Quick Summary
-
Authentication verifies a user’s identity.
-
Authorization determines what that verified user is allowed to access.
-
Authentication always occurs before authorization.
-
Authentication uses credentials (passwords, biometrics, MFA).
-
Authorization uses policies, roles, and permissions to grant or deny access.
-
Together, they secure apps, APIs, and user data in modern identity systems.
-
In CIAM, strong authentication reduces fraud, while granular authorization enforces least privilege.
-
Common authorization models include RBAC, ABAC, PBAC, and ReBAC.
-
In API security, authentication issues tokens; authorization evaluates scopes and claims.
Introduction
Despite being two of the most fundamental concepts in identity and access management, authentication vs authorization remains one of the most commonly misunderstood comparisons in security. The terms often appear together in login flows, yet they solve entirely different security problems. Authentication verifies *who *a user is, while authorization determines *what *that verified user can access.
As applications move toward cloud-native, API-driven, and Zero Trust architectures, understanding this distinction is essential for developers, architects, and security teams. This blog breaks down both concepts with clear definitions, workflows, and real-world examples so you can implement identity decisions with accuracy and confidence.
What is Authentication? (AuthN)
Authentication is the process of verifying a user’s identity. It answers a simple but critical question: “Are you really who you claim to be?” In modern identity systems, authentication is the first step in establishing trust before granting access to any application, API, or resource.
At its core, authentication compares user-provided credentials against what the system already knows. These credentials typically fall into three categories:
-
Something you know: passwords, PINs, recovery questions
-
Something you have: OTP apps, hardware tokens, smart cards
-
Something you are: biometrics such as fingerprints or facial recognition
Developers often combine these factors, such as a password plus a one-time code, to increase assurance levels and reduce credential-based attacks.
In practice, authentication follows a predictable flow: a user presents credentials, the identity provider evaluates them against stored records, and if the match is valid, establishes the user’s identity. Once authenticated, the system may initiate the next steps, such as generating a session, issuing an ID token or access token, or prompting for additional factors depending on the required assurance level.
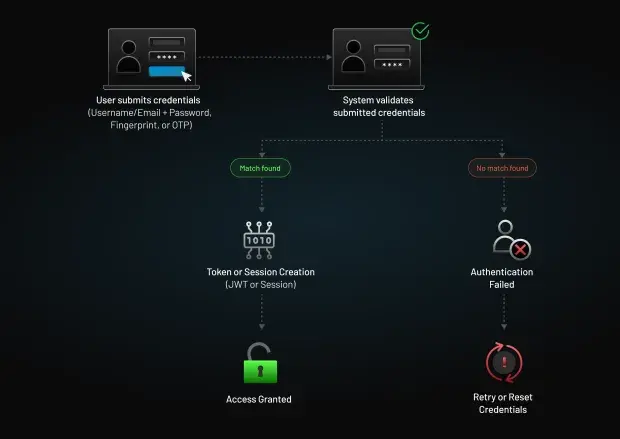
For deeper fundamentals, see our full guide on authentication.
What is Authorization? (AuthZ)
Authorization is the process of determining what an authenticated user is allowed to access or do. While authentication establishes identity, authorization evaluates the permissions, roles, and policies associated with that identity to answer: “What actions are you permitted to perform?”
Authorization decisions typically operate at multiple levels:
-
Resource-level access: which APIs, endpoints, or data objects a user can reach
-
Action-level access: read, write, edit, delete, approve, or administer
-
Context-based rules: location, device, time of day, risk score, or session state
This makes authorization essential in modern CIAM, multi-tenant SaaS, and API-first architectures where different user types, customers, partners, admins, service accounts require different access scopes.
Unlike authentication, authorization happens behind the scenes. The end user rarely sees the logic; they simply encounter allowed actions or access-denied responses based on predefined rules. These rules are commonly implemented through models such as role-based access control (RBAC), attribute-based access control (ABAC), or policy-based frameworks.
Authentication vs Authorization: Key Differences
From an implementation standpoint, authentication and authorization sit at different layers of the identity stack and operate on different types of data. Authentication focuses on identity assurance, while authorization focuses on policy enforcement. Both are required, but they are executed by different services, triggered by different signals, and validated through different mechanisms.
Authentication (AuthN) establishes identity by validating factors, like credentials, biometrics, or cryptographic proofs against an identity store. Its output is an asserted identity, often represented as a session, token, or signed claim.
Authorization (AuthZ) consumes that asserted identity and evaluates it against access control logic. This logic may be based on roles, attributes, environmental conditions, resource scopes, or policy evaluation engines.
Technically, the difference between authentication and authorization looks like this inside a modern IAM flow:
| Dimension | Authentication (AuthN) | Authorization (AuthZ) |
|---|---|---|
| Primary Function | Identity proofing and credential validation | Policy evaluation and access decisioning |
| Executed By | Identity provider (IdP), authentication service, or login gateway | Authorization server, policy engine, API gateway, or resource server |
| Data Evaluated | Password hashes, public keys, biometrics, device signals | RBAC roles, ABAC attributes, OAuth scopes, JWT claims, policy rules |
| Artifacts Produced | ID token, session cookie, authenticated principal | Allow/deny decision, enforced permissions, filtered data responses |
| Failure Mode | Invalid credentials → no identity established | Insufficient permissions → identity valid but access denied |
| Protocol Interaction | OIDC, SAML, MFA flows, cryptographic challenges | OAuth scopes, policy languages (e.g., Cedar, Rego), entitlement APIs |
| Position in Flow | Always occurs first | Always evaluated after AuthN, often at every request |
This division of responsibilities is intentional: authentication produces the identity context, and authorization consumes that context to determine access rights. In distributed architectures, especially API-driven or microservice environments, these responsibilities are often handled by separate components to maintain clarity and enforce least privilege at scale.
How Authentication and Authorization Work Together in Identity Flows
While authentication and authorization serve different purposes, they function as tightly connected stages in a modern access workflow. Authentication establishes the identity context, and authorization consumes that context to determine whether a user, device, or service is permitted to access a specific resource. The two processes are sequential, interdependent, and critical for enforcing Zero Trust principles.
A typical identity flow looks like this:
Step 1: Credential Submission (Authentication Trigger)
A user or client presents credentials to the identity provider (IdP). Depending on the assurance requirements, this may involve:
-
Passwords or passkeys
-
One-time codes
-
Device-bound cryptographic assertions
-
Biometrics
-
Certificate-based authentication
At this stage, no access decisions are made. The system is only attempting to verify identity.
Step 2: Identity Validation by the IdP
The IdP evaluates the submitted factors against trusted sources such as identity stores, public key sets, device registries, or MFA services. If validated, the IdP generates an authenticated identity represented by:
-
ID tokens (OIDC)
-
SAML assertions
-
Session cookies
-
JWTs containing identity claims
This is the handoff between authentication and authorization.
Step 3: Token or Session Exchange with the Application
The authenticated identity is passed to the application or API gateway. At this point, no permissions have been evaluated yet. The system only knows who the user is and what identity attributes they carry.
Step 4: Authorization Evaluation (Policy Decision)
The authorization layer processes the identity context through policy engines or access control logic. This may include:
-
RBAC checks: user roles mapped to permitted actions
-
ABAC evaluation: attributes such as department, location, device trust level
-
Policy-based enforcement: Rego, Cedar, or custom rules
-
OAuth scope or claim checks: validating what operations the token allows
This stage produces the actual allow/deny decision and often determines the exact resources, methods, or fields the user can interact with.
Step 5: Enforcement by the Resource Server
Once authorization provides a decision, the resource server or API gateway enforces it. This may include:
-
Allowing or rejecting the request
-
Filtering data based on permissions
-
Escalating to additional challenges (step-up authentication)
-
Logging access outcomes for audit
Step 6: Continuous Evaluation (Zero Trust)
In Zero Trust architectures, authorization is not a one-time event. Each request can trigger ongoing policy checks using dynamic signals such as risk level, device state, session age, or anomaly detection.
Authentication vs Authorization in API Security
API environments make the distinction between authentication and authorization particularly important. Every API request must establish who the caller is and what level of access that caller should have. This separation allows distributed systems, microservices, and third-party integrations to operate securely at scale.
API Authentication: Identifying the Caller
API authentication focuses on validating the entity behind a request, whether it’s an end user, a backend service, or a partner application. Common approaches include:
-
API keys for simple server-to-server identification
-
OAuth 2.0 client authentication using client IDs and secrets
-
JWTs that carry signed identity claims
-
mTLS to authenticate both client and server using certificates
Once authentication succeeds, the system has an identity context it can rely on for subsequent decisions.
API Authorization: Enforcing Access Based on Context
Authorization determines what operations the authenticated entity is permitted to perform. In API architectures, this typically involves:
-
OAuth scopes that define allowed operations
-
JWT claims such as roles, privilege levels, or tenant identifiers
-
Attribute-based policies evaluating factors like device, location, or request type
-
Route- and method-level rules set within the API gateway
This step ensures that callers interact only with the resources and operations aligned with their assigned permissions.
Coordinating AuthN and AuthZ at the Gateway
API gateways commonly handle both authentication and authorization because they sit at the entry point of the system. A typical gateway workflow includes:
-
Validating tokens or certificates to authenticate the caller
-
Evaluating scopes, claims, and policies to authorize the requested action
-
Forwarding the request to backend services with a validated identity context
This approach creates consistent enforcement and removes the burden of identity logic from individual microservices.
Common API Vulnerabilities When AuthZ Falls Short
Most API security issues arise when authorization is incomplete or inconsistently implemented. Examples include:
-
IDOR caused by missing resource-level checks
-
Privilege escalation due to trusted but unverified JWT claims
-
Overly broad scopes that grant more access than intended
-
Weak tenant isolation in multi-tenant applications
These patterns illustrate why both authentication and authorization must be deliberately designed and continuously enforced across API ecosystems.
Common Authorization Models (RBAC, ABAC, PBAC, ReBAC)
Authorization models define how a system interprets identity context and converts it into access decisions. The model you choose affects scalability, administrative overhead, and your ability to support complex user journeys across consumer, workforce, and partner ecosystems.
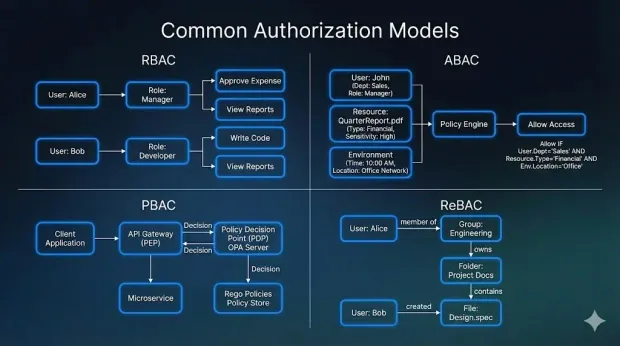
Below is a deeper look at four widely adopted models and the scenarios where they excel.
1. Role-Based Access Control (RBAC)
RBAC assigns permissions based on predefined roles. Users receive capabilities by being mapped to one or more roles, and each role carries associated privileges.
Strengths:
-
Straightforward permission management: Administrators assign capabilities once per role instead of managing user-level permissions.
-
Predictable access patterns: Works well when access does not change frequently or dynamically.
-
Efficient for hierarchical structures: Organizations with clearly defined job functions benefit from RBAC’s simplicity.
Common Uses:
-
Internal tools with defined operational roles
-
Administrative dashboards
-
Multi-tier systems that separate read-only, editor, and admin access
Also read: How to Implement RBAC Using LoginRadius CIAM
2. Attribute-Based Access Control (ABAC)
ABAC evaluates requests based on a combination of attributes, including user attributes (role, department), resource attributes (sensitivity), and environmental conditions (location, device, time).
Strengths:
-
Fine-grained control: Decisions factor in more than just roles, enabling tailored access based on user or resource characteristics.
-
Context-aware enforcement: Access can adapt based on risk signals, device posture, or real-time conditions.
-
Dynamic scalability: As applications grow or diversify their user base, ABAC rules can evolve without restructuring role hierarchies.
Common Uses:
-
Large enterprises with complex access policies
-
Organizations implementing adaptive or risk-based access
-
Multi-tenant applications requiring tenant-specific or resource-specific rules
For a detailed comparison between models, see our RBAC vs ABAC guide.
3. Policy-Based Access Control (PBAC)
PBAC centralizes authorization decisions in formal policies evaluated by dedicated engines. Instead of binding permissions to users or roles, administrators define policies that declare what *is *and is not allowed under specific conditions.
Strengths:
-
Highly expressive logic: Policies can represent complex conditions that exceed the capabilities of basic RBAC or ABAC.
-
Consistent authorization across services: Central policy engines ensure uniform enforcement across microservices, APIs, and gateways.
-
Well-suited to Zero Trust: Continuous evaluation of policy decisions aligns with modern security architectures.
Common Uses:
-
API-driven and microservice-based environments
-
System architectures using service meshes or API gateways
-
Zero Trust implementations that require ongoing, context-driven decisions
How It Works:
PBAC engines, like OPA (Rego) or Cedar evaluate identity context, request parameters, and resource attributes against structured policy sets before generating an allow/deny decision.
4. Relationship-Based Access Control (ReBAC)
ReBAC models access using the relationships between users, groups, and resources. Access decisions reflect how entities are connected rather than which roles they hold.
Strengths:
-
Natural fit for graph-like user interactions: Many real-world authorization scenarios reflect relationships (ownership, sharing, delegation), not fixed roles.
-
Flexible permission delegation: Users can grant access to collaborators without involving administrators.
-
Supports nested or hierarchical ecosystems: Ideal for B2B partner networks or complex organizational structures.
Common Uses:
-
Collaboration platforms where resources are shared across user groups
-
Social applications where relationships define visibility
-
Enterprise and partner ecosystems with multi-level organizational structures
Many organizations combine these models. For example, RBAC may define baseline access while ABAC or PBAC applies conditional rules for sensitive actions. The right approach depends on your application's complexity, user diversity, and compliance requirements.
Real-World Examples: Authentication vs Authorization in Action
The distinction between authentication and authorization becomes easier to understand when applied to real environments. Below are scenarios that reflect how modern applications enforce identity verification and access control across different industries and architectures.
Example 1: Online Banking Application
Authentication:
A customer signs in using a username and password, followed by a one-time passcode delivered via SMS or authenticator app. The bank’s identity provider validates these factors and establishes the user’s identity.
Authorization:
Once authenticated, the customer can view account balances, download statements, or schedule transfers. However, high-risk actions, such as adding a new payee or initiating a large transaction, may trigger additional authorization checks or step-up authentication.
This ensures that permissions align with risk and regulatory requirements.
Example 2: Multi-Tenant SaaS Platform
Authentication:
Business customers log in via SSO using their corporate IdP (e.g., Azure AD or Okta). The platform receives a signed token representing the authenticated employee.
Authorization:
The system evaluates tenant identifiers, roles, and claims from the token to control access. For example:
-
A “Manager” may access all project records for their department.
-
A “Contributor” may only update resources they own.
-
Tenant boundaries ensure that no user can view data from another customer organization.
Authorization ensures data isolation and granular capability mapping across tenants.
Example 3: B2B Partner Portal
Authentication:
Partners authenticate using federated SSO or a dedicated login. The system verifies the partner’s identity and associates them with their organization.
Authorization:
Access to shared resources depends on partner-specific policies. For instance:
-
A franchise manager may view performance reports for their locations.
-
A regional administrator may access multiple franchises.
-
Certain actions, like approving workflows or accessing sensitive financial data, are limited to predefined organizational roles.
In this context, authorization governs access across an ecosystem with multiple organizational tiers.
Example 4: API-Driven Microservices Architecture
Authentication:
A microservice receives a request bearing a JWT issued by the API gateway. The token contains signed identity claims representing either an end user or another service. The service validates the token signature to authenticate the caller.
Authorization:
The microservice inspects scopes or claims to determine whether the caller can perform the requested action. For example:
-
The token may allow
read:ordersbut notwrite:orders. -
A service account may be limited to specific internal APIs.
-
Sensitive data fields may be filtered based on permission levels.
Authorization ensures that granular access rules are upheld at each microservice boundary.
Example 5: Enterprise Admin Console
Authentication:
Administrators authenticate using MFA and device trust checks. The IdP validates their identity and establishes an authenticated session.
Authorization:
Not all admins have the same privileges. The console applies role- and attribute-based rules to determine who can:
-
Manage user accounts
-
Configure security policies
-
View audit logs
-
Integrate external identity providers
This prevents over-privileged access and aligns administrative capabilities with organizational responsibilities.
Across these scenarios, the separation between authentication and authorization becomes clear: authentication confirms identity, and authorization governs what that identity can access. Each system relies on both processes to enforce least privilege, maintain data integrity, and support secure user experiences.
Why Authentication Always Comes Before Authorization
Authentication and authorization are often discussed together, but their order in an access flow is not interchangeable. Modern identity systems, whether they support web applications, APIs, mobile apps, or distributed services, depend on authentication occurring first because authorization requires a validated identity to evaluate.
In practice, authorization has nothing to act on without the identity context established by authentication.
Identity Must Be Established Before Any Policy Can Be Applied
Authorization engines rely on attributes derived from the authenticated identity, like roles, group memberships, tenant identifiers, risk scores, device context, and other claims. These attributes are only available once authentication has confirmed who the entity is. Without this foundation:
-
No roles can be resolved
-
No policies can be evaluated
-
No scopes or claims can be trusted
-
No resource-level filtering can be applied
Every decision in authorization depends on authenticating the caller first.
Token-Based Architectures Reinforce This Sequence
In OAuth 2.0 and OpenID Connect, the sequence is explicit:
-
Authenticate the user or client
-
Issue a token representing that identity
-
Authorize the request based on scopes, roles, or claims in the token
The token itself is the bridge linking authentication outputs with authorization inputs.
API gateways, service meshes, and microservices all rely on this order because downstream components expect a validated token to evaluate permissions reliably.
Security Risks When the Order Is Reversed
If authorization logic is applied before authentication, systems risk making access decisions based on unverified or spoofed information. This can lead to:
-
Trusting unvalidated claims in forged tokens
-
Allowing anonymous access to privileged endpoints
-
Inconsistent enforcement across distributed services
-
Privilege escalation due to missing identity context
Reversing the sequence breaks the principle of identity-first access control and invites avoidable vulnerabilities.
Supporting Zero Trust and Continuous Evaluation
Zero Trust architectures strengthen, but do not alter the sequence. Authentication still establishes identity first, but authorization is re-evaluated continuously based on dynamic conditions such as device health, request patterns, or session age. Even in continuous verification models, identity remains the anchor point.
Authentication provides the assurance needed to trust the identity behind a request. Authorization then determines what that trusted identity is allowed to do. That dependency is why authentication always precedes authorization in every secure access flow.
Also read: Implementing Zero Trust? Make Sure You're Doing It Correctly
Best Practices for Strong Authentication and Authorization
Effective identity security requires treating authentication and authorization as distinct but complementary controls. The following best practices help maintain this balance across applications, APIs, and distributed services.
Strengthen Authentication with Modern Identity Assurance
-
Use multi-factor authentication (MFA): Combining knowledge, possession, or inherence factors significantly reduces the risk of credential-based attacks.
-
Adopt passwordless and phishing-resistant methods where possible: Passkeys, WebAuthn, and device-bound cryptographic assertions provide stronger protection than traditional passwords.
-
Enforce step-up authentication for sensitive actions: High-risk operations, such as changing credentials or accessing regulated data, should require additional verification.
-
Validate device and session context: Signals like device trust level, IP reputation, and session age contribute to the overall assurance level of each request.
Apply Authorization Principles Consistently Across the Stack
-
Follow least privilege as a baseline: Users and services should only receive the minimum permissions required to perform intended tasks.
-
Use structured authorization models: RBAC, ABAC, PBAC, and ReBAC provide clear frameworks for organizing permissions, reducing ad hoc decision-making.
-
Enforce authorization at multiple layers: In distributed systems, authorization should be validated at the API gateway, internal services, and resource endpoints.
-
Implement continuous access evaluation: Modern architectures benefit from re-assessing authorization on each request, especially when context or risk changes.
Build Secure API Interactions Through Token Governance
-
Validate tokens on every request: Signatures, issuers, audiences, scopes, and expiry times must be verified consistently.
-
Align scopes and claims with actual business operations: Overly broad scopes or claims introduce privilege escalation risks.
-
Rotate keys and secrets regularly: Key rotation helps prevent long-term exposure in the event of compromise.
-
Use short-lived access tokens: Reducing token lifetime limits the window of opportunity for attackers.
Maintain Centralized Policy Governance
-
Adopt a unified policy engine or framework: Centralizing authorization logic reduces inconsistencies across microservices.
-
Version policies and track changes: Visibility and control over policy evolution support audit, compliance, and incident response.
-
Regularly test for authorization gaps: Authorization testing helps identify missing checks, broken access control, and resource-level vulnerabilities.
Together, these best practices help ensure that identity verification remains strong and that access decisions remain accurate, consistent, and aligned with operational requirements. Organizations with well-structured authentication and authorization pipelines are better positioned to support scalable, secure digital experiences.
How LoginRadius Supports Authentication and Authorization in CIAM
LoginRadius provides a CIAM platform designed to help organizations implement consistent, secure authentication and authorization across consumer applications, APIs, and partner ecosystems. The platform separates identity verification from access control, allowing each to be applied with the appropriate level of assurance and governance.
Authentication Through a Centralized Identity Layer
LoginRadius supports modern authentication methods that help establish a trusted identity before any access evaluation occurs. Depending on the implementation, organizations can leverage:
-
Standard authentication flows such as username/password
-
Multi-factor authentication (MFA) for additional assurance
-
Passwordless options, including one-time passcodes
-
Social login providers for streamlined consumer authentication
-
OAuth 2.0 and OpenID Connect–based identity workflows
-
Token-based authentication aligned with industry best practices
These capabilities ensure that applications begin each session with a validated and reliable identity context.
Authorization Through Structured Roles and Permissions
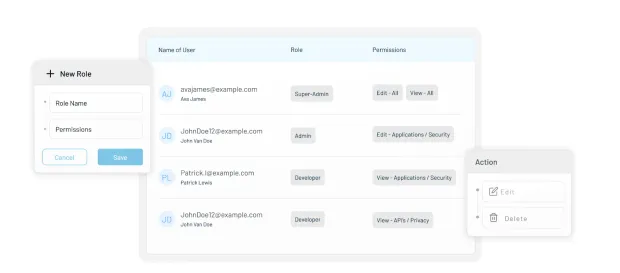
Once authentication is complete, LoginRadius allows organizations to assign and enforce access through role-based authorization. Using Roles and Permissions, teams can:
-
Create roles aligned with business functions
-
Assign permissions to those roles at a granular level
-
Apply role mappings to users or groups
-
Manage access across consumer, internal, or partner-facing applications
This approach provides clear, maintainable authorization policies without embedding access logic directly into applications.
Support for Complex Access Scenarios Through RBAC and Policy Extensions
For environments that require more flexible access control, LoginRadius supports RBAC as a foundational model and can be paired with external policy engines or application-level authorization logic. This allows organizations to implement:
-
Context-aware authorization decisions
-
Multi-tenant permission boundaries
-
Tiered administrative access
-
Resource-level access restrictions handled at the application or API layer
LoginRadius provides the identity and claims foundation that policy engines and downstream services rely on.
CIAM-Centric Integration Across Applications and APIs
LoginRadius integrates authentication and authorization signals into API and application workflows through:
-
OAuth 2.0 and OIDC tokens carrying identity claims
-
JWT-based access representations following recommended best practices
-
Standard endpoints and SDKs that pass validated identity context to backend systems
These components help organizations maintain consistent enforcement of identity-driven access decisions across distributed environments.
LoginRadius’ authentication and authorization capabilities give teams a structured way to verify identities, apply role-based access, and maintain predictable control across consumer and partner-facing applications, without introducing unnecessary complexity or dependencies.
Looking Ahead
As digital ecosystems continue to expand across applications, APIs, microservices, and partner networks, the distinction between authentication and authorization becomes even more important. Authentication provides the identity foundation for every interaction, while authorization ensures access decisions remain accurate and aligned with evolving business requirements.
Looking ahead, organizations will need identity systems that can adapt to shifting user expectations, emerging threat patterns, and increasingly distributed architectures. This means adopting authentication methods that strengthen identity assurance, and authorization models that can scale from simple role assignments to more dynamic, policy-driven access decisions.
By approaching authentication and authorization as complementary, independently governed layers, teams are better equipped to support Zero Trust initiatives, enforce consistent access across channels, and manage growing volumes of user identity data. As CIAM architectures mature, the organizations that succeed will be those that ensure identity verification and access control evolve together, with clarity, precision, and a continuous focus on user security and experience.
FAQs
1. What is the difference between authentication and authorization?
Authentication verifies a user’s identity, while authorization determines the actions and resources that identity is allowed to access. Authentication comes first to establish identity; authorization follows to enforce permissions.
2. How does authentication work in modern identity flows?
Authentication works by validating credentials or identity factors, such as passwords, biometrics, or tokens against trusted records. Once verified, the system issues a session or token that represents the authenticated identity.
3. What does authorization evaluate after a user is authenticated?
Authorization evaluates roles, attributes, scopes, and policy rules to determine whether the authenticated identity has the required permissions to access a specific resource or perform an action.
4. Why must authentication come before authorization in any access workflow?
Authentication must come first because authorization depends on identity context. Without a verified identity, policy engines cannot resolve roles, evaluate claims, or apply access rules securely.
5. How do authentication and authorization work together in a single identity flow?
Authentication establishes who the caller is, and authorization consumes that identity context to make an access decision. The workflow moves from identity verification to policy evaluation before the resource is accessed.
6. What is the role of authentication vs authorization in API security?
In API security, authentication validates the caller (user or service) using tokens, credentials, or certificates. Authorization then checks scopes, claims, and policies to determine what operations that caller can perform on the API.
7. Which authorization models are commonly used in CIAM?
Four common models include RBAC (role-based), ABAC (attribute-based), PBAC (policy-based), and ReBAC (relationship-based). Each model defines how permissions are structured and evaluated in different application architectures.
8. How do real-world applications separate authentication from authorization?
Applications authenticate users through credentials or MFA, then apply authorization rules, like roles, scopes, or policies to limit which data or actions are available. This separation prevents over-privileged access and maintains least privilege.
9. What best practices improve authentication and authorization security?
Best practices include enforcing MFA, validating tokens on every request, implementing least privilege, centralizing policy management, and using structured models like RBAC or ABAC for predictable access control.
10. How does LoginRadius support authentication and authorization for CIAM?
LoginRadius supports authentication through standard and MFA-based login flows and supports authorization through role-based access controls, permissions management, and identity claims used by downstream policy engines.



