Introduction
In an age where our lives are deeply intertwined with digital platforms from banking apps and eCommerce sites to workplace tools and streaming services, security has quietly become the invisible backbone of every online interaction. Yet, behind every “Login” button lies a sophisticated process designed not just to protect data but to build digital trust. This foundation rests on two essential pillars: authentication and authorization.
If you’ve ever searched what is authentication and authorization, you’ve likely noticed people treat them like the same thing. They aren’t. The difference between authentication and authorization matters because each one protects a different part of your system. Think of it like authorization vs authentication (or authentication vs authorization) as two sequential gates: first you prove who you are, then the system decides what you can do.
These terms are often used together, and sometimes even interchangeably, but they serve distinct and critical purposes in modern cybersecurity. Authentication focuses on confirming who the user is, while authorization decides what that user is allowed to do once their identity has been verified. Both processes work hand in hand to ensure that systems remain secure, user experiences remain seamless, and organizations maintain control over sensitive resources.
Understanding how authentication and authorization work together is key to protecting both users and enterprises. It’s not just a technical concept; it’s a strategic layer of defense that determines whether a system is merely functional or truly secure.
In this blog, we’ll dive deep into what these two terms mean, how they differ, and why mastering both is essential for building trustworthy, compliant, and user-centric digital ecosystems.
What Is Authentication?

At its core, authentication is about trust, confirming that the person, device, or system trying to access a digital service is truly who they claim to be. It’s the first and most crucial step in securing any online environment. Without authentication, there’s no way to distinguish between a legitimate user and a potential attacker, leaving sensitive information and digital assets vulnerable to exploitation.
In simple terms, authentication answers one question: “Who are you?” When a user attempts to log in, the system asks for proof of identity, often in the form of credentials. These credentials could be a password, a security token, a biometric scan, or a one-time code sent to a verified device. The system then cross-verifies this information with stored data. If the two match, access is granted; if not, it’s denied.
To make it even clearer, how does authentication work in practice? A system typically
-
collects identity proof (credentials or factors),
-
validates it against a trusted identity store or identity provider, and
-
issues a session or token that represents the verified identity.
That token (or session) becomes the “proof” used across the app or API layer to continue the user journey securely.
But authentication today goes far beyond entering a password. The evolution of digital threats has pushed organizations to adopt stronger, layered authentication systems that go beyond static credentials.
Let’s look at the most common types:

1. Single-Factor Authentication (SFA):
This is the most basic form, typically a username and password combination. While easy to use, it offers limited security, as stolen or weak passwords can easily be exploited.
2. Two-Factor Authentication (2FA):
This method adds another layer, combining something you know (like a password) with something you have (like a mobile verification code). It’s a significant step up in security and helps prevent unauthorized logins even if passwords are compromised.
3. Multi-Factor Authentication (MFA):
MFA expands this further by adding multiple layers, such as biometrics (fingerprint or facial recognition), a one-time token, or a hardware key. It’s widely considered the gold standard for securing user identity because it makes unauthorized access exponentially more difficult.

4. Passwordless Authentication
The future of secure access. Instead of relying on passwords, users verify their identities through biometrics, device-based cryptographic keys (like passkeys), or secure login links. This method eliminates the risk of password theft altogether.
Beyond preventing unauthorized access, authentication also plays a crucial role in personalizing user experiences. Once a system identifies who the user is, it can tailor interfaces, preferences, and data access based on past behavior, creating a seamless and consistent experience across devices.
Also read : Beyond Passwords: Navigating Tomorrow's Authentication Landscape
In essence, authentication is more than a security gate; it’s the handshake that builds digital trust. However, verifying identity alone isn’t enough. Once the system knows who you are, it must determine what you’re allowed to do within its boundaries. That’s where authorization steps in.
What Is Authorization?
Once a user’s identity has been verified through authentication, the next question a system must answer is: “What can this user do?” That’s where authorization comes into play.
If authentication is about verifying who you are, authorization is about defining what you’re allowed to access. It governs the actions, data, and resources that each user can interact with within a system. In other words, authorization ensures that users, even those who are authenticated, operate strictly within the limits of their assigned privileges.
This is also why authorization in cyber security is treated as a core control, not an optional feature. Many breaches don’t happen because authentication failed; they happen because someone got in and then had more access than they should have.
In digital systems, this same principle applies. After you’ve logged in, authorization decides whether you can view, edit, delete, or manage specific data. This fine-grained control helps organizations:
-
Protect sensitive information from internal misuse or data leaks.
-
Maintain compliance with security standards like GDPR, HIPAA, and SOC 2.
-
Prevent privilege abuse, where users with unnecessary permissions could accidentally or maliciously alter data.
To achieve this, organizations use well-defined authorization models, each catering to different levels of control and flexibility:
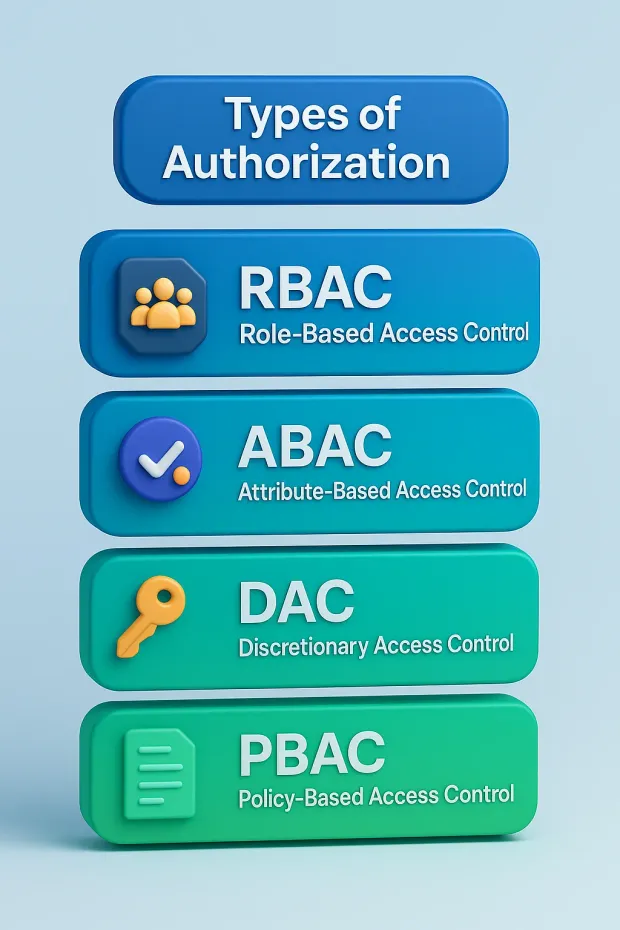
1. Role-Based Access Control (RBAC):
Permissions are assigned based on a user’s role within the organization. For example, a “Manager” might have access to performance reports that a “Team Member” does not. RBAC is widely used because it’s structured, easy to manage, and aligns with organizational hierarchies.
2. Attribute-Based Access Control (ABAC):
Access decisions are made based on attributes such as location, department, device, or time of login. It offers greater flexibility and context-awareness than RBAC.
3. Discretionary Access Control (DAC):
The data owner determines who can access their resources. While this model offers freedom and flexibility, it can become complex in large organizations with many users.
4. Policy-Based Access Control (PBAC):
A modern approach where access decisions are governed by policies and logical rules that evaluate multiple conditions in real-time, offering scalability for cloud and API-based environments.
By combining these models or adapting them based on their needs, organizations create dynamic access frameworks that balance security, flexibility, and usability.
Authorization is more than just permission management; it’s a safeguard against internal and external risks. Without it, even legitimate users could end up accessing data they shouldn’t, leading to compliance violations, data exposure, or system misuse.
Together, authentication and authorization form the backbone of secure access. But while they’re often mentioned side by side, their differences are what make them so effective when combined.
Let’s explore how these two work together and where they diverge.
Authentication vs. Authorization
Although authentication and authorization often work together, they serve two entirely different purposes within a security framework. Understanding their differences helps businesses design systems that not only keep intruders out but also ensure users stay within their rightful boundaries once inside.
In the simplest sense, authentication verifies identity, while authorization determines access. You can think of them as two sequential stages in a digital security journey: one answers “Who are you?” and the other answers “What can you do?”’
If you’re wondering how is authentication different from authorization, the simplest answer is: authentication proves identity; authorization enforces permissions. That’s the real-world difference between authentication and authorization, and it’s why authorization vs authentication is not an either/or decision you need both.
Here’s a clear breakdown of how they differ in function, sequence, and purpose:
| Aspect | Authentication | Authorization |
|---|---|---|
| Definition | The process of verifying a user’s identity. | The process of granting or restricting access to resources. |
| Purpose | Confirms that the user is who they claim to be. | Determines what the authenticated user is allowed to do. |
| Sequence | This always occurs before any access is granted. | This happens after authentication, once the identity is verified. |
| Involves | User credentials like passwords, biometrics, or tokens. | Permissions, policies, or access rules. |
| Outcome | Grants entry into the system. | Grants or denies specific privileges or actions. |
| Analogy | Showing your ID to enter a building. | Accessing the rooms or files you’re authorized for. |
Together, these two layers create a complete access management lifecycle. Authentication ensures that only legitimate users make it past the gate, while authorization ensures that those users operate within the right confines once inside. This combination is especially critical in modern, interconnected systems where users access multiple applications, databases, and APIs from a single login.
Without proper synchronization between authentication and authorization, even a verified user could unintentionally breach sensitive areas of a network.
Authentication and Authorization in APIs
API Authentication focuses on verifying who is making the API request, whether it’s a user, an application, or another service. Before granting any access, the system needs to confirm that the request comes from a trusted source. This can be done using several mechanisms:
-
API Keys: A unique key assigned to each client to identify them. It’s simple but lacks flexibility for fine-grained control.
-
OAuth 2.0: A widely adopted authorization framework that allows users to grant limited access to their data without sharing their credentials. For example, when you log into a new app using your Google account, OAuth is working behind the scenes.
-
JWT (JSON Web Tokens): Compact, digitally signed tokens used to verify identity securely across systems. JWTs are popular for stateless authentication because they eliminate the need for session storage.
-
OpenID Connect (OIDC): Built on top of OAuth 2.0, OIDC adds an extra layer for identity verification, confirming who the user is, not just whether they’re allowed access.
Once the API confirms the requester’s identity, authorization steps in to determine what level of access that requester has. This means deciding whether a verified entity can read, write, update, or delete data.
For example:
-
A customer-facing application might be authenticated through OAuth but authorized only to read customer profile data and not modify it.
-
A system administrator’s API token, on the other hand, might be authorized to read and write data, reflecting higher privileges.
Authorization in APIs is typically managed through scopes and permissions, which define what an authenticated user or system can do. Scopes can limit actions (like read-only access) or restrict access to specific resources (like one endpoint in an API instead of the entire system).
This dual-layer protection authentication, followed by authorization, ensures that every interaction between systems is both verified and controlled. It’s especially important in cloud-based ecosystems, where hundreds of microservices exchange data simultaneously.
Without strict API authentication and authorization, a single compromised endpoint could become an entry point for massive data breaches.
Why Both Are Critical for Modern Identity and Access Management
Individually, authentication and authorization serve different purposes, but their true strength lies in their synergy. Authentication establishes trust, while authorization governs control. Without authentication, systems wouldn’t know who the user is.
Without authorization, they wouldn’t know what that user is allowed to do. Combine the two, and you create a dynamic, layered defense that protects both user data and organizational assets.
Here’s why their relationship is indispensable in today’s environment:
1. Protection Against Unauthorized Access
Authentication ensures only verified users enter a system, while authorization restricts their actions within that system. This dual approach prevents both external attacks and internal misuse, minimizing security loopholes.
2. Compliance and Audit Readiness
Regulations like GDPR, HIPAA, and SOC 2 require strict access control and traceability. Proper authentication and authorization frameworks make it easier to demonstrate compliance, track user actions, and generate audit trails for accountability.
3. Enhanced User Experience
Strong security doesn’t have to mean friction. Modern solutions like Single Sign-On (SSO) and Passwordless Authentication simplify login processes while maintaining security integrity. Once authenticated, users can seamlessly move between applications without repeatedly verifying their identity, boosting productivity and satisfaction.
4. Scalable Security for Growing Businesses
As organizations expand, so do their users, roles, and access requirements. A strong authentication and authorization setup, especially when powered by a Customer Identity and Access Management (CIAM) platform, scales effortlessly to manage millions of users across multiple environments without compromising performance or safety.
5. Zero Trust and Adaptive Security
In a Zero Trust framework, no user or device is trusted by default, even if they’re inside the network. Every action requires continuous authentication and authorization checks. This adaptive approach, combined with behavioral analytics and device intelligence, ensures threats are detected and mitigated in real time.
Ultimately, authentication and authorization together create a holistic security fabric, one that balances user convenience with enterprise-grade protection. It’s this balance that defines successful digital transformation strategies today.
To make this work effectively, organizations must also adopt best practices that strengthen both layers, ensuring that security doesn’t hinder usability but rather enhances it.
Best Practices for Implementing Authentication and Authorization
Building a secure digital environment isn’t just about having authentication and authorization in place; it’s about implementing them effectively. As cyberattacks become more sophisticated, even a small configuration error or outdated policy can lead to major vulnerabilities. Following modern best practices ensures that your access control framework is both resilient and user-friendly.
Here are the key strategies organizations should adopt to make authentication and authorization airtight:
1. Implement Multi-Factor or Passwordless Authentication
Passwords alone are no longer enough. Weak or reused credentials remain one of the leading causes of breaches worldwide. Adding additional layers of security through Multi-Factor Authentication (MFA) significantly reduces this risk. MFA combines something you know (password), something you have (a mobile device or token), and something you are (biometrics).
Even better, many enterprises are now embracing passwordless authentication using biometrics, device-based passkeys, or security tokens to remove the risk of password theft altogether.
2. Adopt Secure Protocols like OAuth 2.0 and OpenID Connect
When connecting users across multiple apps or services, using trusted frameworks such as OAuth 2.0 (for authorization) and OpenID Connect (OIDC) (for authentication) is essential.
These standards ensure secure token-based communication between clients, servers, and identity providers, minimizing credential exposure while enhancing interoperability.
3. Define Clear Access Roles and Policies
Clarity in access control prevents privilege abuse and operational chaos. Implement structured authorization models such as:
-
Role-Based Access Control (RBAC) to assign permissions based on job roles.
-
Attribute-Based Access Control (ABAC) to grant access dynamically based on user or device attributes.
-
Policy-Based Access Control (PBAC) for modern, context-driven environments where rules and logic guide access decisions. The more precise your access definitions, the stronger your internal data governance.
4. Regularly Review and Revoke Access Rights
User roles evolve over time, and so should their access. Periodic audits ensure that employees or partners no longer in specific roles lose their privileges. This practice, known as access recertification, helps prevent insider threats and keeps systems aligned with the principle of least privilege.
5. Keep Systems Patched and Updated
Cybercriminals often exploit vulnerabilities in outdated software. Regularly updating authentication systems, libraries, and security patches ensures your environment remains protected against newly discovered threats.
6. Monitor and Log All Access Activities
Visibility is critical. Maintain detailed logs of authentication and authorization events of who accessed what, when, and from where. These logs support anomaly detection, incident response, and forensic investigations in case of a breach. Integrating them with a SIEM (Security Information and Event Management) system allows real-time alerting and threat analysis.
7. Integrate Authentication and Authorization with a CIAM Platform
For customer-facing applications, implementing a CIAM solution like LoginRadius centralizes and simplifies identity control. A CIAM platform allows seamless authentication, adaptive MFA, and fine-grained authorization across millions of users while maintaining compliance, scalability, and a frictionless user experience.
Incorporating these practices transforms authentication and authorization from simple checkpoints into dynamic defense mechanisms that adapt to user behavior and evolving threat landscapes.
With these foundations in place, the next step is to understand how these two processes, though distinct, work together to create a complete security ecosystem that balances protection and convenience.
How Authentication and Authorization Work Together in Real Life
While authentication and authorization are distinct, their true value emerges when they work together seamlessly, creating a security flow that’s both intelligent and effortless for the end user.
In fact, this combination defines how most modern digital experiences operate, whether it’s logging into your email, accessing cloud storage, or approving a payment on your banking app.
Let’s visualize this process through a relatable scenario.
Imagine you’re logging into your company’s internal dashboard:
1. Authentication kicks in first
You enter your credentials, perhaps your username, password, and a verification code from your phone. The system checks this data against its records to confirm that it’s really you. This step verifies your identity.
2. Authorization follows next
Once you’re authenticated, the system determines your level of access based on your role. As a marketing executive, for instance, you might be permitted to view campaign data but not access financial or HR records. This ensures that every user operates strictly within their assigned boundaries.
This two-step process happens behind the scenes in milliseconds, yet it’s what keeps organizations safe from unauthorized exposure and ensures users interact only with data relevant to their function.
By ensuring that authentication (identity verification) and authorization (access control) work in harmony, organizations achieve two critical outcomes: security and efficiency.
-
Security, because no unauthorized entity can access restricted systems.
-
Efficiency, because verified users can move freely within their designated access zones without constant friction.
In essence, authentication and authorization together form a trust loop, one that continuously validates who the user is and what they’re permitted to do. This loop has become the foundation of Zero Trust security models, where no user, device, or application is automatically trusted.
As digital ecosystems evolve, this trust loop is being enhanced by technologies like AI-driven risk analysis and adaptive authentication, which make identity systems smarter, faster, and more context-aware.
The Future of Authentication and Authorization
As cyber threats evolve and user expectations rise, the future of authentication and authorization is no longer just about protecting access; it’s about anticipating risk, adapting in real time, and creating seamless digital trust.
The world is moving from static security checkpoints to intelligent, context-aware identity systems that learn and respond dynamically to user behavior.
Here’s how the next generation of authentication and authorization is taking shape:
1. AI-Powered Risk Detection and Behavioral Analytics
Artificial intelligence is reshaping identity management. Instead of relying solely on fixed credentials, AI-driven systems continuously analyze user behavior, device signals, and contextual data to detect anomalies.
For example, if an employee logs in from a new location or device at an unusual hour, the system can trigger an adaptive response such as prompting additional verification or temporarily limiting access.
This risk-based authentication approach reduces friction for trusted users while automatically tightening security in suspicious situations.
2. Adaptive Authentication: Security That Adjusts in Real Time
Traditional MFA applies the same checks to every login attempt. Adaptive authentication, however, adjusts its requirements based on context such as IP address, geolocation, device type, or login history.
Low-risk users may experience a one-click login, while high-risk attempts face additional layers of verification. This balance between convenience and security is critical for modern businesses that can’t afford to frustrate legitimate users or delay workflows.
3. Zero Trust Architecture Becomes the Standard
The Zero Trust model, built on the principle of “never trust, always verify,” is now the foundation of enterprise security. It treats every request, internal or external, as potentially untrusted until authenticated and authorized.
This approach ensures continuous verification throughout a user’s session rather than relying on a single point of entry. In practice, that means every access attempt to a file, an app, or an API is re-evaluated using authentication tokens and policy-based authorization rules.
Zero Trust combines strong identity verification, adaptive access controls, and micro-segmentation to minimize the blast radius of any potential breach.
4. Decentralized and Passwordless Identity Systems
The future of authentication is passwordless and increasingly decentralized. Technologies like passkeys and biometric-based verification eliminate the weaknesses of password management altogether.
Meanwhile, decentralized identity (DID) models allow users to control their own digital identities, sharing only necessary credentials through secure blockchain or cryptographic mechanisms. This shift enhances privacy, reduces data silos, and gives users more autonomy over their identity data.
5. Unified Identity Across Platforms and Devices
As organizations embrace digital ecosystems that span cloud platforms, mobile apps, and IoT devices, the need for consistent identity management becomes vital. Future-ready CIAM and IAM systems focus on unified identity, enabling one to have a secure identity across multiple channels, devices, and applications powered by federated authentication and dynamic authorization policies.
In short, the future of authentication and authorization is intelligent, adaptive, and user-centric. It’s moving toward an era where identity systems no longer just gatekeep access but proactively build digital trust, creating environments where security and convenience coexist harmoniously.
The final piece of this puzzle is implementation, ensuring these systems are applied effectively and continuously optimized. And that’s where the power of modern identity platforms comes into play.
Conclusion
In the digital era, where every interaction, transaction, and collaboration happens online, authentication and authorization are not just technical processes they are the guardians of trust. Together, they ensure that every access point, every identity, and every data exchange happens securely and intentionally.
Authentication lays the groundwork by confirming who a user is. Authorization builds upon it by defining what that verified user can do. One without the other is incomplete. A system that verifies identity without managing access is as vulnerable as one that manages permissions without confirming who’s asking. When integrated seamlessly, they create a closed-loop of protection that’s vital for both businesses and end users.
As cyber threats continue to evolve, static solutions no longer suffice. Businesses need adaptive, intelligent, and scalable identity frameworks that evolve with their systems that can deliver both airtight security and seamless user experience. That’s where a robust Customer Identity and Access Management (CIAM) platform steps in.
A CIAM solution like LoginRadius brings all these layers together, offering enterprise-grade authentication, adaptive MFA, and fine-grained authorization through developer-friendly APIs. It’s designed to protect millions of digital identities while empowering organizations to deliver frictionless, secure user journeys at scale.
Ready to build a secure foundation of trust for your users?
Explore how LoginRadius CIAM simplifies authentication and authorization with built-in MFA, passwordless login, and access control all designed to help you safeguard data, comply with regulations, and deliver a seamless digital experience.
FAQs
Q: What is the difference between authentication and authorization?
A: Authentication verifies who the user is, while authorization determines what the user can access after their identity is confirmed. Both work together to secure systems and prevent unauthorized actions.
Q: Why is multi-factor authentication (MFA) important?
A: MFA adds additional layers of security beyond passwords, making it significantly harder for attackers to gain access. Even if one factor is compromised, the extra steps help block unauthorized logins.
Q: Which authorization model is best for modern applications?
A: A combination of RBAC and ABAC is often ideal. RBAC simplifies role assignments, while ABAC adds contextual, dynamic rules—together offering flexible and scalable access control.
Q: How do authentication and authorization support Zero Trust security?
A: Zero Trust requires continuous verification. Authentication confirms identity at each step, and authorization enforces strict, context-based access—reducing the chances of lateral movement inside the system.



