Key Takeaways
-
Every login, app session, and digital interaction begins with one foundational element: a device.
-
To trust that device, systems rely on a Device ID—a unique identifier that establishes strong device identity for authentication, access control, analytics, and attribution.
-
In this guide, you’ll learn what Device ID is, how device authentication works, the differences between security-driven Device IDs and marketing-driven identifiers, and how businesses use them across mobile, web, and IoT environments.
-
We’ll explore device-based authentication, device-to-device authentication, device identity management, and modern device authentication methods.
-
You’ll also see how a CIAM platform like LoginRadius empowers organizations to manage device identity, enforce secure user-based device access management, and unify device-based verification across their digital ecosystem.
By the end, you’ll understand how Device ID powers everything from cybersecurity to mobile attribution to personalized CX—and how to implement it responsibly.
A Device ID is a unique, persistent identifier associated with a physical device, used to authenticate the device, track app activity, personalize experiences, or verify user access. In security, Device ID enables strong device identity and device-based authentication. In marketing, Device ID supports mobile attribution, analytics, and cross-app measurement.
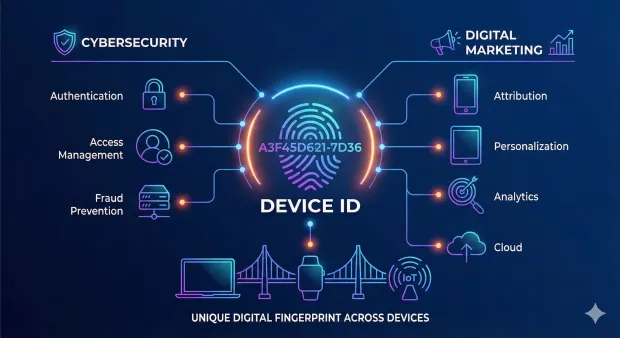
In a nutshell, a Device ID is a unique identifier tied to a physical device—such as a smartphone, tablet, laptop, or IoT sensor. It acts as the device’s “digital fingerprint,” enabling systems to recognize the device across sessions, applications, and networks. Depending on context, Device ID can refer to system-level identifiers (like Apple’s Identifier for Advertisers, Android’s GAID), hardware identifiers (IMEI), or platform-generated cryptographic identifiers used for device authentication.
In cybersecurity, Device ID establishes a trusted device so organizations can implement device-based authentication, device-to-device authentication, or user-based device access management. Security teams use Device ID to verify whether the device attempting access is the same device that was originally registered, helping prevent impersonation, account takeover, or fraud.
In digital marketing and analytics, Device ID helps attribute user actions to a device across apps and campaigns. Although privacy regulations have limited long-term tracking, Device ID is still used for mobile attribution, fraud detection, retargeting, and optimizing user journeys.
Across both security and analytics contexts, the goal remains the same: establish strong device identity in a way that benefits the business while respecting user privacy. With the rise of passwordless authentication, multi-device experiences, and mobile-first products, Device ID has become fundamental to modern identity ecosystems.
How Device IDs Work
A Device ID works by assigning a unique identifier to a device and using that identifier during interactions between the device and an application, server, or network. The identifier may be hardware-based (tied to chip components), software-based (generated by OS or app), or cryptographic (derived using secure hardware modules).
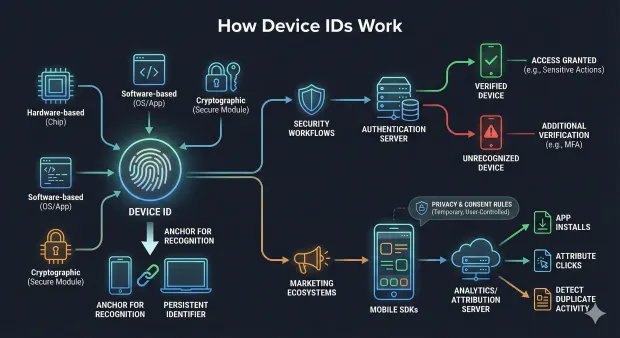
Regardless of how it’s created, a Device ID becomes the anchor for recognizing the device in future sessions.
When a device connects to an app or service, the Device ID is used to authenticate or verify the device’s legitimacy. In security workflows, this allows systems to enforce device-based authentication or device-based verification—two essential components of strong device identity. For example, an organization may restrict sensitive actions (like password reset or financial transactions) to devices that have been previously authenticated. If the Device ID doesn’t match, the system triggers additional verification such as MFA.
Meanwhile, in marketing ecosystems, mobile SDKs generate or retrieve Device IDs from the OS to measure app installs, attribute clicks, and detect duplicate activity. These Device IDs are temporary and subject to consent rules, reflecting the shift toward privacy-preserving identifiers.
In either use case, Device ID acts as a trusted reference point. It helps create continuity, maintain security, personalize experiences, and reduce fraud—whether you're securing logins, attributing campaigns, or managing device clusters in IoT environments.
What is Device Authentication
Device authentication is a security process that verifies a device’s identity using identifiers, cryptographic keys, or certificates. It ensures only trusted devices can access accounts, networks, or applications.
It’s a process of verifying that a device is genuine, uncompromised, and authorized to connect to a system. While user authentication confirms who is accessing a system, device authentication confirms what they’re using. Both are necessary for robust security.
Traditionally, authentication in mobile apps relied heavily on passwords or SMS-based device authentication methods. However, these approaches can’t guarantee that the device itself is trustworthy. Modern systems use strong device identity established through Device IDs, secure hardware elements, cryptographic tokens, or certificates. This allows organizations to create a “chain of trust,” ensuring that both the user and device meet security requirements.
Companies increasingly use device-based authentication to enable passwordless experiences. When a trusted Device ID is paired with a verified user identity, login becomes smoother while security remains intact. In high-risk industries like fintech, healthcare, and enterprise SaaS, device authentication methods such as certificate pinning, secure enclaves, and private key storage provide added assurance.
Solutions like LoginRadius enhance this model by providing user-device linking, adaptive authentication, policy-based access control, and device risk scoring—helping organizations manage device identity at scale while protecting sensitive data.
Types of Device IDs: Security vs Marketing
Device IDs fall into two major categories: security-oriented identifiers and marketing/analytics identifiers. Each has different use cases, lifecycles, and privacy considerations.
Security-Focused Device IDs
These identifiers verify device authenticity and support device identity management. Examples include:
-
Cryptographically derived device keys
-
Device-bound tokens stored in secure hardware
-
Certificates for device-to-device authentication
-
Internal app-generated Device IDs tied to the user’s account
These identifiers power device-based verification, device-bound passkeys, OAuth device code flows, and zero-trust models.
Marketing-Focused Device IDs
Used to track installs, measure campaigns, and understand mobile user behavior.
Examples include:
-
IDFA (Apple’s Identifier for Advertisers)
-
GAID (Google Advertising ID)
-
Android ID
-
Vendor-specific app installation IDs
These IDs support app attribution, analytics models, retargeting, and cross-app measurement—though privacy regulations have increasingly restricted them.
Understanding these categories helps product teams design compliant, secure, and privacy-aligned device identity frameworks across both web and mobile ecosystems.
Device Authentication Methods
Organizations use a variety of device authentication methods, often layered for stronger assurance.
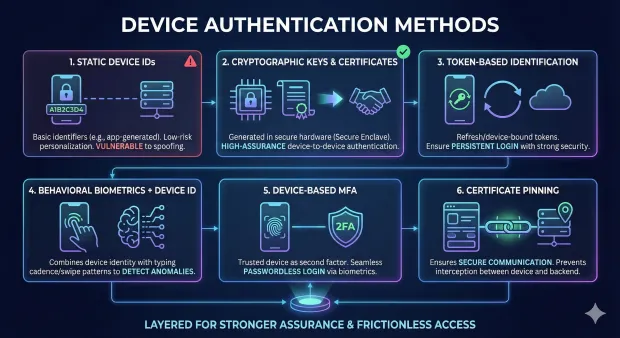
1. Static Device IDs
Basic identifiers stored locally (e.g., app-generated IDs). Used for low-risk personalization but vulnerable to spoofing without additional safeguards.
2. Cryptographic Keys & Certificates
Device keys generated and stored in secure hardware (Secure Enclave, Trusted Execution Environment) are the modern standard. These keys enable high-assurance device-to-device authentication and device-based verification.
3. Token-Based Identification
Refresh tokens or device-bound OAuth tokens stored securely on the device ensure persistent login while maintaining strong security.
4. Behavioral Biometrics + Device ID
Systems combine device identity with behavioral signals—swipe patterns, typing cadence—to detect anomalies or potential account takeover.
5. Device-Based MFA
A trusted device acts as a second factor, allowing seamless passwordless login. The user confirms via biometrics or a secure element–backed key.
6. Certificate Pinning
Used in mobile apps to ensure secure communication between the device and backend servers, ensuring the connection cannot be intercepted.
Using multiple device authentication methods together—especially cryptographic ones—helps organizations maintain secure and frictionless access experiences.
Device-to-Device Authentication (Machine-to-Machine Authentication)
Device-to-device authentication, aka machine-to-machine (M2M) authentication, enables two devices to securely identify and communicate with each other without human intervention. This is essential for IoT environments, edge computing, smart homes, industrial sensors, and enterprise networks where hundreds or thousands of devices interact autonomously.
At its core, this method uses cryptographic keys, certificates, and secure protocols to ensure both devices can mutually verify identity. This prevents unauthorized devices from injecting data, joining networks, or impersonating legitimate hardware.
In mobile ecosystems, device-to-device authentication and authorization plays a key role in pairing workflows (Bluetooth pairing, hotspot sharing), secure file transfers, and multi-device account continuity. For example, when a new device is added to a user’s identity cluster, an existing trusted device often authorizes the new one using secure pairing protocols.
From a CIAM perspective, device-to-device authentication strengthens user-based device access management. When users manage multiple devices—phones, tablets, desktops—organizations can enforce policies about which devices can access sensitive resources, how they must authenticate, and when they need re-verification.
As IoT devices proliferate, secure device-to-device authentication becomes essential—not just for functionality but also for compliance, safety, and operational integrity.
Device Identity Management
Device identity management involves registering, tracking, validating, and governing devices that connect to an organization’s digital ecosystem. It is an extension of identity access management (IAM), but applied to devices instead of people.
This includes:
-
Linking devices to specific users
-
Defining trust levels for each device
-
Monitoring device behavior and risk signals
-
Enforcing authentication and re-authentication requirements
-
Managing device revocation (lost, stolen, compromised devices)
Strong device identity management is essential for industries like fintech, healthcare, retail, and enterprise SaaS — where device activity can expose vulnerabilities if not properly controlled. Without proper management, attackers can clone device IDs, hijack tokens, or bypass user verification.
A mature device identity strategy helps organizations:
-
Reduce account takeover (ATO)
-
Identify suspicious devices or patterns
-
Enforce adaptive MFA
-
Improve user experience by allowing trusted devices to bypass friction
-
Support multi-device journeys across web and mobile
With the rise of passwordless authentication and passkeys, device identity management has become intertwined with user identity. Trusted devices now act as cryptographic authenticators, making secure device identity essential for user access.
Applications of Device ID
Device IDs have diverse applications across industries:
1. Security & Authentication
Organizations use Device ID to:
-
Recognize returning devices
-
Enable device-based authentication
-
Block unknown devices from accessing sensitive workflows
-
Trigger step-up verification during anomalies
2. Personalization & Experience
Device ID helps tailor content, save preferences, keep users logged in, and deliver tailored recommendations—without requiring constant user authentication.
3. Fraud Prevention
By identifying abnormal device fingerprints, organizations detect:
-
Bot activity
-
Device emulators
-
High-risk devices
-
Credential stuffing
-
ATO attempts
4. Mobile Attribution & Analytics
Marketing teams rely on device identifiers to:
-
Attribute ad clicks to installs
-
Measure campaign performance
-
Prevent duplicate counting
-
Optimize user acquisition
5. IoT Trust Models
Device ID allows IoT devices to securely authenticate with hubs, gateways, and cloud platforms—preventing tampering or bad data injection.
Across all these use cases, a secure and privacy-aligned Device ID framework becomes the cornerstone of digital trust.
Best Practices for Building a Secure Device ID Framework
Use privacy-safe identifiers instead of raw hardware IDs
Avoid exposing IMEI or other fixed hardware identifiers. Use rotating, cryptographically derived Device IDs stored in secure hardware (Secure Enclave, TEE) to prevent spoofing and enhance privacy.
Link every device to a specific user profile
Implement user-based device access management so each trusted device is explicitly tied to an account. Give users full visibility and control over their registered devices to support revocation, recovery, and transparency.
Apply device risk scoring and continuous evaluation
Assess device posture using signals such as OS version, jailbreak/root status, network reputation, geolocation patterns, and historical behavior. Use these scores to trigger adaptive MFA, limit access, or block high-risk devices.
Be transparent about how identifiers are used
Clearly communicate when Device IDs are used for authentication, fraud prevention, personalization, or attribution. This reinforces trust and avoids compliance issues related to tracking or consent.
Unify device identity with your CIAM platform
Centralize device governance within your identity infrastructure. Integrate policies for authentication, access control, device verification, and session management to maintain consistent security across all apps and channels.
How LoginRadius CIAM Strengthens Device Identity and Device Authentication
A modern identity platform like LoginRadius strengthens every aspect of device identity by providing secure, scalable infrastructure across user authentication, device tracking, and access control.
LoginRadius enables organizations to register and manage trusted devices at the identity layer. This includes securely linking devices to user profiles, managing device metadata, and enforcing device-based verification rules. Its adaptive authentication engine uses device intelligence—IP reputation, geolocation, device posture—to determine risk in real time and trigger step-up authentication when necessary.
For organizations deploying passwordless flows, LoginRadius supports device-based authentication using WebAuthn, passkeys, and FIDO2. The platform ensures cryptographic keys stay bound to the user’s device while offering seamless login experiences across sessions.
LoginRadius also supports user self-service device management, enabling people to view, approve, and revoke devices directly from their profile. This improves transparency and reduces helpdesk load.
For enterprises, LoginRadius integrates device identity with SSO, MFA, and policy-based access control—ensuring consistent enforcement across all digital properties. Whether you're verifying mobile devices, managing IoT access, or enforcing device-to-device authentication, LoginRadius provides the unified identity foundation needed for secure, scalable device identity management.
Conclusion
Device ID has evolved from a simple identifier into a multi-dimensional tool that powers security, personalization, analytics, fraud detection, and mobile attribution. Whether used for device authentication, device-to-device authentication, mobile attribution, or strong device identity, Device ID sits at the intersection of security and experience. As digital ecosystems grow more complex, strong device identity and device-based verification become essential—not optional.
Organizations adopting Device ID must balance security with privacy, ensuring transparent, ethical use of device identifiers while maintaining frictionless access. With a modern CIAM platform like LoginRadius, businesses can unify device identity management, user-based device access management, and adaptive security under one consistent framework.
In a mobile-first, passwordless world, Device ID is becoming the new cornerstone of trust. Implement it wisely, and it becomes a competitive advantage across security, CX, and analytics.
FAQs
1. What is Device ID?
Device ID is a unique identifier tied to a physical device, used for authentication, attribution, personalization, and mobile analytics.
2. How does device authentication work?
Device authentication verifies a device’s identity using identifiers, cryptographic keys, or certificates to ensure only trusted devices can access systems.
3. What is device-based verification?
It’s an approach where a verified device becomes part of the authentication flow, reducing reliance on passwords and preventing unauthorized access.
4. What is device identity management?
Device identity management tracks, verifies, and governs devices linked to user accounts to strengthen security and enable multi-device journeys.



