Key Summary
-
2FA authentication adds a second verification factor to strengthen login security beyond passwords.
-
Core 2FA methods include SMS/email codes, authenticator apps, push notifications, and hardware security keys.
-
Basic OTP-based 2FA is vulnerable to phishing and SIM-swap attacks, making stronger factors increasingly necessary.
-
Modern security strategies pair 2FA with MFA or risk-based authentication to protect users and high-value accounts.
-
LoginRadius enables secure, flexible 2FA and MFA implementation through configurable SMS, TOTP, push, and hardware-key authentication flows.
Introduction
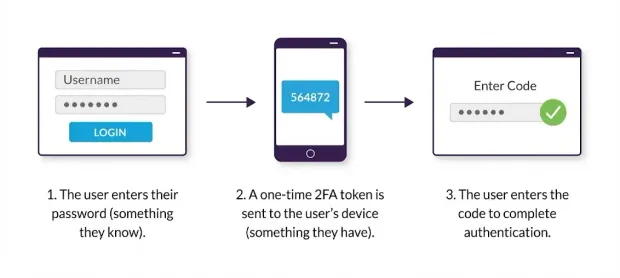
Two-factor authentication (2FA) is the process of requiring a user to verify their identity in two distinct ways before gaining access to an application or account. Most users are familiar with traditional login flows that rely on a unique identifier, such as an email address, username, or phone number, combined with a password. While this model is widely used, passwords are vulnerable to theft, reuse, and automated attacks.
2FA authentication strengthens this flow by adding a second verification step that confirms the user’s identity using a factor only they should possess or control. In most cases, this second step involves entering a one-time 2FA token generated by an authenticator app, delivered via SMS or email, or produced by a hardware device. In other scenarios, two-factor authentication uses biometric verification, such as a fingerprint or facial scan as the additional factor.
By requiring two independent factors, 2FA login flows significantly reduce the likelihood of unauthorized access, even when passwords are compromised. The following sections explain how 2FA works, the methods available, key risks to consider, and best practices for implementing secure and user-friendly authentication.
What is 2FA?
Two-factor authentication (2FA) is a security process that requires users to prove their identity using two independent pieces of evidence, known as authentication factors. These factors must come from different categories to ensure that compromising one does not automatically compromise the other.
In any 2FA authentication flow, verification is based on one of the following factor types:
1. Something you know
A password, PIN, or security question.
This is the most common first factor and the one most frequently targeted by attackers.
2. Something you have
A physical or digital item that generates or receives a 2FA token, such as:
-
a mobile device running a TOTP authenticator app
-
an SMS-capable phone
-
a hardware security key
-
a smart card or dedicated 2FA token device
3. Something you are
Biometric attributes unique to the user, such as fingerprints, facial recognition, or retina patterns.
For an authentication flow to qualify as true two-factor authentication, it must use two factors from different categories. For example:
-
Password (something you know) + TOTP code from an authenticator app (something you have)
-
Password + hardware security key
-
Password + biometric factor
Using two variations of the same type, such as a password and a security question, does not count as valid two-factor authentication, because both rely on the same knowledge-based factor.
Why 2FA Provides Stronger Security
The strength of 2f authentication comes from its layered design. Even if an attacker obtains a user’s password through phishing, credential stuffing, or data breaches, they typically cannot complete the second step without access to the device, token, or biometric required for verification.
This additional requirement significantly decreases the likelihood of successful account takeover and is a key reason why 2FA authentication is now considered a minimum standard for secure login flows.
Core Principle of Independent Verification
For 2FA to be effective, each factor must be independent, meaning one factor does not reveal or compromise the other. The second factor must also be difficult for an attacker to intercept or replicate, which is why methods such as hardware-backed keys or app-based tokens are generally more secure than SMS codes.
Also read : How to Set Up Two-factor Authentication on All Your Online Accounts?
Common 2FA Methods: Their Strengths and Weaknesses
Two-factor authentication can be implemented using several different verification methods. Each provides a unique balance of usability, security, and implementation complexity. Understanding these differences is critical when choosing the right approach for your 2FA authentication workflow.
Below are the most common 2FA methods used in modern applications, along with their advantages and limitations.

1. SMS One-Time Passwords (SMS OTP)
How it works:
The user enters their password, then receives a one-time 2FA token via SMS. They need to enter this token to complete the login.
Strengths:
-
Easy for users to understand
-
No additional apps or devices required
-
Widely supported across all mobile devices
Weaknesses:
-
Vulnerable to SIM-swapping, number porting, and SMS interception
-
Can be delayed or undelivered due to carrier issues
-
Not considered phishing-resistant
-
Higher operational cost due to SMS delivery fees
Best for: Low- to medium-risk accounts or environments where maximum accessibility is required.
2. Email One-Time Passwords (Email OTP)
How it works:
A one-time verification code is sent to the user’s email inbox as part of the 2fa login process.
Strengths:
-
Requires no additional setup
-
Works well for users who prefer email-based communication
-
Good fallback when other factors are unavailable
Weaknesses:
-
Email accounts are often less secure than authentication apps or hardware keys
-
Susceptible to phishing and account compromise
-
Delivery delays are common with high-volume providers
Best for: Basic 2f authentication flows or as a secondary fallback method.
3. Authenticator Apps (TOTP/HOTP)
How it works:
Users scan a QR code with an authenticator app (such as Google Authenticator, Authy, or Microsoft Authenticator). The app generates time-based one-time passwords (TOTP) that refresh every 30 seconds.
Strengths:
-
More secure than SMS or email-based codes; works offline
-
Resistant to SIM-swapping and message interception
-
Easy to integrate via open standards like TOTP
Weaknesses:
-
Users must install and maintain an app
-
Phone loss may require recovery mechanisms
-
Still vulnerable to certain phishing and man-in-the-middle attacks
Best for: Most consumer applications and medium- to high-security environments.
4. Push Notification Authentication
How it works:
A push notification is sent to the user’s device. The user approves or denies the login attempt with a single tap.
Strengths:
-
User-friendly and fast
-
Eliminates code entry errors
-
Reduces friction in the 2FA authentication process
-
Can include contextual information (location, device, IP) for risk analysis
Weaknesses:
-
Requires reliable internet connectivity
-
Susceptible to “push fatigue” if users are spammed with approval requests
-
Device compromise can impact security
Best for: Mobile-first apps and organizations seeking a balance between usability and stronger verification.
5. Hardware Security Keys (FIDO2/WebAuthn/U2F)
How it works:
Users authenticate using a physical cryptographic key (e.g., YubiKey). The key generates a unique challenge-response signature during the 2FA login flow.
Strengths:
-
Strongest protection against phishing, MITM attacks, and credential theft
-
Keys are device-bound; attackers cannot intercept codes
-
Fast and simple user experience
-
Supports modern passwordless authentication
Weaknesses:
-
Requires purchasing physical devices
-
Users may misplace the key, necessitating backup methods
-
Some older devices or browsers may have limited compatibility
Best for: High-security environments, administrative accounts, and organizations needing phishing-resistant two-factor authentication.
6. Biometric Verification
How it works:
A fingerprint scan, facial recognition, or retina scan serves as the second factor in the authentication process.
Strengths:
-
Extremely convenient for users
-
Fast and frictionless
-
Difficult to replicate or spoof when implemented securely
Weaknesses:
-
Biometric data cannot be “reset” if compromised
-
Requires supported hardware and secure device storage
-
Not always suitable for shared or public devices
Best for: Mobile apps and environments where seamless authentication is essential.
Learn more: What is Biometric Authentication and How It's Changing Login
7. Dedicated 2FA Tokens and Smart Cards
How it works:
Users authenticate with a physical token or smart card that generates or stores a unique 2FA token or digital certificate.
Strengths:
-
Strong security guarantees
-
Ideal for enterprise environments and controlled workforces
-
Resistant to remote attacks
Weaknesses:
-
More complex to distribute and manage
-
Additional hardware cost
-
Limited use for consumer-facing applications
Best for: Enterprise systems, VPNs, and regulated industries requiring strict identity controls.
The Limitations of 2FA and Where It Falls Short
While 2FA authentication significantly improves security compared to password-only login flows, it is not a complete defense against modern threats. Not all two-factor authentication methods provide equal protection, and some factors commonly used in 2FA login workflows introduce their own risks. Understanding these limitations is essential when designing a secure authentication strategy.
Below are the primary weaknesses organizations must consider when evaluating 2FA or planning to move toward stronger MFA and phishing-resistant methods.
1. Vulnerabilities in SMS and Email-Based 2FA
SMS and email OTPs remain widely used because they are convenient, but they also represent the weakest link in 2 factor authentication online.
Key risks include:
-
SIM-swapping and port-out fraud: Attackers convince carriers to transfer a victim’s phone number to a new SIM card.
-
SMS interception: Messages can be intercepted over insecure networks or via malware.
-
Email compromise: If an attacker gains access to a user’s email, they can obtain every 2FA token sent to it.
-
Message delays or delivery failures: Poor network conditions can lock out legitimate users.
For these reasons, SMS and email should not be the sole factor for accounts requiring high assurance.
2. Phishing and Man-in-the-Middle (MitM) Attacks
Traditional 2FA tokens, such as SMS OTPs, email codes, and TOTP app codes can all be phished.
Attackers now use:
-
Spoofed login pages to capture both passwords and 2FA tokens
-
Real-time phishing kits that forward OTPs directly to the legitimate service
-
Reverse-proxy tools that mirror login flows and intercept authentication data
If a code can be typed, it can be stolen. Only phishing-resistant authentication methods, such as hardware keys or device-bound passkeys, fully mitigate these threats.
3. Device Loss and Weak Recovery Mechanisms
Even strong 2FA authentication systems can be undermined by poor recovery processes.
Common risks include:
-
Users losing access to the device that generates their 2FA tokens
-
Backup codes stored insecurely or in plain text
-
Weak fallback methods (e.g., easily guessed security questions)
-
Customer support processes that reset 2FA with inadequate identity verification
Weak recovery flows are one of the most common ways attackers bypass two-factor authentication entirely.
4. Push Notification Fatigue
Push-based 2FA login flows improve usability but can create a risky pattern known as “push fatigue.”
This occurs when:
-
Users receive too many approval requests
-
Habitual approval leads to accidental confirmation of fraudulent attempts
-
Attackers intentionally spam push requests hoping users will “approve to stop the notifications”
Without rate limiting and risk-based checks in place, push authentication can be exploited.
5. Dependency on User Hardware and Environment
Some 2FA methods rely on hardware or apps that users may not have, including:
-
Authenticator apps on unsupported devices
-
Hardware keys that are easy to lose
-
Biometric sensors that vary across devices
-
Limited accessibility for users with disabilities
This introduces friction and may exclude users if alternative factors are not provided.
6. Single-Point Weakness in Knowledge Factors
Even with 2FA auth enabled, the first factor (password) is still a single point of failure. If attackers:
-
Steal credentials through breaches
-
Use automated credential stuffing
-
Apply password spraying
-
Harvest passwords through phishing
…they only need to compromise one poorly protected second factor to gain access.
7. 2FA Alone Does Not Equal Zero Trust
Two-factor authentication is a layer, not a complete security model. It does not account for:
-
Unusual device behavior
-
Risky IP addresses
-
Impossible travel patterns
-
Compromised but authenticated sessions
-
Malware on user devices
Modern attacks require modern defenses that go beyond basic two-factor authentication.
Why These Limitations Matter
Understanding these risks helps organizations determine when 2FA is sufficient and when it must be paired with:
-
MFA that combines multiple strong factors
-
Phishing-resistant authentication (e.g., FIDO2/WebAuthn)
-
Risk-based or adaptive authentication
-
Passwordless flows that eliminate weak factors entirely
Why Organizations Shift to MFA and Stronger Authentication
While 2FA authentication dramatically improves security over password-only logins, it is not always sufficient for modern threat models. Attackers now use advanced phishing tactics, automated tooling, and real-time interception methods that can bypass weaker two-factor authentication flows. As a result, organizations increasingly turn to multi-factor authentication (MFA), phishing-resistant methods, and adaptive risk-based checks to close the gaps left by basic 2FA.
Here’s more on why 2FA eventually reaches its limits, and when you should move to more advanced authentication methods to protect user accounts, high-value data, and critical systems.
1. When the Application Handles High-Risk or Sensitive Data
If your platform stores or processes data that could cause material harm if compromised, 2FA authentication may not provide enough assurance.
High-risk environments include:
-
Financial services
-
Healthcare and regulated industries
-
Enterprise admin dashboards
-
Shared workforce applications
-
Developer portals with API keys or infrastructure access
In these cases, MFA with strong possession factors, such as hardware keys, cryptographic signatures, or device-bound credentials provides the necessary protection against targeted attacks.
2. When You Need Protection Against Phishing and Real-Time Attacks
Most common 2FA login methods (SMS, email OTPs, TOTP codes) can be phished because users manually enter a 2FA token. Attackers can capture these codes through spoofed login pages or real-time reverse-proxy tools.
Transitioning to phishing-resistant authentication becomes essential when:
-
Your users face frequent phishing attempts
-
You operate a high-value platform where attackers use sophisticated techniques
-
Regulatory frameworks recommend or require phishing-resistant verification
Hardware security keys (FIDO2/WebAuthn), passkeys, and device-bound authentication eliminate code entry and provide cryptographic, origin-bound verification that attackers cannot intercept.
Also learn : How to Integrate Passkeys in 5 Minutes
3. When User Experience Suffers Under Basic 2FA
Not all two-factor authentication online provides a smooth experience. Users may encounter:
-
SMS delays or undelivered messages
-
App-based code entry friction
-
Confusion during device upgrades
-
Support tickets related to lost 2FA devices
MFA systems that support push notifications, biometric factors, or passwordless flows reduce friction and create a smoother login experience, without sacrificing security.
4. When You Need Stronger Verification for Workforce or Admin Access
Internal and administrative accounts are often the first target in account takeover attempts because compromising an admin unlocks broad access.
Basic 2FA is not enough for:
-
System administrators
-
IT or DevOps teams
-
Access to internal dashboards or sensitive internal tools
-
Accounts with elevated privileges
Stronger MFA that uses hardware-backed keys or device-bound authentication is now considered best practice for these roles.
5. When Regulatory or Industry Standards Require MFA
Many compliance frameworks now recommend or mandate MFA rather than basic 2FA, including:
-
NIST 800-63
-
PCI-DSS
-
HIPAA security guidelines
-
Financial sector regulations
-
Corporate zero trust frameworks
When compliance requirements specify high-assurance authentication, MFA with strong second factors is the clear path forward.
6. When You Need Adaptive, Risk-Based Authentication
Even strong 2FA does not account for contextual risk signals such as:
-
Device anomalies
-
Risky or unfamiliar IP addresses
-
Impossible travel patterns
-
Behavioral deviations
-
Known bad networks
Adaptive authentication evaluates these signals in real time and prompts for additional verification only when risk is detected. This helps organizations:
-
Enhance protection
-
Reduce friction
-
Focus strong authentication where it matters most
Risk-based MFA is increasingly used to balance security and usability.
7. When You Want to Future-Proof Your Authentication Strategy
Authentication technology is moving toward passwordless and cryptographic methods. Organizations that rely solely on 2FA authentication may struggle to evolve as:
-
More platforms adopt passkeys
-
Device-bound credentials become standard
-
Hardware-backed cryptography replaces OTP-based flows
Implementing MFA that supports FIDO2, WebAuthn, and passwordless options ensures long-term alignment with modern identity standards.
When to Go Beyond 2FA
You should consider transitioning from 2FA to stronger MFA methods when:
-
You need protection against phishing
-
You handle high-value or regulated data
-
You require lower friction for user logins
-
Admin or workforce accounts demand higher assurance
-
Compliance frameworks mandate MFA
-
You want advanced risk-based or passwordless capabilities
Best Practices for Implementing 2FA and MFA Securely
Implementing 2FA authentication or MFA adds meaningful security to any login system, but the effectiveness of these controls depends on the design of the authentication flow. Poor configuration, weak fallback methods, or incorrect factor selection can create gaps that attackers exploit.
The following best practices help organizations deploy strong, reliable, and user-friendly two-factor authentication online.
1. Prioritize Secure Factor Choices Over Convenience Alone
Not all 2FA factors offer the same protection. When selecting methods, evaluate both user experience and security strength.
-
Avoid relying on SMS or email OTP as the primary factor.
-
Prefer authenticator app codes (TOTP), push-based verification, or hardware-backed 2FA tokens.
-
Offer multiple secure options to accommodate different user needs.
2. Use Phishing-Resistant Authentication Wherever Possible
To protect against phishing and man-in-the-middle attacks, incorporate factors that cannot be intercepted or replayed, like
-
FIDO2/WebAuthn security keys
-
Passkeys tied to a specific device
-
Cryptographic challenge–response flows
3. Apply Adaptive, Risk-Based Authentication
Adaptive authentication strengthens the login flow by evaluating contextual risk signals before deciding whether to prompt for 2FA or additional verification. Risk signals can include:
-
New or unrecognized devices
-
Suspicious IP addresses, VPNs, or Tor networks
-
Impossible travel patterns
-
Abnormal behavior or access times
-
Device reputation or OS integrity issues
4. Implement Strong Rate Limiting and Anti-Automation Controls
2FA authentication does not prevent brute-force attacks on the first factor (the password), nor does it stop attackers from attempting to guess OTPs.
Mitigate this by:
-
Enforcing rate limiting on password and 2FA token entry
-
Blocking or challenging automated traffic
-
Monitoring for rapid, repeated OTP attempts
-
Applying CAPTCHA only where appropriate
5. Secure and Thoughtfully Design “Remember This Device” Logic
Device recognition can reduce friction in 2FA login flows, but poorly implemented versions undermine security. Best practices include:
-
Storing device tokens securely and binding them to the browser and machine
-
Limiting how long a device can remain “trusted”
-
Revoking trust when risk signals change
-
Avoiding permanent or unlimited bypasses
6. Provide Safe, Well-Controlled Account Recovery Options
Account recovery is one of the most frequently exploited weak points in two-factor authentication online. To secure it:
-
Offer backup 2FA tokens or recovery codes that users can store offline
-
Allow users to register multiple trusted devices
-
Require identity verification for recovery, not simple knowledge-based questions
-
Log and alert users of recovery attempts
7. Offer Multiple 2FA Methods to Support Diverse Users
A secure system must also be inclusive. Some users do not have smartphones, some lack strong network coverage, and others rely on assistive technologies.
Offer alternatives such as:
-
TOTP authenticator apps
-
Push notifications on mobile or desktop
-
Hardware security keys
-
Backup codes
-
Email or SMS OTP as a last-resort fallback
8. Monitor and Log Authentication Events
Visibility is a key component of secure 2f authentication. Always monitor:
-
Repeated failed 2FA attempts
-
Suspicious login patterns
-
Recovery event frequency
-
Factor enrollment and removal
-
IP and location anomalies
These signals help identify compromised accounts early.
10. Build With Future Authentication Methods in Mind
Identity security is evolving toward passwordless and hardware-backed authentication. Designing with flexibility ensures longevity. Future-ready systems should:
-
Support WebAuthn and passkeys
-
Allow MFA to be extended or strengthened over time
-
Integrate adaptive risk engines
-
Make factor enrollment and management straightforward
How to Implement 2FA and MFA With LoginRadius
LoginRadius provides a standards-based identity platform that allows developers to add 2FA authentication and MFA to their applications without building factor management, token validation, or security controls from scratch. The system handles enrollment, factor verification, recovery workflows, and risk evaluation, while exposing APIs and SDKs that developers can integrate directly into web and mobile apps.
Below are the essential components of implementing two-factor authentication and multi-factor authentication with LoginRadius.
1. Core 2FA Factors: SMS, Email, and TOTP
LoginRadius supports all common 2FA token delivery methods:
SMS and Email OTP
-
LoginRadius generates a time-bound one-time code linked to the user’s session.
-
Codes are hashed server-side and validated through the Identity API.
-
Developers can configure TTL, retry limits, and delivery behavior.
These factors offer accessibility and broad device coverage, making them suitable as optional or fallback methods.
TOTP Authenticator Apps
-
LoginRadius generates a TOTP secret and exposes it via a QR code for enrollment.
-
Users verify the binding by submitting a valid TOTP code.
-
Server-side validation follows the RFC 6238 standard with clock-skew tolerance.
TOTP provides stronger protection than SMS or email for most 2FA authentication workflows.
2. Push-Based Authentication
Push MFA allows LoginRadius to send a signed challenge to a user’s registered device through the LoginRadius mobile SDK. The device returns a cryptographically signed approval, confirming:
-
Possession of the registered device
-
Integrity of the challenge
-
User interaction (tap-to-approve)
This reduces friction compared to code entry while maintaining strong assurance for 2FA login flows.
3. WebAuthn and Hardware Security Keys
For organizations needing phishing-resistant MFA, LoginRadius supports:
-
WebAuthn platform authenticators (Touch ID, Windows Hello, Android biometrics)
-
FIDO2 hardware keys (YubiKey, SoloKey, etc.)
LoginRadius manages WebAuthn challenges, validates signatures, and stores public key metadata, allowing developers to add hardware-backed authentication without managing cryptographic workflows themselves.
4. Adaptive and Risk-Based Step-Up Authentication
LoginRadius evaluates contextual signals during authentication, including:
-
Device recognition
-
IP reputation and geolocation
-
Velocity anomalies
-
Behavioral patterns
When risk is detected, LoginRadius can automatically “step up” authentication by requiring a stronger factor (e.g., push or WebAuthn). This ensures that two-factor authentication online adapts to threat levels without forcing every user through high-friction flows.
5. Enrollment, Management, and Recovery
LoginRadius provides built-in workflows for:
-
Self-service 2FA factor enrollment
-
Multi-device registration
-
Backup code generation
-
Factor revocation
-
Secure recovery flows
All factor events are logged, enabling auditability and compliance for environments that require traceability.
6. Integrating 2FA and MFA Into Applications
Developers can add 2fa auth using:
-
REST Identity APIs
-
JavaScript, Android, and iOS SDKs
-
Hosted Login pages with configurable MFA policies
A typical flow includes:
-
User completes primary authentication
-
LoginRadius returns “2FA pending” with allowed factor types
-
Application triggers 2FA token verification endpoint
-
Successful verification issues access and refresh tokens following OAuth 2.0 and OIDC standards
This separates factor handling from application logic while ensuring secure session creation.
7. Policy and Access Controls
LoginRadius allows administrators to define:
-
Mandatory 2FA for all or specific user groups
-
Conditional MFA based on risk or user attributes
-
Factor-type restrictions (e.g., hardware keys for admins)
-
Step-up authentication for sensitive actions
These policies allow organizations to operationalize strong authentication without hardcoding rules into the application.
Lean more : Detailed step-by-step guidance for MFA implementation
Real-World Scenarios and Use Cases
Below are three practical scenarios that illustrate when and how different 2FA and MFA methods strengthen identity assurance without introducing unnecessary friction.
1. Consumer Applications: Preventing Account Takeover at Scale
Consumer-facing services, like e-commerce platforms, fintech apps, streaming services, or loyalty programs, are constant targets for credential-stuffing and automated attacks. Users often reuse passwords, access accounts from shared devices, or log in over insecure networks.
Here’s what you can add:
-
Primary authentication: password or passwordless email/SMS magic link
-
Default 2FA factor: TOTP authenticator app or mobile push
-
Fallback: SMS or email OTP only when necessary
-
Step-up MFA: triggered during high-risk actions such as adding a payment method, changing email/phone number, or viewing saved financial information
Why this works
-
TOTP and push provide stronger assurance than SMS for normal 2FA login attempts
-
Step-up MFA protects sensitive actions even if the initial session was compromised
-
The design balances usability with security which is critical for conversion and retention in consumer apps
This flow will reduce account takeover risk without overloading users with unnecessary friction.
2. Administrative and Privileged Access: High-Assurance MFA Required
Admin dashboards, internal tools, DevOps consoles, or support portals often grant elevated permissions. A single compromised admin account can expose customer data, modify security settings, or disrupt operations.
Here’s what you can add:
-
Primary authentication: password or SSO (SAML/OIDC)
-
Mandatory MFA: WebAuthn platform authenticators (Windows Hello, Touch ID) or hardware security keys
-
Optional secondary factor: push-based confirmation during sensitive actions such as privilege elevation or configuration changes
-
Continuous session monitoring: device fingerprint + IP reputation + velocity anomaly checks
Why this works
-
Hardware-backed factors provide phishing-resistant authentication
-
WebAuthn ensures origin-binding, preventing credential replay even through advanced MITM tooling
-
Step-up verification adds protection to critical admin-level operations
Looking Ahead: The Future of Authentication
The way users access digital services is changing. People expect fast, effortless logins, while organizations need stronger protection against increasingly sophisticated attacks. Two-factor authentication will remain an important baseline, but the future of authentication is moving toward methods that feel almost invisible to users and far more resistant to attackers.
We are shifting away from passwords and manually entered codes toward approaches that rely on cryptographic proof, device-bound credentials, and continuous evaluation of context. Instead of asking users to type a 2FA token, future systems will authenticate them through a combination of trusted devices, biometric unlocks, and behind-the-scenes risk checks that confirm whether the request is legitimate.
Organizations that start adopting these patterns today will be better prepared as threats evolve and user expectations continue to rise. The long-term goal is clear: stronger identity assurance delivered with less effort from the user. 2FA authentication is a critical step on that journey, but the future belongs to authentication that is smarter, more contextual, and almost effortless.
FAQs
1. What is 2FA authentication and how does it work?
2FA authentication requires users to verify their identity using two independent factors, usually a password plus a second element such as a TOTP code, push approval, hardware key, or biometric scan. It strengthens login security by ensuring that compromising one factor alone is not enough for account access.
2. What are the three types of authentication factors used in 2FA?
2FA relies on two of three factor categories:
-
Something you know (password or PIN)
-
Something you have (2FA token, mobile device, hardware key)
-
Something you are (biometric characteristics)
3. Which 2FA methods are most secure?
The most secure 2FA methods are hardware-backed keys (WebAuthn/FIDO2) and device-bound passkeys because they provide phishing-resistant verification. TOTP authenticator apps and push notifications also offer strong protection, while SMS and email OTPs are considered weaker due to interception risks.
4. Is SMS-based two-factor authentication still safe?
SMS 2FA provides basic protection but is vulnerable to SIM-swapping, number porting fraud, and message interception. It is acceptable as a fallback method but should not be used as the primary factor for sensitive accounts or administrative access.
5. Can attackers bypass 2FA?
Yes. Attackers can bypass weaker 2FA methods through phishing kits that capture OTP codes, reverse-proxy attacks, SIM-swapping, malware, or exploiting weak recovery flows. Strong factors like WebAuthn and hardware keys significantly reduce bypass risk because they cannot be relayed or intercepted.
6. When should organizations move from 2FA to MFA?
Organizations should move to MFA when they manage high-risk data, face phishing threats, operate in regulated industries, or require higher assurance for administrative and workforce accounts. MFA with strong possession factors or phishing-resistant methods offers greater protection than basic two-factor authentication.
7. How does adaptive or risk-based authentication work?
Risk-based authentication evaluates signals such as device fingerprint, IP reputation, geolocation, behavioral patterns, and login velocity. If risk is high, the system automatically requires stronger 2FA or MFA factors. If risk is low, users experience reduced friction.
8. How do you implement 2FA securely in an application?
Secure implementation includes offering strong factors like TOTP or push, avoiding SMS-only flows, enforcing rate limits, securing recovery processes, supporting multiple devices, and using an identity platform that handles factor enrollment, token validation, and session integrity.
9. What is the best 2FA method for admin and privileged users?
Administrators should use phishing-resistant MFA such as WebAuthn platform authenticators or hardware security keys. These methods cryptographically bind authentication to the legitimate domain and block real-time relay attacks.
10. What is a 2FA token?
A 2FA token is a temporary, one-time verification code generated or delivered as part of the second authentication step. It may come from an authenticator app (TOTP), SMS message, email, hardware token, or push approval process. The token proves possession of a trusted device.
11. Is 2FA required for compliance?
Many regulations, including NIST 800-63, PCI-DSS, and various financial or healthcare standards recommend or require MFA for high-assurance access. While basic 2FA may satisfy some requirements, stronger MFA or phishing-resistant methods are increasingly mandated.
12. What role does 2FA play in Zero Trust security?
In a Zero Trust model, authentication is not a single event. 2FA strengthens initial identity verification, but the model also requires continuous evaluation of device trust, session behavior, and contextual signals. MFA and risk-based checks extend 2FA into an ongoing trust assessment.



