Customer expectations are dramatically different now from what they were a decade ago. They want speed, personalization, convenience - and they want it all with no compromise on security.
That's where CIAM, or Customer Identity and Access Management, steps in.
In this guide, we will break down what CIAM is, why businesses use it, how it works, what CIAM components matter, real-world use cases, CIAM vendor comparisons, challenges, best practices, and how to choose the right CIAM platform for your stack.
Let's get started.
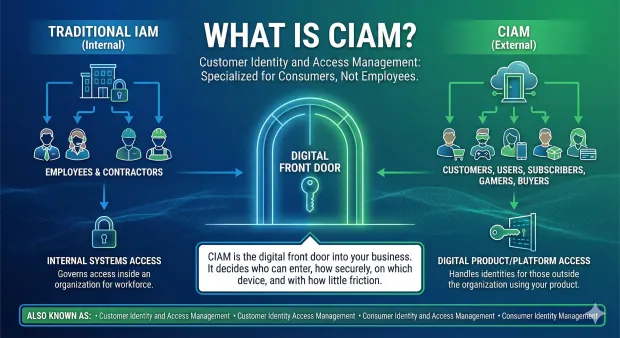
What is CIAM?
Customer Identity and Access Management, or CIAM, is a specialized branch of identity and access management that has been designed just for consumers - not employees.
Traditional IAM governs who gets access inside an organization: employees and contractors.
CIAM handles identities for those outside of your organization: all your customers, users, subscribers, buyers, gamers, and application users who touch and use your digital product.
A simple way to think about CIAM: It is the digital front door into your business. It decides who can enter, how securely, on which device, and with how little friction.
It's also known as :
-
Customer Identity and Access Management
-
Customer Identity Access Management
-
Consumer Identity and Access Management
-
Consumer Identity Management
-
Customer Identity and Access Management Solutions
All of these terms essentially describe the same thing: managing customer identity at scale, both securely and seamlessly.
Why do Businesses use CIAM?
Businesses adopt CIAM to solve three major problems:
1. Security
Customers have high expectations for account safety, fraud prevention, strong authentication, and privacy controls.
2. Growth
Frictionless sign-up and login directly impact conversions and retention.
Slow login = lost revenue.
3. Single Identity Across Channels
Today's businesses operate across apps, web, mobile, kiosks, marketplaces, and partner ecosystems. You can't deliver personal and consistent experiences without a single identity backbone.
Simply put:
Businesses use CIAM to scale without losing trust, security, or user experience.
Why is CIAM Important for Unified Customer Data?
Most companies store customer data across a variety of systems: CRM, marketing tools, loyalty apps, eCommerce, mobile apps, POS systems, and more.
This creates fragmentation.
And, fragmentation kills personalization.
CIAM can help address this fragmentation because it provides:
-
Single source of truth for unified customer identities
-
Profiles consolidated across all channels
-
Consent and privacy management across touchpoints
-
Cleaner data pipelines for analytics and personalization
This turns disconnected interactions into a continuous customer journey, not a series of disjointed events.
Why is CIAM Important for Customer Experience?
Every conversion funnel starts with identity:
Signup → Login → MFA → Profile → Preferences → Checkout → Support
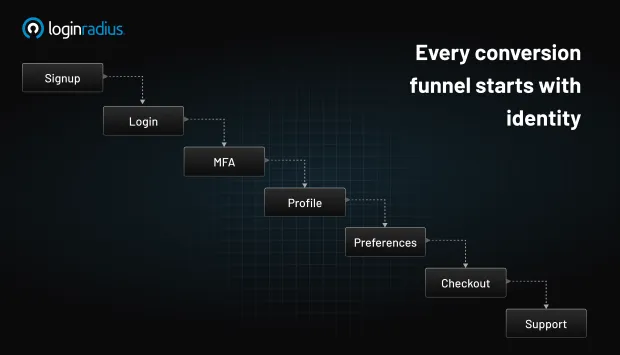
Any confusing or slow step means users drop.
The powerful CIAM system enhances CX by offering:
-
Frictionless login and sign-up
-
Passwordless and social login
-
Fast, adaptive authentication
-
Localization across languages
-
Consistent cross-device experiences
That's why companies such as Microsoft place so much emphasis on CIAM as a CX-first layer, rather than just a security tool.
How CIAM Works
Although every CIAM platform implements features differently, the general pattern for workflow is typically as follows:
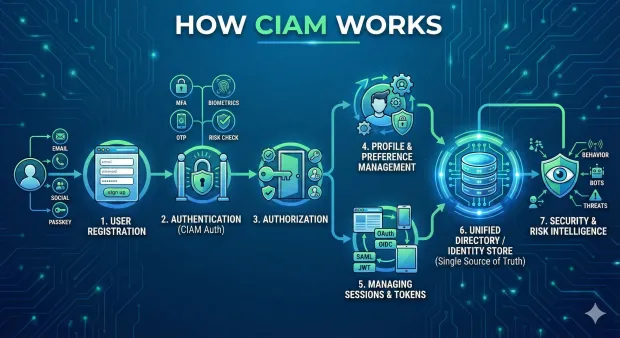
User Registration
This journey starts with sign-up. Users sign up through email, phone, social login, passwordless methods, or passkeys. CIAM has made this step fast and flexible, tailored according to user preference.
Authentication (CIAM Authentication)
Users authenticate using passwords, MFA, biometrics, OTPs, passkeys, or adaptive risk-based checks once registered. This helps in balancing security and convenience.
Authorization
After authentication, the system authorizes the user to access resources based on permissions, roles, and contextual policies.
Profile & Preference Management
CIAM platforms maintain dynamic profiles that capture preferences, consent choices, and progressive profiling data, while doing all of it in a manner that respects privacy and compliance requirements.
Managing Sessions and Tokens
It maintains secure sessions by using standards such as OAuth 2.0, OpenID Connect, SAML, and JWTs. They ensure consistent access across applications and devices.
Unified Directory / Identity Store
Central to it all is a centralized identity store: a single source of truth that ensures customer data is consistent across each and every digital touchpoint.
Security & Risk Intelligence
The CIAM platform evaluates the risk signals continuously. The signals may involve unusual behavior, suspicious logins, compromised credentials, or bots to protect accounts without interrupting the user experience.
What Are the Core Components of CIAM?
The key elements of a CIAM platform include:
Authentication & Access
-
Passwordless, passkeys, MFA
-
Social login
Registration & Onboarding
-
Flexible signup and onboarding flows
-
Custom verification steps
Identity Data Management
-
Single user directory
-
Profile and preference management
-
Self-service account management
Security, Privacy & Compliance
-
Consent and privacy controls
-
Fraud prevention and risk detection
Performance & Reliability
-
High scalability
-
Global availability and redundancy
Developer Tools & Extensibility
-
Identity APIs and SDKs
-
Webhooks, event triggers, and custom logic
-
Integration frameworks
Insights & Optimization
-
Analytics and reporting
-
Journey optimization and monitoring
Every CIAM vendor offers some combination of these. However, depth, flexibility, and ease of implementation vary so widely that often this becomes the deciding factor for enterprise teams.
Key CIAM Challenges You Shouldn’t Ignore
CIAM promises security, scale, and seamless experience, but getting there isn't always as straightforward. Common challenges that most organizations face include:
Balancing Security With UX
Stronger authentication generally involves friction, while weakening it exposes a risk. And finding the right middle ground is difficult.
Migrating Existing Users Safely
Migrating millions of accounts-passwords, hashes, tokens, identities-on without breaking login or trust is arguably one of the hardest technical steps.
Integrating with Legacy Systems
Custom-built auth, old infrastructure, or stitched-together tools make the adoption of CIAM complex.
Managing Global Privacy Regulations
GDPR, CCPA, PDPA, and region-specific requirements are in constant evolution; CIAM shall move ahead, not hurting the user journey.
Avoiding Vendor Lock-In
Some platforms make it easy to customize. until it's time to scale or change direction.
Handling Traffic Spikes Reliably
Sales events, product launches, and seasonal surges require elastic, fail-proof infrastructure.
Supporting Multi-device, Multi-channel Journeys
Customers now hop between web, mobile, smart devices, and social accounts, where authentication must remain consistent everywhere.
Therefore, it is critical to select a CIAM platform that solves these challenges out of the box and can provide a secure and seamless experience at global scale.
CIAM Best Practices
A strong CIAM strategy isn't just about securing accounts; it's about creating a seamless experience for customers and an easy-to-maintain product for developers. Here are the practices most modern teams lean on today:
Go Passwordless-first
More and more businesses are abandoning passwords, as they cause friction and introduce risk. Passkeys, magic links, or OTPs keep things secure without slowing the user down.
Adopt Strong MFA Everywhere it Makes Sense
MFA should not be a thing that customers fear. The idea is simple: let's safeguard accounts with options that feel natural, whether by push notifications, biometrics, or one-tap approvals.
Use Progressive Profiling
Instead of asking for everything upfront, collect customer data over time. It builds trust and increases conversion.
Choose Platforms Built on APIs and Extensibility
When your CIAM sits on clean, modern APIs, integrations, custom workflows, and automation all become much easier.
Align with Zero Trust Principles
Treat every login, every device, every session as something which needs validation. It’s the safest way to operate at scale.
Centralize Identity Across all Touchpoints
One single identity layer maintains consistency in data, diminishes duplication, and makes the customer experience smoother.
Balance Friction and Security with Adaptive Policies
Not every login should be treated equally. Step-up only when necessary; for example, suspicious behavior, high-value actions.
Developers Should be Kept in Mind
CIAM should reduce complexity, not add to it. Dev-friendly SDKs, docs, and workflows make long-term maintenance easier.
Eliminate Dark Data and Identity Silos
Consolidating your identity data will improve analytics, privacy compliance, and personalization.
When all this comes together, your CIAM strategy stops being just "security infrastructure"; it becomes a real competitive advantage.
Common CIAM Use Cases
CIAM isn't just something that tech giants care about; it quietly powers the login and identity experience for almost every modern industry. Wherever customers need to sign up, sign in, or manage their profile, CIAM sits at the center.
Across all these industries, the pattern is the same: customers want fast, secure, unified access on every device, with no hoops to jump through. And modern CIAM platforms are looking to deliver the same.
Ecommerce & Retail
-
Quicker logins translate to better conversions.
-
One customer profile across web, mobile, and even in-store POS
-
Strong fraud prevention during big sale events or spikes in traffic.
Media & Entertainment
-
Personalized content based on user behavior
-
Single sign-on across smart TVs, mobile apps, and browsers
SaaS & Digital Platforms
-
Secure account creation and user onboarding
-
Multi-tenancy identity support
-
Flexible, API-driven customization for varied product flows
Financial Services & Fintech
-
Strong, compliant authentication
-
Meeting regulations such as KYC, PSD2 and regional privacy rules
-
Real-time fraud and risk monitoring
Healthcare
-
Privacy-first identity and strict data protection
-
Easy and secure access to patient portals and health records
IAM vs. CIAM
CIAM and IAM sound similar. However, they serve different audiences and solve different problems.
The easiest way to understand the difference is this:
-
IAM is built for employees.
-
CIAM is built for customers.
IAM deals with internal security and access control. On the other hand, CIAM provides a seamless, secure, and personalized experience in apps, websites, and devices for millions of customers.
Key Differences at a Glance
| Feature | IAM: Identity & Access Management | CIAM - Customer Identity & Access Management |
|---|---|---|
| Who it's for | Employees, contractors | Customers, members, end users |
| Scale | Hundreds to thousands | Millions+ |
| User Experience | Not a priority | Top priority: fast and frictionless |
| Security Focus | Insider threats | Fraud, bots, account takeover |
| Authentication Style | Strict, standardized | Flexible: social login, passkeys, passwordless, adaptive MFA |
| Integrations | Internal applications, HR systems, corporate tools | Mobile apps, websites, APIs, IoT |
| Privacy Needs | Compliance-driven access control | Consent, preferences, transparency, trust |
| Data Handling | Role-based access | Unified customer profiles and behavioral data |
In other words,
IAM secures your business from within.
CIAM keeps your customers safe — and keeps them coming back.
Which IAM Challenges Does CIAM Solve?
Traditional IAM works great for employees, but it falls short when trying to use it for customers. CIAM fills in those gaps by handling things IAM was never designed for.
Here's what CIAM solves that IAM can't:
-
Massive scale-high millions of users, without slowing down one bit.
-
Consistent experiences across every channel — from web, mobile, APIs, to IoT.
-
Consumer-grade UX: fast, simple, low friction.
-
Modern authentication options: social login, passwordless, biometrics, passkeys.
-
User-level consent and privacy controls - not just role-based policies.
-
Unified profiles personalize each moment, with the same identity across every touchpoint.
-
Built-in fraud detection and risk scoring to prevent bots and account takeovers.
IAM alone can't handle these because it was built for employees, not millions of customers moving across devices and platforms.
How to Choose a CIAM Vendor
Picking a CIAM platform is a big decision. It affects your security, customer experience, and future growth. When you evaluate the vendors, focus on the areas that actually matter to long-term success.
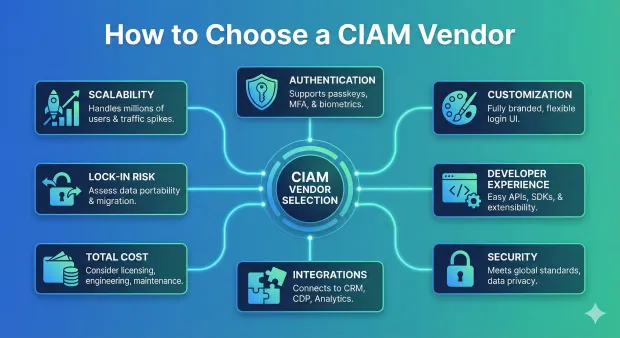
Scalability & Performance
-
The platform can handle millions of users.
-
Does it stay fast during traffic spikes, product launches, or sale events?
Authentication Models
-
Does it support modern login methods: passkeys, passwordless, MFA, and biometrics?
-
Does it support adaptive authentication and MFA?
Customization
-
Can the login UI be fully controlled by both marketing and dev teams?
-
Is it flexible enough to match your brand across every touchpoint?
Developer Experience
-
Are the APIs, SDKs, and docs easy to work with?
-
Does it provide webhooks, rules, and extensibility for custom logic?
Security & Compliance
-
Does the vendor meet global standards and certifications?
-
Are there any in-built privacy tools (consent, data rights, policies)?
Integration Ecosystem
Can it plug into your CRM, CDP, e-Commerce platform, analytics, or marketing automation stack?
Total Cost of Ownership
What are you really paying for - licensing, engineering time, maintenance, hidden costs?
Vendor Lock-In Risk
If necessary, can you migrate without a painful rebuild?
Top CIAM Vendors
Choosing the best CIAM solution is one of the most important decisions for any business. It should be able to handle customer login, identity, or authentication at scale.
The market is full of options. Yet each CIAM platform offers a different mix of scalability, extensibility, and customer experience.
1. LoginRadius
LoginRadius is best for High-Scale Customer Identity and Access Management.
Pros
-
Purpose-built customer identity and access management platform
-
Handles millions of users with low latency
-
Fully customizable, hosted login pages
-
Excellent developer experience: clean APIs, SDKs, and documentation
-
Strong support for passwordless, passkeys, MFA, and modern CIAM authentication
-
Global privacy controls and consent management
-
Fastest time-to-market with no-code, low-code, AI-branding options
Cons
Smaller brand than Microsoft/Okta, but far more specialized in CIAM.
2. Auth0 & Okta Customer Identity Cloud
Pros
-
Large ecosystem and marketplace
-
Flexible rules and extensibility
-
Popular with startups
Cons
-
High cost at scale
-
Rate limits and pricing changes
-
More complex for customized journeys
3. Ping Identity
Pros
-
Enterprise-grade security
-
Great for hybrid deployments
-
Strong federation features
Cons
-
Complex setup
-
UI Customization Limitations
4. ForgeRock
Pros
-
Extremely powerful CIAM workflows
-
Advanced governance and compliance
-
Great for very large enterprises
Cons
-
Heavy engineering effort
-
Not ideal for growth-stage companies
5. Microsoft Entra External ID
Pros
-
Strong security
-
Deep integration with the Microsoft ecosystem
-
Reliable global infrastructure
Cons
-
Limited flexibility for consumer UX
-
Requires Azure expertise
-
Not built for high-freedom customization
6. AWS Cognito
Pros
-
Low cost
-
Great for AWS-native applications
-
Scalable infrastructure
Cons
-
Limited UX customization
-
Difficult setup
-
Not marketer-friendly
7. Stytch
Pros
-
Passwordless-first approach
-
Clean developer APIs
-
Good for fast builds
Cons
-
Not enterprise-deep
-
Limited global compliance support
8. Frontegg
Pros
-
Strong B2B/tenant management
-
Good dashboards and RBAC
Cons
-
Better for B2B SaaS than consumer identity
-
Can get expensive with increasing use
9. Descope
Pros
-
No-code and low-code builder
-
Quick setup for authentication screens
-
Developer-friendly
Cons
-
Newer vendor
-
Smaller ecosystem
Comparing Top CIAM Solutions
| Vendor | Best For | Key Strengths | Common Limitations |
|---|---|---|---|
| LoginRadius | Consumer-scale CIAM, high CX | Customization, scalability, UX, modern CIAM authentication, human support, strong uptime | Smaller brand vs giants |
| Auth0 (Okta CIC) | Flexible dev teams | Extensibility, marketplace | Pricing + complexity |
| Ping Identity | Large enterprises | Security, hybrid identity | Harder setup; limited UI |
| ForgeRock | Complex enterprise identity | Workflow depth, compliance | Heavy engineering |
| Microsoft Entra External ID | Microsoft-centric orgs | Security, ecosystem fit | Limited customization |
| AWS Cognito | AWS-native apps | Low cost, scalable | Rigid UI, complex documentation |
| Stytch | Startups | Passwordless API simplicity | Limited enterprise features |
| Frontegg | B2B SaaS | Tenant management | Less suited for CIAM |
| Descope | No-code auth | Visual builder | Smaller ecosystem |
Ultimately, selecting the appropriate CIAM solution is not a question of features. It is about finding the platform that can grow with your product, your users, and your future road map. So choose carefully!
Why LoginRadius?
LoginRadius is not an identity tool for general purposes. It's a CIAM platform engineered specifically to handle high-scale consumer experiences.
Its differentiation comes through a mix of performance, customization, security, and real human support that the majority of vendors don't offer.
Here's why companies choose LoginRadius:
-
Blazing fast performance: ~99.99% uptime and sub-200ms authentication response times across a globally distributed edge network
-
Massive scalability: Proven to support hundreds of millions of monthly active users without slowdown
-
Zero breach history: An impeccable security record owing to strict controls, continuous monitoring, and enterprise-grade architecture.
-
AI-powered branding: With Hosted Pages 2.0, create fully branded login experiences in minutes, powered by AI.
-
Real human support: direct access to senior identity engineers, not bots or slow ticket queues
-
Developer-first experience: Clean APIs, modern SDKs, and deep extensibility for any use case
-
Modern authentication: Passwordless, passkeys, MFA, adaptive policies, and biometric flows
-
**Full UI ownership: **Complete control over login, sign-up, profile, and MFA journeys; no rigid templates.
-
Better ROI: faster implementation, lower maintenance, predictable pricing
-
Enterprise security + compliance: GDPR, CCPA, SOC2, ISO27001, HIPAA options, privacy-by-design
-
Low vendor lock-in: Built on open standards; OAuth 2.0, OIDC, SAML, WebAuthn, so you are never trapped
If you're looking for a fast, scalable, secure CIAM platform with unparalleled branding freedom, then LoginRadius is designed for just that.
To Sum Up
CIAM is more than a login system. It's the backbone of customer experience, security, personalization, and growth.
As customers demand seamless yet secure digital experiences, businesses require a CIAM strategy that can scale without slowing them down.
If you are exploring CIAM platforms or building your identity architecture:
-
Start your journey with LoginRadius
-
Click here to request a demo.
-
Contact our identity team today!
FAQs
1. What is CIAM?
CIAM is Customer Identity and Access Management, enabling secure signup, login, and access for customers. It ensures a seamless identity experience while protecting user data.
2. Why do businesses need CIAM?
Businesses use CIAM to improve security, reduce login friction, and unify customer identities across channels. This boosts conversions, retention, and trust.
3. How does CIAM improve customer experience?
CIAM provides fast, frictionless login options like passwordless and social authentication.
It keeps access consistent across devices for a smooth user journey.
4. How does CIAM work?
CIAM works through registration, authentication, authorization, profile management, and secure sessions. It centralizes identities and uses risk intelligence to prevent threats.
5. How do you choose the right CIAM vendor?
Look for scalability, modern authentication options, customization, strong security, and easy integrations. Also consider total cost, developer tools, and vendor lock-in risks.


