Introduction
In today's interconnected digital world, enterprises increasingly depend on third-party partners, vendors, and affiliates to deliver services and drive growth. This growing ecosystem demands secure, scalable, and efficient access controls. Partner Identity and Access Management (Partner IAM) provides the foundation for managing partner identities securely.
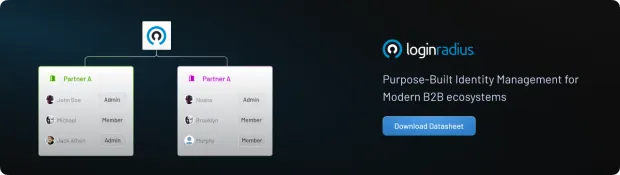
One of the most transformative elements of Partner IAM is delegated administration—a model where enterprises grant external users limited administrative rights to manage their own teams and resources.
As digital collaboration deepens, delegated access has become essential for efficiently managing B2B identity. By enabling this model, enterprises empower partners to act quickly, securely, and in alignment with their operational needs.
This blog explores the fundamental best practices, strategic architecture considerations, and how LoginRadius equips businesses with powerful tools to implement a scalable, secure, and auditable delegated administration structure tailored for Partner IAM.
What is Delegated Administration in the Context of Partner IAM?
Partner IAM (also known as B2B IAM) is the process of enabling secure access management for external business entities like partners, vendors, suppliers, and affiliates.
Delegated administration plays a key role in this model by empowering these external users to manage their own internal users, roles, and permissions—without needing constant support from the core enterprise IT team.
This model solves core challenges in identity and access management such as:
-
Securely scaling user access across different external organizations
-
Managing complex hierarchies of roles and permissions
-
Enabling flexible integration with various identity providers (like SAML, OAuth, and OpenID Connect)
-
Enforcing compliance with industry standards like GDPR and SOC 2
Unlike traditional internal IAM - where employees are the primary user base—Partner IAM supports multi-tenant architectures and external organizational boundaries. It introduces the need for tools that can dynamically manage users, assign roles per organization, and customize access experiences at the partner level.
Examples include:
-
A SaaS platform enabling client admins to manage their own accounts and users within separate tenants.
-
A retail enterprise onboarding suppliers and franchisees who manage local staff and require custom login portals, unique permissions, and SSO integrations.
-
A pharmaceutical company managing distributors across regions, each with dedicated roles and branded login pages.
Delegated administration allows companies to strike the perfect balance between security, scalability, and autonomy.
It is a defining characteristic of modern consumer identity and access management (CIAM)—especially for B2B-focused platforms. Platforms like LoginRadius lead in this space by offering robust delegation, seamless federation, and adaptive authentication under one roof.
Why Delegated Admin is Critical for Partner IAM
The benefits of delegated administration extend beyond convenience. It’s a strategic necessity for B2B operations:
Scalability
With an ever-expanding partner network, manually provisioning users is impractical. Delegated admin allows partners to manage their own user base, significantly reducing IT workload.
For instance, a global enterprise working with 200+ resellers would otherwise need an army of IT personnel to handle daily user management. Delegation solves this by distributing responsibilities across the network.
Agility
Delegated access means partners can respond quickly to their business needs, such as onboarding new employees or adjusting access levels.
This flexibility enhances partner satisfaction and speeds time-to-value. A regional distributor can grant access to new sales staff instantly, ensuring productivity from day one.
Security
Delegated models support the principle of least privilege, ensuring users only access what they need. Combined with role-based access control (RBAC) and multi factor authentification, this approach minimizes attack surfaces.
LoginRadius supports adaptive security measures that dynamically adjust access based on risk factors, keeping systems safe.
Compliance
Organizations can maintain centralized audit trails, access reviews, and enforce approval workflows, aligning with regulatory mandates such as GDPR, HIPAA, and SOC 2. Delegated admin ensures actions taken by external users are documented and monitored—a vital feature for compliance-conscious enterprises.
A strong delegated admin model supports B2B SSO, federated identity, and secure access controls—all foundational elements for CIAM providers and essential to robust CIAM authentication.
Key Best Practices for Delegated Access in B2B Identity
As organizations scale their partner ecosystems, maintaining control while empowering third-party users becomes critical. Delegated administration, when left unstructured, can lead to compliance gaps, security vulnerabilities, and operational inefficiencies. That’s why it’s essential to follow a set of proven, practical best practices to govern how access is assigned, monitored, and revoked.
These practices ensure that while partners gain the autonomy they need, your enterprise retains full visibility, security, and compliance. Below are foundational strategies to help you strike this balance effectively:
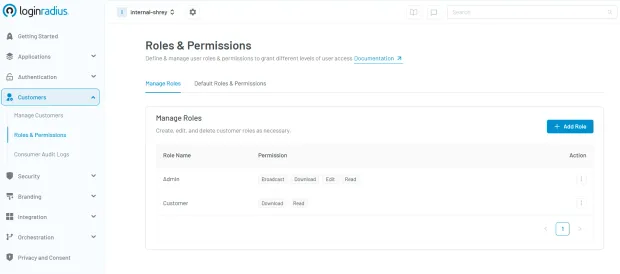
Use Role-Based Access Control (RBAC)
Implementing Role-Based Access Control (RBAC) is foundational in building a secure and scalable Partner IAM strategy. By assigning specific roles (ex: Admin, Manager, or Viewer) to users based on their responsibilities, you prevent the common pitfall of over-permissioning, where users have more access than necessary, often leading to compliance and security risks.
In the context of Partner IAM, RBAC ensures that external users can perform only those actions relevant to their job function.
For instance, a regional partner’s HR representative might be authorized to add or deactivate users, while their marketing manager may only access campaign analytics. This granular control not only enhances operational clarity but also reinforces the principle of least privilege.
To understand how RBAC fits within a broader identity management strategy and why it's critical for organizations that leverage delegated access, check out our comprehensive guide: What is Role-Based Access Control (RBAC)? The blog explores real-world scenarios and best practices, demonstrating how LoginRadius empowers organizations to implement RBAC with precision and flexibility.
Whether you're securing a handful of partner logins or managing thousands of external users, RBAC—when implemented via LoginRadius—provides the structure and simplicity needed to stay in control. Here’s how easy it is to implement RBAC through the LoginRadius admin console:
Implement Organizational Units or Tenants
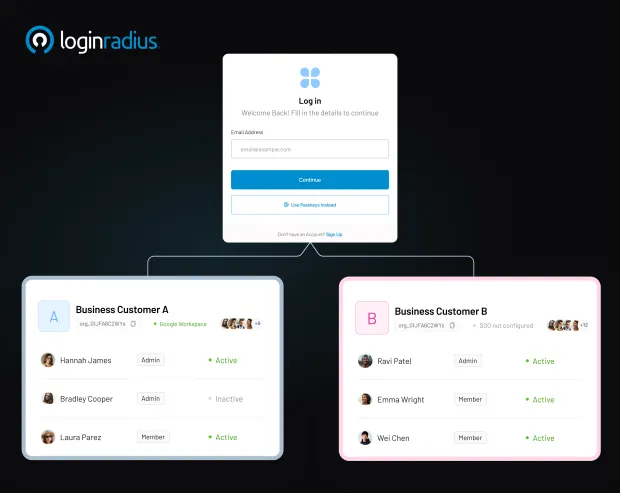
Organizing partner users into logical groups or “tenants” is essential—it ensures both data isolation and clean access boundaries across partner ecosystems.
This practice is particularly valuable in Partner IAM solutions, which often serve hundreds of partner organizations, each needing separate access, user data, and governance.
With multi-tenant architecture, LoginRadius provides a single instance of the Identity Platform that serves multiple clients, each with its own separate database and API routing layer—keeping user data and logs siloed per partner while sharing the underlying infrastructure.
This approach offers an excellent balance between cost-efficiency and secure compartmentalization, ideal for fast-growing enterprises managing diverse partner types.
For higher security demands, private or single-tenant cloud deployments allow complete isolation. Each partner operates in its own dedicated environment, which supports compliance-heavy use cases like healthcare or finance where data sovereignty and customization are critical.
Why this matters:
-
Security : No cross-tenant data leakage risks.
-
Compliance : Easier to enforce jurisdictional policies and audit trails.
-
Scalability : Add new partners without architectural overhauls.
Example: A SaaS provider onboarding ten international distributors can use multi-tenancy to isolate data per distributor. If one tenant experiences an incident, others remain unaffected, ensuring resilience.
This architecture enhances agility and governance, making it a pillar of secure, scalable partner identity and access management (IAM) and B2B identity management. Learn more about tenant management in LoginRadius. Also, you can download this insightful datasheet to understand more about LoginRadius Partner IAM:
Enable Just-In-Time (JIT) Provisioning
With JIT provisioning, accounts are automatically created upon a partner’s first login using federated single sign-on (SSO). This simplifies onboarding and enhances the user experience. Imagine a new vendor associate accessing a portal for the first time—LoginRadius ensures their account is securely generated on the fly.
Maintain Centralized Governance with Local Autonomy
Balance is key: allow partner admins autonomy within their scope, while maintaining centralized oversight through logs, approvals, and exception handling. LoginRadius supports unified dashboards for governance without micromanaging partner activities.
Ensure Lifecycle Management
Automate user deactivation based on inactivity, contract expiry, or internal triggers. Implement periodic access reviews and re-certification processes to maintain hygiene. Integrating these workflows avoids orphan accounts and ensures timely updates to access rights.
Need help setting this up? Explore LoginRadius’s delegated user management documentation.
Technical Architecture for Partner IAM with Delegated Admin
A robust Partner IAM architecture integrates seamlessly with existing identity ecosystems. Here's how:
Core Components
-
Identity Provider (IdP) : LoginRadius or a third-party IdP managing authentication.
-
Partner Portals : Interfaces used by partners to access and manage users.
-
Federated Identity Protocols : SAML, OIDC for B2B authentication and secure trust setup.
-
SCIM APIs : For user provisioning and de-provisioning.
Identity Provider (IdP) : The IdP is responsible for authenticating users and issuing identity tokens. This can be a provider like LoginRadius, which offers built-in, secure CIAM capabilities, or a third-party IdP that supports standards like SAML and OpenID Connect. The IdP validates credentials and provides identity assertions during Single Sign-On (SSO), forming the backbone of trust in a B2B IAM architecture.
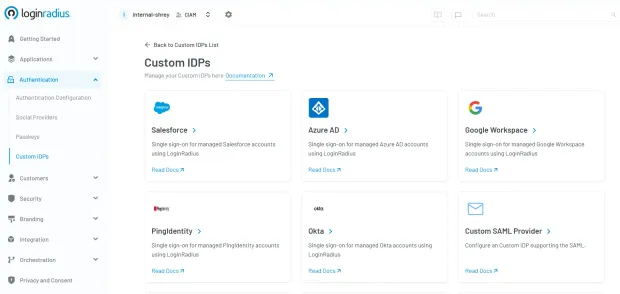
Partner Portals : These are web or mobile interfaces provided to external organizations—such as distributors, vendors, or resellers—where they can log in, manage users, configure roles, and access partner-specific resources. With LoginRadius, these portals can be fully branded and customized to reflect each partner's identity, delivering a seamless and familiar experience.
Federated Identity Protocols : Protocols like SAML (Security Assertion Markup Language) and OIDC (OpenID Connect) enable federated identity between your organization and partner companies. These standards allow partners to authenticate via their own identity systems while accessing your resources, ensuring B2B authentication is both secure and user-friendly.
SCIM APIs : System for Cross-domain Identity Management (SCIM) APIs are used to automate user provisioning and de-provisioning. This ensures that when a partner adds, updates, or removes users from their own directory, the changes are instantly reflected in your system—keeping data synchronized and secure without manual intervention.
Architecture Flow
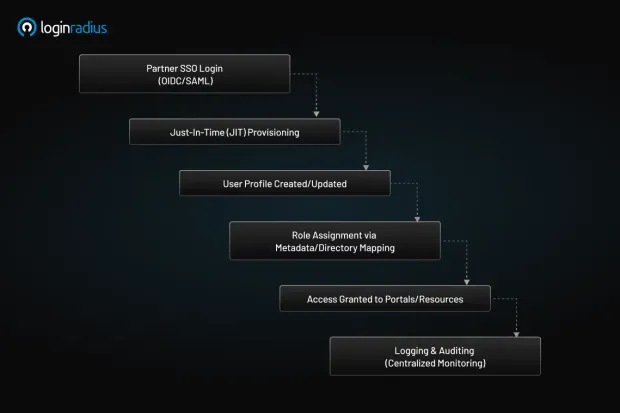
-
Partner signs in via B2B SSO using OIDC/SAML.
-
JIT provisioning creates or updates the user profile.
-
Role is assigned based on metadata or directory mapping.
-
Access is granted to relevant portals/resources.
-
All actions are logged and auditable.
Consider the case of a regional logistics partner accessing a global retailer’s portal. Once authenticated through B2B SSO, LoginRadius provisions the user, assigns roles based on their organizational metadata, and enforces security rules including multi factor authentification. All actions are logged, providing transparency and auditability.
This architecture aligns with industry-leading practices from top identity management companies, ensuring that systems are scalable, secure, and regulation-ready.
Why Choose LoginRadius for Partner IAM
LoginRadius provides a robust and flexible platform specifically designed to support the complexities of Partner IAM in modern B2B ecosystems.
Whether you’re managing thousands of users across hundreds of partner organizations or looking to create a fully branded access experience per tenant, LoginRadius delivers everything needed out-of-the-box.
The platform offers advanced features such as multi-tenant architecture, SSO integration with major identity providers, custom workflows, and real-time user activity tracking. With flexible API-first design, organizations can tailor user onboarding, role assignments, and authentication workflows to match their exact operational requirements.
LoginRadius also supports identity federation with protocols like SAML, OAuth, and OIDC—ensuring seamless integration with partner systems. Its role-based access control engine, partner-level MFA, and centralized logging capabilities make it a go-to choice for compliance-focused businesses.
With extensive documentation, pre-built SDKs, and a developer-friendly environment, LoginRadius minimizes time-to-market while providing enterprise-grade scalability and security. From Retail and SaaS to Healthcare and Finance, organizations choose LoginRadius to future-proof their partner identity infrastructure. Explore LoginRadius Partner IAM capabilities.
Conclusion
Delegated administration is a cornerstone of secure and scalable Partner IAM. It empowers external users while giving enterprises the oversight and control they need to meet compliance, performance, and security demands. As businesses grow and partnerships evolve, so does the need for a mature identity orchestration platform.
LoginRadius provides the tools, flexibility, and security to implement a future-ready B2B IAM strategy—whether you're a SaaS provider, a global retailer, or a complex supply chain operator. By following best practices, adopting the right technical architecture, and avoiding common pitfalls, organizations can unlock seamless, compliant, and secure access for all their external users.
Start your journey today by discovering how LoginRadius helps enterprises scale their partner identity programs without compromise. Contact us to learn more.