Introduction
Access control design is one of those things teams believe they’ve handled until something breaks.
A customer sees data they shouldn’t. An internal tool gets locked down so tightly that teams bypass it entirely. A security review surfaces hundreds of permissions no one remembers creating. None of this happens because RBAC is flawed. It happens because RBAC is often treated like a configuration task instead of a design problem.
Most systems don’t fail at authentication. They fail at authorization. They fail quietly, over time, as roles pile up, permissions get reused for convenience, and exceptions become permanent. What started as a clean RBAC system slowly turns into an access maze that no one wants to touch.
This is why access control design deserves far more attention than it usually gets.
Designing an effective RBAC system isn’t about creating a long list of roles. It’s about understanding how actions flow through your application, how responsibilities evolve, and how access should change as your product grows. It’s about building something that both beginners can reason about and experts can extend without fear.
In this blog, we’ll look at RBAC from the inside out starting with permissions, shaping roles deliberately, grounding decisions in real-world rbac model examples, and designing an access control system that stays understandable under pressure. Whether you’re building your first RBAC system or redesigning one that’s already showing cracks, the goal is the same: clarity that lasts.
Why RBAC Still Matters in Modern Access Control Design
RBAC is still widely used not because it’s trendy, but because it solves a very human problem: clarity.
Most organizations don’t think in attributes, policies, or runtime conditions. They think in responsibilities. Who is allowed to approve this? Who can change that setting? Who should never see this data? RBAC aligns naturally with those questions, which is why it remains central to modern access control design, even as systems grow more complex.
What’s changed is the environment RBAC operates in. Applications are no longer single systems with a handful of users. They’re multi-tenant platforms, distributed services, partner ecosystems, and admin consoles layered on top of each other. In that complexity, RBAC provides something increasingly valuable: a stable, understandable baseline for authorization decisions.
That stability matters. When access logic becomes too dynamic or implicit, teams lose the ability to reason about permissions. Debugging turns into guesswork. Audits become painful. RBAC anchors authorization in some concrete roles tied to explicit permissions so teams can explain, review, and change access with confidence.
RBAC still matters because systems still need a clear answer to a simple question: what is this user allowed to do right now, and why? When designed well, RBAC answers that without ambiguity.

Start With Permissions, Not Roles
Starting RBAC design with roles feels intuitive. It’s also one of the most common mistakes teams make.
Roles are abstractions. Permissions are reality.
If you define roles first, you’re guessing. You’re assuming you already understand every action your system supports and every boundary that matters. In practice, that understanding usually comes later after features expand, edge cases appear, and security reviews ask uncomfortable questions.
Strong user roles and permissions design begins by cataloging actions. What can actually happen in the system? What data can be read? What can be modified? What actions are irreversible or sensitive? These questions force clarity early, before shortcuts creep in.
Permissions should be small, specific, and composable. A permission that means “manage everything” is rarely helpful. It hides risk and encourages overuse. Clear permissions make intent visible, which is essential for audits, debugging, and future redesigns.
Once permissions are explicit, roles stop being guesses. They become deliberate groupings of actions that make sense together. That shift from role-first to permission-first is what separates RBAC that survives growth from RBAC that collapses under it.
Turning Permissions Into Roles Without Creating Chaos
After permissions are defined, the temptation is to create many highly specific roles. This is where RBAC often starts to unravel.
Role explosion doesn’t happen overnight. It happens when teams respond to every edge case with a new role instead of questioning the structure underneath. Over time, roles overlap, differ by one permission, and become impossible to reason about.
Effective rbac system design treats roles as stable interfaces, not disposable configurations.
Good roles represent responsibilities, not exceptions. They describe what someone is broadly accountable for, not every possible variation of access. When a role starts to accumulate “just one more permission,” it’s usually a signal that scope or hierarchy should be adjusted instead.
Another pattern that keeps roles manageable is separating what someone can do from where they can do it. Scope such as project, workspace, or organization often explains differences better than creating new roles. This keeps the role set small while still supporting complex access needs.
When roles stay few and intentional, RBAC remains readable. When roles multiply unchecked, even experts stop trusting the system.
Choosing the Right RBAC Model (Without Overengineering)
RBAC isn’t a single rigid structure. It’s a family of models, each solving slightly different problems. The mistake teams make isn’t choosing the “wrong” model, it's choosing a complex one too early.
For many systems, a simple core RBAC model is enough. Users are assigned roles. Roles grant permissions. Access decisions are clear and predictable. This simplicity is a feature, not a limitation.
As systems grow, hierarchy often becomes useful. Senior roles inheriting permissions from base roles reduce duplication and make access reviews easier. Instead of redefining permissions repeatedly, teams build on existing structures.
In higher-risk environments, constraints matter. Separation of duties prevents conflicting responsibilities from being held by the same role. These constraints add safety without fundamentally changing how RBAC works.
A practical rbac model example doesn’t aim for theoretical completeness. It aims for clarity. The right model is the one that solves today’s problems cleanly while leaving room to extend later. Overengineering RBAC upfront usually leads to confusion, not security.
RBAC works best when it grows alongside the system it protects—not when it tries to predict everything in advance.
A Practical Role-Based Access Control Example
Most RBAC explanations fall apart at the example stage. They either oversimplify or quietly ignore the hard parts.
So let’s use a scenario that actually mirrors how modern systems work: a multi-tenant SaaS platform with admin and business users.
Start by identifying resources. These aren’t abstract concepts, they’re real objects in your system. Think workspaces, users, billing records, reports, API keys. Next, define actions against those resources. Read, create, update, delete, invite, approve. Clear verbs, clear intent.
From there, roles emerge naturally.
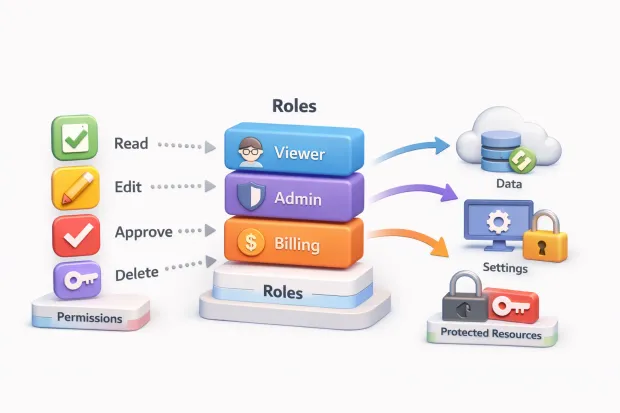
A Workspace Viewer can read data but change nothing. A Workspace Admin can manage users and settings inside a single workspace. A Billing Admin can view invoices and update payment methods but has no visibility into user management or product configuration.
This role-based access control example works because every role has a clean boundary. There’s no “almost admin” role and no “temporary exception” baked in. Access is predictable. Reviews are straightforward. Debugging doesn’t require tribal knowledge.
Good RBAC examples aren’t clever. They’re boring and that’s exactly why they scale.
RBAC Database Design That Scales Cleanly
RBAC doesn’t live in diagrams. It lives in tables.
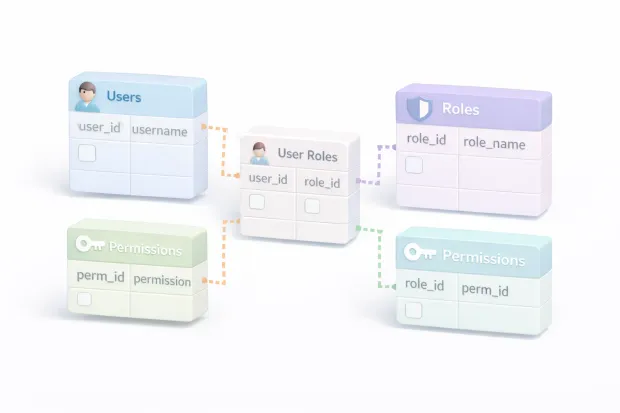
A scalable rbac database design starts with explicit relationships. Users are not granted permissions directly. They’re assigned roles. Roles grant permissions. Those connections are stored in junction tables, not hidden in application logic.
This structure matters more than it seems. It allows you to answer important questions without writing custom code. Who has access to this permission? Which roles grant this capability? What changes when a role is updated?
As soon as you introduce multiple organizations or workspaces, scope becomes critical. The same user may hold different roles in different contexts. Encoding scope directly into role assignments keeps the model flexible without multiplying roles.
Auditability is another reason database design matters. When access changes, you need to know when it happened and why. Systems that skip this early often struggle later when compliance or incident response enters the picture.
A clean RBAC schema doesn’t try to be clever. It stays explicit, readable, and easy to reason about especially when the system is under stress.
Enforcement Is Where RBAC Becomes Real
Designing roles and permissions is only half the story. Enforcement is where RBAC either proves its value or quietly breaks.
In many systems, access checks are scattered across controllers, services, and UI logic. This makes behavior inconsistent and hard to test. A permission might be enforced in one place but missed in another.
Effective access control design centralizes enforcement. Access decisions flow through a consistent layer middleware, policy engine, or authorization service where rules are applied uniformly. This creates predictability, which is essential for both security and developer confidence.
Caching improves performance, but it must be handled carefully. When roles or permissions change, enforcement should reflect that change quickly. Stale access is a subtle risk because it feels like nothing is wrong until it is.
RBAC becomes real at runtime. If enforcement is weak, the best-designed model won’t save you.
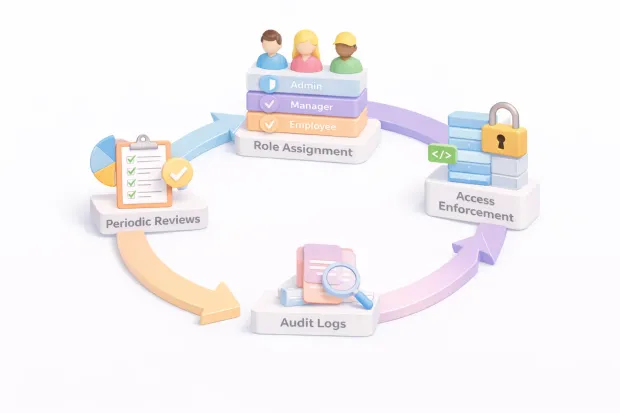
Governance: The Part Everyone Skips (Until They Can’t)
RBAC systems don’t fail because they’re poorly designed. They fail because they’re never revisited.
Over time, users change roles, teams reorganize, and temporary access becomes permanent. Without governance, privilege creeps in quietly. Suddenly, no one is confident enough to remove access, because no one remembers why it was granted.
Governance brings discipline back into access control design. Roles have owners. Permissions are reviewed periodically. Access changes are logged and traceable. High-risk roles require explicit approval.
This isn’t about bureaucracy. It’s about keeping RBAC trustworthy. When teams trust the system, they use it properly. When they don’t, they work around it and that’s when security erodes.
Governance turns RBAC from a static configuration into a living system that stays aligned with reality.
When RBAC Isn’t Enough on Its Own
RBAC answers a foundational question: what is this user allowed to do? But modern systems often need to ask more.
Is the request coming from a trusted device? Is the user logging in from an unusual location? Is this action high risk right now?
This is where RBAC reaches its natural limits. It isn’t designed to evaluate context. It’s designed to define responsibility.
The mistake teams make is abandoning RBAC entirely instead of extending it. In practice, RBAC works best as a stable core, with contextual signals layered on top. Roles define baseline access. Context refines decisions at runtime.
When RBAC is treated this way, it remains readable and governable while still supporting dynamic security needs. It doesn’t compete with newer models, it complements them.
RBAC doesn’t need to do everything. It just needs to do its part well.
Conclusion
A well-designed RBAC system doesn’t draw attention to itself. It quietly does its job—granting the right access, blocking the wrong actions, and staying out of the way of everyday work.
That’s the real benchmark of effective access control design.
When permissions are clearly defined, roles remain stable. When roles are stable, audits become easier. When audits are easy, teams stop being afraid to remove access. And when access can be safely removed, security improves without slowing anyone down.
The most successful RBAC implementations share a common trait: they prioritize understanding over cleverness. They resist role explosion. They treat user roles and permissions design as a living structure, not a one-time setup. They invest in clean rbac database design and centralized enforcement so future changes don’t feel risky.
RBAC doesn’t need to be perfect on day one. It needs to be intentional. Designed with growth in mind. Built so that six months or three years from now, someone new can look at it and say, “Yes, this still makes sense.”
That’s when RBAC stops being just an authorization mechanism and becomes a foundation. One that supports scale, security, and trust without constantly getting in the way.
Design it once. Design it thoughtfully. And let it evolve, instead of unravel. Book a Demo
FAQs
Q: What is RBAC in access control design?
A: RBAC (Role-Based Access Control) is a method of managing access by assigning permissions to roles instead of individual users. It simplifies access control design by making permissions easier to review, audit, and manage as systems grow.
Q: When should you use RBAC instead of other access control models?
A: RBAC works best when access is tied to clear responsibilities, such as admin, manager, or support roles. It’s especially effective in SaaS, enterprise, and multi-user systems where clarity and governance matter more than dynamic conditions.
Q: What causes RBAC systems to become hard to manage?
A: RBAC breaks down when roles are created before permissions, leading to role explosion and overlapping access. Lack of regular reviews and unclear role ownership also contribute to permission sprawl over time.
Q: Can RBAC scale for large or multi-tenant systems?
A: Yes, when designed with scoped role assignments and a clean RBAC database design. Keeping roles stable and permissions explicit allows RBAC to scale without becoming fragile or confusing.


