Authentication has seen a massive change in the last five years - more than it has seen in the previous twenty. Yes, passwords, SMS OTPs, and traditional MFA are still used. But security teams are moving to stronger, simpler methods: passwordless authentication, passkeys, push MFA, device trust, and continuous risk checks.
And the most interesting aspect is - there's no artificial hype driving this shift. It’s actually driven by a very simple reality: shared secrets are easy to attack, while device-bound credentials are not.
If you run an e-commerce app, a consumer SaaS product, or any digital experience where customers log in, you're probably facing one or more of the following challenges:
-
Rising credential-stuffing attacks
-
High abandonment at login
-
Customers forgetting passwords
-
UX friction during checkout
-
MFA fatigue
-
Compliance pressure
-
A cluttered mess of legacy login flows
Passwordless and MFA are often pitched as "the fix". But the truth is: they only work if implemented with clarity, context, and real user behavior in mind.
In this blog, we are trying to find out a breakdown of modern authentication's core components for 2026. We’ll cover how passwordless works, when to trigger MFA, how passkeys improve security and UX, and why organizations are quickly abandoning legacy MFA.
Let’s get started!
What Passwordless Authentication Really Means
One of today's highest-searched identity topics is "passwordless authentication", and for good reasons. But more often than not, the term is misconstrued.

Passwordless authentication is not “logging in without typing a password.” It means removing passwords entirely from the security model.
Instead of relying on something the user knows- “a password” -passwordless authentication depends on:
-
Something the user possesses - a trusted device.
-
Something the user is - a biometric such as fingerprint or FaceID.
-
Something the system verifies silently - a cryptographic key pair.
Passwordless authentication solutions today are based on public-key cryptography. During registration, the user's device creates a private-public key pair. The private key remains on the device and the public key is sent to the server.
When a user signs in, the server challenges, the device signs it with the private key, and the server verifies the public key. No shared secret is ever sent. Nothing can be phished or replayed.
This is why passwordless security has become the foundation of modern consumer identity systems: stronger, simpler, and far less prone to user error.
Passkeys, WebAuthn & Multi-Device Credential Sync
Passkeys are the most common and accessible form of passwordless authentication today. They're built on the W3C standard known as WebAuthn that all major platforms support.
Why passkeys matter
Passkeys offer:
-
Phishing-resistant login
-
Instead of typing a password, biometric unlock
-
Faster onboarding and fewer support tickets
-
Automatic multi-device sync across Apple, Google, and Microsoft ecosystems
One of the biggest user-experience wins is multi-device credential sync. A customer creating a passkey on an iPhone can easily use it on a MacBook or iPad through iCloud Keychain. Similarly, passkeys sync via Google Password Manager and Windows Hello.
Because they offer security, speed, and recovery without the need for a password, passkeys have become the recommended default authentication method for most consumer applications.
Push MFA vs SMS OTP
One of the biggest questions that teams have when modernizing MFA is whether SMS OTP still has a place.
SMS OTP is:
-
Easy for the user to comprehend
-
Simple to implement
-
Universally supported
But SMS OTP comes with serious disadvantages:
-
Vulnerable to SIM-swap attacks
-
OTP interception malware
-
Phishing kits that request OTPs from users
-
Delivery delays or failures
-
High operational costs
That’s where Push MFA comes in as its modern replacement
Push MFA sidesteps these issues altogether by authenticating the trusted device directly. When a login requires additional assurance, the user is sent a secure push notification via their app. They confirm the request and, if necessary, unlock it with a biometric.
Benefits of Push MFA:
-
Phishing-resistant
-
Fast and low friction
-
Tied to user's actual device
-
Supports real-time context: location, IP, risk signals
-
Much harder to trick or intercept
In 2026, push MFA over SMS is the preferred option for most organizations since it is far more secure and more user-friendly.
When to Trigger Step-Up Authentication
The question "What is MFA?" is still common, but today, more relevant is the question of when to use MFA.
Step-up authentication is invoked only when necessary. Modern systems no longer ask for MFA on every login; they adapt to context.
Common triggers include:
-
New device or browser
-
Suspicious IP or behavior
-
High-risk location
-
Impossible travel: too far, too fast
-
Sensitive user actions: password reset, payment update
-
Privileged account activity
Step-up MFA strikes a balance between user experience and security by making authentication dynamic, not rigid. Low-risk logins stay fast. High-risk situations invoke extra verification.
Behavioral & Continuous Authentication
Authentication is no longer a one-time check at login. In 2026, security teams will be increasingly employing continuous authentication, a continuous evaluation of the user's behavior and context throughout the session.
This includes:
-
Mouse movement patterns
-
Typing behavior
-
Geolocation patterns
-
Network changes
-
Device posture
-
Sudden spikes in requests
-
Unusual navigation paths
If something doesn’t look right, such as a user suddenly operating like a bot or accessing data at unusual hours, the system can:
-
Trigger MFA
-
Lock the session
-
Revoke access
-
re-authenticate the requestor
Continuous authentication reduces the window attackers can exploit. It also improves overall session integrity without interrupting normal users.
Device Trust, Impossible Travel & Risk Scoring
Modern authentication decisions rely heavily on device intelligence and risk scoring.
Device Trust
It gauges the confidence of the system that this device belongs to the user based on:
-
OS type and version
-
Device ID
-
App integrity
-
Browser fingerprint
-
Rooting or jailbreak status
-
Past behavior
Impossible Travel
It is one of the more straightforward, but quite effective signals. If a user logs in from Delhi and then appears to log on 10 minutes later from Berlin, it assumes the second login is suspicious.
Risk Scoring
Risk scoring brings multiple signals together:
-
IP address reputation
-
Network indicator
-
Using VPN or Tor
-
Behavioral anomalies
-
Device posture
-
Time of day
-
Failed attempts
Based on the score, the system decides to:
-
Allow
-
Step-up MFA
-
Block
-
Alert security teams
This is an inherently more adaptive approach than relying on static rules.
Login Notifications & Suspicious Activity Alerts
As passwordless authentication proliferates, organizations increasingly rely on proactive account protection features such as:
-
Login notifications
-
New device notifications
-
Suspicious activity warnings
-
Account recovery confirmations
These notifications help in the early detection of unauthorized access and serve as a safety net for passwordless flows.
Combined with passkeys and push MFA, notifications create a comprehensive security experience: strong protection, yet still easy to use.
Passwordless vs. MFA: How They Fit Together
Many people think passwordless replaces MFA, but in reality, passwordless and MFA work in tandem.
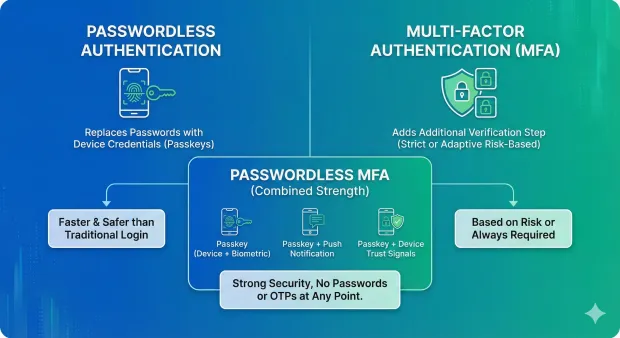
Passwordless authentication
Replaces passwords with device-based credentials like passkeys. It's faster and much safer compared to the traditional login flows.
Multi-factor authentication
Adds an additional verification step when necessary, either always (strict MFA) or, based on risk, adaptive MFA.
Passwordless MFA
A growing category where both factors are passwordless, such as:
-
Passkey (device + biometric)
-
Passkey + push notification
-
Passkey + device trust signals
Passwordless MFA provides users with strong security, not requiring passwords or OTPs at any point.
Why Legacy MFA Is Dying
Legacy MFA methods—SMS OTP, email OTP, security questions—are losing their relevance because the attackers have adapted.
Today's threats include:
-
Automated phishing kits
-
Reverse-proxy attacks
-
OTP stealing malware
-
MFA fatigue attacks
-
Credential stuffing
Legacy MFA was built for the password era. Passkeys, WebAuthn, and push MFA are built for today's threat landscape.
Organizations are abandoning legacy MFA due to the following:
-
High friction increases drop-off.
-
Users are tired of OTP loops.
-
Resets and failures increase the cost of support.
-
Phishing threat continues to rise
Modern MFA is at once easier and more secure.
Why LoginRadius Leads in Passwordless UX
LoginRadius is all about providing safe authentication without making people jump through hoops. For consumer apps in particular, this really matters: every additional step affects conversion.
What makes LoginRadius special? It offers:
-
Native Passkey + WebAuthn Support: Built directly into the platform, with straightforward setup and full device sync support.
-
Push notification MFA: Fast, biometric-confirmed MFA without the risks of SMS OTP.
-
Device Trust Framework: Identifies trusted devices, reduces unnecessary MFA prompts, and strengthens risk detection.
-
Continuous Authentication: Adaptive checks throughout the session, rather than just at login.
-
Global Scale & Reliability: Serving millions of logins a day with predictably low latency.
-
Fully Branded Experiences: No-code hosted pages give companies complete visual control without requiring intensive development.
-
Developer-Friendly Implementation: Flexible APIs and SDKs, fully documented.
LoginRadius combines strong security with a smooth user experience—two things that often feel at odds in traditional systems.
Conclusion
Passwordless authentication and modern MFA are no longer "future ideas"; they are today's foundations for secure, user-friendly login flows. Passkeys, push MFA, device trust, and continuous authentication make it possible to reduce friction, cut fraud, and streamline the entire identity experience.
Teams that invest in passwordless now are building a login experience that is faster, safer, and easier for both users and developers.
Whether you want to deploy passkeys, push MFA, or a full passwordless-first approach, LoginRadius will get you there faster with a secure, completely branded experience.
Click here to book a personalized demo. Explore the LoginRadius Passkey and MFA documentation. Discuss with our identity experts.
FAQs
1. What is passwordless authentication?
Passwordless authentication replaces passwords with secure device-based verification methods such as passkeys, biometrics, or push notifications.
2. How does passwordless authentication work?
It uses public-key cryptography. Your device stores a private key and signs a challenge. The server verifies the signature using the public key. No password is ever sent.
3. Is passwordless more secure?
Yes. It removes passwords, which are the most common attack vector. Passkeys and WebAuthn are phishing-resistant and tied to the user’s device.
4. What are examples of passwordless methods?
Passkeys, WebAuthn, biometric login, magic links, push MFA, and device-bound authentication.
5. What is MFA?
Multi-factor authentication verifies a user using two or more factors: something they know, have, or are.
6. What are common MFA methods?
Push notifications, TOTP apps, SMS OTP, email OTP, biometrics, and passkey-based MFA.
7. What is passwordless MFA?
A form of MFA where both factors are passwordless—for example, a passkey plus a biometric prompt or a push notification.
8. Is SMS OTP still safe?
It is widely used but increasingly vulnerable to phishing, SIM-swaps, and malware. Push MFA and passkeys are more secure.
9. What is step-up authentication?
Triggering MFA only when needed, based on device trust, behavior, or risk level.
10. What is continuous authentication?
Real-time checks that verify users throughout the session, not only at login.
11. Can passwordless work for consumer apps?
Yes. Passkeys and push MFA are ideal for large-scale consumer applications because they reduce friction and support multi-device sync.
12. How do I get started with passwordless?
LoginRadius provides built-in support for passkeys, push MFA, and adaptive authentication, making implementation straightforward for development teams.