Quick Summary
-
SAML is an XML-based standard used for federated authentication and SSO between an Identity Provider (IdP) and a Service Provider (SP).
-
The SAML authentication process relies on signed SAML assertions that contain user identity, authentication context, and time-bound security conditions.
-
The SAML authentication flow uses browser redirects or POST bindings to transport the AuthnRequest and SAML Response between the SP and IdP.
-
In CIAM environments, SAML is commonly used to integrate external enterprise IdPs, such as ADFS, Okta, PingFederate, or Azure AD—into customer or partner login workflows.
-
LoginRadius operates as the SP in these integrations, validating SAML assertions, enforcing signatures and conditions, and mapping SAML attributes into customer profiles.
-
Secure SAML-based authentication depends on correct metadata exchange, certificate management, strict audience and recipient validation, and consistent NameID and attribute configurations.
-
A reliable SAML implementation requires attention to ACS URLs, clock skew, binding selection, certificate rotation, and precise attribute mapping for identity resolution.
Introduction
Security Assertion Markup Language (SAML) remains one of the most widely used standards for federated authentication, especially in enterprise and B2B environments. Many organizations continue to rely on established SAML-based IdPs to control access across their systems. When these enterprises connect to your product, they expect seamless SAML-based authentication without modifying their existing identity stack.
For CIAM teams, this makes it essential to understand how SAML authentication works: how the Identity Provider and Service Provider exchange data, what a SAML assertion contains, how the browser passes messages between both systems, and how the SAML authentication flow influences session creation and attribute handling. These fundamentals determine whether your SAML integration will operate reliably across different customer IdPs.
What is SAML (Security Assertion Markup Language)?
SAML is an XML-based standard that allows an Identity Provider (IdP) to authenticate a user and send a signed SAML security token to a Service Provider (SP). CIAM platforms use SAML so customers and partners can log in with their own enterprise IdPs without storing new passwords or identity data. LoginRadius supports SAML by validating assertions, enforcing signatures, and mapping SAML attributes into unified customer profiles.
SAML is a widely adopted XML standard for federated SSO, designed to securely transmit authentication and authorization data between an IdP and an SP. Instead of requiring an application to authenticate users directly, SAML delivers identity information through a signed SAML assertion, which acts as a verifiable security token.
From a protocol perspective, SAML defines:
-
A structured format for representing user identity and authentication context
-
The process for creating and validating SAML-based authentication messages
-
Rules for exchanging those messages through the browser
-
Strict requirements for signing, encrypting, and time-bounding assertions
How SAML is Used for Authentication in CIAM
In CIAM implementations, SAML is most commonly used when an enterprise customer wants to allow its workforce or partners to authenticate using its own IdP. Instead of provisioning new accounts, the user authenticates with the customer’s IdP, and the IdP issues a signed assertion consumed by the CIAM platform.
Typical scenarios include:
-
B2B SaaS where each customer brings its own IdP
-
Partner and reseller portals requiring controlled, high-trust access
-
Customer deployments where existing corporate identity is mandatory
-
Regulated industries relying on established SAML IdPs
In these cases, SAML provides a secure and predictable way to map external identities into a CIAM profile without disrupting enterprise workflows.
Why SAML Still Matters Despite Newer Protocols
Even with the rise of OAuth 2.0 and OpenID Connect, SAML remains critical because:
-
Enterprise ecosystems are heavily invested in SAML. Many large organizations maintain long-standing IdPs such as ADFS or PingFederate.
-
SAML provides strong assurance. Signed assertions, strict timestamps, and audience restrictions make SAML dependable for high-assurance logins.
-
Enterprise procurement often requires SAML SSO. Supporting SAML can be a prerequisite for closing B2B deals.
For CIAM platforms, this means SAML integration is part of long-term interoperability with enterprise identity systems.
How LoginRadius Fits Into SAML CIAM Workflows
In most customer and partner CIAM use cases, LoginRadius acts as the Service Provider:
-
It receives and validates the SAML assertion from the external IdP
-
Enforces signature verification and certificate checks
-
Processes NameID formats and authentication context
-
Maps identity attributes into a LoginRadius profile
-
Establishes a LoginRadius session or issues tokens for downstream apps
When required, LoginRadius can also act as a SAML Identity Provider, enabling applications to authenticate using SAML without implementing IdP functionality themselves. This flexibility allows organizations to bridge older SAML-based environments with modern application architectures.
Core SAML Building Blocks Every Architect Should Know
The core components of SAML-based authentication are the Identity Provider (IdP), the Service Provider (SP), and the SAML assertion. In CIAM workflows, the IdP authenticates the user, the SP consumes and validates the assertion, and the browser transports messages between the two.
Identity Provider (IdP) and Service Provider (SP)
At the center of how SAML authentication works are two entities:
Identity Provider (IdP)
The IdP authenticates the user. It verifies credentials locally via AD, LDAP, MFA, conditional access rules, or any enterprise policy and produces a signed SAML security token (assertion) that declares the user’s identity.
Common enterprise IdPs include:
-
ADFS
-
PingFederate
-
Okta
-
Azure AD (SAML mode)
-
Shibboleth
Service Provider (SP)
The SP consumes the SAML assertion and establishes a session or access token based on it.
In CIAM environments, these roles map directly to how LoginRadius is used when customers bring their own enterprise IdP. LoginRadius typically operates as the SP and handles the full lifecycle of consuming and standardizing incoming identity data.
In this role, LoginRadius:
-
Receives SAML Responses from the customer’s IdP
-
Parses the NameID and user attributes for profile resolution
-
Normalizes inconsistent IdP attribute formats
-
Creates or updates federated profiles based on mapped fields
-
Provides a consistent identity object to downstream applications
This makes SAML IdP diversity invisible to the applications integrated with LoginRadius.
Learn more: How to configure a SAML identity provider with LoginRadius
SAML Assertions: The Core Security Token
A SAML assertion is the XML document that contains the actual identity data issued by the IdP. Understanding its structure is essential for any SAML authentication flow.
Core Components of a SAML Assertion
-
Issuer: Identifies the IdP that issued the assertion.
-
Subject: Defines who the user is and is often expressed through the NameID. Formats may include email, persistent identifiers, or unspecified format.
-
Conditions: Time-bound and audience-bound rules that control whether the assertion is valid. Key fields include:
NotBefore, NotOnOrAfter, AudienceRestriction.These ensure the assertion is only usable by the correct SP and only for a limited window. -
AttributeStatement: Contains user attributes (email, name, user ID, roles, tenant IDs) needed to build a profile.
-
AuthnStatement: Describes how and when the user authenticated, including authentication context and session index.
Why assertions matter
If the assertion is malformed, expired, incorrectly signed, or addressed to the wrong audience/ACS, the entire SAML-based authentication process fails. Assertions are the single source of truth for identity in SAML.
Once an IdP issues a SAML assertion, the SP is responsible for validating it and extracting identity data. LoginRadius performs these steps automatically to ensure assertions meet security and interoperability requirements.
During assertion processing, LoginRadius:
-
Validates XML signatures using the IdP’s certificate
-
Enforces Conditions, including expiration and audience restrictions
-
Interprets NameID formats (email, persistent, unspecified)
-
Extracts AttributeStatements for profile mapping
-
Rejects assertions that are unsigned, expired, or scoped incorrectly
This allows LoginRadius to absorb variability between different SAML IdPs and present a stable identity model to applications.
SAML Metadata and Entity Configuration
Metadata is how the IdP and SP understand each other’s capabilities and endpoints. It’s a foundational element in SAML implementation.
What metadata contains
-
EntityID — unique identifier of the IdP or SP
-
Endpoints — SSO, SingleLogout, ArtifactResolve, etc.
-
Bindings — HTTP-POST, HTTP-Redirect, or Artifact
-
Certificates — used for signing and sometimes encryption
-
Supported NameID formats
-
Contact and organizational info (optional but common)
Why metadata is critical
Correct metadata ensures both systems:
-
Know which endpoints to call
-
Validate the right certificates
-
Accept the correct NameID formats
-
Enforce intended bindings
Incorrect metadata is one of the most common sources of failed SAML authentication flow attempts.
Reliable SAML implementation depends on both systems understanding each other’s identifiers, endpoints, binding methods, and certificates. LoginRadius uses this metadata to support predictable authentication flows across various customer IdPs.
During metadata exchange, LoginRadius:
-
Publishes its ACS URL, EntityID, certificates, and supported bindings
-
Stores the IdP’s metadata, including SSO URLs and signing certificates
-
Determines which binding (Redirect or POST) to use for AuthnRequests
-
Validates that incoming responses match the expected EntityID and endpoint
-
Keeps metadata up to date to handle certificate rotations and IdP changes
This prevents the mismatches and configuration drift that commonly break SAML integrations.
Learn more about LoginRadius Custom IdPs.
Certificates and Signatures
SAML relies heavily on cryptographic signatures to assure integrity and authenticity.
How signatures work in SAML
-
Assertions are signed with the IdP’s private key.
-
The SP (LoginRadius in many cases) validates the signature using the IdP’s public certificate.
-
Optionally, entire SAML responses may also be signed.
Why signatures matter
Without signature validation, SAML is vulnerable to:
-
Assertion forgery
-
Replay attacks
-
Man-in-the-middle modifications
Strict enforcement of signature checks is non-negotiable in any SAML deployment. Moreso, SAML depends on cryptographic signatures to guarantee integrity and authenticity. LoginRadius enforces these requirements rigorously as part of its SAML processing pipeline.
For certificate and signature handling, LoginRadius:
-
Verifies signatures on assertions and responses
-
Rejects tokens signed with untrusted or expired certificates
-
Enforces secure hashing algorithms (e.g., RSA-SHA256)
-
Validates certificate-bound key material during metadata updates
-
Blocks assertion reuse and timestamp violations
This ensures that only valid, correctly scoped assertions can be exchanged in the CIAM environment.
How the SAML Authentication Flow Works
The SAML authentication flow is a browser-mediated exchange where the Service Provider sends an AuthnRequest to the Identity Provider, the IdP authenticates the user, and a signed SAML Response containing a SAML assertion is returned to the SP’s ACS endpoint. This flow enables secure SSO without sharing passwords, and it forms the foundation of most SAML-based authentication used in CIAM platforms like LoginRadius.
SP-Initiated SAML SSO
In SP-initiated SAML SSO, the user begins at the application or CIAM platform. This is the dominant flow for customer and partner login scenarios because the application can control when SSO is triggered and where a user should return after authentication.
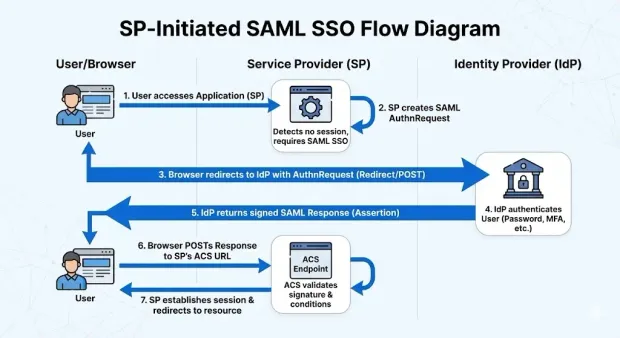
Here’s how it happens:
-
User accesses the application (SP). The SP detects there is no active session and SAML SSO is required.
-
SP creates an AuthnRequest. The SP builds a SAML request referencing its EntityID, expected ACS endpoint, NameID format, and optional authentication context.
-
Browser redirects the user to the IdP. The AuthnRequest is sent via Redirect or POST binding.
-
IdP authenticates the user. Authentication is performed using the IdP’s normal policies (passwords, MFA, conditional access, etc.).
-
IdP returns a signed SAML Response. The SAML response contains the SAML assertion, including NameID, Conditions, and AttributeStatements.
-
Browser posts the response to the SP’s ACS URL. The ACS endpoint processes the assertion and verifies signatures and conditions.
-
SP establishes a session. After validation, the SP issues its own session or access token and redirects the user to the intended resource.
Why This Matters in CIAM
SP-initiated SSO gives the platform full control over the login trigger, allows consistent redirect handling across customers, and is the easiest pattern for downstream applications to consume via LoginRadius.
IdP-Initiated SAML SSO
In IdP-initiated SSO, the user begins at the enterprise IdP, often inside a corporate application launcher or dashboard. The IdP issues a SAML Response without receiving a preceding AuthnRequest from the SP.
Here’s how it happens:
-
User logs into the enterprise IdP directly.
-
IdP selects the target SP (or user clicks an application tile).
-
IdP immediately creates a SAML Response and assertion.
-
Browser posts the response to the SP’s ACS endpoint.
-
SP validates the assertion and establishes a session.
Why It’s Used
-
Enterprise app launchpads or portals
-
Workforce environments where users navigate from internal systems
-
Scenarios where the IdP controls application entry points
Key Considerations
-
There is no InResponseTo binding back to an SP request.
-
Strong Recipient and Audience validation becomes more important.
-
RelayState must be parsed carefully to prevent open redirects.
A Simple SAML Flow Diagram
1User → SP (App) → AuthnRequest → Browser Redirects → IdP
2IdP → Authenticates User → Generates SAML Assertion → SAML Response
3Browser → Posts SAML Response → SP ACS Endpoint → Session CreatedThis structure highlights a key SAML principle:
-
The browser acts as the message carrier.
-
The SP and IdP never communicate directly.
Where LoginRadius Fits in This Flow
In most CIAM integrations, LoginRadius sits between the application and the customer’s IdP:
-
The application redirects the user to LoginRadius as the SP.
-
LoginRadius issues the AuthnRequest and handles the full SAML authentication flow.
-
After assertion validation, LoginRadius standardizes attributes and returns a LoginRadius session or token to the application.
This design:
-
Removes SAML parsing and XML signature handling from applications
-
Simplifies multi-tenant SAML setups
-
Ensures enterprise IdPs remain interoperable regardless of implementation differences
Also read about LoginRadius SSO overview describing supported authentication protocols and federated login workflows.
Deep Technical Walkthrough: Inside a Real SAML Authentication Flow
A SAML authentication flow works by having the Service Provider send an AuthnRequest to the Identity Provider, the IdP authenticates the user, and then returns a signed SAML Response containing a SAML assertion. The SP validates that assertion and uses it to create a session. This exchange is the core of SAML-based authentication and is central to most CIAM SAML implementations.
The AuthnRequest: How the SP Initiates Authentication
In an SP-initiated SAML authentication flow, the first message is an AuthnRequest. This request tells the IdP who is asking for authentication, what method the SP prefers, and where the IdP should return the user afterward.
A simplified AuthnRequest looks like this:
1<samlp:AuthnRequest
2 ID="_a12345"
3 Version="2.0"
4 IssueInstant="2025-01-01T12:00:00Z"
5 Destination="https://idp.example.com/sso"
6 AssertionConsumerServiceURL="https://sp.example.com/saml/acs">
7 <saml:Issuer>https://sp.example.com/metadata</saml:Issuer>
8 <samlp:NameIDPolicy
9 Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress"
10 AllowCreate="true" />
11</samlp:AuthnRequest>Key Elements in the AuthnRequest
-
ID — used by the SP to match the IdP’s response
-
Destination — the IdP’s SSO endpoint
-
ACS URL — where the IdP must return the SAML Response
-
Issuer — the SP’s unique identifier
-
NameIDPolicy — identifier format the SP prefers (email, persistent, unspecified)
How LoginRadius Uses the AuthnRequest
When LoginRadius is the Service Provider:
-
It constructs the AuthnRequest using its configured ACS URL and EntityID
-
It signs the request if required by the customer’s IdP
-
It selects the correct binding (Redirect or POST) based on IdP metadata
-
It embeds RelayState when applications specify a post-login destination
This ensures consistent SAML initiation across all customer IdPs.
The SAML Response: What the IdP Returns
Once the user is authenticated, the IdP returns a SAML Response, which contains the assertion, i.e., the core SAML security token.
Here is a trimmed-down example:
1<samlp:Response
2 ID="_b98765"
3 InResponseTo="_a12345"
4 Destination="https://sp.example.com/saml/acs">
5 <saml:Issuer>https://idp.example.com/metadata</saml:Issuer>
6 <saml:Assertion ID="_assert123">
7 <saml:Subject>
8 <saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress">
9 user@example.com
10 </saml:NameID>
11 </saml:Subject>
12 <saml:Conditions
13 NotBefore="2025-01-01T11:59:00Z"
14 NotOnOrAfter="2025-01-01T12:05:00Z">
15 <saml:AudienceRestriction>
16 <saml:Audience>https://sp.example.com/metadata</saml:Audience>
17 </saml:AudienceRestriction>
18 </saml:Conditions>
19 <saml:AttributeStatement>
20 <saml:Attribute Name="email">
21 <saml:AttributeValue>user@example.com</saml:AttributeValue>
22 </saml:Attribute>
23 <saml:Attribute Name="givenName">
24 <saml:AttributeValue>Alice</saml:AttributeValue>
25 </saml:Attribute>
26 </saml:AttributeStatement>
27 </saml:Assertion>
28</samlp:Response>Inside the SAML Assertion: What Each Field Means
The SAML assertion is where most of the important identity and security information lives.
1. Subject
Defines who the user is.
-
Often carries an email
-
May carry a persistent opaque identifier
-
May use a proprietary IdP-specific format
2. NameID
This is the user identifier the SP will rely on. NameID format inconsistencies are a frequent cause of failed SAML implementations.
3. Conditions
Defines when and where the assertion is valid.
Key fields:
-
NotBefore / NotOnOrAfter — strict validity window
-
AudienceRestriction — ensures the assertion is intended for the SP
-
Recipient — prevents token replay against unintended ACS endpoints
4. AttributeStatement
Carries the attributes needed to build or update a user profile. Examples include:
-
email
-
firstName / lastName
-
department
-
unique enterprise user ID
-
tenant or role attributes
5. AuthnStatement
Describes the authentication event (e.g., password, MFA) and is important for compliance-driven industries.
How LoginRadius Interprets the SAML Assertion
Before the assertion is accepted, LoginRadius performs a full validation pass. Here is the contextual explanation:
During assertion validation, LoginRadius:
-
Confirms the XML signature matches the IdP’s certificate
-
Checks the assertion’s time window and rejects expired responses
-
Evaluates AudienceRestriction to prevent token reuse across tenants
-
Parses NameID and maps it to the correct identifier type
-
Extracts AttributeStatements and normalizes them into profile fields
-
Applies custom attribute mappings defined in the LoginRadius dashboard
This step is what allows SAML IdPs with different schemas to appear uniform to downstream applications.
Putting It Together: The End-to-End Flow
When you combine the AuthnRequest and Response cycles, how SAML works becomes clear:
-
SP wants to authenticate a user
-
SP sends AuthnRequest → browser → IdP
-
IdP authenticates
-
IdP produces a signed SAML assertion
-
Browser posts SAML Response to ACS
-
SP (LoginRadius) validates the assertion
-
SP creates a session / token
-
User is redirected to the application
This flow ensures SAML-based authentication happens without exchanging passwords and without a direct network connection between the SP and the IdP.
Implementing SAML with LoginRadius
To implement SAML integration with LoginRadius, you configure LoginRadius as the Service Provider, import the customer’s SAML metadata (SSO URL, certificate, EntityID), define bindings, and map SAML attributes to LoginRadius profile fields. During authentication, LoginRadius issues the AuthnRequest, receives the SAML Response, validates the SAML assertion, and establishes the user’s CIAM profile and session.
LoginRadius as the Service Provider
In customer and partner authentication scenarios, LoginRadius typically serves as the SAML SP. The customer’s enterprise IdP handles user authentication, and LoginRadius consumes the SAML Response and assertion. This model centralizes SAML logic inside LoginRadius instead of individual applications.
When LoginRadius acts as the SP, it:
-
Generates the AuthnRequest
-
Sends the request to the IdP’s SSO endpoint
-
Receives and validates the SAML Response at its ACS URL
-
Verifies signatures and certificate data
-
Extracts NameID and attributes
-
Creates or updates the user profile
Issues LoginRadius tokens or sessions to downstream applications
This architecture makes enterprise SAML onboarding mostly configuration-driven rather than code-driven.
Configuring a SAML Identity Provider in LoginRadius
When integrating a customer’s IdP, the main setup steps occur in the LoginRadius Admin Console.
1. IdP Metadata and SSO URL
LoginRadius needs the enterprise IdP’s metadata or manual entries for:
-
SSO URL
-
EntityID
-
Signing certificate
-
Supported bindings
Providing accurate metadata is essential for a stable SAML authentication flow.
2. Selecting the Binding (Redirect or POST)
LoginRadius supports:
-
HTTP-Redirect binding — common for AuthnRequest
-
HTTP-POST binding — common for SAML Response
You choose based on the IdP’s capabilities. LoginRadius automatically sends the request using the binding configured for the IdP.
3. Setting ACS URL and SP Metadata
When LoginRadius is the SP, its ACS URLs are fixed and provided in the documentation. The ACS URL is where the customer’s IdP posts the SAML Response.
LoginRadius SP metadata includes:
-
SP EntityID
-
ACS URL
-
Certificate (if signing is enabled)
-
Supported NameID formats
This metadata must be added to the customer’s IdP configuration.
Mapping SAML Attributes to LoginRadius Profiles
SAML IdPs vary widely in how they name attributes (email vs. mail vs. userPrincipalName). LoginRadius uses attribute mapping to normalize those into consistent CIAM fields.
Common mappings include:
-
Email →
Email -
First name →
FirstName -
Last name →
LastName -
Unique enterprise user ID →
ID -
Groups, roles, or department →
Custom fields
LoginRadius supports flexible mapping definitions so attributes from any IdP schema can be aligned with your user model.
Learn more about SAML attribute mapping in LoginRadius
RelayState and Application Routing
RelayState is used to return the user to the correct application route after authentication. LoginRadius preserves RelayState between the AuthnRequest and SAML Response, allowing:
-
Deep links
-
App-specific redirects
-
Multi-tenant routing controls
This enables seamless handoffs even in complex application structures.
Example End-to-End SAML Authentication Flow with LoginRadius
Below is a typical B2B/enterprise SSO scenario.
Scenario: Enterprise IdP → LoginRadius (SP) → Application
-
User attempts to access the application.
-
Application redirects the user to LoginRadius for authentication.
-
LoginRadius generates the AuthnRequest and sends it to the customer’s IdP.
-
IdP authenticates the user (password, MFA, conditional access).
-
IdP returns a signed SAML Response to LoginRadius’s ACS URL.
-
LoginRadius verifies the assertion and extracts profile attributes.
-
LoginRadius creates or updates the CIAM profile.
-
LoginRadius returns a session or access token to the application.
-
User is granted access with normalized identity data.
Outcome
-
Applications do not need to understand SAML.
-
Customers retain complete control over authentication.
-
LoginRadius acts as the normalization and security enforcement layer
Common Security Risks in SAML SSO Authentication
SAML is secure when implemented correctly, but there are recurring patterns that weaken deployments:
-
Unsigned or partially signed assertions
- Some IdPs can be configured to sign only parts of the SAML message or not sign assertions at all.
- Unsigned assertions undermine the trust model and make SAML security tokens vulnerable to tampering.
-
Loose audience and recipient validation
- Failing to verify the
AudienceRestrictionorRecipientfields allows assertions intended for one SP or ACS to be reused elsewhere. - This is especially risky in multi-tenant CIAM environments.
- Failing to verify the
-
Clock skew and expired assertions
- Time windows (
NotBefore,NotOnOrAfter) that are too wide or not validated enable assertion replay. - Time mismatch between IdP and SP can cause valid tokens to be rejected, leading to “intermittent” login issues.
- Time windows (
-
Open redirect via RelayState
- If RelayState values are not validated against an allowlist, they can be used to redirect users to untrusted domains after successful login.
-
Weak certificate lifecycle management
- Expired certificates, outdated algorithms, or untracked rotations can invalidate a working SAML implementation overnight.
- Attack surface increases when old certificates are not retired or removed.
Hardening Checklist for SAML-Based Authentication
Before putting any SAML SSO authentication integration into production, it helps to treat security as a checklist rather than an assumption.
Core hardening actions:
-
Enforce signed assertions at minimum
- Prefer signing both the SAML Response and the assertion.
- Reject any assertion that is not signed or uses unexpected algorithms.
-
Validate audience and recipient strictly
- Confirm the
Audiencematches your SP EntityID. - Confirm
RecipientandDestinationmatch your ACS URL. - Treat mismatches as hard failures, not warnings.
- Confirm the
-
Use tight validity windows
- Verify
NotBeforeandNotOnOrAfterand reject tokens outside a small, configurable tolerance window. - Configure reasonable clock skew tolerance (e.g., a couple of minutes) to account for system time differences.
- Verify
-
Limit and validate RelayState
- Restrict RelayState to known paths or identifiers.
- Avoid passing arbitrary URLs; use internal route keys or IDs instead.
-
Monitor certificate state and algorithms
- Track certificate expiry dates and plan rotations well in advance.
- Ensure only modern, secure algorithms (e.g., RSA-SHA256) are used.
- Remove legacy certificates from configuration as soon as they are rotated out.
How LoginRadius Supports a Hardened SAML Implementation
LoginRadius can centralize many of these controls so individual applications don’t have to manage XML security on their own.
In a hardened deployment, LoginRadius can be configured to:
-
Accept only SAML responses and assertions that are correctly signed with trusted certificates
-
Validate
AudienceRestriction,Recipient, andDestinationfor each request -
Enforce strict time checks on each SAML security token
-
Normalize and validate NameID formats and required attributes before creating a session
-
Integrate custom business rules for RelayState and post-login routing
Because this logic lives at the platform level, adding a new customer IdP reuses the same hardened behavior without custom code in the application.
MFA and SAML: Where Stronger Assurance Belongs
SAML itself doesn’t define multifactor authentication, but it can carry information about how the user authenticated.
Best practices for MFA in SAML environments:
-
Perform MFA at the IdP
- Enterprises typically own the authentication policy; they enforce MFA before issuing a SAML assertion.
-
Use authentication context where supported
- Some IdPs populate
AuthnContextClassRefto indicate MFA or step-up was used.
- Some IdPs populate
-
Avoid duplicating MFA at the SP layer
- When LoginRadius is consuming SAML, it should be configured to respect the IdP’s assurance level rather than re-challenge the user, unless you explicitly require step-up for sensitive actions.
LoginRadius can rely on the IdP’s policy while still applying its own rules for specific applications or high-risk flows.
Logging, Monitoring, and Incident Response for SAML Authentication
Even a well-hardened SAML authentication flow can fail or be misconfigured. Logging is critical for both troubleshooting and security monitoring.
What to log:
-
IdP entity ID and SP entity ID involved in each SAML transaction
-
Timestamps for AuthnRequest, Response, and assertion validity window
-
Result of signature and certificate validation
-
Reason for any failed assertion (expired, audience mismatch, missing attribute)
-
Mappings applied (e.g., which attribute became the primary identifier)
How LoginRadius helps:
-
Acts as a central logging point for all SAML interactions across customers
-
Gives operations teams one place to review failures and investigate anomalies
-
Reduces the need for each application to have deep SAML diagnostics built in
This makes SAML-related incident response faster and more consistent.
Common Pitfalls to Avoid in SAML Implementation
To close out the security section, here are some recurring issues that cause problems in production:
-
Testing with no signatures and forgetting to turn them on
-
Using different ACS URLs in test vs. production without updating IdP config
-
Relying on email as the only identifier when it isn’t stable in the enterprise
-
Allowing any RelayState value instead of validating it
-
Ignoring time synchronization between IdP and SP systems
Addressing these early keeps your SAML-based authentication predictable and reduces the support overhead once more customers connect their IdPs.
Troubleshooting SAML Authentication Flow Issues
Troubleshooting SAML authentication issues requires checking metadata configuration, ACS URLs, certificates, NameID formats, timestamps, and signature validity. Most failures in a SAML authentication flow come from mismatched configuration between the Identity Provider and Service Provider, especially around audience, certificates, and time-based conditions.
Why Troubleshooting SAML Can Be Difficult
SAML errors rarely appear as readable messages. Most problems surface as generic failures such as:
-
“Login failed.”
-
“We were unable to process the SAML Response.”
-
“Invalid signature.”
-
“No valid assertion found.”
Because SAML messages pass through browser redirects and contain signed XML, diagnosing issues requires a structured process.
Below is a practical, architect-focused troubleshooting approach.
Most Common SAML Integration Errors and Their Fixes
1. “Signature validation failed”
Cause:
-
Incorrect or outdated IdP certificate
-
Signature applied to the wrong XML element
-
SAML Response signed but not the assertion (or vice versa)
-
Modified or malformed XML
Fix:
-
Confirm the IdP’s certificate in LoginRadius matches the active signing certificate.
-
Re-import IdP metadata after certificate rotation.
-
Ensure assertions are fully signed (recommended).
-
Validate that the XML was not altered by proxies or formatting tools.
2. “Audience restriction failed” / “Audience mismatch”
Cause:
The assertion’s <Audience> does not match the SP’s EntityID.
Fix:
-
Ensure the IdP’s SAML config uses the exact LoginRadius EntityID.
-
Avoid trailing slashes or environment mismatches (prod vs staging).
-
If using multi-tenant SAML, ensure each tenant has a unique EntityID and correct mapping.
This is the single most common SAML integration failure in CIAM deployments.
3. “Recipient mismatch” / “Invalid ACS URL”
Cause:
The SAML Response was posted to the wrong ACS URL or the ACS in the assertion doesn’t match what LoginRadius expects.
Fix:
-
Verify the ACS URL in the IdP matches the one provided in the LoginRadius configuration.
-
Double-check protocol (http vs https), environment, and trailing slash.
-
Ensure the assertion’s Recipient and Destination fields point to the correct ACS.
4. “SAML assertion has expired”
Cause:
The validity window in the Conditions block has passed.
Fix:
-
Validate
NotBeforeandNotOnOrAftertimestamps. -
Reduce time skew between servers (NTP sync is critical).
-
Narrow the validity window for security, but ensure it accounts for network latency.
5. “NameID is missing or unsupported”
Cause:
The IdP sent a NameID in a format the SP doesn’t accept, or didn’t send any NameID at all.
Fix:
-
Standardize NameID to email or persistent format.
-
Confirm the IdP is populating NameID in every SAML assertion.
-
Fall back on attribute-based identifiers if required and supported.
6. “Required attributes missing”
Cause:
The IdP did not include necessary attributes such as email, user ID, or profile data.
Fix:
-
Add required attributes to the IdP’s SAML claim rules.
-
Ensure correct attribute names (email vs mail vs userPrincipalName).
-
Adjust attribute mapping in LoginRadius to match the IdP schema.
7. RelayState issues (redirect errors)
Cause:
RelayState contains an unexpected or invalid value, often a full external URL.
Fix:
-
Allow only approved relay values or route keys.
-
Validate RelayState before redirecting the user.
-
Ensure IdPs don’t override the RelayState provided by LoginRadius.
8. Compression and encoding problems
Cause:
Improperly compressed or encoded SAML messages, especially during Redirect binding.
Fix:
-
Confirm the IdP uses deflate compression correctly.
-
Capture the raw AuthnRequest/Response with browser dev tools to verify encoding.
-
Switch to POST binding if redirect encoding is inconsistent.
Step-by-Step Debugging Workflow for CIAM Architects
When a SAML implementation fails, use this consistent workflow:
Step 1: Capture the Raw SAML Response
-
Use browser dev tools → Network tab
-
Look for the POST to the ACS endpoint
-
Copy the
SAMLResponsebase64 value for analysis
Step 2: Decode and Validate the XML
-
Use a SAML decoder (or LoginRadius debug tools)
-
Check for malformed XML, missing signatures, wrong issuer
Step 3: Verify Certificates
-
Compare the signing certificate in the SAML Response to the certificate configured in LoginRadius
-
Recheck metadata if mismatched
Step 4: Check Conditions
-
Inspect
NotBefore,NotOnOrAfter -
Validate the time window against server clocks
Step 5: Confirm Audience and Recipient
-
Ensure Audience = SP EntityID
-
Ensure Recipient = LoginRadius ACS URL
Step 6: Review Attributes
-
Confirm expected fields: email, ID, NameID, custom attributes
-
Correct any mismatches between IdP and LoginRadius mappings
Step 7: Re-test with debug logging enabled
- Most failures resolve quickly once the mismatched field is identified.
How LoginRadius Simplifies Troubleshooting
You can integrate any customer IdP without dealing with the underlying XML each time. LoginRadius centralizes:
-
Signature and certificate validation
-
Audience and condition checking
-
NameID and attribute normalization
-
Detailed error logs for failed SSO attempts
-
Multi-tenant SAML routing and configuration
This reduces friction when onboarding new customers or maintaining long-term SAML integrations.
Also read: SAML or OIDC: Which Protocol is Better for Your Business?
Wrapping up: SAML’s Role in a LoginRadius CIAM Architecture
SAML remains a required protocol for enterprise and B2B authentication. Many organizations still depend on established SAML IdPs, which means modern CIAM platforms must support reliable SAML-based authentication to integrate with customer and partner identity systems.
LoginRadius simplifies this by handling the full SAML authentication flow i.e., issuing AuthnRequests, validating assertions, checking signatures and conditions, and mapping SAML attributes into unified profiles. This keeps SAML complexity out of applications and ensures consistent, secure onboarding for any enterprise IdP.
As long as organizations rely on SAML to manage identity, LoginRadius provides the foundation to integrate those systems cleanly, securely, and at scale.
FAQs
1. What is SAML (Security Assertion Markup Language)?
SAML is an XML-based standard used to transfer authentication and authorization data between an Identity Provider (IdP) and a Service Provider (SP). It enables secure SSO by allowing the IdP to issue a signed SAML assertion that the SP can trust without exchanging passwords.
2. How is SAML used for authentication in CIAM?
In CIAM, SAML allows enterprise customers or partners to authenticate with their own IdP. The IdP verifies the user’s identity and sends a signed SAML assertion to the CIAM platform, which then creates or updates the user’s profile and establishes a session—without storing enterprise credentials.
3. Why does SAML still matter even with newer protocols like OIDC?
SAML remains essential because many organizations still rely on mature, enterprise-grade IdPs such as ADFS, PingFederate, Okta, and Azure AD. These systems power workforce and partner authentication and are deeply integrated into corporate infrastructure, making SAML support mandatory for CIAM and SaaS vendors.
4. What are the core components of SAML that architects should understand?
Key building blocks include IdP and SP roles, SAML assertions, metadata, certificates, NameID formats, Conditions (validity rules), AttributeStatements (profile data), and bindings such as HTTP-Redirect and HTTP-POST. These elements define how SAML-based authentication operates.
5. How does the SAML authentication flow work?
The SP sends an AuthnRequest to the IdP, the IdP authenticates the user, and the browser posts a signed SAML Response back to the SP’s ACS endpoint. The SP validates the assertion’s signature, time window, and audience before creating a session. This browser-mediated sequence is the foundation of how SAML authentication works.
6. What happens during a real SAML authentication exchange?
A full exchange includes building a signed AuthnRequest, authenticating at the IdP, generating a SAML Response, validating the SAML assertion, checking Conditions timestamps, ensuring correct Audience and Recipient fields, processing NameID formats, and mapping attributes to the user’s profile.
7. How do you implement SAML integration with LoginRadius?
LoginRadius is typically configured as the SP. You import IdP metadata, set the ACS URL, configure bindings, upload signing certificates, and define attribute mappings. LoginRadius handles AuthnRequest creation, assertion validation, and profile updates, simplifying multi-IdP onboarding.
8. What are the common security risks in SAML SSO authentication?
Risks include unsigned assertions, mismatched certificates, weak audience validation, expired or future-dated Conditions timestamps, inconsistent NameID formats, and unsafe RelayState values that can create redirect vulnerabilities.
9. What are best practices for hardening SAML-based authentication?
Best practices include enforcing signed assertions, validating audience and recipient fields, tightening validity windows, ensuring accurate metadata, validating RelayState, rotating certificates regularly, and using stable identifier formats for long-term identity resolution.
10. What common pitfalls should be avoided during SAML implementation?
Frequent issues include incorrect ACS URLs, outdated IdP certificates, mismatched EntityIDs between environments, missing NameID fields, inconsistent attribute naming conventions, and failing to synchronize server clocks between the IdP and SP.
11. How does LoginRadius simplify debugging and maintaining SAML integrations?
LoginRadius centralizes assertion validation, certificate checks, metadata management, attribute normalization, and error reporting. This reduces complexity for applications and provides a consistent, platform-level approach to diagnosing and resolving SAML SSO authentication issues.


