What is Identity and Access Management (IAM)?
Identity and Access Management in cybersecurity refers to the security framework and disciplines for managing digital identities. It regulates the responsibilities and access privileges associated with individual consumers and the conditions in which such privileges are allowed or denied.

Table of Contents
- What is IAM
- What Is Identity and Access Management in Cybersecurity
- How IAM Works
- Designing a Modern IAM Program for Your Enterprise
- Benefits of Identity and Access Management
- How IAM and Compliance Are Related to Each Other
- The Future of IAM in the Post-COVID Digital Era
- How LoginRadius IAM Solution Can Accommodate Your Enterprise Requirements
- Conclusion
What is IAM
What is IAM

Identity and Access Management (IAM) is a core discipline for any enterprise IT, as it is inseparably linked to the security and sustainability of companies.
When more and more businesses storing their confidential data electronically, it is important to ensure that data remains secure.
"Users," "roles," "access" might be some of the terms you have heard concerning identity and access management. So, let's break it down.
- Identity: Identity implies how you are represented and digitally documented online, sometimes through social login, work email address, or personal email ID.
- Access: Access refers to determining that the right user can access the right resource securely inside a network, at the right time.
This is majorly what an ideal identity and access management strive to provide.
What Is Identity and Access Management in Cybersecurity
Identity and Access Management in cybersecurity refers to the security framework and disciplines for managing digital identities. It regulates the responsibilities and access privileges associated with individual consumers and the conditions in which such privileges are allowed or denied.
In simpler terms, IAM encompasses:
- The provisioning and de-provisioning of identities in the IAM system.
- Securing and authenticating identities.
- Authorizing access to resources or performing certain actions.
- Incorporating the correct levels of protection and access for sensitive data.
IAM includes tools like two-factor authentication, multi-factor authentication, single sign-on, and privileged access management. These tools can store identity and profile data safely.
They also comply with data governance functions to ensure that only appropriate and relevant information is being shared.
Information technology (IT) administrators can restrict user access to sensitive data within their organizations by putting an IAM security framework in place.
What Are the Key IAM Terms
Here are some of the key terminologies that you will encounter while processing identity and access management.
- Access management: It refers to the processes and tools used to control and monitor network access for both on-premises and cloud-based systems.
- Authentication– It is the first in the login process in which users enter their credentials to verify their identity.
- Authorization– After authentication, the system now determines whether the authenticated user has permission to perform the action they have requested.
- De-provisioning- It is the process of removing an identity from an ID repository and terminating access privileges.
- Entity- The identification that has been used to authorize an entry. Usually, this comes either from a task grouping or an individual user account.
- Identity Analytics – They are repositories that capture logging activities for authentication and authorization.
- Managed Policy - It is a set of rules that an IAM system follows to track which users, organizations, and positions have access to which services.
- Multi-Factor Authentication - It verifies consumer identities by adding (compulsory or optional) additional layers of security to the authentication process, usually in the form of numeric or alphanumeric codes.
- Principal: The source that demands permission to access a resource. It can be a human being or an automated system.
- Privileged account management: It refers to managing and auditing accounts and data access based on consumers' allowed privileges.
- Risk-Based Authentication - It is an advanced authentication method that uses real-time intelligence to verify a consumer based on certain risk scores. They usually include factors like login device, consumer identity, geolocation, geo velocity, number of failed login attempts, and more.
- Single Sign-On - It allows consumers to log in to multiple independent applications with a single set of credentials, eliminating the need for multiple usernames and passwords.
- User Provisioning – It is the process of creating new enterprise accounts for users and assigning them access privileges.
How IAM Works
Identity and access management systems perform three main tasks viz. identification, authentication, and authorization. In other words, IAM functions to provide the right people access to devices, hardware, software applications, or any IT tool to perform a specific task.
All IAM includes the following core components:
- A database that includes the identities and access rights of users.
- IAM tools to provision, monitor, change and remove access privileges.
- A framework for auditing login and access history.
The list of access rights must be up-to-date all the time with the entry of new users or the change of roles of current users. In an enterprise, the responsibilities of identity and access management typically come under IT or departments that handle data processing and cybersecurity.
The key functionalities of an IAM
- It manages identities: IAM creates, modifies, and deletes users. It also integrates with one or more other directories and synchronizes with them.
- It provisions/provisions users: Once a user seeks permission to enter a system, IAM specifies which resource the user has access to and what level of access (like editor or viewer) based on their roles in the organization. On the contrary, when a user leaves the organization, IAM deprovisions from all the systems they have access to. After all, an ex-employee still having access to an organization's resources can have serious security implications.
- It authenticates users: IAM authenticates users using tools like multi-factor authentication and adaptive authentication when they request access.
- It authorizes users: After authenticating, IAM authorizes access to specific apps and resources based on predefined provisioning.
- It provides report: IAM provides reports to help organizations identify possible cybersecurity threats, and strengthen their safety processes under global compliances.
- It offers single sign-on: IAM allows consumers to access any connected web properties with a single identity. SSO adds security to the process of authentication and makes it even easier and faster to access resources.
Designing a Modern IAM Program for Your Enterprise
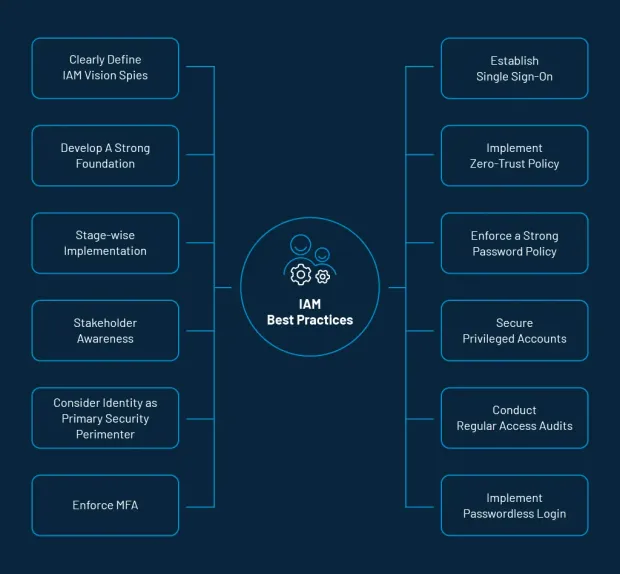
Here are the best practices to enable a smooth and seamless integration of a modern IAM program.
Define your IAM vision
Your IAM should be a combination of modern technologies and business processes. You need to understand your current IT and network infrastructure and build your future capabilities around it.
Later, incorporate authorization, privileges, policies, and other constraints to ensure secure access into your web properties.
A strong foundation is a must.
This includes a thorough assessment of the capabilities of the IAM product and its sync with organizational IT. An efficient risk evaluation should ideally cover:
- An understanding of what third-party apps are currently in use.
- What are your technological forte and limitations?
- Should you build or buy your IAM solution?
Stage-wise implementation.
An IAM program is usually implemented based on the two practices mentioned above. However, to avoid any complications, most IAM experts recommend a stage-wise implementation process.
Conduct a stakeholder awareness program.
Your stakeholder awareness program should cover detailed training about your product abilities, scalability standards, and what technologies you are using. However, more than anyone, train your IT teams as they should most definitely know about your IAM's core capabilities.
Identity should be your core security parameter.
Organizations should move from the conventional focus of securing a network to securing identity. Centralize security controls around the identities of users and facilities.
Enable multi-factor authentication (MFA).
MFA is a crucial part of identity and access management. After all, it adds multiple security layers to user identities before allowing access to an application or database. Therefore, ensure that you have enabled MFA for all users and consumers, including IT admins and C-suite executives.
Implement Single Sign-On (SSO).
Establish SSO for all your web properties (devices, apps, and services) so consumers can use the same set of credentials to access multiple resources.
Enforce a zero-trust policy.
Zero Trust is a holistic approach to network security where consumer identities are strictly verified, regardless of whether they are located inside or outside the network perimeter. However, it is only effective when you track and verify the access rights and privileges of consumers on an ongoing basis.
Implement a strong password policy.
Enforce a strong password policy for both employees and your consumers. Make sure they are updating passwords regularly and aren't using sequential and repetitive characters.
Secure all privileged accounts.
A good way to protect your critical business asset is to secure all privileged accounts. For starters, limit the number of users who have access to those accounts.
Conduct access audits from time to time.
Regularly conduct access audits to ensure that whatever access you have granted is still required. You can offer additional access or revoke consumer access based on your audit report.
Favor passwordless login.
Passwordless login simplifies and streamlines the authentication process by swapping traditional passwords with more secure factors. These extra-security methods may include a magic link, fingerprint, PIN, or a secret token delivered via email or text message.
Benefits of Identity and Access Management
It reduces security risk.
Organizations can use identity and access management solutions to detect unauthorized access privileges, validations, or policy violations under a single system. You can also ensure that your organization meets necessary regulatory and audit requirements.
It is easy to use.
With IAM, it is easier to provision and manage access to end-users and system administrators. It also simplifies and secures the process of registration and authentication.
It reduces IT costs.
Using IAM can lower operation costs to quite an extent. For example, with federated identity, organizations can integrate third-party services into their system. Similarly, with cloud IAM organizations need not buy or maintain on-premise infrastructure.
It improves user experience.
SSO removes the need for users to recall and enter multiple passwords. Gone are the days of trying to remember dozens of password variations. With SSO, every time consumers switch to a new connected device, they can enjoy automatic logins.
It enhances security profiles.
Modern IAM systems use SSO with additional levels of protection. A majority of these systems use Security Assertion Markup Language (SAML) 2.0 that can authenticate and authorize users based on the access level indicated in their directory profiles.
A few other benefits of identity and access management system include:
- It enables secure, low-friction access through seamless authentication to different web properties.
- It demonstrates an extreme degree of scalability by anticipating potential surges and dips in consumer registrations and activities.
- It provides a unified experience by utilizing consolidated reports and analytics of user demographics, social registration and login data, revenue activities, and more.
- It adheres to privacy regulations for protecting data in transit and at rest.
- It keeps user data protected at all times by developing flexible schemas to get the most out of a system.
How IAM and Compliance Are Related to Each Other
Consumer data centricity is crucial to the success of any business today. Organizations should securely collect, manage, analyze, and protect their data. However, the method of capturing and safely storing user data can be difficult.
Many companies keep hundreds of separate data silos to get the job done. Fortunately, an identity and access management solution can help organizations break down these silos and store data into a unified database that provides a consistent view of the client across the business ecosystem.
Consumers want more control over their data at the same time. They want the nod on how brands use their data, they also wish to know precisely what they agreed to while using the product or service. An IAM solution offers trust and transparency to consumers by helping organizations ensure compliance with local and global regulations.
Speaking of regulations, many are industry-specific, such as the Health Insurance Portability and Accountability Act (HIPAA) for healthcare organizations. Others apply more broadly, such as the Payment Card Industry Data Security Standard (PCI DSS) that must be adopted by any organization that collects debit and credit card information.
The most disruptive regulations in recent years are the ones related to ensuring consumer privacy, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA).
The following are a few of the major security assurance programs identity solutions adhere to:
- OpenID - End-user identity verification supported by OAuth 2.0 protocol
- PCI DSS - Administered standard for payment transactions
- ISO 27001:2013 - Information security management system
- ISO 27017:2015 - Information security for cloud services
- AICPA SOC 2 (Type II) - System-level controls for Trust Services Criteria - security, availability, process integrity, confidentiality, and privacy
- ISAE 3000 - International attestation standard for assurance over non-financial information
- NIST Cybersecurity Framework - Standardized security framework to manage and reduce cybersecurity risk.
- CSA CCM Level 1, Level 2 - STAR Self-Assessment, STAR Certification, STAR Attestation, and C-STAR Assessment.
- CIS Critical Security Controls Global standards for internet security
- US Privacy Shield Complaint resolution for EEA citizens
- ISO/IEC 27018:2019 - PII Protection
The Future of IAM in the Post-COVID Digital Era
We live in the age of ever-growing cybersecurity threats. Organizations cannot afford to undermine the value of managing identities inside or across their systems. An IAM solution ensures that all identities are tracked, updated, and maintained throughout the users' lifecycle.
Although 2020 has been a year-long roller coaster with the pandemic hitting hard, there's one thing that happened for sure. Digital transformation has progressed at an unparalleled pace, and identity and access management (IAM) is a major part of that evolution.
Let's look at some of the most changing developments in the IAM market anticipated in 2021.
User managed access (UMA) will reign supreme in 2021.
With more and more services migrating to the digital front, users are expecting amazing experiences online. To keep up with these demands, as more organisations continue to adopt the delegation model, digital interactions will need to include more than one identity.
In 2021, conventional authentication and MFA controls will take over solutions that include a central management framework for organizing digital resources that reside in many places.
2021 will be the year of zero login methods.
Now that passwordless authentication (such as biometrics) has witnessed abundant adoption, we can see a shift to a "zero login" mechanism that reduces user friction.
Since, there will be no credentials to remember, MFA will take the backseat. Zero login will allow consumers to use variables such as fingerprints, keyboard typing habits, the way the phone/device is kept, and other markers to verify identification in the background while the user enjoys a frictionless experience.
IT will infuse access governance to protect workforce cybersecurity.
The threat landscape is rapidly changing, courtesy, the increasing pressure on conventional identity governance and administration (IGA) solutions. In addition to rising compliance risks, business IT environments are becoming more complex every year.
In 2020, we will witness AI being increasingly employed to enable an autonomous approach to identity. AI-infused authentication and authorization solutions will be integrated with existing IGA solutions.
And when that happens, it will be easier for enterprises to capture and analyze all identity data and provide insight into various risk levels.
How LoginRadius IAM Solution Can Accommodate Your Enterprise Requirements
With the right IAM provider, organizations can enjoy enormous time-saving, efficiency-building, and security-boosting benefits, irrespective of where they operate.
LoginRadius' extensive experience in the identity and access management market will help you build the right process for your enterprise.
LoginRadius offers you the following tools to help you build secure, seamless experiences for your consumers and workforce.
-
Single Sign-On: LoginRadius SSO provides your users with a single identity to access all of your web assets, mobile applications, and third-party systems.
As your users navigate from one property to the next, you can recognize who they are, and document and access their activities in a central profile.
-
Multi-factor authentication: MFA verifies identities by adding additional layers of security to the authentication process. By requiring at least an extra step to verify identities, MFA ensures that the right consumer has the right access to your network.
It lifts off the burden of stolen or lost passwords on consumers and makes it harder for criminals to get into their accounts.
Additional forms of MFA by LoginRadius include security questions, biometric verification, automated phone calls, Google Authenticator, and social login.
-
Federated SSO: Federated SSO allows users to gain access to multiple organizations' web applications using one digital identity.
LoginRadius supports standard SSO protocols like SAML, JWT, OAuth 2.0, OpenID Connect (OIDC), and Web Services Federation. The IAM platform offers a simple dashboard to manage all configurations required for these protocols.
-
User management: LoginRadius offers complete user management features, including:
-
Authorization: To validate the access rights of users.
-
Provisioning: To create user accounts.
-
Deprovisioning: To block, or delete user accounts.
-
Account Management: To disable user accounts, and grant, or restrict access.
-
Password Management: To trigger the password reset option for user accounts.
-
Compliance with privacy regulations: The LoginRadius Identity Platform handles consent management by ensuring continued compliance with all major privacy regulations, including the GDPR of the EU and the CCPA of California.
Conclusion
Powerful identity and access management solutions offer the right tools to ensure users can engage with enterprises at any time, from any device, securely. Organizations will need to rethink their business and operating models.
There is a huge demand to invest in new digital methods of communication. And prioritizing digital security will go a long way.

Featured Posts
Building Community Beyond Borders: Our Thailand Story
1FA vs 2FA vs MFA: Which Method Secures You Best?
B2B IAM Best Practices and Architecture Guide
Adding Partner IAM With LoginRadius: A Complete Guide to B2B Identity Management
What is User Authentication, and Why is it Important?
What is Partner IAM / B2B IAM - A Complete Guide
Still Bending Workforce IAM for Your B2B Networks? Introducing LoginRadius Partner IAM—Built from the Ground Up
What is Biometric Authentication and How It's Changing Login
Location-Based Data Residency Boosts Trust and Conversions
The Impact of AI on Cybersecurity
PINs vs Passwords: Which is More Secure?
Why Canadian Data Centers Lead in Privacy-First Hosting
Passkeys vs Passwords: The Upgrade Your Security Needs
What is the Best Way to Authenticate Users?
Canada as a Global Hub for Privacy-First CIAM Platforms
How to Choose a Strong Password- A Quick Guide
A Complete Guide to Device Authentication Methods
What is a One-Time Password (OTP) ? – A Complete Guide
A Quick Guide to Username and Password Authentication
Types of Authentication and Identity Verification
What is Strong Authentication in Cybersecurity?
Top 9 User Authentication Methods to Stay Secure in 2025
Authentication vs Authorization: What's the Difference?
Guide to Authentication Methods & Choosing the Right One
Identification and Authentication: A Quick Comparison
Understanding Authentication, Authorization, and Encryption
Introducing the LoginRadius Trust Center: Always Up-to-Date and at Your Fingertips
What is Token Authentication and How Does It Work?
What is OTP Authentication and How Does it Work?
What is Role-Based Access Control (RBAC)?
LoginRadius Launches Next-Generation CIAM Console: Self-Serve, No-Code, and Built for Speed
Quick Guide to Single-factor, Two-factor, and Multi-factor Authentication
Democratizing Authentication: Introducing LoginRadius' Free Forever Developer Plan
Mobile Authentication: Everything You Need to Know
What is Push Notification Authentication and How It Works?
Code Less, Build More: Unveiling LoginRadius' AI-Powered Developer Documentation
Types of Multi Factor Authentication & How to Pick the Best
Risk-Based Authentication vs. MFA: Key Differences Explained
Revamped & Ready: Introducing the New Developer-First LoginRadius Website
What is SCIM? A Developer's Guide to Understanding and Using SCIM
RBAC vs ABAC: A Developer’s Guide to Choosing the Right Fit
CISOs’ Top Cybersecurity Threats 2025: Scattered Spider, Deepfakes, and More
LoginRadius 2024: A Year of CIAM Innovations
What is Passkey Authentication - A Complete Guide
How AI-Enabled Cybersecurity Solutions Are Strengthening Our Online Security
What is Identity Orchestration
LoginRadius Releases 2024 Consumer Identity Report, Highlights the Shifting Trends in Consumer Preferences
Celebrating 8th Year Milestone: How Our Collaboration with a Leading Healthcare Company Transformed Millions of Lives
Unlock Your Digital Freedom: How Automating Passwordless Authentication Can Transform Your Security
How To Secure GenAI by Implementing RBAC In The Enterprise
The Hidden Pitfalls: Why Most CIAM Systems Fail Under Pressure
No More Login Hassles: Effortless Migration to LoginRadius Awaits
How Cookie Management Supports GDPR and CCPA Compliance
LoginRadius Launches Identity Orchestration for Seamless Identity Workflows
Passkeys: Unlocking Benefits for a Better Online Shopping Experience
AI and the Changing Face of Enterprise Security Threats
Leading the Charge in Customer IAM: LoginRadius Recognized as an Overall Leader by KuppingerCole
Gearing Up for Better Customer Experiences? Choose No-Code Identity Orchestration
Announcement - LoginRadius Launches PassKeys to Redefine Authentication Security and User Experience
Decoding the Rise of Zero-Trust Adoption in Government Sector
Say Goodbye to Passwords: How Passkeys Are Reinventing Online Security
Announcement - LoginRadius Unveils the Future of Authentication with Push Notification MFA
Is Your CIAM Adapting to Global Needs? 6 Key Areas to Win Privacy-Concerned Customers
The Growing Threat of Identity-Based Attacks and the Need for an Advanced Identity Security Approach
How AI Is Changing the Game in User Authentication
eIDAS 2.0: The Digital Revolution Is Here – Is Your Business Ready to Comply?
A Quick Guide To Choosing The Right Zero Trust Vendor
Cloud Security Governance: Protecting Assets in the Digital Frontier
What is Silver SAML Vulnerability and How Can We Protect Our Digital Identities?
Identity Security for Device Trust: Navigating 2024 & Beyond
Exciting Leadership Updates Amid Strategic Growth at LoginRadius
From Past to Present: User Authentication's Evolution and Challenges
How Does Multi-Tenancy in Customer IAM Solutions Boost Security?
How No/Low Code CIAM Balances Security and User Engagement?
Beyond Passwords: Navigating Tomorrow's Authentication Landscape
How does identity management address the top 5 security challenges in B2B SaaS?
Reinforcing Security with Advanced Risk-Based Authentication in 2024 & Beyond
2FA vs MFA: Understanding the Differences
Okta Token Theft Implicated in Cloudflare's Security Breach
Voice OTP by LoginRadius: Revolutionizing Secure and Seamless User Authentication
Which is Safer: Biometric or Password?
7 Reasons to Use Biometric Authentication for Multi-Factor Authentication
Exploring Digital Identity Verification with Effective Crucial Data Checks
5 Reasons Why LoginRadius Leads the Way in the CIAM Landscape in 2024 & Beyond
Above the Horizon: Exploring the Power of a Strong Cloud Identity Platform
Streamlining Authentication: Elevate User Experience with LoginRadius AutoLookup
A Journey Through Our Top 10 Blogs from 2023
Now and Beyond- Staying Ahead with the 10 Key Cybersecurity Trends of 2024
B2B SaaS SSO Login: Exploring Enterprise Considerations in 2024
Securing Corporate Applications: A Comprehensive Guide to Enterprise Application Security
Strengthening Security Measures: The Role of Two-Factor Authentication (2FA)
Securing the Throne: Privileged Access Management (PAM) Best Practices Unveiled
7 Common Authentication Vulnerabilities to Steer Clear of
What is Identity Lifecycle Management?
Strengthening Security and Compliance: The Role of Identity Governance
Understanding the Okta Hack: Breach in Customer Support and Lessons for Organizations
Managing Generative AI Security Risks in the Enterprise- A Quick Guide
Empowering Your Security: Exploring the Advantages of Time-Based One-Time Passwords (TOTP)
The Future of Personalization: Embracing Zero-Party Data
Comprehensive Guide to Flexible CIAM Deployment Options with LoginRadius
Small Steps, Big Shields: Navigating Cybersecurity Awareness Month 2023 Safely
Streamlining Access with Converged Identity Platforms
How Retailers Can Balance Privacy While Foiling Thieves
The Power of No-code Customer IAM in Reducing Churn
CIAM: Enhancing Security & Building Consumer Trust-All At Once
Maintaining Trust: Customer Identity Verification Challenges & Best Practices
Unlocking Smartphone Security: How to Hackproof Your Smartphone
Phishing-Resistant MFA Login for Mobile Applications: Strategies and Challenges
True Passwordless Authentication: Stronger Defense Against Cyberattacks
Identity Governance vs. Identity Management: Navigating the Differences
Navigating Identity Verification Challenges in Regulated Industries: 7 Effective Solutions
Enhancing Security: Leveraging 5 Real-Time Techniques to Detect Phishing Attacks
A Comprehensive Guide to the Five A's of Cloud Identity Management
Understanding the Difference Between Identity Access Management On-Premise and Cloud
Learn the Impact of Identity Theft on Businesses in 2023
LDAP Authentication: Meaning and How it Works?
7 Things Your Security Team Need To Know Before Creating A CIAM Strategy
Choosing Between Self-Managed and Service-Based SSO Solutions: A Comprehensive Comparison
What is Cloud Identity and its Benefits?
The Legal Implications of SSO: Privacy, Security, and Compliance
Data Privacy Laws for 2023: A Closer Look at 9 Key Regulations
4 Reasons Why SSO Integrations Are a Must-Have For Online Businesses
Consumer vs. Enterprise: Navigating the Dual Nature of Digital Identity
LoginRadius Releases Consumer Identity Trend Report 2023, Highlights The Future of Customer Identity
What is a Password Vault and How Does it Work?
How a Culture of Identity Governance Empowers Digital Transformation?
Securing the Digital Frontier: The Power of AI in Next-Gen CIAM
Replatforming 101: Everything You Need to Know
Best Practices for Username and Password Authentication
The Ultimate Guide to Choosing the Right CIAM Solution
How to Use Identity Management at Every Stage of the Customer Journey?
Protecting Your Cloud Data: The Power of SaaS Security and IAM Governance
The Rise of Account Creation Fraud: What You Need to Know
Why Direct-to-Consumer (D2C) Businesses Must Take A Strategic Approach To CIAM?
What are Self-Sovereign Identities?
7 Uncommon Cyber Attacks in 2023: Why Your Organization Needs To Be Ready For The Worst-Case Scenarios
Identity Modernization: What Is It & Why Should You Care?
A Lot Can Happen In The Cloud: Multi-Cloud Environment and its Optimization Challenges
Can Security and User Experience Co-Exist in the Authenticating and Authorizing Space?
Business On The Move: How Just-in-Time Migrations Are Making Smooth CIAM Transitions
3 Digital Onboarding Trends To Watch In 2023 (And What You Can Do About It Now)
A Look Back At Our 20 Top Performing Blogs in 2022
6 Tips to Prevent Accidental Data Exposure Within Your Company
Top Priorities for Customer IAM Leaders in 2023 and How to Prepare
Electronic Theatre Controls: A LoginRadius Customer Success Story
Distributed Multi-Cloud Identity Management and Its Endless Business Benefits
How The Age Of Smart Credentials Is Rewriting The Rules For Physical Verification?
Incident Response Vs. Disaster Recovery: What’s The Difference and Which Do You Need?
10 Ways To Keep Your Business Safe On Black Friday and Cyber Monday
The Customer Experience is About to Get Even Better With Passive Authentication
What is Dynamic Authorization & Why Does it Matter?
What’s the Difference Between Attack Surface and Attack Vector?
How Identity-Based Access Ensures Robust Infrastructure Security Amidst the Growing Identity Crisis?
2FA Bypass Attacks- Everything You Should Know
IAM vs. Customer IAM: Understanding the Role of CIAM in Accelerating Business Growth
Why MFA Fatigue Attacks May Soon Be Your Worst Nightmare?
InfoSec Director, Alok Patidar Answers Your Most Difficult Questions on Cybersecurity
Understanding MITRE ATT&CK Framework?
Identity Fabric vs. Zero Trust: Is One a Better Alternative Than The Other?
The Role of Customer Identity Management in IoT Security: How It's a Must!
Securing Centralized Access Without Compromising User Experience
User Authentication in the Metaverse: What’s Changing?
LoginRadius Celebrates National Cybersecurity Month 2022 - Here’s Everything You Should Know
Public Cloud Risks - Is Your Organization Prepared for Cloud Threats?
What Brands Need to Know for Building the Future of Data Compliance?
Okta Identity Credentials on the Radar of Oktapus Phishing Campaign
BC Municipality Digitizes its Citizen Services. LoginRadius Brings Identity to the Table.
The Role of Customer Authentication in Paving the Way for Digital Agility
What Brands Need to Know for Building the Future of Data Compliance?
6 Alternative Authentication Methods For Your Online Customers
Implementing Zero Trust? Make Sure You're Doing It Correctly
What is Federated SSO (Single Sign-On)?
MFA Prompt Bombing: Is it a New Threat Vector to Worry About?
Privacy-Centric Enhancements: CEO Rakesh Soni Shares His Thoughts on Shifting Data Strategies
The Role of Identity Management in Securing Your Citizen’s Data
Why is Data Privacy an Immediate Enterprise Priority?
What is Out-of-Band Authentication?
How Can Enterprises Use SSO to Boost Data Collection?
Why Your Business Needs A Simple Passwordless Experience (Minus the User Friction)
Will Apple’s ‘Lockdown Mode’ Reduce State-Sponsored Attacks?
Authentication, Identity Verification, and Identification: What's the Difference
IoT Botnet Attacks: Are They the Next Big Threat to Enterprises?
Skiperformance - a LoginRadius Customer Success Story
Cross-Device Authentication and Tracking: The Opportunities and Underlying Privacy Risks
How Identity Modernization Will Thrive Business Success in 2022 and Beyond
The Pros & Cons of Reusable Digital Identity: What You Need To Know
What is Cloud Security and How it Works?
Age of No-Code Technologies: Identification and Authentication
SSO vs. Social Login: What’s the Difference? [Infographic]
Planning a Digital Makeover For Your Business? LoginRadius CIAM Can Help!
What is Cloud Computing?
Authentication vs Login - What’s the Difference?
How a Simple Password Reset Can Ruin Your Customer's Experience
GovTech is On The Rise: How Can This Technology Improve Government Services?
5 Access Management Best Practices and Benefits For Businesses
LoginRadius Releases Consumer Identity Trend Report 2022, Key Login Methods Highlighted
BITB Attacks: The New Destructive Phishing Technique
5 Reasons Why You Need to Strengthen Your Identity Authentication
What is the Difference Between MFA vs. SSO?
What is Login Authentication?
5 Ways to Improve Your Customer Verification Process
5 Myths About Phishing You Should Know
4 Common Security Issues Found In Password-Based Login
Personal Information and PII - What’s the Difference?
OTT Platforms and CIAM: How Identity Management Ensures Millions of Viewers to Scale with Ease
Is the Rise of Machine Identity Posing a Threat to Enterprise Security?
LoginRadius Integrates Search in Navigation for Better Customer Experience
5 Privacy Threats in Social Media You Should Know in 2022
Importance of Multi-factor Authentication for SSO
How LoginRadius Creates a Perfect Harmony of UX and Security
Smart Cities and Cyber Security Trends to Watch Out in 2022
Harry Rosen, a LoginRadius Customer Success Story
Top 7 Security Tips from LoginRadius’ Cybersecurity Expert to Follow in 2023
Top 7 Security Tips from LoginRadius’ Cybersecurity Expert to Follow in 2023
This Is How Scammers Get Your Email Address & How to Stop Them
Will Decentralized Auth Change the Perception of Consumer Identities in 2022?
Emerging Threat of Deepfakes: How To Identify And Prepare Against It
Everything You Need to Know Before Buying Cyber Insurance in 2022
5 Challenges for Government Adoption of Citizens’ Access Control
Are You Thinking of Token Management for Your API Product? Think about JWT!
Top 10 Performing Identity Blogs in 2021
LoginRadius Launches M2M Authorization for Seamless Business Operations
LoginRadius Offers PerfectMind Integration for a Seamless UX
Take Control of Your CIAM Environment with LoginRadius' Private Cloud
10 Tips From CIAM Experts to Reduce the Attack Surface of User Authentication
Why You Should Use Open Source Project For Your Business
How LoginRadius Webhook Allows You to Sync Your Data in Real-Time
17 Tips to Avoid Shopping Scams on Black Friday & Cyber Monday
Federated Identity Management vs. SSO: What's The Difference?
How to Evaluate the Quality of Your User Authentication System
How LoginRadius Offers Customer-Centric Capabilities that Drive ROI
How to Mitigate BGP Attacks and Secure Your User's Data
3 Best Stages of IT Security for Implementing Gartner's CARTA
How to Choose the Right User Authentication Option for your Product
An Introduction to Financial-Grade API (FAPI) for Open Banking
Why is PKI The Future of Secure Communications
How to Find the Right SSO Strategy that Fits Your Business
Cybersecurity Best Practices for Businesses in 2023 & Beyond [Infographic]
SSO Integration: How to Secure the Customer Experience on Loyalty Platforms
The Top 5 Trends in CIAM We’ve Watched in 2021
The Major Challenges of Customer Identification in the Retail Industry
Cybersecurity Awareness Month: Predicting the Deadliest Cyber Attacks in 2022
LoginRadius Delivers a Seamless User Experience that Increases Conversions through Enhanced Progressive Profiling
Avoid these Common Mistakes When Dealing with Data Breaches
Tiroler Tageszeitung (TT), a LoginRadius Customer Success Story
What are Security Keys? What are its Advantages?
Everything You Need to Know About OAuth and How it Works
Decentralized Authentication: What Is It And How It Is Changing the Industry
Getting Started with OpenID Connect
Discover the Benefits of Re-Authentication for Enhanced Security
Stand Out from the Crowd: Improve Your Customer Support with CIAM
Why Should You be Customizing Your Identity System to Your Needs
SMS Authentication — Can it Really Protect Your Business?
How Poor Login Concurrency can Impact OTT Platforms' Business
A Comprehensive Guide to Privileged Access Management (PAM)
How Cities Can Improve Civilians’ Digital Experience with Unified Identity
Refresh Tokens: When to Use Them and How They Interact with JWTs
How Progressive Disclosure Makes Your User's Onboarding Easy
What is Digital Identity Verification and Why is it Necessary?
How OTT Services can Simplify Authentication on Various Devices
A Beginner's Guide to Zero Trust Security Model
What is Identity Security?
What is a Token? What are its Pros and Cons?
How to Scale Your Business Quickly with Identity Management
How to Manage Situation After a Data Breach
How to Strike the Right Balance Between Security and Consumer Experience
How NIST is Changing Password Creation in 2021
COVID-19 and Beyond: 5 Risk Management Essentials for Your Enterprise
How WebAuth Secures Your Users’ Login
Adaptive Authentication- Is it the Next Breakthrough in Customer Authentication?
The Rise of BYOI (Bring your own Identity)
Understanding PII Compliance: A Key to Enterprise Data Security
Cyber Security Round-Up: What Happened in June 2021
How Businesses are Experiencing Digital Transformation with Consumer IAM
What is SAML SSO?
LoginRadius Offers Additional Security Layer through Newly-Enhanced Step-up Authentication Feature
Why Big Merchants Need to Deliver a Unified Consumer Experience?
All About Google One Tap Login—Explained!
What to Do if Someone Steals Your JSON Web Token?
What is Web SSO
Working With Industry Authorization: A Beginner's Guide to OAuth 2.0
Password History, Expiration, and Complexity: Explained!
SAML or OIDC: Which is Better For Your Business?
10 Reasons For Businesses to Implement SASE with a Zero Trust Strategy
Move beyond Traditional Risk Management with Holistic APIs
Identity Provider: What Is It And Why Should You Invest In One?
What is User Session Management?
How Entertainment Companies Use the LoginRadius CIAM platform
Consumer Data Protection: How to Handle Data Breaches in Your Business
Top 5 User Provisioning Mistakes Enterprises Should Avoid in 2021
How Secure is Two-Factor Authentication (2FA)?
The Changing Role of Identity Management in Enterprise Decision-Making
5 Reasons Why Cloud Governance Matters For Your Business
Implementing Effective Social Authentication Solution with LoginRadius
The Future of Authentication is Passwordless With Magic links
Handling Scalability and Enhancing Security with LoginRadius
Maintaining Quality Data Security Practices
Introduction to Mobile Biometric Authentication
Data Security in Hospitality: Best Practices for Operating In a Post-COVID Era
The Role of Identity management in the media industry
A Detailed Guide on How UX/UI Affects Registration
What Is a Salt and How Does It Boost Security?
Login Using Microsoft Account
A Detail Guide to Consent Management and Processing Data
Workflow Automation- What is it and Why Do You Need It?
How Companies can Enable Account security for their Consumers
What is Progressive Profiling and How it Works?
Password Spraying: What Is It And How To Prevent It?
5 Tips to Prevent OAuth Authentication Vulnerabilities
Calculating ROI, Build vs Buy (Part 1)
Identity Theft Frauds- Staying Ahead in 2021
What is privacy compliance and why is it so important?
What is Authentication? Definition and How It Works
What are Federated Identity Providers?
Login with Google Apps
What is Passwordless Login?
What is Standard Login
IoT authentication in the airline industry
Announcement - Authentication API Analytics to Evaluate the Performance of LoginRadius APIs for Your Applications
Multi-Factor Authentication - A Beginner’s Guide
Single Sign-On- A Beginner’s Guide
Top 10 Cybersecurity Predictions for 2021 That SMBs Must Know
How to Put Yourself In Control of Your Data by Leveraging LoginRadius' SSO
What Is User Management?
How CIAM Will Address The 5 Most Popular Issues In The Utility Industry
CIAM Continues to Draw Attention as Okta acquires Auth0
Protecting a Unified Cloud Platform through Cloud Security Management
What is Continuous Authentication
What is Brute Force Attack
What is the Power of PIN Authentication Security?
What is Risk-Based Authentication (RBA)?
Understanding the Difference Between Single-Tenant and Multi-Tenant Cloud [Infographic]
What is Phone Login
Why Organizations Must Use API-Driven CIAM for Digital Agility
Why Do Consumers Prefer Social Login [Infographic]
5 Best Practices of Implementing Business Resilience during a Data Breach
What is Broken Authentication Vulnerability and How to Prevent It?
Announcement - LoginRadius Introduces Convenient and Secure Biometric Authentication for Mobile Apps
6 Strategies to Secure Your Cloud Operations Against Today's Cyber Threats
Announcement - LoginRadius Introduces Password Policy to Ensure Best Practices for Businesses and Consumers
How Is New Age Ciam Revolutionizing Consumer Experience?
What is Federated Identity Management
7 Common Web Application Security Threats
Identity Management in Cloud Computing
What is Identity and Access Management (IAM)?
Announcement - LoginRadius Announces Identity Brokering To Establish Trust Between Identity and Service Providers
5 Ways User Onboarding Software Can Revamp Your Application
How to secure an email address on your website
What is Formjacking
DNS Cache Poisoning: Why Is It Dangerous for Your Business
How to Set Up Two-factor Authentication on All Your Online Accounts?
What is Digital Transformation
The Do's and Don'ts of Choosing a Secure Password
How To Secure Your Contact Form From Bot Attacks
What is Identity Proofing and Why is it Important?
What is Identity Governance & Administration?
Announcement: LoginRadius Embraces Privacy Policy Management Amid Heightened Regulatory Updates
Login Security: 7 Best Practice to Keep Your Online Accounts Secure
9 Data Security Best Practices For your Business
How To Make Sure Your Phone Isn’t Hacked
Safe Data Act: A New Privacy Law in the Town
Email is Hacked!: 7 Immediate Steps To Follow
Announcement - LoginRadius Smart and IoT Authentication to Offer Hassle-Free Login for Input-Constrained Devices
Announcement - LoginRadius Announces Authentication and SSO for Native Mobile Apps
9 Identity and Access Management Best Practices for 2021
E-commerce Security: 5 Ways to Enhance Data Protection During the Shopping Season
Identity Management in Healthcare: Analyzing the Industry Needs
Identity Management for Developers: Why it's required more than ever
Announcement - LoginRadius Launches Passwordless Login with Magic Link or OTP, Keeps Barriers Low During Registration and Login
Announcement - LoginRadius Simplifies the Implementation of Federated SSO With Federated Identity Management
Best IDaaS Provider - Why Loginradius is Considered as the Best IDaaS Solution
Social Engineering Attacks: Prevention and Best Practices [Infographic]
Announcement – LoginRadius Announces the Availability of User Management
Consumer Identity Management for the CMO, CISO, and CIO
Announcement - LoginRadius Delivers Exceptional Authentication With The Launch Of Identity Experience Framework
Best SSO Provider: Why LoginRadius Is Considered As The Best SSO Solution
Single-Page Applications: Building A Secure Login Pathway with LoginRadius
LoginRadius Releases Consumer Digital Identity Trend Report 2020
Securing Enterprise Mobile Apps with LoginRadius
Data Governance Best Practices for Enterprises
Top 10 Benefits of Multi-Factor Authentication (MFA)
Build vs Buy: Securing Customer Identity with Loginradius
LoginRadius Identity Import Manager, An Automated Feature for Seamless Data Migration
Why Identity Management for Education Sector has Become Crucial
LoginRadius Approves Consumer Audit Trail for In-Depth Data Analysis and Risk Assessment
Online Casino and Gambling Industry Is Gaining Momentum, So Is the Cyber Threat
How LoginRadius Future-Proofs Consumer Data Privacy and Security
Authentication and Authorization Defined: What's the Difference? [Infographic]
LoginRadius Launches Consent Management to Support the EU's GDPR Compliance
Streaming Applications: How to Secure Your Customer Data
Protecting Organization From Cyber-Threats: Business at Risk During COVID-19
Announcement - LoginRadius China CIAM for Businesses to Benefit From Its Lucrative Market
Why Financial Industry Needs an Identity Management System Now More Than Ever
Announcement - LoginRadius Now Supports PIN Login with Enhanced Features
LoginRadius Bans Video Conferencing App ‘Zoom’ Over Security Concerns
Corporate Account Takeover Attacks: Detecting and Preventing it
Marriott Data Breach 2020: 5.2 Million Guest Records Were Stolen
How LoginRadius Help Retail and E-commerce Industry to Manage Customer Identities
Announcing New Look of LoginRadius
LoginRadius Announces Its Business Continuity Plan to Fight COVID-19 Outbreak
Unlock the Future of Smart Cities
How LoginRadius Helps Enterprises Stay CCPA Compliant in 2020
What is Social Login?
Identity as a Service (IDAAS): Managing Digital Identities (Updated)
The Worst Passwords of 2019
Digital Privacy: Securing Consumer Privacy with LoginRadius
One World Identity Report Names LoginRadius a Customer Identity and Access Management (CIAM) Industry Leader
7 Benefits of Single Sign-On (SSO) and Why Your Business Needs It
Cloud Security Challenges Today: Expert Advice on Keeping your Business Safe
The Role of Passwordless Authentication in Securing Digital Identity
LoginRadius presents at KuppingerCole Consumer Identity World
Digital Identity Management: 5 Ways to Win Customer Trust
CCPA vs GDPR: Global Compliance Guide [Infographic]
Credential Stuffing: How To Detect And Prevent It
A History of Human Identity in Pictures Part 3
A History of Human Identity in Pictures Part 2
A History of Human Identity in Pictures - Part 1
What is Multi Factor Authentication (MFA) and How does it Work?
Why LoginRadius Is the Best Akamai Identity Cloud (Janrain) Alternative
5 Reasons To Know Why B2C Enterprises Should Use Single Sign-On
8 Key Components of a Perfect CIAM Platform
What is Customer Identity and Access Management(CIAM)?
What is Single Sign-On (SSO) and How it Works?
California's CCPA 2.0 Passed: Everything You Need to Know About the New CPRA
IAM vs. CIAM: Which Solution is Right For You?
Looking for a Gigya Alternative? Try LoginRadius, a Superior and Modern Identity Platform
Presenting: Progressive Profiling from LoginRadius
Best Practices for Choosing Good Security Questions
How Do I Know If My Email Has Been Leaked in a Data Breach?
The Death of Passwords [Infographic]
How to Use Multi-Factor Authentication When You Don’t Have Cell Phone Access
The Customer Identity Infrastructure that Cruise Line Passengers Don’t See
Why Your Enterprise Needs a Digital Business Transformation Strategy
Reconsidering Social Login from a Security and Privacy Angle
Improving Customer Experience in the Public Sector
Customer Spotlight - Hydro Ottawa
Digital Transformation: Safeguarding the Customer Experience
Rede Gazeta, a LoginRadius Customer Success Story
4 Barriers to Building a Digital Business and How to Overcome Them
LoginRadius Announces $17M Series A Funding from ForgePoint and Microsoft
BroadcastMed, a LoginRadius Customer Success Story
Why Municipalities Are Investing in Citizen Engagement
Customer Experience is Driving Digital Transformation
Identity Fraud Hits All-Time High in 2017
Phishing Attacks: How to Identify & Avoid Phishing Scams
IFMA, a LoginRadius Customer Success Story
Canada To Fine Companies For Not Reporting Data Breaches
Mapegy, a LoginRadius Customer Success Story
Aurora WDC, a LoginRadius Customer Success Story
IOM X, a LoginRadius Customer Success Story
Customer Identity Preference Trends Q2 2016
Customer Identity Preference Trends Q1 2016

