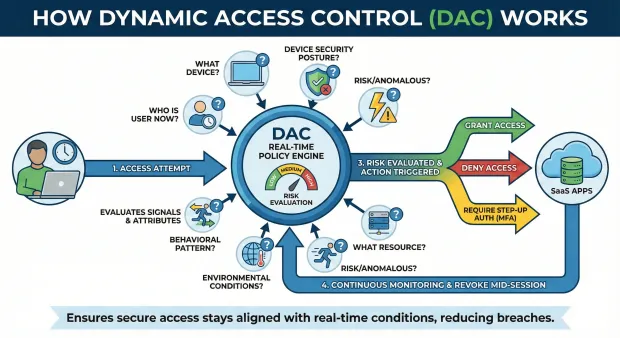
A typical DAC workflow looks like this:
-
The user attempts to access a resource.
-
The system checks identity, device posture, and context.
-
Risk is evaluated—low, medium, or high.
-
Policies trigger an action (grant, deny, or challenge).
-
Access is continuously monitored and can be revoked mid-session if risk changes.
This is a major shift from traditional access control programs, which decide permissions once and rarely update them. DAC ensures that secure access control stays aligned with real-time conditions, reducing breaches and limiting exposure.
Key Components of Dynamic Access Control
Dynamic Access Control consists of several interconnected components that work together to deliver adaptable, real-time security access. These components form the architecture behind modern access control in cyber security.
1. Identity Attributes
Information about the user—role, department, seniority, certifications, privileges. This forms the baseline access model.
2. Device Posture & Trust Level
DAC checks device identity, OS version, jailbreak/root status, malware presence, security patches, and trust score.
3. Contextual Signals
Context includes network reputation, IP address, time of access, geolocation, and impossible travel indicators.
4. Behavioral Analytics
User behavior such as login patterns, click activity, typing rhythm, or session movement, helps identify anomalies.
5. Policy Engine
Rules define how access is determined. Policies may block access from untrusted devices or require MFA for high-risk actions.
6. Continuous Monitoring
Unlike static systems, DAC monitors access during sessions, revoking permission if risk spikes.
These elements collectively form a dynamic, adaptive access control meaning that adjusts to risk and context. When implemented correctly, they transform the access control program into a highly responsive defense layer.
Dynamic Access Control vs. Traditional Access Models
To understand why DAC matters, compare it with traditional access models like:
-
RBAC (Role-Based Access Control)
-
ABAC (Attribute-Based Access Control)
-
ACLs (Access Control Lists)
Static models rely on predefined roles and group memberships. While useful, they lack the adaptability required for modern cybersecurity threats.
Dynamic Access Control expands ABAC by integrating real-time data, not just static attributes. Instead of evaluating attributes once, DAC reevaluates them during every login attempt and even throughout the session.
This solves common access control challenges such as:
-
Stale permissions accumulating over years
-
Users retaining access after role changes
-
Risky device access without verification
-
Access granted during abnormal behavior
-
Inability to detect compromised accounts
DAC also supports continuous authentication—access is maintained only while trust is maintained. If behavior becomes suspicious or device posture deteriorates, access can be paused or revoked immediately.
In short, DAC turns access control from a static checklist into a dynamic, always-on decision engine.
Use Cases of Dynamic Access Control
Dynamic Access Control has critical use cases across industries:
1. Zero Trust Architecture
DAC powers Zero Trust by ensuring no access request is automatically trusted. Every action must be verified continuously.
2. Workforce Access Management
Enterprises with shifting roles and distributed teams use DAC to provide least-privilege access while minimizing risk.
3. Fraud Prevention & Account Security
If a user logs in from a risky IP or uses a jailbroken device, DAC can demand MFA or block the action entirely.
4. Customer Identity (CIAM)
Customer apps use DAC to personalize access while preventing fraudulent transactions, suspicious logins, or abnormal behavior. A reliable customer identity and access management solution, like LoginRadius, helps businesses effortlessly implement dynamic access control.
5. Healthcare & Financial Systems
Regulated industries rely on DAC for compliance with HIPAA, PCI, and SOX by enforcing dynamic, risk-based rules.
6. Device Trust & BYOD
DAC ensures that personally owned devices meet security requirements before accessing internal applications.
7. Cloud & Multi-App Environments
DAC provides consistent access rules across SaaS, on-prem, and hybrid platforms.
Across all these use cases, DAC enhances secure access control without compromising user experience.
Access Control Challenges Addressed by DAC
Organizations face recurring challenges that make traditional access control systems brittle and risky:
1. Over-Permissioning
Static policies lead to permissions accumulating as roles change.
2. Insider Threats
Employees might misuse privileges, intentionally or unintentionally.
3. Device Risk Variability
In a BYOD world, device posture changes constantly—and access must change with it.
4. Identity-Based Attacks
Credential stuffing, phishing, and session hijacking exploit static access assumptions.
5. Lack of Visibility
Organizations struggle to track who accessed what, from where, and under what circumstances.
6. Compliance Gaps
Regulations require contextual access decisions and auditability that static models can’t provide.
Dynamic Access Control directly addresses these issues by enforcing real-time, risk-based access, improving both security access and compliance alignment. It eliminates outdated assumptions about identity and device trust, replacing them with continuous evaluation.
Best Practices for Adopting Dynamic Access Control
Organizations implementing DAC must adopt a flexible and risk-aware mindset. Start by mapping identity, device, and contextual attributes that matter most for your environment. Define which scenarios require strict verification versus those that can tolerate flexibility.
Build a policy framework that includes rules such as:
-
Block access from outdated OS versions
-
Require MFA for new devices
-
Deny access from high-risk locations
-
Re-authenticate during unusual behavior
Next, integrate continuous behavioral analytics to detect anomalies. Ensure your policies account for real-world workflows—too much friction can reduce adoption.
From a governance standpoint, define clear visibility into device trust, policy outcomes, and audit logs. These support compliance and incident investigation.
Finally, ensure your DAC strategy is integrated with modern identity systems—access control shouldn’t operate in isolation. When identity, authentication, device trust, and risk scoring work together, organizations achieve a balanced approach to security and usability.
How LoginRadius Supports Dynamic Access Control
A modern CIAM platform like LoginRadius brings Dynamic Access Control to life by providing a unified foundation for identity, authentication, device trust, and contextual risk evaluation.
LoginRadius enhances DAC by:
1. Real-Time Identity and Access Policies
Administrators can create dynamic rules that evaluate user identity, behavioral signals, device type, and access context before granting access.
2. Adaptive MFA
When risk is detected—such as login anomalies, new devices, or suspicious behavior—LoginRadius triggers step-up authentication automatically.
3. Device Trust & Recognition
LoginRadius models device identity, tracks trusted devices, and monitors device posture, making device trust essential for secure access control.
4. Behavioral Analytics
The platform analyzes user interactions to detect deviations from normal patterns, supporting continuous authentication and anomaly detection.
5. Zero Trust Enablement
LoginRadius aligns perfectly with Zero Trust principles, ensuring that no access request is implicitly trusted. Every request must meet dynamic policy requirements.
6. Centralized Governance & Audit Trails
Organizations gain detailed logs for compliance, investigation, and visibility.
With LoginRadius, enterprises can build a modern access control program that is dynamic, risk-based, and tightly aligned with real-world identity behavior—resulting in stronger security without compromising experience.
Conclusion
Dynamic Access Control is no longer optional. As organizations grow more distributed, attackers grow more sophisticated, and environments grow more complex, static access control models cannot keep up. DAC ensures access decisions remain accurate, contextual, and risk-driven.
By continuously evaluating identity, device posture, behavior, and context, Dynamic Access Control protects data while enabling seamless user experiences. Paired with the right identity infrastructure—such as LoginRadius—organizations gain the ability to adapt access dynamically, enforce Zero Trust, prevent misuse, and meet compliance demands without slowing down their users.
In today’s landscape, the question isn’t whether to adopt DAC—it’s how quickly you can deploy it to strengthen your secure access control strategy.
FAQs
1. What is dynamic access control?
Dynamic Access Control is a security method that grants or denies access based on real-time identity, device, and risk signals.
2. What is access control in security?
Access control in security determines who can access which resources and under what conditions.
3. What are common access control challenges?
Challenges include excessive privileges, device risk, insider threats, and lack of contextual awareness.
4. What is access control and security?
It refers to enforcing rules that protect data, applications, and systems by controlling who or what can access them.