Introduction Summary
The modern digital experience is overloaded with passwords, logins, and fragmented identity workflows. Users switch between dozens of applications daily—each demanding separate authentication. IT teams spend hours on password resets. Businesses lose conversions due to login friction. Attackers exploit weak credentials with increasing speed.
Single Sign-On (SSO) solves these problems by letting users authenticate once and access multiple apps without logging in again. It simplifies user journeys, centralizes identity governance, reduces password burden, and strengthens security.
In this comprehensive guide, you’ll learn:
-
What single sign on means (sso meaning + sso login foundations)
-
How SSO works technically using SAML, OAuth, and OIDC
-
Types of SSO across enterprise, consumer, and federated environments
-
Security benefits and real-world applications of SSO
-
Challenges, risks, and best practices
-
How LoginRadius enables secure, scalable SSO
-
Why SSO is essential for Zero Trust and modern IAM
By the end, you’ll have a complete, expert-level understanding of SSO—both conceptually and practically.
Single Sign-On (SSO) is an authentication method that lets users log in once and access multiple applications without re-entering credentials. A centralized Identity Provider (IdP) verifies identity and issues secure tokens that connected apps trust.
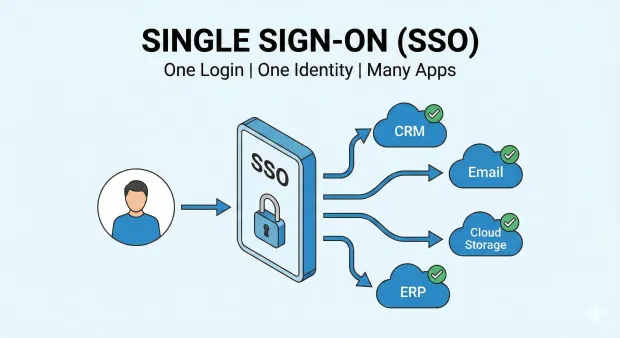
Single Sign-On (SSO) is a centralized authentication approach that allows users to sign in once and use that one authenticated session to access multiple independent apps, services, or systems. Instead of entering credentials repeatedly, users authenticate through a single identity provider (IdP). Each application then trusts the authentication performed by this IdP.
This means:
-
One login
-
One identity provider
-
Many applications
-
No repeated authentication
SSO meaning can be simplified as: a unified login experience across all systems you need to access.
SSO solves major modern challenges:
-
Password fatigue : People can’t manage dozens of unique passwords.
-
Security vulnerabilities : More passwords mean more opportunities for credential theft.
-
Fragmented UX : Logging into each app disrupts flow.
-
Operational overhead : IT spends time on password resets rather than strategy.
With SSO, security and convenience coexist. Users log in faster. Admins manage access easily. Developers integrate authentication without rebuilding it for every app. Businesses deliver seamless cross-application experiences.
How Does SSO Work?
SSO works by centralizing authentication in an identity provider. Once the IdP verifies the user, it issues a signed token or assertion that connected applications trust. This lets users access multiple apps without logging in again.
SSO operates through a trust relationship between applications (service providers) and a centralized identity provider (IdP). The IdP handles all authentication and generates secure tokens that applications accept.
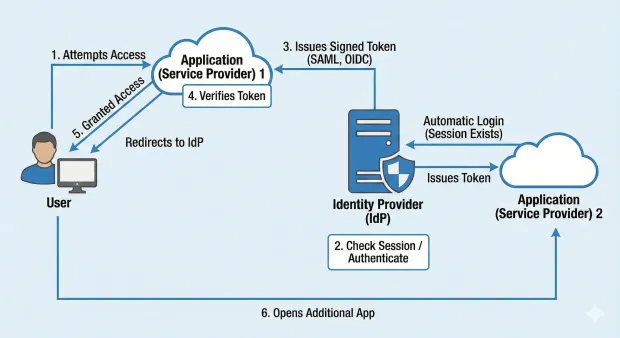
Here’s the expanded SSO flow:
1. User attempts to access an application
The app detects no active session and redirects the user to the identity provider. This redirection includes metadata identifying the app and the requested action.
2. Identity provider checks for an existing session
If the user is not logged in, they authenticate using a password, MFA, passkey, biometrics, or passwordless methods. If they’re already authenticated, the IdP skips new login prompts, maintaining a smooth UX.
3. Identity provider issues a signed token
The IdP generates a cryptographically signed assertion/token (SAML, OIDC ID token, or OAuth access token) containing identity information. Its signature prevents tampering.
4. Application verifies the token
The app checks the digital signature, audience, issuer, timestamps, nonce, and other claims to ensure validity.
5. The user is granted access
After validation, the user gains access. A secure session is established.
6. User opens additional applications
Each app checks with the IdP. Because a session already exists, the login is automatic.
This makes SSO login incredibly fast, consistent, and secure across multiple systems.
SSO Protocols: SAML, OAuth 2.0, OpenID Connect
SSO isn't one technology—it’s a framework powered by modern identity protocols. Let’s learn about them in detail.
SAML 2.0 (Security Assertion Markup Language)
SAML 2.0 is used heavily for enterprise workforce SSO.
-
XML-based assertions
-
Strong digital signatures
-
Ideal for older and enterprise SaaS apps
-
Robust cross-domain identity federation
OAuth 2.0
Focused on authorization, not authentication.
-
Delegates controlled resource access
-
Common for API authorization
-
Often paired with OIDC for login
OpenID Connect (OIDC)
OpenID Connect is a modern SSO standard, built on top of OAuth.
-
JSON-based
-
Developer-friendly
-
Mobile-friendly
-
Supports passwordless + modern MFA
-
Ideal for customer IAM
OIDC has become the default protocol for new applications.
Types of Single Sign-On
Enterprise Workforce SSO
Enables employees to access corporate apps with a single login.
Consumer SSO (Social Login)
“Login with Google/Apple/LinkedIn” flows.
Federated SSO
Trust established across multiple organizations.
Cross-Domain SSO
Single login across multiple internal apps or product suites.
Cloud SSO
Distributed access across SaaS and cloud-native applications.
Benefits of Single Sign-On
SSO provides meaningful advantages across usability, security, and operational efficiency. These expanded bullets highlight the real impact:
A Unified, Seamless User Experience That Reduces Drop-Off
With SSO, users authenticate once and navigate across applications without interruption. The elimination of repetitive logins significantly reduces friction during onboarding, product exploration, and daily workflows.
This improves user satisfaction, increases time-on-task for workforce apps, and boosts conversion and retention in consumer products. SSO is a direct antidote to “login fatigue,” which causes users to abandon sessions prematurely.
Stronger Security Through Centralized Credential Management
Centralizing authentication eliminates fragmented credential stores across dozens of systems. By consolidating login into one authoritative IdP, organizations drastically reduce password reuse, weak passwords, and inconsistent policy enforcement.
Security teams can enforce MFA, monitor authentication risk, and apply adaptive controls at a single point—strengthening the entire security boundary.
Operational Efficiency for IT and Support Teams
Password resets are among the top drivers of IT support load. With SSO, fewer credentials mean fewer reset tickets and less administrative overhead.
Onboarding becomes faster (one identity, many apps), and offboarding is more secure (terminating one profile revokes access everywhere). As systems scale, this results in massive time and cost savings for IT teams.
Better Governance and Compliance Visibility
SSO gives organizations a centralized audit trail of all authentication activity. This unified view simplifies compliance with frameworks like SOC 2, HIPAA, GDPR, PCI DSS, and ISO 27001.
Consistent access policies, quick revocation, and fine-grained reporting all contribute to a cleaner governance posture.
SSO Security Model
The SSO security model ensures that identity verification is consistent, trusted, and tamper-proof across all applications. Here’s how it looks like:
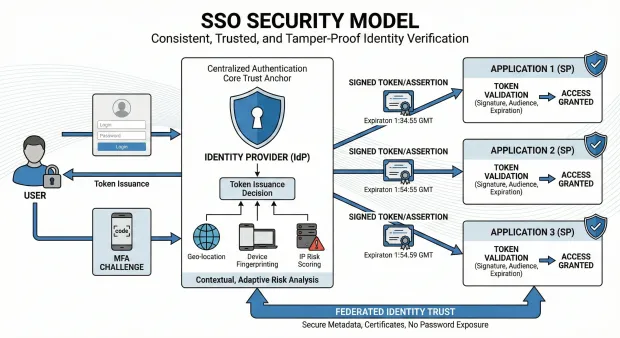
Centralized Authentication as the Core Trust Anchor
By having the IdP authenticate users, organizations eliminate the need for each app to maintain its own passwords or MFA setup. The IdP becomes the system of record for identity verification, ensuring consistent security controls and centralized policy enforcement.
Token-Based Trust Using Secure, Signed Artifacts
SSO relies on signed assertions and tokens that applications validate cryptographically. These artifacts ensure the identity information has not been altered and originates only from the trusted IdP. Expiration, audience matching, and signature validation protect against replay and impersonation.
Contextual, Adaptive Risk Analysis Before Token Issuance
Modern SSO uses adaptive intelligence—geo-location, device fingerprinting, IP risk scoring—to evaluate whether a login is normal or suspicious. High-risk activity can trigger MFA, block the session, or require re-authentication. This layered defense ensures identity verification is dynamic rather than static.
Federated Identity Trust Across Applications and Domains
Trust relationships between the IdP and service providers are established through secure metadata and certificates. Federation ensures that identity can travel securely between apps and organizations without exposing passwords or relying on insecure user-managed credentials.
SSO Challenges and Risks
SSO delivers immense value, but organizations must be aware of the potential risks and misconfigurations that can weaken it.
Dependence on the Identity Provider as a Single Point of Failure
Because all authentication flows through the IdP, downtime or latency at the identity layer can cascade into system-wide outages. High availability, redundancy, and distributed IdP architecture are essential for minimizing access disruptions.
Incorrect Token Validation or Misconfigured Trust Relationships
Service providers must validate the issuer, signatures, timestamps, audience, and token structure. Misconfigurations can undermine SSO security, especially in multi-app, multi-domain deployments. Regular trust audits and certificate rotation are essential.
Security Risks from Long-Lived Sessions
If SSO sessions persist for too long, compromised or unattended devices can provide ongoing unauthorized access. Organizations must balance user convenience with secure session expiration, idle timeout policies, and real-time device checks.
Over-Reliance on Password-Based Primary Authentication
When SSO still uses a password as the first authentication step, the entire ecosystem inherits password vulnerabilities. Upgrading the IdP to MFA or passwordless methods is crucial for preventing credential-based attacks.
How SSO Fits Into Zero Trust
Zero Trust requires continuous identity verification—SSO supports this by centralizing authentication and enabling consistent policy enforcement. It allows:
-
MFA verification at the identity layer
-
Secure token-based access across applications
-
Continuous session evaluation
-
Identity and device posture checks
-
Least-privilege access enforcement
SSO is often the first step toward a full Zero Trust architecture.
SSO Best Practices
To implement SSO securely and effectively, organizations should follow these expanded best practices:
Use Modern Protocols (OIDC) and Short-Lived Tokens
OIDC provides modern, lightweight authentication that’s compatible with mobile, web, and API-based ecosystems. Short-lived tokens minimize exposure if compromised. Using refresh tokens with revocation lists further strengthens the session boundary.
Enforce MFA or Passwordless Authentication at the IdP Level
All downstream applications inherit security from the IdP. Enforcing MFA or passwordless login—via biometrics, passkeys, or app-based verification—ensures that a compromised password doesn’t compromise the entire system.
Apply Adaptive Access Policies Based on Behavior and Context
Adaptive policies evaluate login context such as browser fingerprint, location, device reputation, and behavioral anomalies. When something looks unusual, the system can demand step-up verification, ensuring that SSO remains secure without adding unnecessary friction.
Maintain Strong Governance Through Logging and Audits
Detailed logging allows organizations to investigate incidents, analyze access patterns, and prove compliance. Regular audits—checking certificates, token policies, and trust relationships—ensure SSO stays secure, updated, and aligned with organizational needs.
How LoginRadius Supports Secure, Scalable SSO
LoginRadius simplifies enterprise and consumer SSO by merging security, adaptability, and developer-friendly design.
Full Protocol Support Tailored for Any Application Stack
LoginRadius supports SAML, OAuth 2.0, OIDC, JWT, and custom federation. This allows legacy enterprise systems and modern cloud apps to share the same identity framework without re-architecting integrations.
Built-In Adaptive Authentication for Real-Time Risk Mitigation
LoginRadius evaluates IP risk, device fingerprint, behavioral anomalies, geo-velocity, and network integrity before granting SSO access. High-risk sessions can trigger MFA or block access, ensuring token issuance never becomes a blind trust exercise.
Passwordless Capabilities Integrated Directly Into SSO
With support for biometrics, passkeys, magic links, and OTPs, LoginRadius turns the identity provider into a passwordless gateway. Downstream apps benefit automatically—no need for custom MFA in each system.
Enterprise-Grade Identity Governance and Compliance
LoginRadius centralizes permissions, logs, consent, and audit trails. Security teams maintain full visibility over user access patterns and can enforce compliance for SOC 2, GDPR, ISO 27001, HIPAA, and more.
Conclusion
Single Sign-On has evolved from convenience to a critical foundation for identity. It enables organizations to simplify authentication, eliminate password overload, strengthen security, and provide seamless multi-app experiences. But SSO must be implemented thoughtfully—paired with MFA, adaptive risk analysis, strong governance, and short-lived tokens.
LoginRadius enables organizations to deploy secure, scalable SSO using modern protocols, adaptive authentication, passwordless capabilities, and enterprise governance. It transforms SSO from a simple login convenience into a powerful identity strategy aligned with Zero Trust and modern CIAM.
SSO isn’t just a login solution—it’s the gateway to a seamless digital experience.
FAQs
1. What is single sign on?
Single sign on (SSO) is an authentication method that lets users sign in once and access multiple apps without re-entering passwords.
2. How does SSO work?
SSO works through a centralized identity provider that authenticates the user and issues secure tokens trusted by connected applications.
3. What does single sign on mean?
It means one authenticated session can be reused across many systems, eliminating repeated logins.
4. What is SSO login?
SSO login refers to the seamless process where users sign in through the IdP and gain instant access to all linked applications.


